Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
Fraudsters technically exploit DNS to bypass security systems.
Infoblox reports that the Savvy Seahorse cybercrime group is abusing CNAME records to create a traffic distribution system that supports financial fraud campaigns. The operation began no later than August 2021 and is characterized by short waves of attacks lasting from 5 to 10 days.
Scammers attract victims through Facebook ads*, directing them to fake investment platforms where people are tricked into depositing funds and entering sensitive personal data. A distinctive feature of the campaigns is the use of chatbots that interact directly with victims, convincing them of a high return on investment and automating the fraud process.
Savvy Seahorse creatively uses Canonical Name (CNAME) records as a Traffic Delivery System (TDS) for its operations, making it easy to change IP addresses to evade detection.
A CNAME record is a DNS record that maps a domain or subdomain to another domain name, rather than directly to an IP address. This causes the CNAME to act as an alias for the target domain, which simplifies redirection management and ensures that any changes to the target domain's IP address are automatically applied to the CNAME as well.
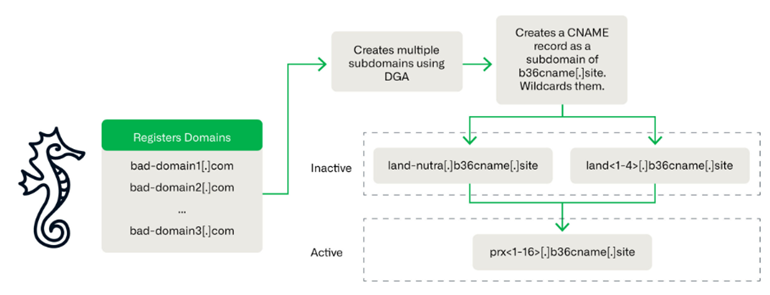
Savvy Seahorse Attack Scheme
For its attacks, Savvy Seahorse registers multiple subdomains that are linked by a common CNAME record that points to the main campaign domain. This technique provides a single IP address for all records, making it easier to rotate targets when IP addresses are blocked by security tools and helping to avoid detection.
This approach requires attackers to have a deeper knowledge of DNS, but has so far remained poorly understood in the cybersecurity literature. Infoblox notes that this is the first publicly recorded case of CNAME abuse for TDS.
Savvy Seahorse uses Domain Generation Algorithms (DGA) to create and manage thousands of domains in the CNAME TDS system. Such domains can change their status from " parked "to" in testing "and" active campaign", which makes it more difficult to track and map their infrastructure.
A distinctive feature of Savvy Seahorse is the distribution of infrastructure across multiple registrars and hosting providers, so as not to attract attention and ensure operational sustainability.
Fraudulent subdomains host registration forms designed to steal the personal information of deceived victims. After sending the data, the subdomain checks the victim's location by IP address and the authenticity of the information provided, after which confirmed users are redirected to a fake trading platform, where they are asked to top up their balance using bank cards, cryptocurrency, and other payment methods.
Chatbots that plausibly mimic ChatGPT, WhatsApp, and Tesla play a key role in social engineering. Scam pages also use Meta Pixel trackers to track performance, which is probably used to improve tactics.
Savvy Seahorse Attack Review
For a complete list of compromise indicators and domains used in Savvy Seahorse campaigns, see the company's full report.
Infoblox reports that the Savvy Seahorse cybercrime group is abusing CNAME records to create a traffic distribution system that supports financial fraud campaigns. The operation began no later than August 2021 and is characterized by short waves of attacks lasting from 5 to 10 days.
Scammers attract victims through Facebook ads*, directing them to fake investment platforms where people are tricked into depositing funds and entering sensitive personal data. A distinctive feature of the campaigns is the use of chatbots that interact directly with victims, convincing them of a high return on investment and automating the fraud process.
Savvy Seahorse creatively uses Canonical Name (CNAME) records as a Traffic Delivery System (TDS) for its operations, making it easy to change IP addresses to evade detection.
A CNAME record is a DNS record that maps a domain or subdomain to another domain name, rather than directly to an IP address. This causes the CNAME to act as an alias for the target domain, which simplifies redirection management and ensures that any changes to the target domain's IP address are automatically applied to the CNAME as well.

Savvy Seahorse Attack Scheme
For its attacks, Savvy Seahorse registers multiple subdomains that are linked by a common CNAME record that points to the main campaign domain. This technique provides a single IP address for all records, making it easier to rotate targets when IP addresses are blocked by security tools and helping to avoid detection.
This approach requires attackers to have a deeper knowledge of DNS, but has so far remained poorly understood in the cybersecurity literature. Infoblox notes that this is the first publicly recorded case of CNAME abuse for TDS.
Savvy Seahorse uses Domain Generation Algorithms (DGA) to create and manage thousands of domains in the CNAME TDS system. Such domains can change their status from " parked "to" in testing "and" active campaign", which makes it more difficult to track and map their infrastructure.
A distinctive feature of Savvy Seahorse is the distribution of infrastructure across multiple registrars and hosting providers, so as not to attract attention and ensure operational sustainability.
Fraudulent subdomains host registration forms designed to steal the personal information of deceived victims. After sending the data, the subdomain checks the victim's location by IP address and the authenticity of the information provided, after which confirmed users are redirected to a fake trading platform, where they are asked to top up their balance using bank cards, cryptocurrency, and other payment methods.
Chatbots that plausibly mimic ChatGPT, WhatsApp, and Tesla play a key role in social engineering. Scam pages also use Meta Pixel trackers to track performance, which is probably used to improve tactics.
For a complete list of compromise indicators and domains used in Savvy Seahorse campaigns, see the company's full report.

