Father
Professional
- Messages
- 2,602
- Reaction score
- 837
- Points
- 113
Recently, the case of Roman Seleznev, a major Russian carder from Vladivostok, known under the pseudonyms nCuX, 2pac, Track2, Bulba, and others, has become widely publicized.
On April 21, 2017, a Seattle court sentenced Roman to 30 years in prison (27 years plus the three years he had already served). In other states, the trial of Roman has not yet begun, where he may face life in prison under the RICO law.
The main points of the case are known to everyone, including from the confession of Roman himself. He has been selling dumps for a very long time, and was involved in the largest hacks of Target, Neiman Marcus, Michaels, Staples, and Home Depot store chains, where Trojans for removing dumps were installed directly on cash registers and PoS terminals. His father is Russian State Duma deputy Valery Seleznev, and Roman himself was badly injured during the terrorist attack in Marrakech in 2011, after which his wife ran away with all the money. The guy was detained in the Maldives, and by the time he was detained, Interpol promptly put him on the wanted list (with a "red notice"). Carder's father then demanded that Russia impose sanctions against the Maldives.
Behind all the tinsel among the hundreds of court documents in the case of Roman Seleznev, there are some details that may seem interesting for a general understanding of the picture of how carding and the entire cybercrime world live in Russia.
Unfortunately, get the full set of documents from the PACER electronic database in the Roman Seleznev case (case 2: 11-cr-00070-RAJ) we haven't been able to do it yet, because it requires more than a thousand dollars at the service's prices. But my colleagues have already pulled the most basic documents from PACER, and my colleague Andrey Sporaw posted them in the public domain and commented on them. Here are some of them::
Of particular interest are some facts mentioned in the memorandum on sentencing. It turns out that the Americans established in 2009 that Roman Seleznev was hiding behind an online character under the nickname nCuX. On May 19, 2009, agents of the US Secret Service and the FBI met with their colleagues from the FSB in Moscow, where they presented "significant evidence" of the suspect's hacking activities, including carding and other crimes. The Americans gave their FSB colleagues the suspect's online nicknames and information about the real identity of Roman Seleznev, a resident of Vladivostok. But the attempt at international cooperation failed. According to the documents, "just a month later, on June 21, 2009, nCuX informed his associates on numerous underground forums that he was going out of business. Shortly after, nCuX completely disappeared from the Internet." After that, he created new online personalities Track2 and Bulba.
One might think that in this case, there is a clear fact of cooperation between the FSB and the criminal world of cybercrime, which experts have long been talking about.
It is quite possible that this is the case. The investigation documents note that information about the actions of US law enforcement agencies "was brought to Seleznev." Apparently, he had his own contacts in the FSB. The materials of the investigation mention an exchange of messages between Roman and his accomplice from 2008, where Roman says that he "received protection through contacts of law enforcement agencies in the department of combating computer crime of the FSB."
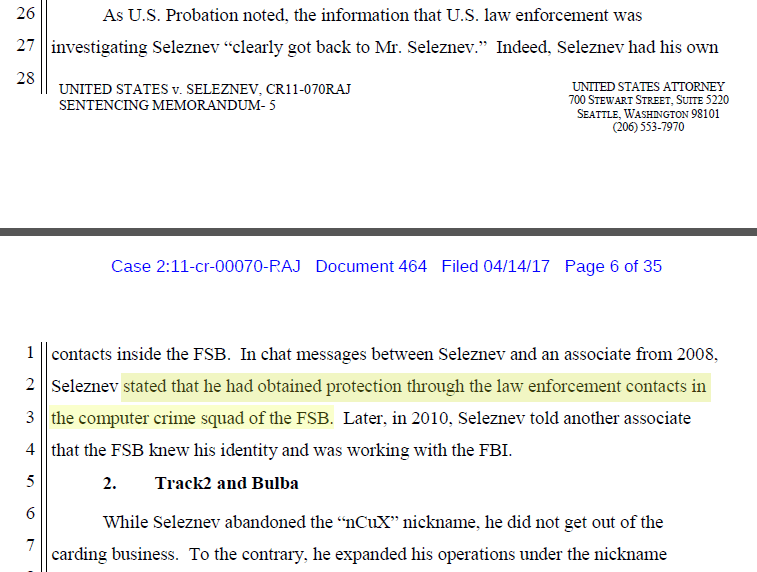
In 2010, Roman told another accomplice that the FSB knew his real name and was working with the FBI. American intelligence agencies feared that due to the impossibility of Roman's extradition from Russian territory (this is prohibited by the Constitution of the Russian Federation), this criminal could go unpunished forever, since he enjoys the patronage of law enforcement agencies and the FSB in Russia.
Therefore, a special operation in the Maldives was the only chance. Although Roman constantly checked PACER's American records, followed the investigation against him, and did not travel to countries where there was a risk of being "under the hood". He only flew where the Americans, in his opinion, could not reach him, but here he still miscalculated. The Americans agreed with the law enforcement agencies of the Maldives and issued the detention five minutes before the flight to Moscow, when Roman formally left the border of the Maldives at the airport and gave his passport to an airport employee.
Among the funds confiscated from him are Liberty Reserve coins worth about $17 million. Roman sold dumps mainly for LR. The investigation found that in total he sold dumps for LR in the amount of $17,886,971.09. The investigation failed to establish how much money Seleznev has on the Bitcoin and WebMoney wallets, which he also accepted payments for, due to the anonymity of these systems. It is likely that after his release, Roman will get access to these wallets.
Interestingly, Roman initially refused to cooperate during his incarceration, but then changed his mind and repeatedly offered his services and tried to provide valuable information. He managed to get a meeting where he revealed to the authorities the identities of many participants in carding forums from 2005 to 2014, but the Secret Service refused to cooperate, because most of this information was already known to it. In addition, Roman made some statements that were obviously false, which reduced the value of cooperation to zero.
If you haven't read the comment to the previous article from user SBKarr, then let's repeat once again where did 30 years of charges for Roman Seleznev come from:
For those who are interested in where they are 30 years old from
The gentleman is charged with 40 felony counts, 38 of which are related to hacking. In US law, episodes are grouped, after which they are either summed up or absorbed by the largest in each group. The largest group is considered as a penalty. In addition, there are crimes that are not grouped and are summed up by the end date of the crime.
In the court decision, the episodes are grouped as follows (I will try to translate them in a way that roughly corresponds to our legal terminology:
Paragraphs 11 and 20 appear to relate to the organization of criminal activity, and the jury decided that they were not proven.
Now about some interesting things.
In addition to this system, the United States has developed a special assessment table that allows you to formalize aggravating parameters, and increase the term in proportion to the severity. For Seleznev, the table takes into account, for example, the following items:
All the more surprising is the fact that these calculations exist in the report, since, according to American laws, they are not relevant to the case and they should have been removed and excluded from the jury's testimony. In my personal opinion, this is evidence of the low qualification of legal assistance provided to a citizen of the Russian Federation, because such calculations clearly incite the jury against the defendant.
In the verdict, you can notice a strange thing, in the description of groups of episodes, it says this:
That is, the punishment for episodes should be served together with other episodes, and together with other groups of episodes. If you think about it, this means that for 1 episode of Wire Froud they give 28 (!) years. This incident is a historical feature of the United States. Fraud involving the use of federal communications (mail, telecom operators) and financial (banks) institutions is a particularly serious crime in the United States.
The proposed prosecution scheme is interesting, according to which the charges against Seleznev were prepared in several states at once, and the episodes were distributed among all of them. At least two states were preparing to press charges under the aforementioned RICO Act, demanding life in prison. The interesting thing is that in any legal country, no one can be tried for the same crime twice, but in the United States, a person can be tried for the same crime several times in different states, if the charges do not completely match the episodes. That is, it is necessary to replace one episode with one for which no charges were brought — and a new trial in another state is ready. There are a lot of episodes in the Seleznev case.
On April 21, 2017, a Seattle court sentenced Roman to 30 years in prison (27 years plus the three years he had already served). In other states, the trial of Roman has not yet begun, where he may face life in prison under the RICO law.
The main points of the case are known to everyone, including from the confession of Roman himself. He has been selling dumps for a very long time, and was involved in the largest hacks of Target, Neiman Marcus, Michaels, Staples, and Home Depot store chains, where Trojans for removing dumps were installed directly on cash registers and PoS terminals. His father is Russian State Duma deputy Valery Seleznev, and Roman himself was badly injured during the terrorist attack in Marrakech in 2011, after which his wife ran away with all the money. The guy was detained in the Maldives, and by the time he was detained, Interpol promptly put him on the wanted list (with a "red notice"). Carder's father then demanded that Russia impose sanctions against the Maldives.
Behind all the tinsel among the hundreds of court documents in the case of Roman Seleznev, there are some details that may seem interesting for a general understanding of the picture of how carding and the entire cybercrime world live in Russia.
Unfortunately, get the full set of documents from the PACER electronic database in the Roman Seleznev case (case 2: 11-cr-00070-RAJ) we haven't been able to do it yet, because it requires more than a thousand dollars at the service's prices. But my colleagues have already pulled the most basic documents from PACER, and my colleague Andrey Sporaw posted them in the public domain and commented on them. Here are some of them::
- Sentencing Memorandum, registered on 14.04.2017, document 464 in case 2: 11-cr-00070-RAJ
- Annex to the memorandum on sentencing, registered on 17.04.2017, document 467
- Memorandum on sentencing by the defense dated 14.04.2017, document 466
- Letter of confession dated 10.04.2017, document 463
- Please classify (edit) parts of the letter of confession (Defender's Motion to Seal), 03.04.2017, document 458
- Translations of prisoner Roman Seleznev's phone conversations with his father on how to delay the hearing for as long as possible in order to use the "Uncle Andrey option". The father offered to pretend to be ill or stop communicating with lawyers, 25.09.2015, document 185-1
- Witness statements on the results of the search of the Hop1 server and the 2Pac server, 17.04.2017, document 467-1
- Claims for damages from victims with amounts of damage (Victim Restitution Amounts per Victim Financial Loss Restitution Statements), 14.4.2017, document 464-1
- United States ' Notice of Filing Paper Materials with the Clerk, 14.4.2017, document 465
- Transcript of the witness ' questioning on the reliability of the amounts of damage caused to 3,715 banks (WOOD — Cross), 14.4.2017, document 466-1
- Letter to Roman Seleznev from King Mohammed VI of Morocco in 2011 expressing condolences after the terrorist attack in Marrakech, 14.4.2017, document 466-2
- Extract from the medical history of 2011 from the A. I. Burnazyan Federal Medical Biophysical Center in Moscow, 14.4.2017, document 466-3
- Certificate of hospitalization from the prison hospital dated 29.05.2015, where the patient was prescribed Elavil, 14.4.2017, document 466-4
- Discharge epicrisis from the Center for Speech Pathology and Neurorehabilitation, Moscow, 2011, 14.4.2017, document 466-5
- Examination of a gastroenterologist-hepatologist dated 20.03.2012 from MedElit Medical Center, Moscow, 14.4.2017, document 466-6
Of particular interest are some facts mentioned in the memorandum on sentencing. It turns out that the Americans established in 2009 that Roman Seleznev was hiding behind an online character under the nickname nCuX. On May 19, 2009, agents of the US Secret Service and the FBI met with their colleagues from the FSB in Moscow, where they presented "significant evidence" of the suspect's hacking activities, including carding and other crimes. The Americans gave their FSB colleagues the suspect's online nicknames and information about the real identity of Roman Seleznev, a resident of Vladivostok. But the attempt at international cooperation failed. According to the documents, "just a month later, on June 21, 2009, nCuX informed his associates on numerous underground forums that he was going out of business. Shortly after, nCuX completely disappeared from the Internet." After that, he created new online personalities Track2 and Bulba.
One might think that in this case, there is a clear fact of cooperation between the FSB and the criminal world of cybercrime, which experts have long been talking about.
It is quite possible that this is the case. The investigation documents note that information about the actions of US law enforcement agencies "was brought to Seleznev." Apparently, he had his own contacts in the FSB. The materials of the investigation mention an exchange of messages between Roman and his accomplice from 2008, where Roman says that he "received protection through contacts of law enforcement agencies in the department of combating computer crime of the FSB."

In 2010, Roman told another accomplice that the FSB knew his real name and was working with the FBI. American intelligence agencies feared that due to the impossibility of Roman's extradition from Russian territory (this is prohibited by the Constitution of the Russian Federation), this criminal could go unpunished forever, since he enjoys the patronage of law enforcement agencies and the FSB in Russia.
Therefore, a special operation in the Maldives was the only chance. Although Roman constantly checked PACER's American records, followed the investigation against him, and did not travel to countries where there was a risk of being "under the hood". He only flew where the Americans, in his opinion, could not reach him, but here he still miscalculated. The Americans agreed with the law enforcement agencies of the Maldives and issued the detention five minutes before the flight to Moscow, when Roman formally left the border of the Maldives at the airport and gave his passport to an airport employee.
Among the funds confiscated from him are Liberty Reserve coins worth about $17 million. Roman sold dumps mainly for LR. The investigation found that in total he sold dumps for LR in the amount of $17,886,971.09. The investigation failed to establish how much money Seleznev has on the Bitcoin and WebMoney wallets, which he also accepted payments for, due to the anonymity of these systems. It is likely that after his release, Roman will get access to these wallets.
Interestingly, Roman initially refused to cooperate during his incarceration, but then changed his mind and repeatedly offered his services and tried to provide valuable information. He managed to get a meeting where he revealed to the authorities the identities of many participants in carding forums from 2005 to 2014, but the Secret Service refused to cooperate, because most of this information was already known to it. In addition, Roman made some statements that were obviously false, which reduced the value of cooperation to zero.
If you haven't read the comment to the previous article from user SBKarr, then let's repeat once again where did 30 years of charges for Roman Seleznev come from:
For those who are interested in where they are 30 years old from
The gentleman is charged with 40 felony counts, 38 of which are related to hacking. In US law, episodes are grouped, after which they are either summed up or absorbed by the largest in each group. The largest group is considered as a penalty. In addition, there are crimes that are not grouped and are summed up by the end date of the crime.
In the court decision, the episodes are grouped as follows (I will try to translate them in a way that roughly corresponds to our legal terminology:
- 1-10-Wire Fraud — 336 months
- 12-19-Intentional Damage to electronic computing devices that perform important operational functions (Intentional Damage to a Protected Computer) in conjunction with
- 21-29-Illegal access to secret / protected information (Obtaining Information from a Protected Computer — - 60 months
- 30-38 — Illegal access to devices (Access Device Fraud) — 120 months
Paragraphs 11 and 20 appear to relate to the organization of criminal activity, and the jury decided that they were not proven.
Now about some interesting things.
In addition to this system, the United States has developed a special assessment table that allows you to formalize aggravating parameters, and increase the term in proportion to the severity. For Seleznev, the table takes into account, for example, the following items:
- Loss in excess of $550 million — total financial losses exceed $ 550 million
10 or more victims — more than 10 victims - Scheme committed from outside of the U.S. — the crime was committed from outside of the United States
- Organizer / leader — the defendant is the leader of a criminal organization
- Obstruction of justice — the defendant obstructed the administration of justice
All the more surprising is the fact that these calculations exist in the report, since, according to American laws, they are not relevant to the case and they should have been removed and excluded from the jury's testimony. In my personal opinion, this is evidence of the low qualification of legal assistance provided to a citizen of the Russian Federation, because such calculations clearly incite the jury against the defendant.
In the verdict, you can notice a strange thing, in the description of groups of episodes, it says this:
As to each of counts 1-10 (Wire Fraud), defendant shall serve 336 months to be run concurrently with one another, and also concurrently with all other counts except counts 39 and 40
That is, the punishment for episodes should be served together with other episodes, and together with other groups of episodes. If you think about it, this means that for 1 episode of Wire Froud they give 28 (!) years. This incident is a historical feature of the United States. Fraud involving the use of federal communications (mail, telecom operators) and financial (banks) institutions is a particularly serious crime in the United States.
The proposed prosecution scheme is interesting, according to which the charges against Seleznev were prepared in several states at once, and the episodes were distributed among all of them. At least two states were preparing to press charges under the aforementioned RICO Act, demanding life in prison. The interesting thing is that in any legal country, no one can be tried for the same crime twice, but in the United States, a person can be tried for the same crime several times in different states, if the charges do not completely match the episodes. That is, it is necessary to replace one episode with one for which no charges were brought — and a new trial in another state is ready. There are a lot of episodes in the Seleznev case.

