Even when you suspect that your MacOS computer is infected, it can be very difficult to be sure one hundred percent. One way to detect malware is to analyze the behavior of processes, for example, whether it reads keyboard input or launches it every time the system boots. Thanks to the free utilities ReiKey and KnockKnock, we can detect keyloggers and other suspicious applications trying to hide and survive on our system.
There are many ways a keylogger or other types of malware can infiltrate a MacOS system. For example, through an infected file, when a hacker uses a USB Rubber Ducky device or, more likely, your jealous spouse or family member in the heat of overprotectiveness tries to track your activity.
MacOS malware
Patrick Wardle, a former NSA hacker, researches malware tailored to Apple devices and has created several tools to improve the security of MacOS. Patrick posted real malware for MacOS on his website https://objective-see.com/ so that other researchers can study these instances too. Some of the malware found in the "wild" is truly shocking. A simple search for keyloggers returns five different types, tailored for devices where the operating system MacOS is installed.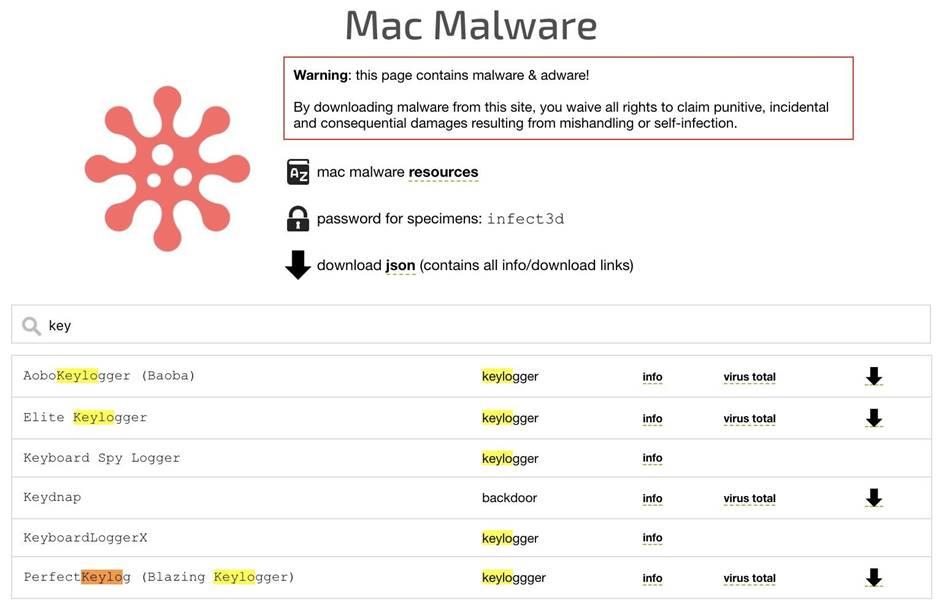
Figure 1: List of keyloggers created for macOS
A natural question immediately arises: how to protect yourself from all kinds of malware, even if there are at least five options for keyloggers? Patrick believes that you need to analyze the behavior of malware, and not search for the programs themselves by signatures.
For example, a keylogger connects to a stream of keyboard events, allowing an attacker to intercept all pressed keys, after which accounts are compromised, communications are intercepted, and so on. However, for a permanent presence in the system, malware must be launched immediately after user authorization, so that the victim only needs to open the malicious file once.
ReiKey and KnockKnock can detect new types of malware
ReiKey allows you to search for keyloggers by one of the most basic characteristics, namely, it searches for programs connected to the stream of keyboard events. Searching for access to the keyboard stream allows us to find all keyloggers installed on the system, not just those present in the antivirus signature database.In addition, since the keylogger is constantly present in the system, we can detect this type of malware using another free utility, KnockKnock. When this application is launched, all permanently installed programs are structured into understandable categories that include programs commonly used by malware: browser extensions, launch elements (such as daemons and agents), kernel modules, and plugins.
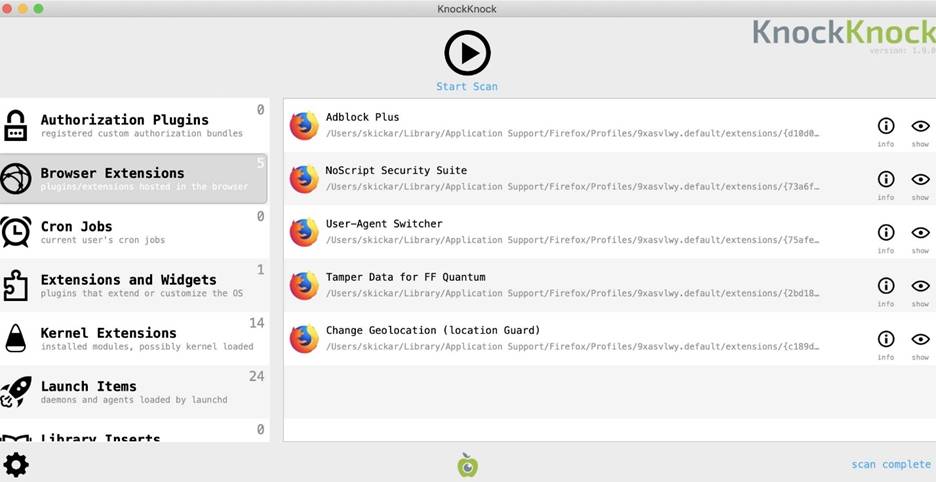
Figure 2: Categorizing Continuous Programs in the KnockKnock Application
After scanning your system, KnockKnock will find all programs that are running on a permanent basis, which will then be checked in the VirusTotal service.
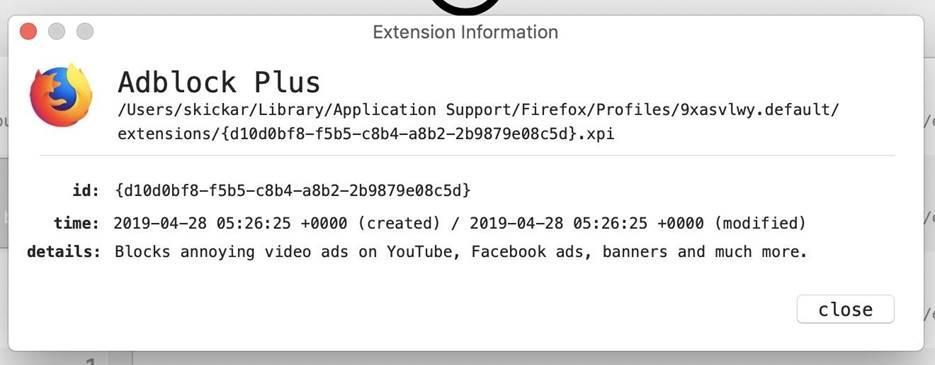
Figure 3: More details on the Adblock Plus extension
If there is malware lurking on your system, you can detect this program and see the details by clicking on the "Info" icon. If it detects files marked with the VirusTotal service and looking suspicious, most likely your system has been compromised and malware, adware, or other unwanted software has been installed.
The video below shows an example of testing a system with MacOS using the above utilities.
What is needed
You will need a MacOS system with all updates, an internet connection, and a browser to download KnockKnock and ReiKey.Step 1. Downloading utilities from Objective-see.com
Go to the section with the ReiKey application and click on the Download link under the icon in the upper left corner.
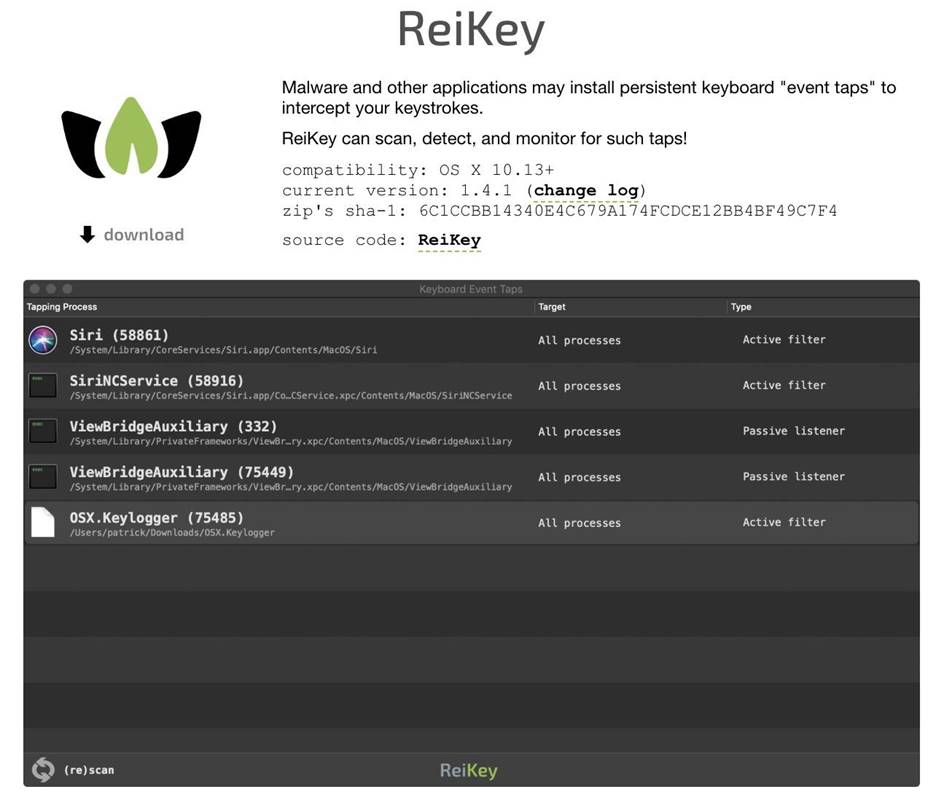
Figure 4: Section of the ReiKey Application
Download and unpack the installer. Then double click on the "ReiKey Installer.app" file to launch the installer.
Step 2. Installing ReiKey
After starting the installer, click on the "Install" button to start installing ReiKey.
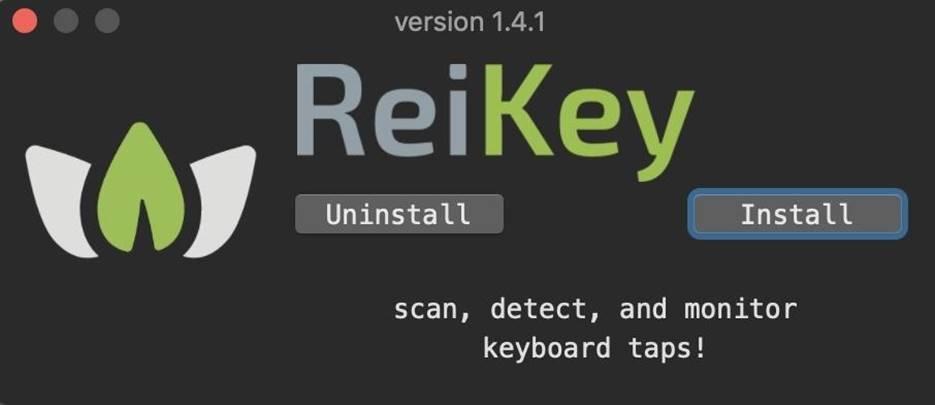
Figure 5: ReiKey Installer Interface
Once the installation is complete, click on the Next button to close the installer. An icon should appear in the taskbar, allowing you to access the ReiKey settings.
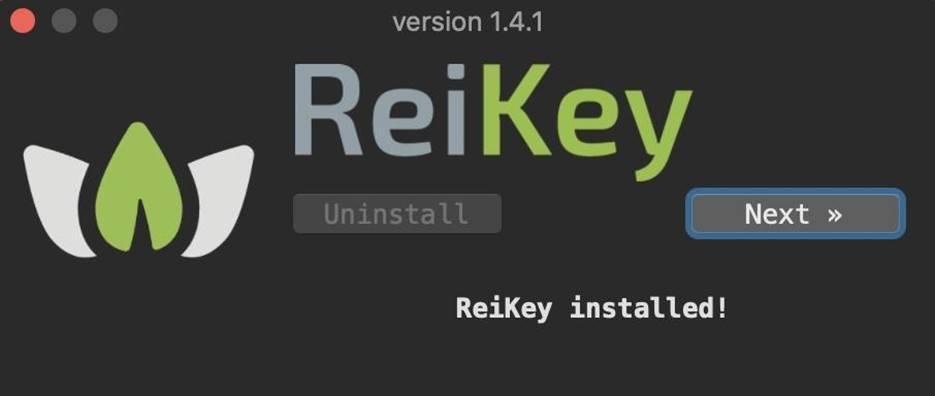
Figure 6: Completing the installation
On the taskbar, click on the ReiKey icon, and then go to the "Preferences" section, where there is a list of options that allow you to specify whether applications should be launched after logging into the system, whether an icon should be displayed in the status bar, and whether Apple applications should be ignored.
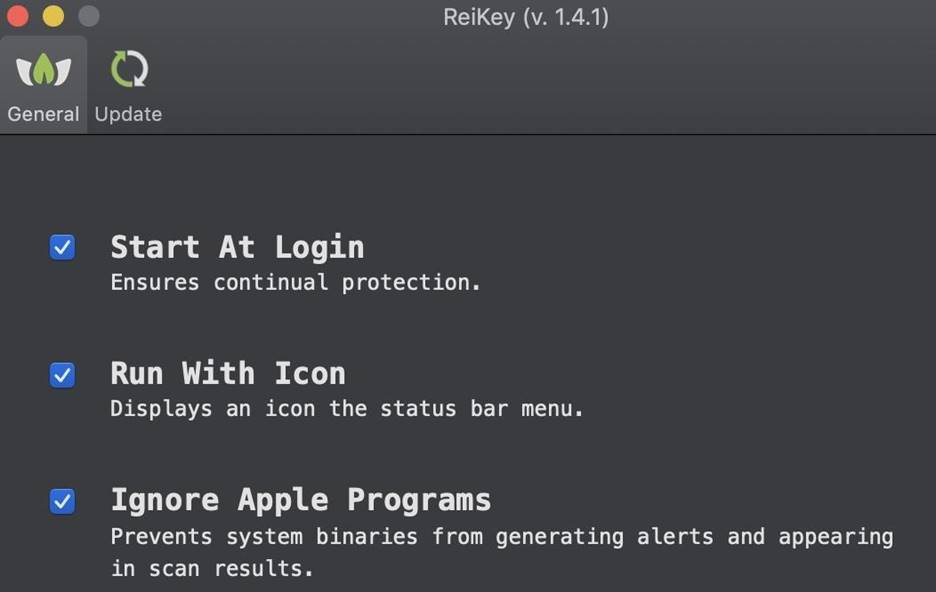
Figure 7: Section with ReiKey application settings
When I ran a Python keylogger, I got the following warning on my device.
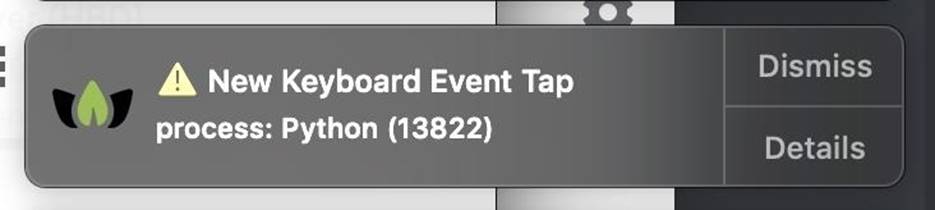
Figure 8: Notification of a new event associated with an available keyboard stream
Step 3. Search for keyloggers
After installing and configuring ReiKey, we are ready to scan the system.
Click on the icon in the status bar again, but this time start scanning. After a while, a window with the results will appear, where the programs that have access to the keyboard stream will be displayed.
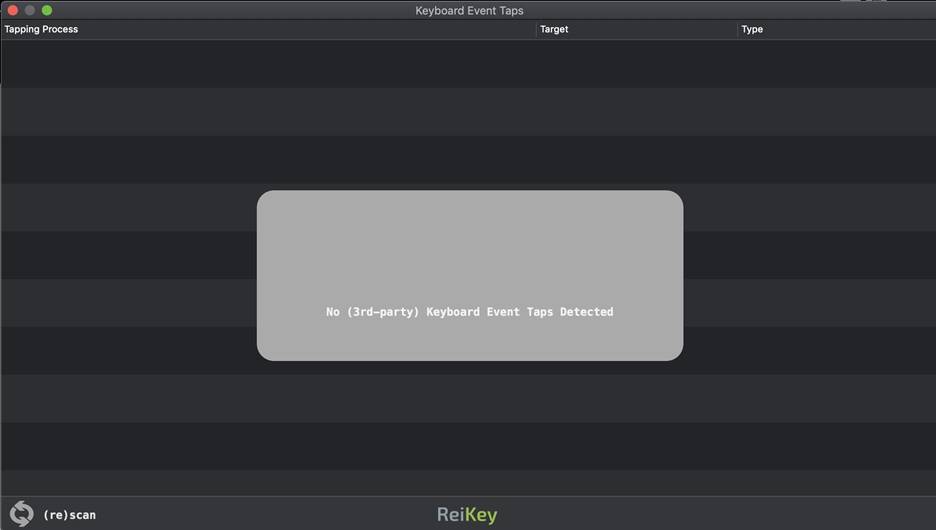
Figure 9: Scan Results
Based on the scan results, as can be seen from the picture above, nothing was found. If the list were not empty, then there are applications that read every keystroke.
Step 4. Installing KnockKnock
Go to the section with the KnockKnock application and click on the Download link under the icon in the upper left corner.
Figure 10: Section of the ReiKey Application
Once downloaded, you can launch KnockKnock immediately without installation.
Step 5. System scan
Click on the "KnockKnock.app" file, and then a window should appear as shown in the figure below. Then click on the arrow icon to initiate scanning. The scanning procedure requires granting rights to the application to access different folders and programs if you are using the latest version of macOS, Catalina.
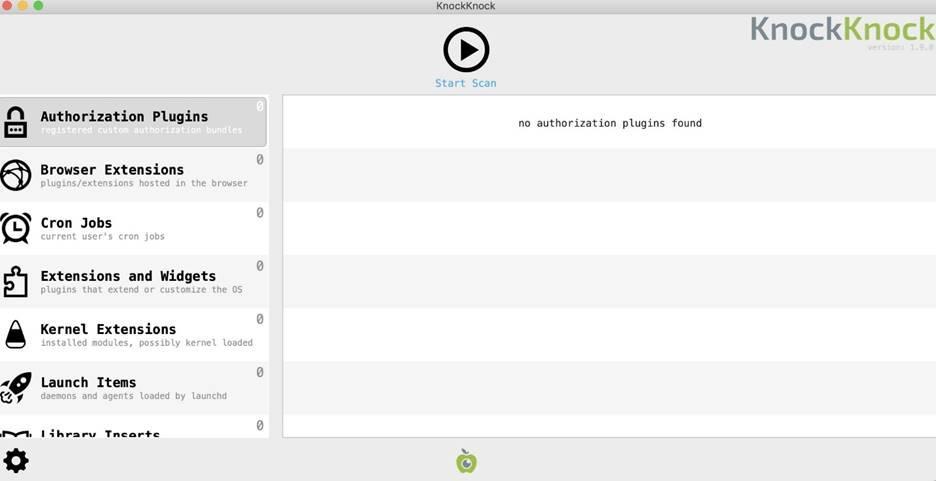
Figure 11: KnockKnock Application Interface
After the scan is complete, a list of permanently installed programs will appear on your system, many of which are not malicious. It is recommended that you check each application carefully. If, for example, you find browser extensions that you have not installed, it is best to uninstall those applications.
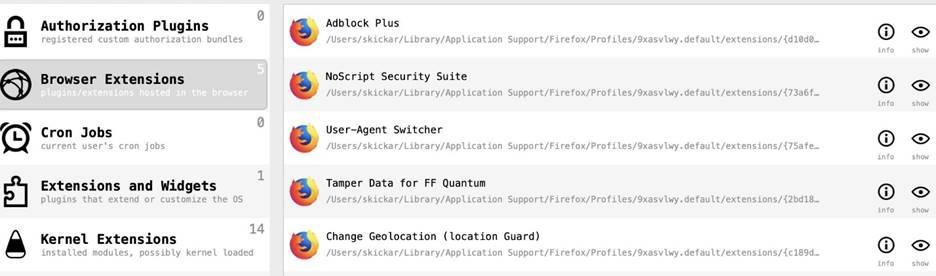
Figure 12: List of found browser extensions
We can also detect applications with suspicious characteristics. For example, an unsigned script installed on a permanent basis, opposite which an icon in the form of an open lock is displayed.
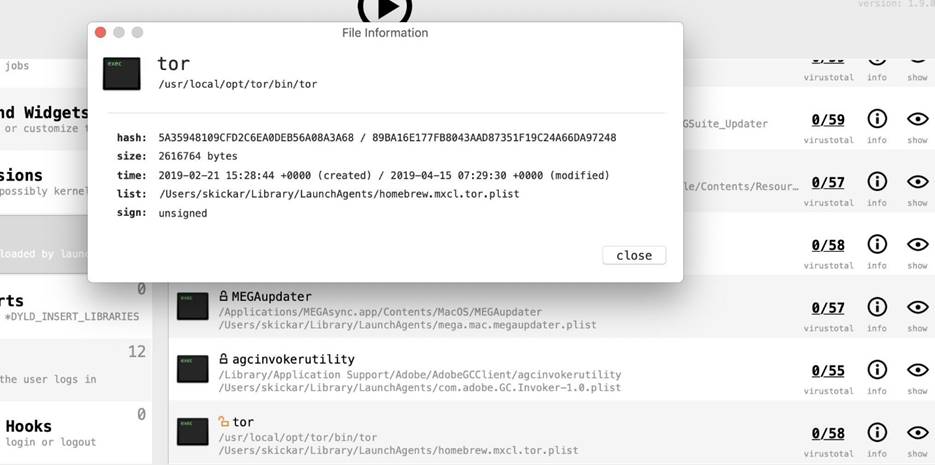
Figure 13: An example of a suspicious application as an unsigned script
More details can be found by clicking on the "Info" icon.
Step 6. Checking questionable files
If we want to know more details about the file, we can look at the information from the VirusTotal service, which reflects the percentage of detection and a link to a detailed report. To resend the file, click on "rescan", after which the file will be sent to VirusTotal again.
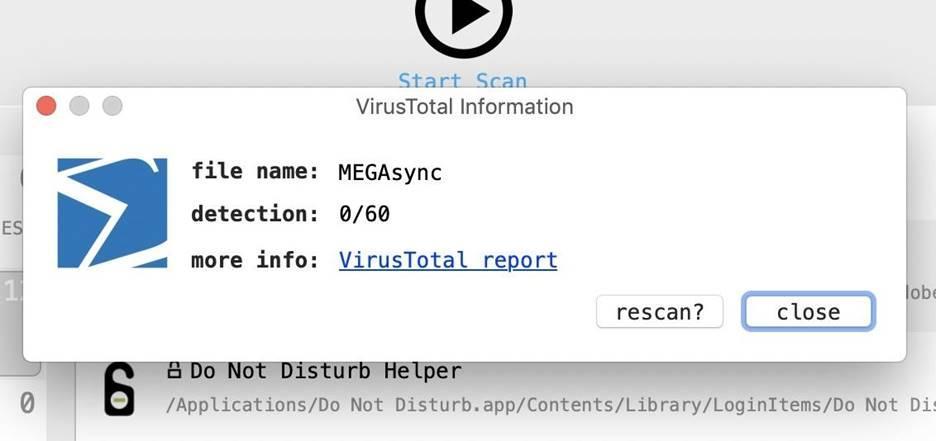
Figure 14: File information from the VirusTotal service
Resubmitting will give you access to a detailed report, which displays information about the detection of a previously detected unsigned Tor application.
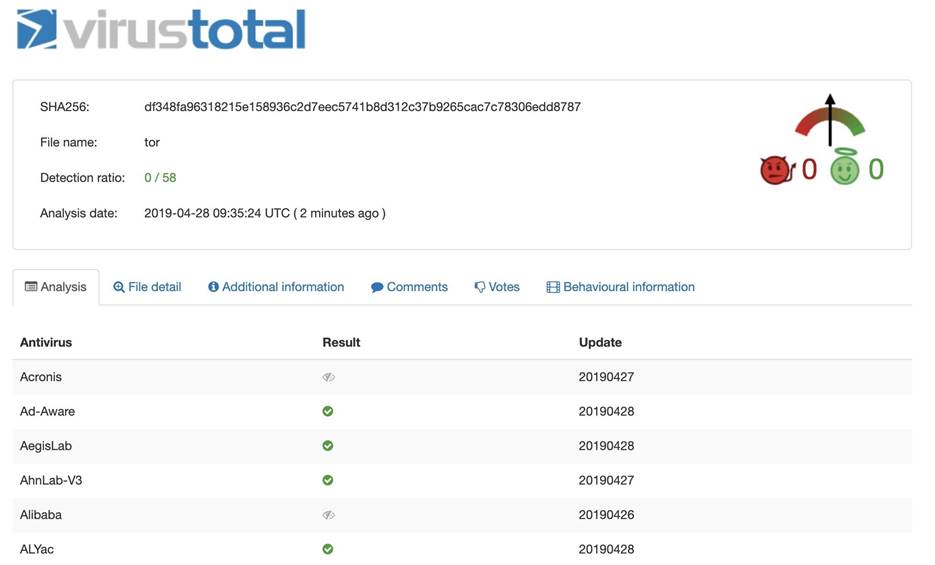
Figure 15: Detailed report of the Tor application
At first glance, the file does not look malicious, but if it were, now we know how to find out exactly.
Conclusion
The typical MacOS user may have difficulties in the field of malware detection, however, thanks to the ReiKey and KnockKnock utilities, suspicious applications can be detected as soon as possible and even immediately after installation. If you suspect that your other half has installed a keylogger or a work colleague is spying on activity on your system or unwanted adware is consuming a lot of memory, these utilities will help you.I also recommend that you familiarize yourself with other free utilities at objective-see.com.
Hope you enjoyed this tutorial on ReiKey and KnockKnock malware detection apps on MacOS.
(c) securitylab.ru
