Brother
Professional
- Messages
- 2,590
- Reaction score
- 533
- Points
- 113

How to block Cryptomining scripts in your web browser
As the value of cryptocurrencies such as Bitcoin and Monero has skyrocketed, a more sinister trend has emerged. Cybercriminals saw an opportunity to use the computing power of unsecured computers to mine cryptocurrency.These calculations require a lot of CPU and power resources, so hackers use browser mining scripts to illegally use other people's computers (called cryptojacking) so that they can mine cryptocurrencies for free.
What is cryptojacking
Like ransomware, cryptominers are by no means a new phenomenon. After all, since about 2011, it has been possible to use computer resources to mine bitcoins without the help of specialized or powerful equipment. However, cybercriminals only started developing malware after the cryptocurrency boom in mid-2017.Cybercriminals realized that if they infect someone else's computer with malware, they could force the infected computer to do mining work, but the attackers would make a profit. After all, multiplying the profit by 1,000 or 1,000,000 infected computers, it is very easy to understand why malicious cryptominers got such a rise.
Moreover, the attackers decided that they could dramatically increase their profits by combining several types of malware.
In fact, a user who follows a phishing link or opens a malicious attachment gets two infections at the same time: cryptomining software and ransomware. Naturally, the attacker chooses which software to activate, because they cannot work at the same time. The choice is made based on factors such as the hardware and software configuration of the computer and which attack is more profitable.
How illegal cryptomining works
Cybercriminals use a variety of methods to infect computers, from compromising individual users' PCs and mobile devices, to infiltrating popular websites and distributing malware to everyone who visits them.In addition, phishing remains an extremely popular infection method. In some cases, worm components are used, which allows malware to attack one machine after another over the network.
The EternalBlue exploit, which was used to spread the WannaCry ransomware in the global epidemic in 2017, is still used to spread malicious cryptomining. But unlike ransomware, most cryptomining victims have no idea what is being stolen from them, other than a vague sense that their system is not working as efficiently as it used to be.
Fake software updates are another popular infiltration method, such as downloading malware that masquerades as a legitimate Adobe Flash Player update. Another common method is to inject a malicious mining script on a legitimate website or in an online ad that appears on many websites. When a victim visits a website or their browser downloads online ads, a cryptomining process begins, stealing resources and profits without the user's knowledge.
Cryptomining malware developers have learned from their early mistakes. Today, it is much less common for malware to consume 100% of the victim's processor power, resulting in a noticeable slowdown that is likely to prompt the user to notice and take corrective action. New releases of crypto-mining malware are taking more reasonable measures to conceal their presence: the victim's CPU utilization up to about 20 percent, looking for user downtime to perform the most resource-intensive computations, etc. Thus, these cryptominers can steal resources from the victim without being detected very long time.
Worse, you don't need to be a highly skilled software engineer to get involved in illegal mining. As with other malware suites, cryptojacking as a service can be purchased for as little as half a US dollar. The high level of privacy and anonymity inherent in some cryptocurrencies, such as Monero and Zcash, also makes it much more difficult to track and catch intruders.
Notable cryptojackers
Smominru
Smominru is arguably the most notorious cryptocurrency botnet of over 520,000 machines that have earned over $ 3 million in Monero by January 2018, fueled by a clever, constantly regenerating botnet design. Smominru was based on EternalBlue, a stolen NSA exploit that was also used in the global WannaCry ransomware epidemic in 2017.BadShell
Smart cryptominers like BadShell hide in legitimate processes like Windows PowerShell through which they execute hidden malicious mining scripts. Few traditional antivirus programs can detect a threat because by default they trust Windows-signed executables such as PowerShell.Coinhive
Originally intended and still used as a legitimate website monetization tool, Coinhive mining code is currently the world's largest crypto hack threat.MassMiner
MassMiner is an interesting example because it uses many exploits for different vulnerabilities in a single payload. Leveraging uncorrected bugs in Oracle WebLogic, Windows SMB, and Apache Struts has earned around $ 200,000 worth of Monero cryptocurrency for the creators of MassMiner.Prowli
Prowli is a large, well-known botnet of more than 40,000 infected web servers, modems and other Internet of Things (IoT) devices that are used to mine cryptocurrency and redirect users to malicious sites. Part of Prowli is a brute-force worm that spreads the Monero miner. In some cases, the botnet also installs backdoors on infected systems.WinstarNssMiner
In three days in May 2018, WinstarNssMiner infected over half a million systems. When this cryptoger detects effective antivirus software on its target machine, it remains dormant, activating itself only on systems with weak security. Even worse, if you try to uninstall WinstarNssMiner, it will crash the infected system.Cryptomining cost
First, we need to understand the nature of cryptocurrency. These digital currencies are based on cryptography (also called hashing algorithms) that records financial transactions. There are only a certain number of hashes available that help establish the relative value of each unit.The creation of new units of cryptocurrency involves solving a complex mathematical problem. The first person to solve the problem will receive money for their efforts in this cryptocurrency. This means that legitimate cryptominers must invest in server farms to provide computing power, massive amounts of electricity, and cooling systems that help maintain mining efficiency while reducing the amount.
Distribution of cryptomining
Browser mining scripts are not malicious. Some websites are experimenting with them as a possible source of income to replace online advertising. For example, one of the first websites to try this approach was Quartz. The idea of distributing encryption efforts to the user's computers in exchange for access to the website seemed reasonable, especially since the user would be informed and asked to agree to the deal.Unfortunately, this approach has been used by criminals. Rather than investing in the infrastructure required for legitimate crypto mining, they see browser mining scenarios as a way to avoid these costs. And whether it's Coinhive offering Monero mining tools that you embed on a website, or Coinhive alternatives like EObot and Awesome Miner that Bitcoin browser miners use, criminals have tools at their fingertips.
How to determine if your computer has been infected
Considering the load on your processor, if your computer suddenly slows down or your battery runs out of power especially quickly, you could be jailbroken. How can you prove it?Open Windows Task Manager or MacOS Activity Monitor and click on Processes. If you see that your browser is consuming too many resources, you can close it and restart it. Unfortunately, this does not tell you which site the browser mining script was running on.
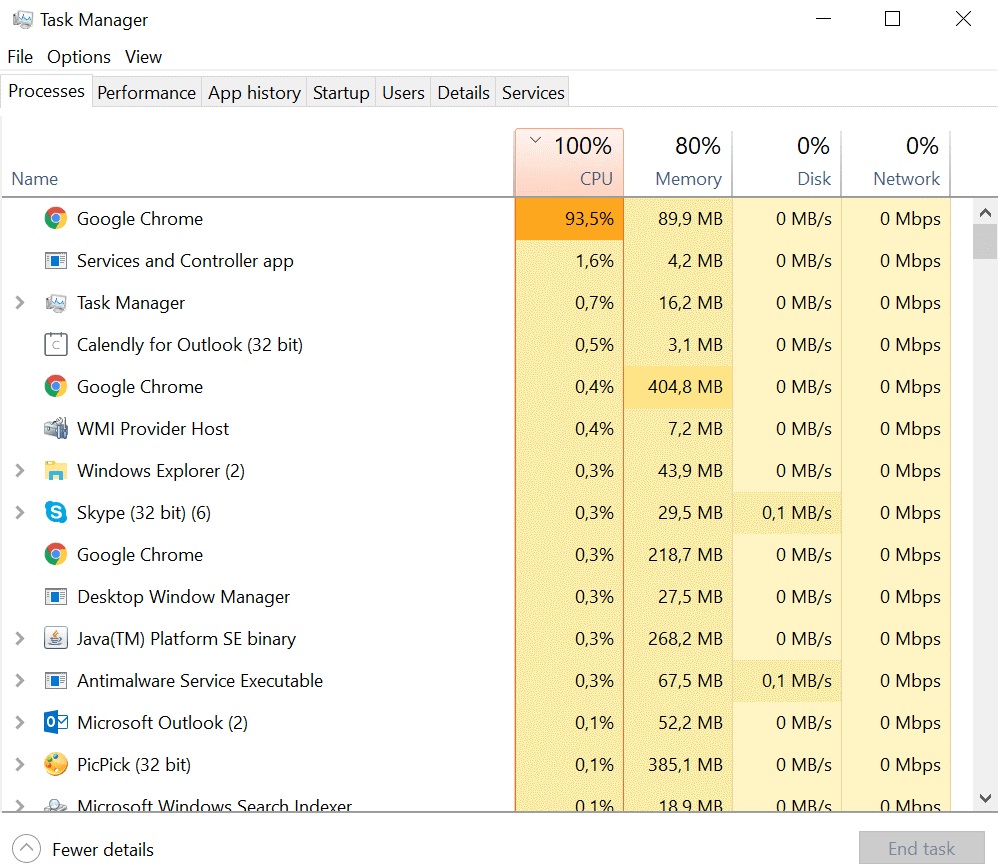
Unfortunately, this is difficult to notice. While the old scripts used the maximum CPU utilization, the new cryptomining scripts were loaded with a maximum of 20 percent, making them difficult to detect.
Stopping cryptomining in browsers
While it has become much more difficult to identify such attacks, there are steps you can take to automatically reduce your vulnerability to browser attacks.Deploying Browser Extensions
Most of the popular web browsers today include extensions that can help stop crypto mining attacks on the network. These can include both solutions developed by the browser developer and open source extensions that can be added. For example, No Coin and MinerBlocker solutions track suspicious activity and block attacks, and both have extensions available for Chrome, Opera, and Firefox.Ad-Blocker Software
Considering the explosion of cryptomining malware, many ad blockers now include a Coinhive blocker, which filters out script execution in your browser. If you have an ad blocker installed, you need to select that script blocker.Disable JavaScript
If you want to completely block certain attacks, most browsers will allow JavaScript to be disabled - although many legitimate sites still use JavaScript, disabling it can cause problems.Block domains
You can also block specific domains that you suspect of crypto mining. Just open your browser, look for the "Setting" dropdown and block the URL. To block Coinhive, you can copy / paste https://coin-hive.com/lib/coinhive.min.js into the text box.Conclusion
Blocking mining scripts in the browser is an essential step to ensure the integrity and efficiency of your system, and it is not at all difficult to take the steps necessary to protect your computer.However, it should be borne in mind that today there are many non-browser-based cryptojackers. Instead, they are separate programs that directly infect your system.
I hope you have licensed antivirus software at least? Of course, today you can use free antivirus software, which is widely available on the market. But is the free antivirus enough for you? I do not think. Although, of course, it's up to you!

