Carding
Professional
- Messages
- 2,870
- Reaction score
- 2,493
- Points
- 113
Who needs to hide behind other cybercriminals for attacks?
Cybersecurity researchers from Deep Instinct discovered a new campaign, called Rusty Flag, aimed at Azerbaijani targets. The attacks use a decoy document related to the Karabakh conflict and a new type of malware in the Rust programming language.
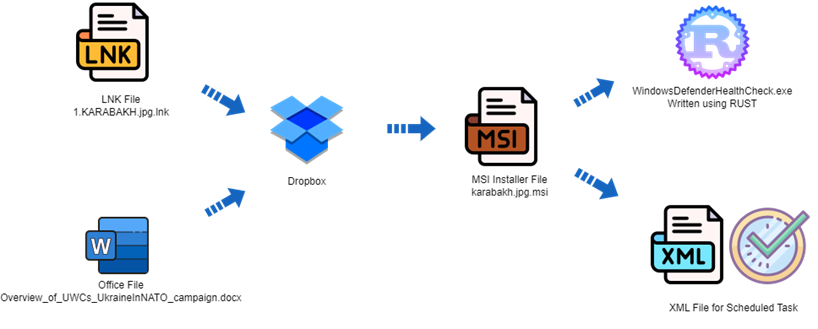
The attack chain starts with a malicious LNK file with a low detection level called "1. KARABAKH. jpg.lnk". The file shows an image related to the Karabakh incident and runs the MSI installer hosted on DropBox. The installer contains malicious code in the Rust language, a task for the task scheduler in XML format, and a decoy in the form of an image. Experts also found another MSI file containing a different version of the same malicious code, but it was not possible to determine the initial access vector for this campaign.
Attack Chain
It turned out that one of the baits was previously used by the Storm-0978 group. However, this is most likely a false flag attack attempt (hence the name of the campaign). Instead of exploiting the CVE-2023-36884 vulnerability, as in the attacks on supporters of Ukraine who attended the NATO summit in Vilnius, the group exploited the CVE-2017-11882 vulnerability, which allows remote code execution to download and install an MSI file.
After installing the file, the malicious code goes into standby mode for 12 minutes to bypass security research and sandbox analysis. Then it starts collecting information about the infected machine, which is then encrypted and sent to the attackers server via the hard-coded port 35667. Deep Instinct researchers were unable to attribute the attacks to any hacker group.
Cybersecurity researchers from Deep Instinct discovered a new campaign, called Rusty Flag, aimed at Azerbaijani targets. The attacks use a decoy document related to the Karabakh conflict and a new type of malware in the Rust programming language.
The attack chain starts with a malicious LNK file with a low detection level called "1. KARABAKH. jpg.lnk". The file shows an image related to the Karabakh incident and runs the MSI installer hosted on DropBox. The installer contains malicious code in the Rust language, a task for the task scheduler in XML format, and a decoy in the form of an image. Experts also found another MSI file containing a different version of the same malicious code, but it was not possible to determine the initial access vector for this campaign.

Attack Chain
It turned out that one of the baits was previously used by the Storm-0978 group. However, this is most likely a false flag attack attempt (hence the name of the campaign). Instead of exploiting the CVE-2023-36884 vulnerability, as in the attacks on supporters of Ukraine who attended the NATO summit in Vilnius, the group exploited the CVE-2017-11882 vulnerability, which allows remote code execution to download and install an MSI file.
After installing the file, the malicious code goes into standby mode for 12 minutes to bypass security research and sandbox analysis. Then it starts collecting information about the infected machine, which is then encrypted and sent to the attackers server via the hard-coded port 35667. Deep Instinct researchers were unable to attribute the attacks to any hacker group.

