Mutt
Professional
- Messages
- 1,061
- Reaction score
- 655
- Points
- 113
This article was written for educational purposes only. We do not call anyone to anything, only for information purposes! The author is not responsible for your actions
Apple Watch is one of the world's most popular smartwatch brands. Their latest version is equipped with a full set of sensors and a processor, the power of which exceeds the budget (and even not very budget) models of smartphones. With the help of watches, Apple collects huge amounts of data. What happens to this data, where is it stored and how can I retrieve it? Let's try to figure it out.
Over the past few years, the popularity of a variety of trackers and smartwatches has grown significantly. In 2018, 141 million smartwatches were sold, which is almost double the result of the previous year. Among the variety of models, the Apple Watch line stands out, with sales of 22.5 million units in 2018. For several years now, the total share of all Apple Watch models is only slightly below half of the global market.
The first version of the Apple Watch was released in 2015. The next year, the Series 1 generation came to replace the first generation of watches, which was released simultaneously with the Series 2. Today, the current model is the fourth (in fact, the fifth) version of Apple Watch 4. All versions of Apple watches run a specialized operating system WatchOS , the code of which, in turn, is based on the iOS mobile system.
Extracting data from Apple Watch via adapter
A more difficult way to extract information from Apple Watch is to connect it to a computer with a specialized adapter, the correct connection of which to the watch is truly a piece of jewelry. In any case, it is imperative to fulfill two requirements:
- Connect the watch to the computer somehow. And if there are ready-made IBUS adapters for the Apple Watch S1, S2 and S3, then we did not find the necessary adapter for the watches of the latest series.
- When your watch connects to your computer, you need to create a trusted connection - just like with an iPhone. And just like with the iPhone, you will need to unlock the watch with the lock code to do this. If this is not done, then it will not work to connect the watch to the computer.
What can you get out of your watch with a direct connection? There are only three types of data available:
- Device information and list of installed applications.
- Files via the AFC (Apple File Conduit) protocol.
- Log files.
PC connection
We managed to find adapters for the first three generations of watches; there is no such adapter for Apple Watch 4. The diagnostic port on the Apple Watch is located under the strap mount; you need a thin needle or paper clip to open the cover. The adapter we use is called IBUS: IBUS for Apple Watch S1 and IBUS for Apple Watch S2 and S3.

It can be difficult to properly connect the adapter to your watch. Nevertheless, it is possible.

As with the iPhone, iTunes will ask for permission to create a trusted connection to the computer.
iTunes will display the watch information (OS version and unique watch ID only).

Now we launch Elcomsoft iOS Forensic Toolkit.
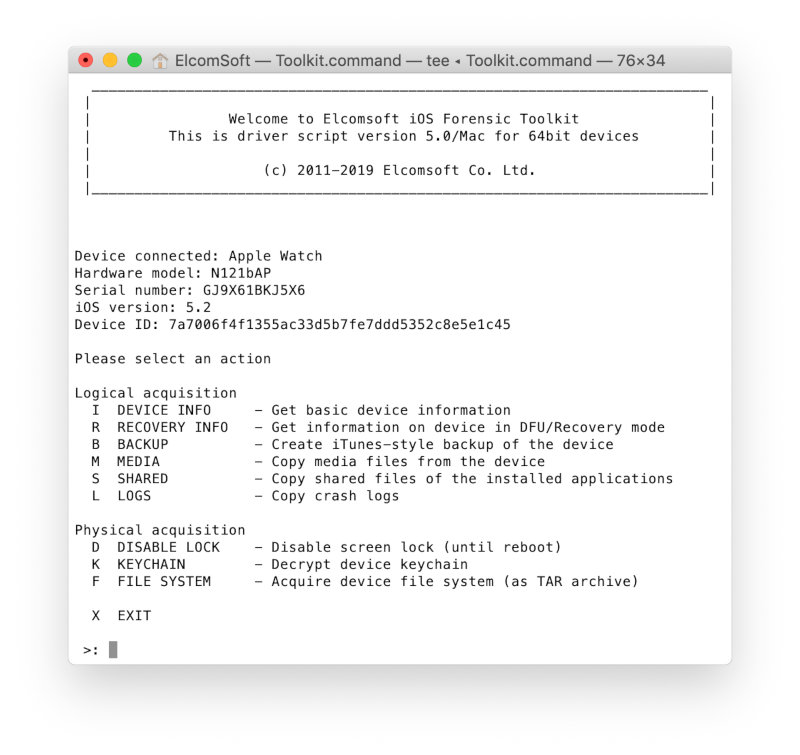
The list of applications installed on the watch is retrieved by the I(Device Info) command and saved to a file.

Three files are created on disk (usually in the same directory where the iOS Forensic Toolkit is installed):
- Ideviceinfo.plist;
- Applications.txt;
- Applictions.plist.
The file ideviceinfo.plistcontains all available information on the Apple Watch, including the exact model identifier (Hardware Model), the version of the WatchOS operating system, the serial number of the watch (Serial Number), UDID, device name (Device Name), MAC addresses of Wi-Fi and Bluetooth adapters , time zone and time at the time of data extraction.
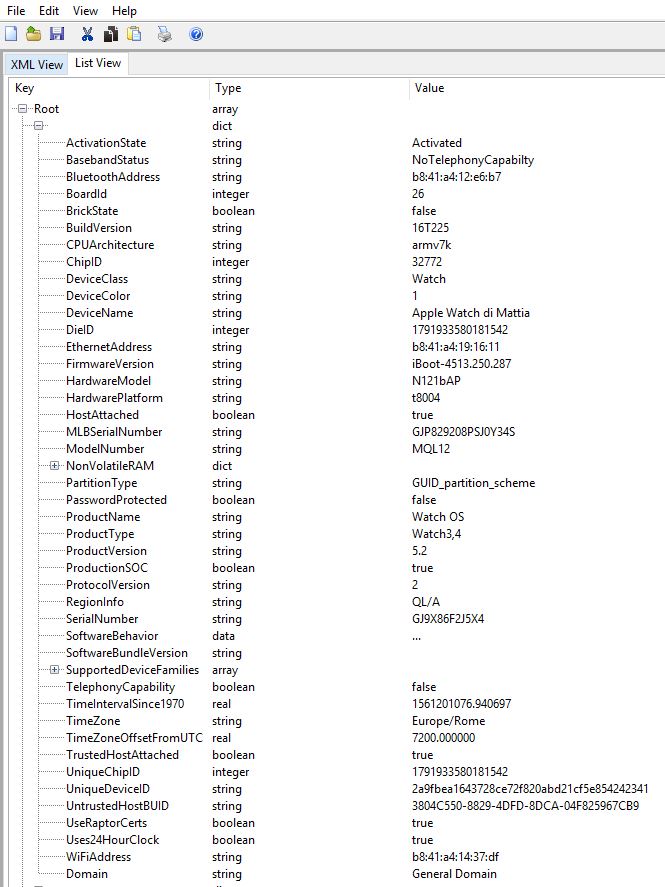
The file also contains information about the free and total volume of the drive and the size of the system partition (attributes Total Disk Capacity, Total System Capacity, Total Data Capacity, Total Data Available). Finally, the Language and Locale attributes contain information about the selected language and culture.

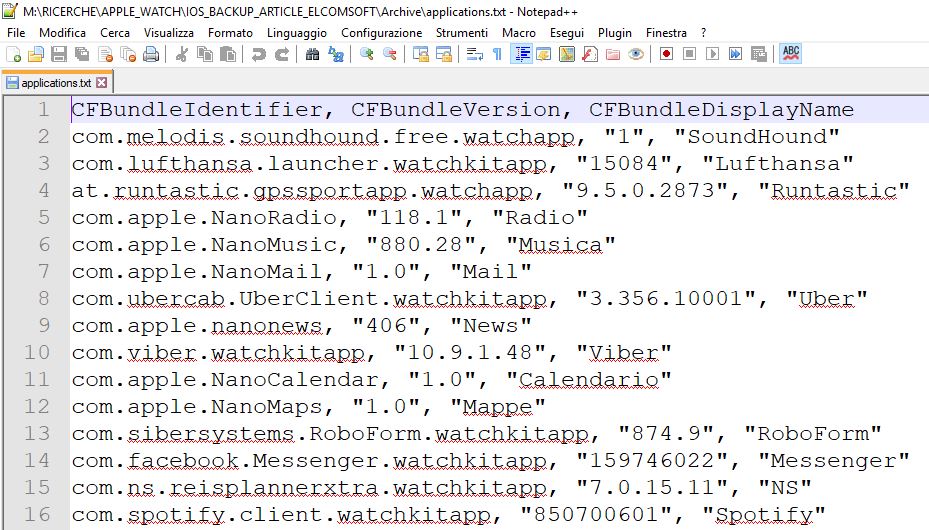
The list of applications installed on the watch is saved to a file Applications.txt. This includes data such as the Bundle Identifier (unique identifier of the application), Bundle Version and Bundle Display Name (the name of the application as it appears on the watch).
Detailed information about each installed application is available in the Applications.plist file (you remember which utility to view it with). It contains information about the exact path in the file system where the application is installed and the paths to its sandbox (Application Path and Container, respectively). Pay attention: we do not have access to the file system of the clock, so we will not get access to data from the sandbox. You can see how the information about the Uber app looks in the screenshot below.

You can copy the system log files using the L(Logs) command .
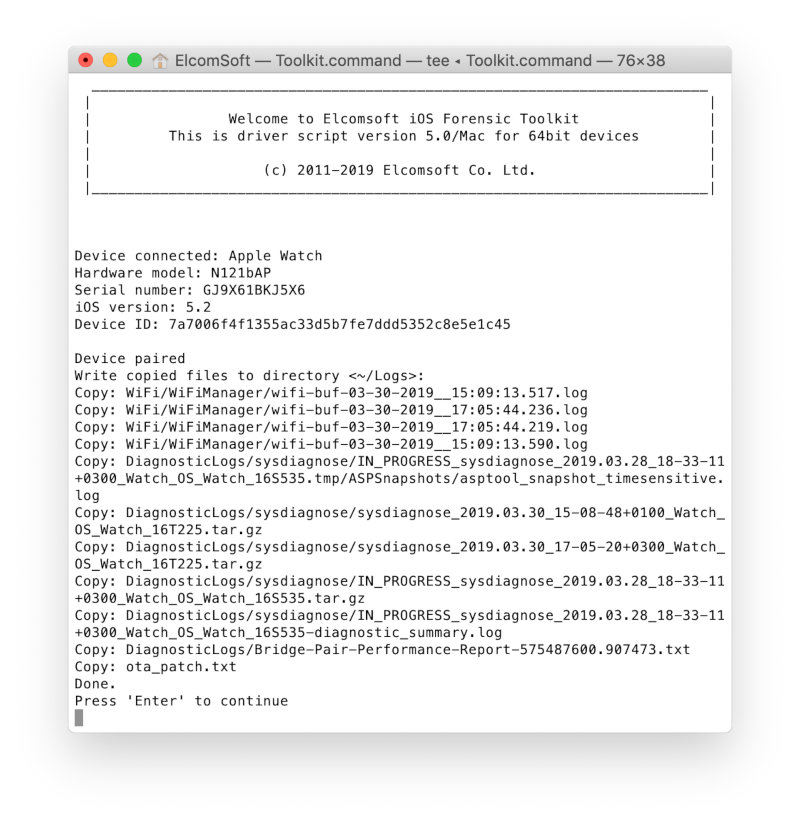
Analysis of watch log files
So, we have extracted the log files from the watch. For more information on iOS log files, see Using Apple "Bug Reporting" for forensic purposes by Mattia Epifani, Heather Mahalik and Adrian Leong, Cheeky4n6monkey. This article explains how to use sysdiagnose profiles to retrieve data from various Apple devices. Let's try the same approach with a watch.
The sysdiagnose data analysis scripts can be downloaded from GitHub. The following system logs are of most interest.
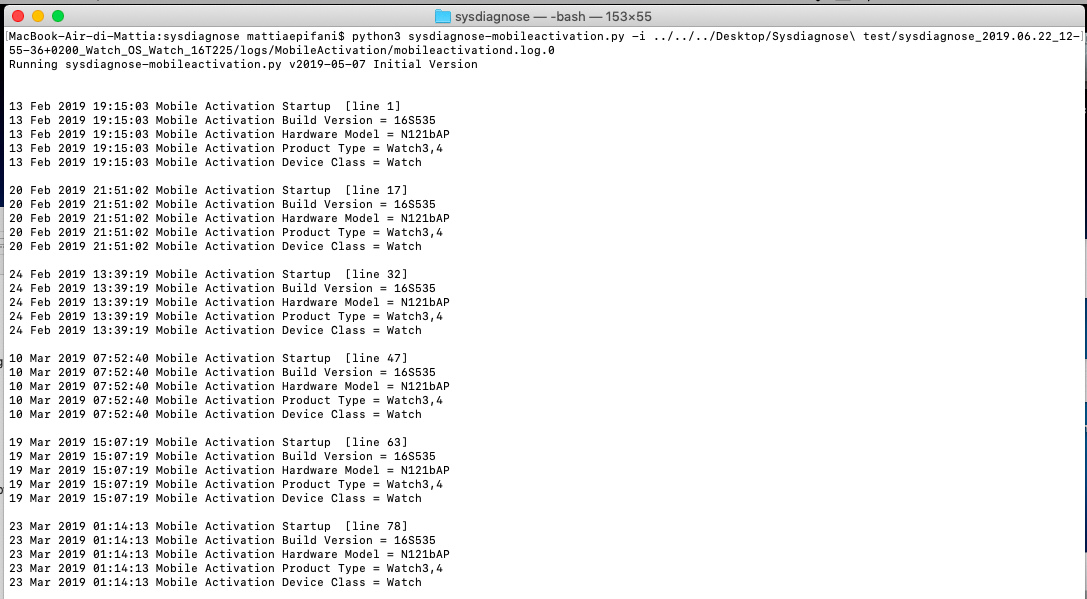
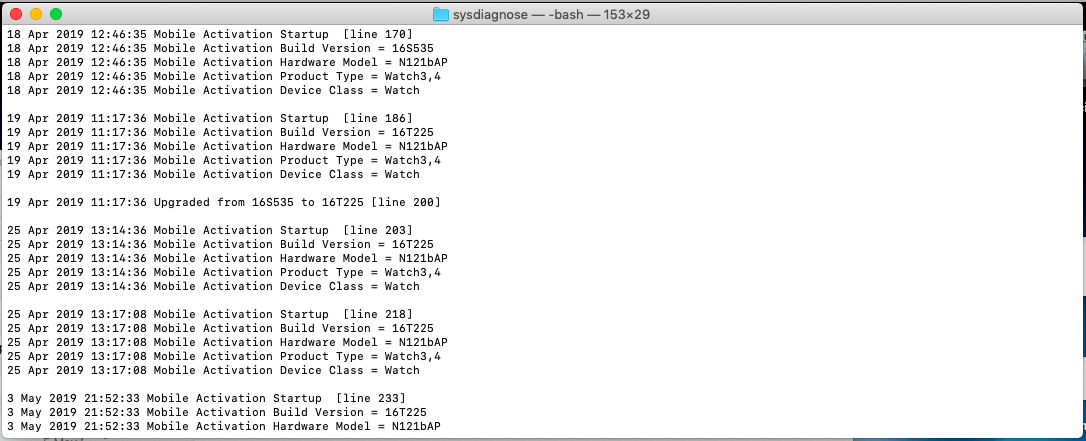
MobileActivationcontains information about OS versions and their installation time, device model and product type. It also stores detailed information about WatchOS updates. The screenshot below shows the script working with the Mobile Activation magazine.
MobileContainerManageris of interest in that it contains information about removing applications from the watch. By analyzing the log, you can understand which applications may have been used on the watch during the period of interest. Below is the parsing of the MobileContainerManager log.
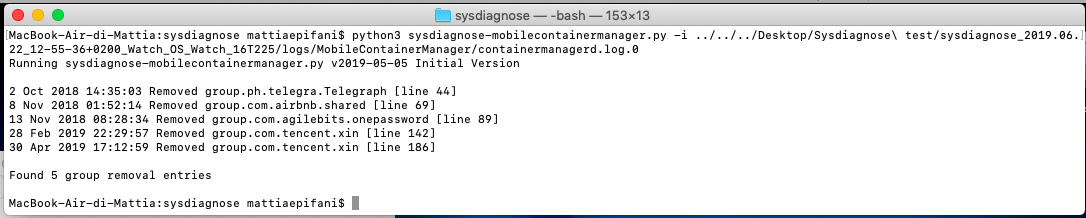
MobileInstallation is similar to the previous one, but the information here is not about uninstalling, but about installing applications on the watch.
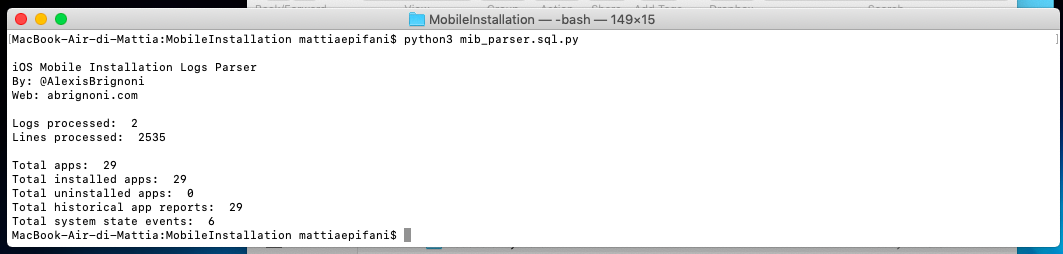
But the most interesting is, perhaps, the PowerLog magazine. This is where information about the user's interaction with the watch is stored. Was the watch on the charge? Have they been picked up? Put it on your wrist? Has the user activated the screen? It is this magazine that experts primarily try to analyze when investigating car accidents. If the driver is distracted by the watch (or turned on the phone screen, it also has a similar log) at the time of the accident, this will testify against him (in the USA there is the concept of Distracted Driving. For information: as a result of distracted driving on American roads in 2017, more than three thousand people). Because of its importance, the structure of this database is well understood. You can read, for example, Sarah Edwards' article ( PDF) or use the ready-made APOLLO toolkit...

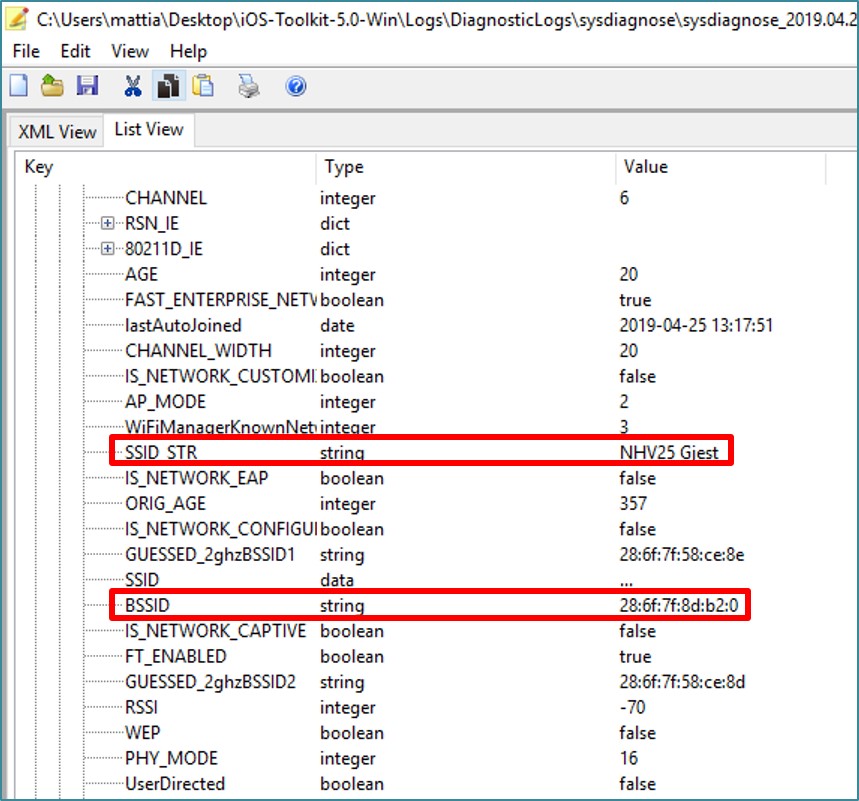
Finally, the Wi-Fi logs contain a list of networks to which the watch has connected. The easiest way is to view the contents of the file com.apple.wifi.plist, in which the records about SSID, BSSID and the date of the last connection to this network are of interest. Of particular interest is the BSSID parameter, which can be used to determine the exact location (radius 15-25 meters) at the time of connection to the network. To determine the coordinates of a Wi-Fi access point by its BSSID, you can use one of the reverse lookup services, for example Wigle.

Access to media files
It is worth talking about access to media files in more detail. You can extract media files using the M(Media) command . Interest is not so much the photos themselves, but the database Photos.sqlite.
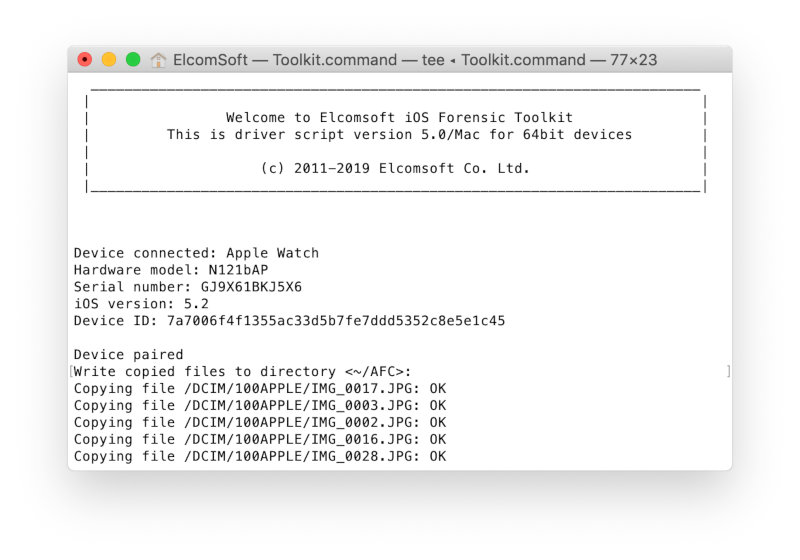
Almost the only way to access media files from your Apple Watch requires using a utility that uses the Apple File Conduit (AFC) protocol. In this case, the watch must be connected to the computer, and a trusted relationship (pairing) must be established between the computer and the watch.
As shown in the previous section, media files can be easily extracted using the M(Media Files) command of the iOS Forensic Toolkit. It would seem that everything is simple: media files are photographs and, possibly, videos; what interesting can be found in the files from the clock? It turns out that there are quite a lot of interesting things - and the main interest is not at all the photographs themselves.
Below is the folder structure created after extracting media files using the AFC protocol.
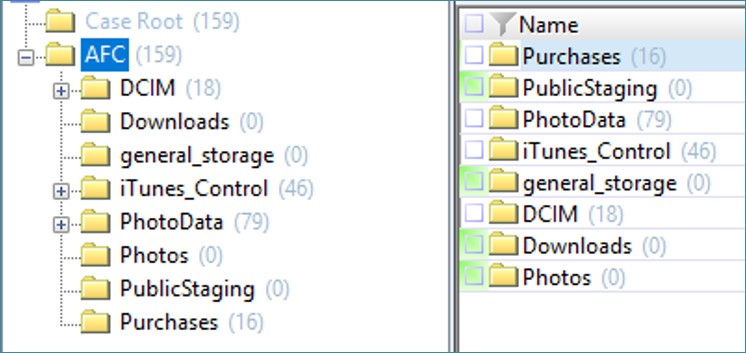
The actual images (greatly reduced in comparison with the originals) are placed in the DCIM folder; here no surprises.
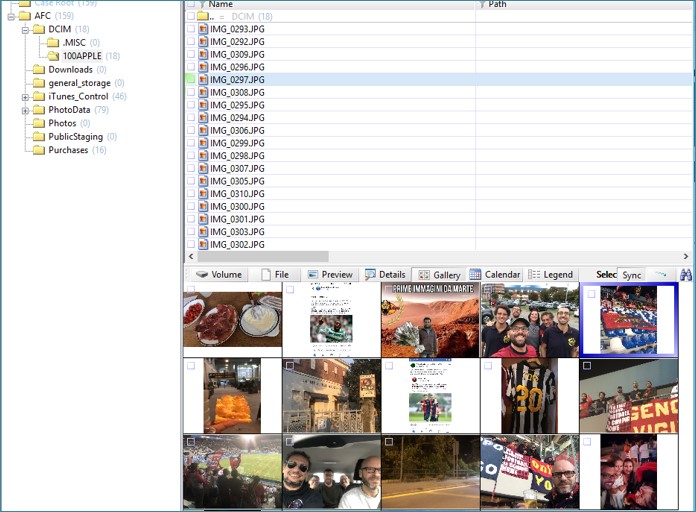
Despite the fact that the images are significantly reduced (it would be strange to transfer full-size photos to the watch), the system stores EXIF meta tags in them, which allows you to determine such parameters as the exact time of shooting and the device used for the photo.

The folder iTunes_Control\iTunescontains a very interesting database MediaLibrary.sqlitedb. This also includes the corresponding SHM (Shared Memory) and WAL (Write Ahead Log) files. The database itself, as the name implies, is stored in SQLite format (like all other databases on the clock, by the way). This database contains information such as the user's iCloud ID, as well as a list of purchases in the iTunes store (purchases of music, movies and e-books). Interestingly, this file stores information about purchases made from all user's devices registered with this account.
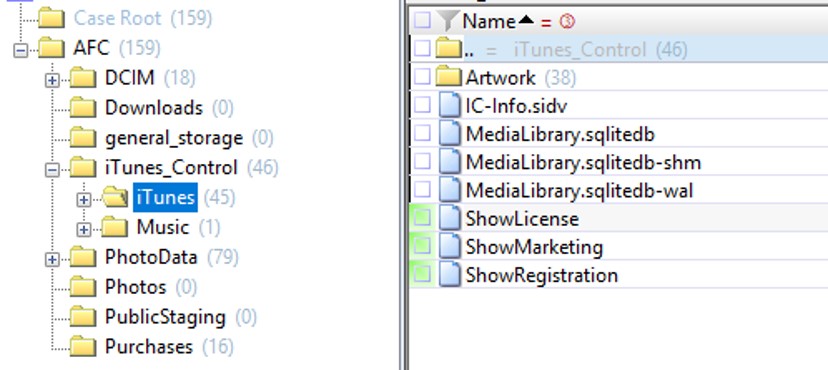
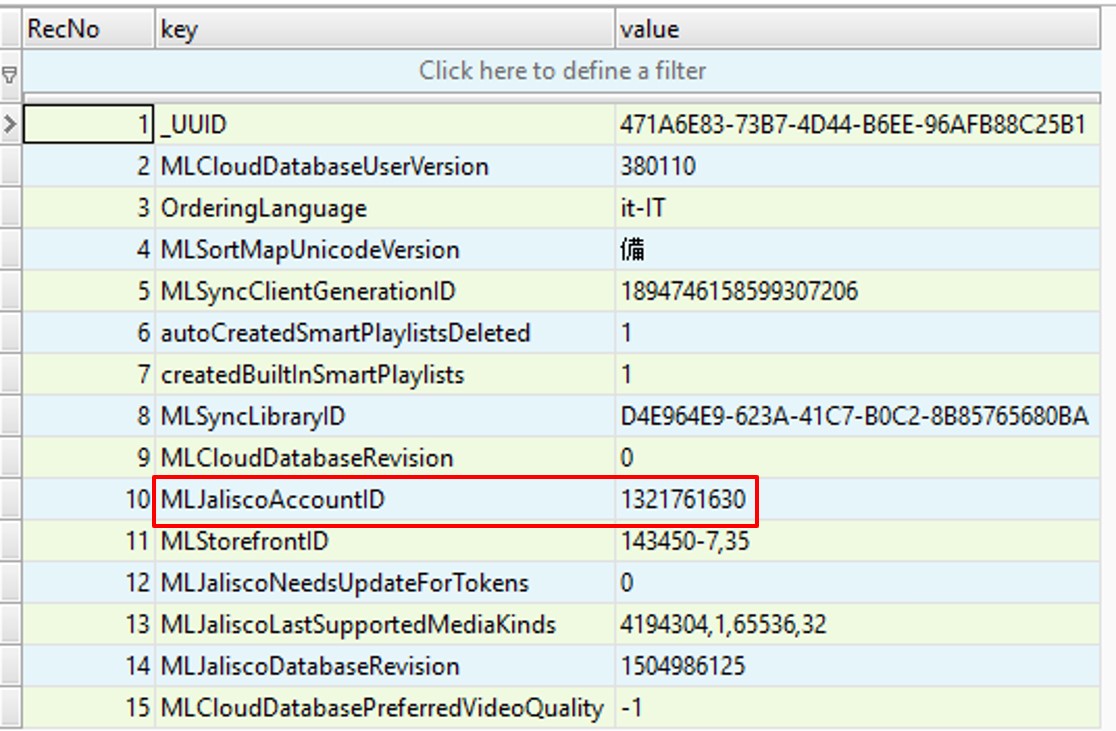
There are 36 tables in the database. The user's iCloud ID is stored in the _MLDatabaseProperties table.
To extract some meaningful information from the database, let's form an SQL query:
Code:
select
ext.title AS "Title",
ext.media_kind AS "Media Type",
itep.format AS "File format",
ext.location AS "File",
ext.total_time_ms AS "Total time (ms)",
ext.file_size AS "File size",
ext.year AS "Year",
alb.album AS "Album Name",
alba.album_artist AS "Artist",
com.composer AS "Composer",
gen.genre AS "Genre",
art.artwork_token AS "Artwork",
itev.extended_content_rating AS "Content rating",
itev.movie_info AS "Movie information",
ext.description_long AS "Description",
ite.track_number AS "Track number",
sto.account_id AS "Account ID",
strftime ('% d /% m /% Y% H:% M:% S', datetime (sto.date_purchased + 978397200, 'unixepoch')) date_purchased,
sto.store_item_id AS "Item ID",
sto.purchase_history_id AS "Purchase History ID",
ext.copyright AS "Copyright"
from item_extra ext
join item_store sto using (item_pid)
join item ite using (item_pid)
join item_stats ites using (item_pid)
join item_playback itep using (item_pid)
join item_video itev using (item_pid)
left join album alb on sto.item_pid = alb.representative_item_pid
left join album_artist alba on sto.item_pid = alba.representative_item_pid
left join composer com on sto.item_pid = com.representative_item_pid
left join genre gen on sto.item_pid = gen.representative_item_pid
left join item_artist itea on sto.item_pid = itea.representative_item_pid
left join artwork_token art on sto.item_pid = art.entity_pidThis query will retrieve detailed information about the user's purchases, including the product name (for example, the title of a movie, music album, or e-book), file size, length of time played or watched, date of purchase, and purchase history ID. If the purchased file is stored on the watch itself, the file name will also be here.
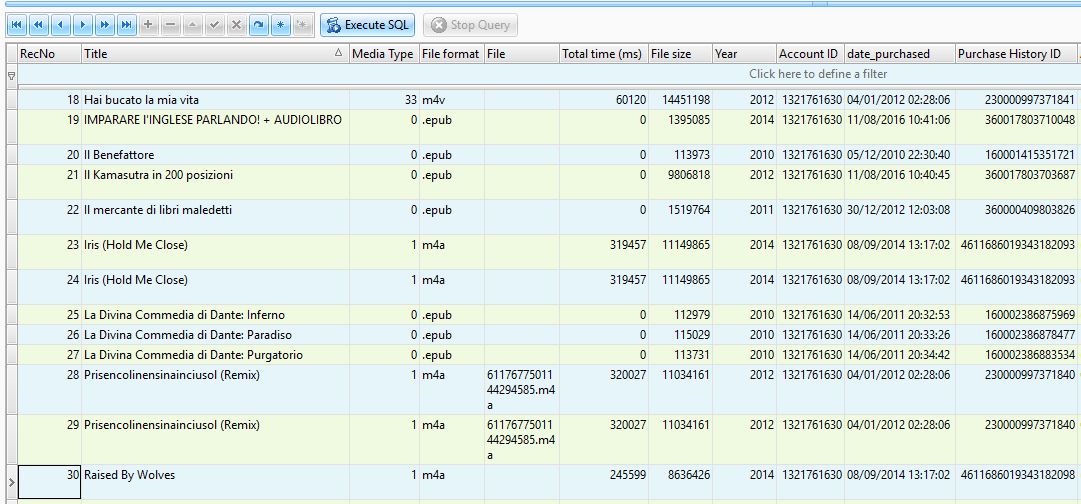
Purchased files (in the example below, this is music) can be found in the folder Purchases:
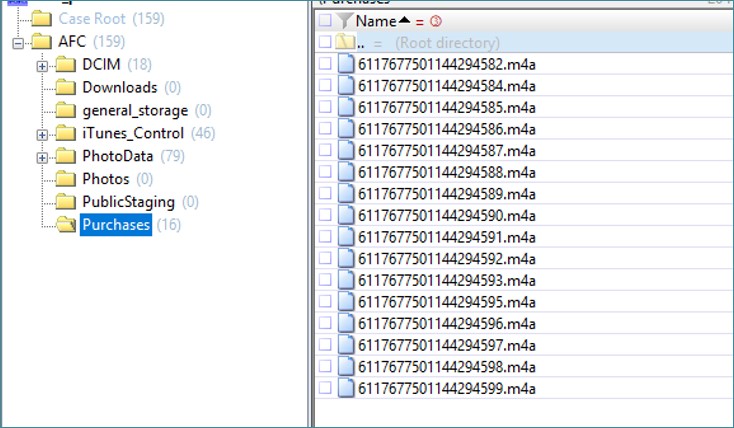
Of interest is the folder PhotoDatathat stores the metadata of the synced photos. The most interesting are the database Photos.sqliteand folder Thumbnails.

The database Photos.sqlitecontains information about the photographs that are stored on the watch. A detailed description of the base structure is available here. Ready-made SQL queries can be downloaded here.
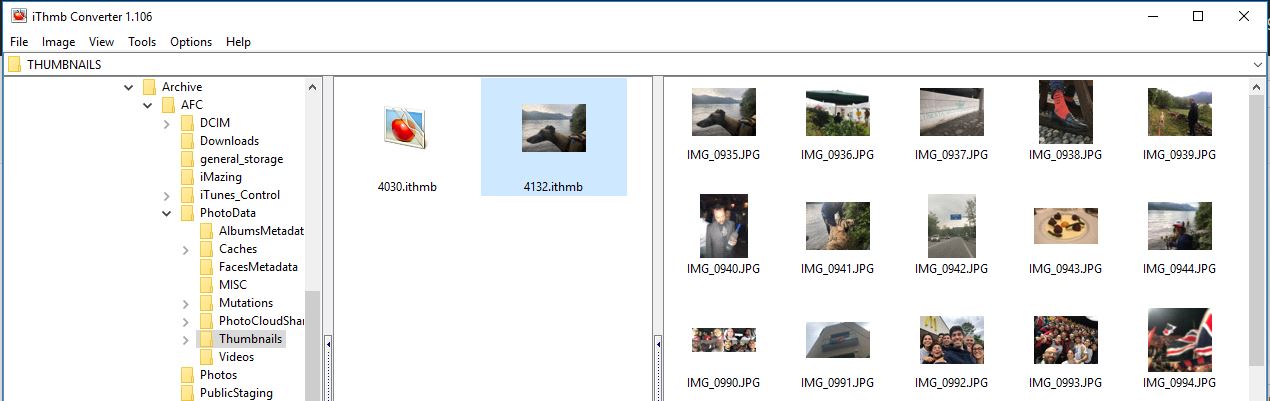
Finally, the Thumbnails folder contains thumbnails of images on the Apple Watch. The ITHMB format can be converted to the usual JPEG using the iThmb Converter utility.
Through the adapter, we received even less information than when analyzing the backup copy of the watch. Nevertheless, the value of this data is incomparably higher than the data from the backup: to access all this information, we do not need an iPhone associated with the watch - the watch itself is quite enough. Many data are unique; especially valuable are watch logs in general and PowerLog logs in particular, as well as coupons from the Wallet application.
xakep.ru
