A group with strong connections in cyberspace captures a large share in the hacker world.
Symantec conducted an analysis of the recently identified RansomHub ransomware and found out that the program turned out to be an updated and renamed version of Knight, which, in turn, is an evolution of another ransomware — Cyclops.
Knight (also known as Cyclops 2.0) first appeared in May 2023 and used double extortion tactics, stealing and encrypting victims ' data for financial gain. The virus works on a variety of platforms, including Windows, Linux, macOS, ESXi, and Android.
Knight was heavily advertised and sold on the RAMP forum. Attacks involving it often used phishing to distribute malicious attachments. Knight's operation as a RaaS model was discontinued at the end of February 2024, when the Knight source code was put up for sale. This gave reason to believe that the virus could have passed into the hands of a new owner, who decided to update and restart it under the RansomHub brand.
The RansomHub virus, whose first victim was recorded in the same month, is already linked to a series of recent attacks, including Change Healthcare, Christie's and Frontier Communications. It is noteworthy that the new version of the virus does not attack objects in the CIS countries, Cuba, North Korea and China.
Symantec noted that both versions of the virus are written in the Go language, and most of their variants are hidden using Gobfuscate. The correspondence in the code between the two families is significant, which makes it difficult to distinguish them. Both viruses have identical help menus, but RansomHub has added a new sleep option that allows you to stay in standby mode before executing commands. Similar commands were observed in other viruses – Chaos/Yashma and Trigona.
Similarities between Knight and RansomHub also include string hiding techniques, ransom notes, and the ability to reboot the system in secure mode before starting encryption. The main difference is the set of commands executed via cmd.exe, although the sequence of their invocation remains unchanged.
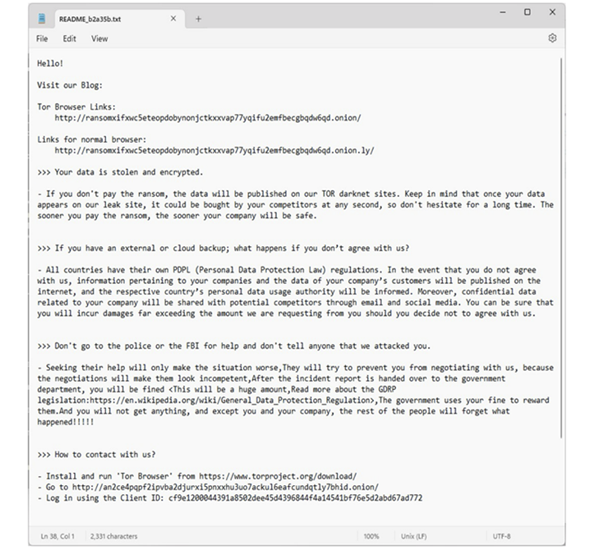
RansomHub Ransom Note
RansomHub attacks exploit ZeroLogon vulnerabilities to gain initial access and install remote management tools (Atera and Splashtop) before deploying the ransomware. According to Malwarebytes, in April 2024, this RansomHub was linked to 26 attacks.
Moreover, RansomHub is trying to attract members of other groups, including LockBit and BlackCat. It is reported that one of the former partners of Noberus, known as Notchy, is already working with RansomHub. In addition, tools previously linked to another Noberus partner, Scattered Spider, were used in the recent RansomHub attack.
The rapid development of RansomHub indicates that the group may consist of experienced hackers with strong connections in cyberspace. The development of the group is taking place against the background of a significant increase in the activity of ransomware. According to the Mandiant report, the number of publications on data leakage sites increased by 75% compared to the previous year.
Symantec conducted an analysis of the recently identified RansomHub ransomware and found out that the program turned out to be an updated and renamed version of Knight, which, in turn, is an evolution of another ransomware — Cyclops.
Knight (also known as Cyclops 2.0) first appeared in May 2023 and used double extortion tactics, stealing and encrypting victims ' data for financial gain. The virus works on a variety of platforms, including Windows, Linux, macOS, ESXi, and Android.
Knight was heavily advertised and sold on the RAMP forum. Attacks involving it often used phishing to distribute malicious attachments. Knight's operation as a RaaS model was discontinued at the end of February 2024, when the Knight source code was put up for sale. This gave reason to believe that the virus could have passed into the hands of a new owner, who decided to update and restart it under the RansomHub brand.
The RansomHub virus, whose first victim was recorded in the same month, is already linked to a series of recent attacks, including Change Healthcare, Christie's and Frontier Communications. It is noteworthy that the new version of the virus does not attack objects in the CIS countries, Cuba, North Korea and China.
Symantec noted that both versions of the virus are written in the Go language, and most of their variants are hidden using Gobfuscate. The correspondence in the code between the two families is significant, which makes it difficult to distinguish them. Both viruses have identical help menus, but RansomHub has added a new sleep option that allows you to stay in standby mode before executing commands. Similar commands were observed in other viruses – Chaos/Yashma and Trigona.
Similarities between Knight and RansomHub also include string hiding techniques, ransom notes, and the ability to reboot the system in secure mode before starting encryption. The main difference is the set of commands executed via cmd.exe, although the sequence of their invocation remains unchanged.

RansomHub Ransom Note
RansomHub attacks exploit ZeroLogon vulnerabilities to gain initial access and install remote management tools (Atera and Splashtop) before deploying the ransomware. According to Malwarebytes, in April 2024, this RansomHub was linked to 26 attacks.
Moreover, RansomHub is trying to attract members of other groups, including LockBit and BlackCat. It is reported that one of the former partners of Noberus, known as Notchy, is already working with RansomHub. In addition, tools previously linked to another Noberus partner, Scattered Spider, were used in the recent RansomHub attack.
The rapid development of RansomHub indicates that the group may consist of experienced hackers with strong connections in cyberspace. The development of the group is taking place against the background of a significant increase in the activity of ransomware. According to the Mandiant report, the number of publications on data leakage sites increased by 75% compared to the previous year.
