BadB
Professional
- Messages
- 2,494
- Reaction score
- 2,549
- Points
- 113

The stories of how antivirus companies track down virus writers are always of great interest to a wide variety of audiences. Even in spite of the fact that in most cases such disclosures occur because the virusmaker has fundamentally screwed up somewhere. So it happened this time too, and the author of the Trojan did not exactly set himself up, but burned his clients, to the delight of information security specialists. Actually, the case that will be discussed clearly illustrates how investigations of such incidents are conducted and what information can be obtained by paying attention to seemingly insignificant details.
It all started with the fact that our whirlab received several samples of the Trojan-stealer, differing from each other in a number of technical details, but clearly created by the same author. Troy had a standard set of functions for such software: searching and collecting saved passwords and cookies from browsers, copying text files, pictures and documents according to the list, stealing passwords from FTP clients, as well as accounts from Telegram and the Steam client. Everything that was acquired by back-breaking labor was packed by the stealer into the archive and uploaded to the cloud storage: in one of the versions - on Yandex.Disk, in later modifications - on pCloud.
One of the earliest versions of the Trojan was distributed through the video hosting YouTube - following links in the comments left from several fake accounts. At the same time, the videos were devoted to the use of cheats and trainers in popular games, and it was allegedly possible to download these applications from the links. That is, the campaign, most likely, was designed for cheating players, and one of the goals was supposedly to hijack Steam accounts. Links to malicious software were also actively promoted on Twitter.They say healthy laughter prolongs life. If this is actually the case, then by analyzing the received samples of stealers, virus analysts clearly won a couple of additional years.
Another modification of the Trojan was multicomponent: in addition to the main spyware module, it included a scanner written in Go that determined the path to the browsers installed on the system, and a separate utility that packed stolen files into an archive and uploaded them to the cloud. The troja dropper was done on AutoIt, which in itself gave the researchers a separate, incomparable fan. To spread this Trojan, the villains came up with a very original method: they contacted the owners of popular Telegram channels, who were offered to advertise the program to connect to Telegram from several accounts at the same time. The application could be tested - for this, the potential victim was sent a link to the executable file in which the Trojan was hiding.
As for the stealers themselves, without exception, all the samples we examined were written in Python and converted into an executable file using py2exe. At the same time, the Trojan code turned out to be crooked, like a fruit knife, and just as dull. Take, for example, a Python function os.listdir()that returns a list of strings, each of which is a directory name. Usually, the obtained values of this function are parsed in a loop. However, the author of the Trojan for some reason formed a string with spaces-delimiters from the list and searched for the required occurrences in it using a given pattern using a regular expression:
steam = os.listdir (steampath)
They say healthy laughter prolongs life. If this is actually the case, then, analyzing the received samples of stealers, virus analysts clearly won a couple of additional years, because it is simply impossible to look at such a wonderful code without laughing:
if score is 0:
Apparently, the virus writer has not yet mastered the most complex syntactic construction, if score != 0: exit(1) or instead of hands, legs are growing out of his shoulders. The second, however, was later fully confirmed.
When a script is compiled, the Python interpreter stores the name of the original script in bytecode. This name, which we got from the executable, turned out to be quite characteristic: enotproject. And in the dropper written in AutoIt, even the path to the folder with the project files is preserved: \ Users \ User \ Desktop \ Racoon Stealer \ build \. A short googling on the keywords "Raccoon" and "Racoon Stealer" brought us to the Lolzteam page, where a user under the nickname "Racoon Pogromist" sells those Trojans to everyone, and also conducts master classes on writing stealers in Python.
Our "Raccoon" turned out to be a difficult animal: among other things, he is also a video blogger, the author of a channel about the development of malware, and the owner of an account on GitHub, where he uploads his own Trojans in the form of source codes.
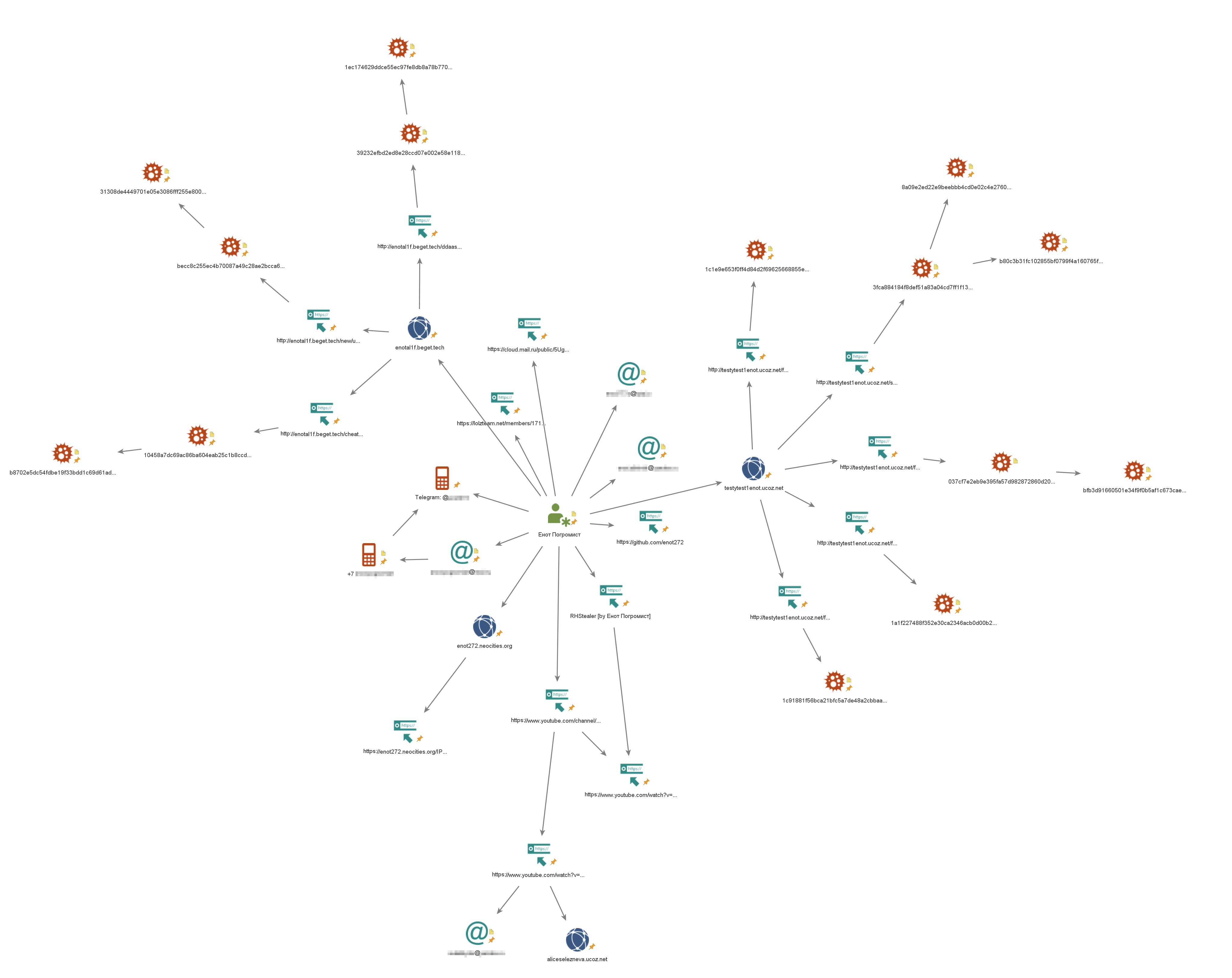
Since "Raccoon" has left a lot on the Web, thanks to his videos and other information posted to the public, analysts very quickly established several technical domains from which he distributed his malicious software, and three personal e-mail addresses he used. The mobile phone number of "Raccoon Pogromist" was also found on the Internet, and a Telegram account was tied to it, which he uses for feedback. The collected information about stealer samples, videos, domains and mailbox addresses formed just such a diagram of connections between the virus writer and the technical means involved.
But the funniest thing was in the Trojan code. Clients to whom "Raccoon" sold its stealers were offered to register an account in the pCloud cloud storage, where the Trojan independently uploaded files packed into an archive from an infected computer. At the same time, the login and password from each account of its clients "Raccoon Pogromist" prudently sewn into the body of the stealers themselves practically in an open form, so that they can be extracted from there without any difficulty.
Well, the Trojan buyers themselves, for the most part, were distinguished by the highest intelligence, remarkable intelligence and devilish intelligence: many of them launched the stealer on their personal machines (probably for test purposes), due to which their personal files were uploaded to the cloud storage, to which, through the efforts of “Raccoon” can be accessed by anyone. Not to mention the fact that some especially gifted humanoids used their personal email addresses, tied to real pages on social networks, as a login to pCloud. Yes, and, of course, they also have the same password everywhere.
Conclusion
It's amazing how much information people voluntarily leave about themselves on the web.Since "Raccoon Pogromist" has kindly leaked private information about its clients to us, it would be foolish not to ask what they are doing in their free time from buying Trojans. It turned out that many of them also use other stealers, which are sold in abundance on the respective forums. From the information we found, threads were drawn to various network resources: one after another, personal pages in social networks, YouTube channels, postal addresses, mobile phone numbers, e-wallet identifiers in payment systems were found ... Some of Raccoon's clients own websites - thanks to the service Whois managed to find out the names of the administrators of the domains they use. One "formidable hacker", among other things, had an electronic diary, which is now used by all schoolchildren.
Thus, all the buyers of the Raccoon Steelers were calculated by us in the shortest possible time, de-anonymized, a detailed dossier was compiled for each and put into a neat little daddy. Raccoons are sometimes extremely useful in the fight against cybercrime.
In general, friends, in order to find the author of viruses, sometimes simple attention to detail is enough - thanks to this, sometimes it is possible to conduct a large and successful investigation.

