Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
Three unchanging stages of the attack have become the hallmark of insidious ransomware.
Trend Micro recently discovered a new wave of activity from the ransomware group RA World, also known as the RA Group. The group began its malicious activity in April 2023 and during its existence managed to attack many organizations, mainly in the health and financial sectors, located in the United States, Germany, India and Taiwan.
Researchers have revealed that the latest wave of RA World attacks targeted several healthcare organizations in Latin America. Attacks were carried out in several stages to increase the overall chances of successful execution of the operation.
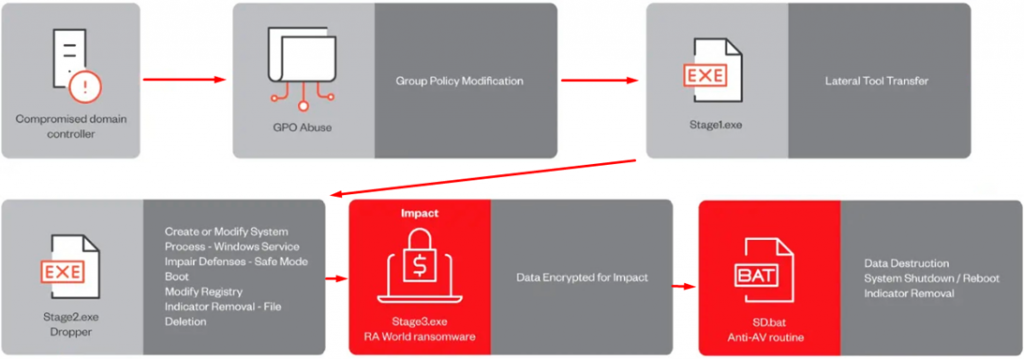
RA World multi-stage attack scheme
In addition, the malware can reboot the system in a special safe mode, which allows it to avoid detection by antivirus programs. It also erases traces of its presence after performing an attack, making it harder for researchers to analyze.
To minimize the risk of becoming one of the victims of RA World attacks, it is recommended to apply the best security practices: restriction of administrative rights, timely updating of the software used, regular data backup, caution when interacting with email and websites, as well as training the company's employees in the basics of cybersecurity.
Applying a comprehensive approach to security allows you to significantly strengthen potential access points to the system, qualitatively improving the protection of the enterprise.
Trend Micro recently discovered a new wave of activity from the ransomware group RA World, also known as the RA Group. The group began its malicious activity in April 2023 and during its existence managed to attack many organizations, mainly in the health and financial sectors, located in the United States, Germany, India and Taiwan.
Researchers have revealed that the latest wave of RA World attacks targeted several healthcare organizations in Latin America. Attacks were carried out in several stages to increase the overall chances of successful execution of the operation.
- Initial access. The attack begins with hackers breaking into a computer system through domain controllers. This is where Group Policy editing (GPO) plays a key role, which allows attackers to set their own rules on the victim's system.
- Stage 1 (Stage1.exe). After entering the system, the virus uses the file "Stage1.exe" to assess and prepare the network for further attack, which includes checking domain controllers and preparing for copying the next stage of the virus.
- Stage 2 (Stage2.exe). At this point, the virus copies itself to other machines on the network and begins preparing for file encryption. "Stage2.exe" responsible for spreading malicious code inside the target network, preparing the ground for launching the main attack.
- Stage 3 (Stage3.exe). This is the final stage at which the virus is activated, encrypting files on infected computers and demanding a ransom for their recovery. It uses sophisticated encryption techniques, making files inaccessible to users and systems.

RA World multi-stage attack scheme
In addition, the malware can reboot the system in a special safe mode, which allows it to avoid detection by antivirus programs. It also erases traces of its presence after performing an attack, making it harder for researchers to analyze.
To minimize the risk of becoming one of the victims of RA World attacks, it is recommended to apply the best security practices: restriction of administrative rights, timely updating of the software used, regular data backup, caution when interacting with email and websites, as well as training the company's employees in the basics of cybersecurity.
Applying a comprehensive approach to security allows you to significantly strengthen potential access points to the system, qualitatively improving the protection of the enterprise.

