Carding Forum
Professional
The company explained for which errors you can now get $151,515.
Google announced an increase in payments for found vulnerabilities in its systems and applications. Since the company's systems have become more secure, and now it takes much longer to detect errors, Google decided to increase some payments by 5 times.
As part of the Vulnerability Reward Program (VRP), you can now receive up to $151,515 for one detected security error. The amount includes $101,010 for RCE vulnerabilities in the company's most sensitive systems, multiplied by a factor of 1.5 for exceptional report quality. All detected vulnerabilities will be considered in accordance with the new payment rules.
In addition to increasing the amount of rewards, Google has expanded the ability to receive payments, including the ability to receive money through the Bugcrowd platform. In the updated Google VRP Rules section, you can find detailed information about the new reward amounts and payout structure.
Examples of new payouts:
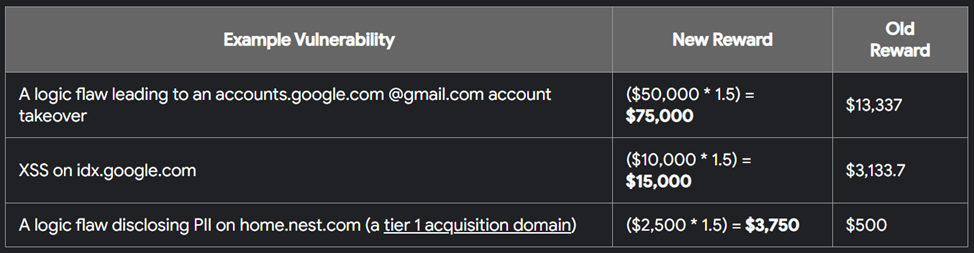
Example of calculating increased payments
Last week, Google launched a new rewards program, kvmCTF, which aims to improve the security of the Kernel-based Virtual Machine (KVM) hypervisor. A $250,000 reward is offered for fully executing the VM exploit in the KVM hypervisor.
Since launching the VRP program in 2010, Google has paid out more than $50 million to security researchers who reported more than 15,000 vulnerabilities. Last year, Google paid out $10 million, with the largest reward being $113,337.
The highest award in VRP history of $605,000 was paid to researcher gzobqq in 2022 for a series of 5 vulnerabilities in the Android exploit chain. The same researcher reported another critical exploit chain for Android in 2021, receiving a payout of $157,000.
Source
Google announced an increase in payments for found vulnerabilities in its systems and applications. Since the company's systems have become more secure, and now it takes much longer to detect errors, Google decided to increase some payments by 5 times.
As part of the Vulnerability Reward Program (VRP), you can now receive up to $151,515 for one detected security error. The amount includes $101,010 for RCE vulnerabilities in the company's most sensitive systems, multiplied by a factor of 1.5 for exceptional report quality. All detected vulnerabilities will be considered in accordance with the new payment rules.
In addition to increasing the amount of rewards, Google has expanded the ability to receive payments, including the ability to receive money through the Bugcrowd platform. In the updated Google VRP Rules section, you can find detailed information about the new reward amounts and payout structure.
Examples of new payouts:
- Logic vulnerability that leads to account hijacking @gmail.com: $75,000 (previously $13,337);
- XSS vulnerability on idx.google.com: $15,000 (previously $3,133. 7);
- Logic error that reveals personal information on home.nest.com: $3,750 (previously $500).

Example of calculating increased payments
Last week, Google launched a new rewards program, kvmCTF, which aims to improve the security of the Kernel-based Virtual Machine (KVM) hypervisor. A $250,000 reward is offered for fully executing the VM exploit in the KVM hypervisor.
Since launching the VRP program in 2010, Google has paid out more than $50 million to security researchers who reported more than 15,000 vulnerabilities. Last year, Google paid out $10 million, with the largest reward being $113,337.
The highest award in VRP history of $605,000 was paid to researcher gzobqq in 2022 for a series of 5 vulnerabilities in the Android exploit chain. The same researcher reported another critical exploit chain for Android in 2021, receiving a payout of $157,000.
Source







