Man
Professional
- Messages
- 3,059
- Reaction score
- 585
- Points
- 113
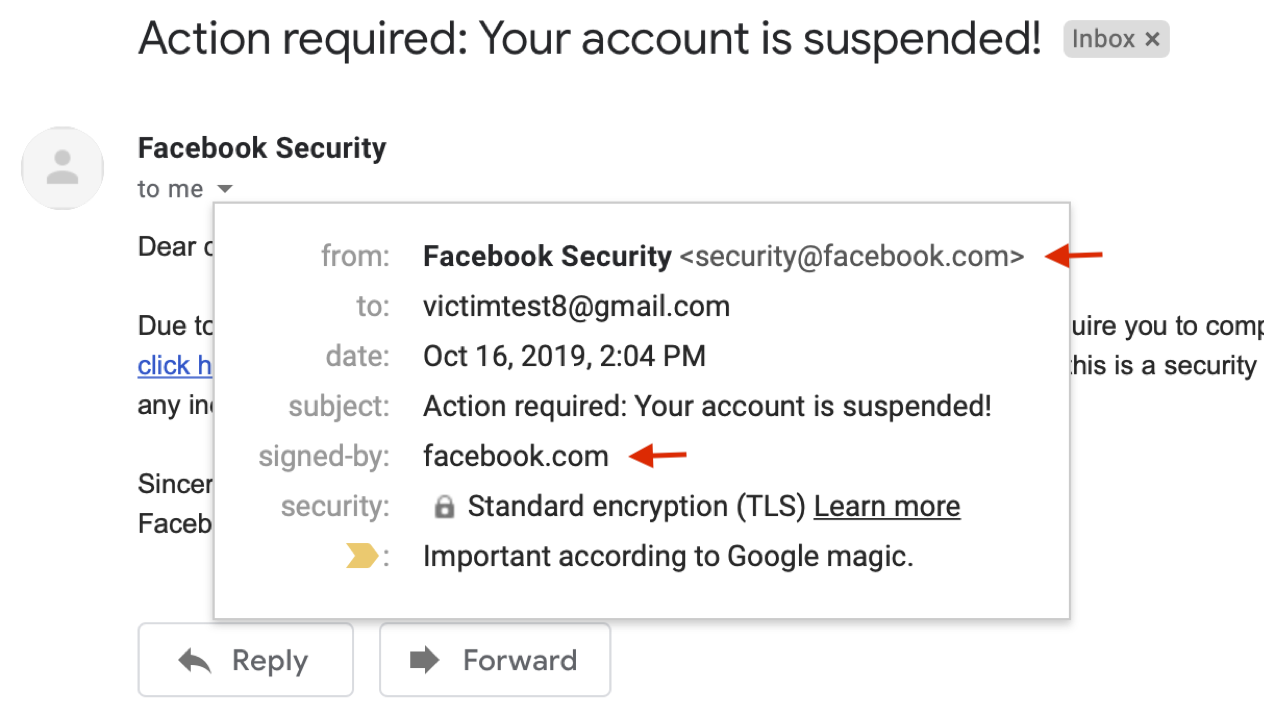
Gmail spoofing example: scammer forged return address facebook.com
Demo:
Many people don't know how easy it is to forge an email's return address. That is, to send a letter from someone else's address or from an arbitrary domain. Spammers, phishers, and other scammers constantly bypass SPF, DKIM, and DMARC protection.
Let's see how they do it and how to protect your letter from spoofing.
The average office worker receives 120 emails a day, most of which do not require an urgent response, and some are outright spam. You can’t do without filtering.
And where there is filtering, there are also errors. For example, your mail server can be blacklisted simply because it has unfortunate neighbors on VPS hosting from the same IP address range. Unfortunately, this is not an uncommon situation.
Another danger is sender address forgery. Examples of Yahoo hacking in 2014, hacks of Gmail accounts of high-ranking officials show that address forgery is a serious and current threat.
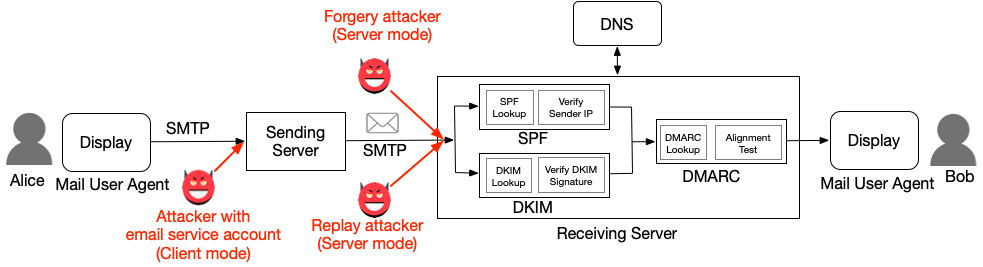
Three types of attacks for forging the return address, source
Forgery of sender's address
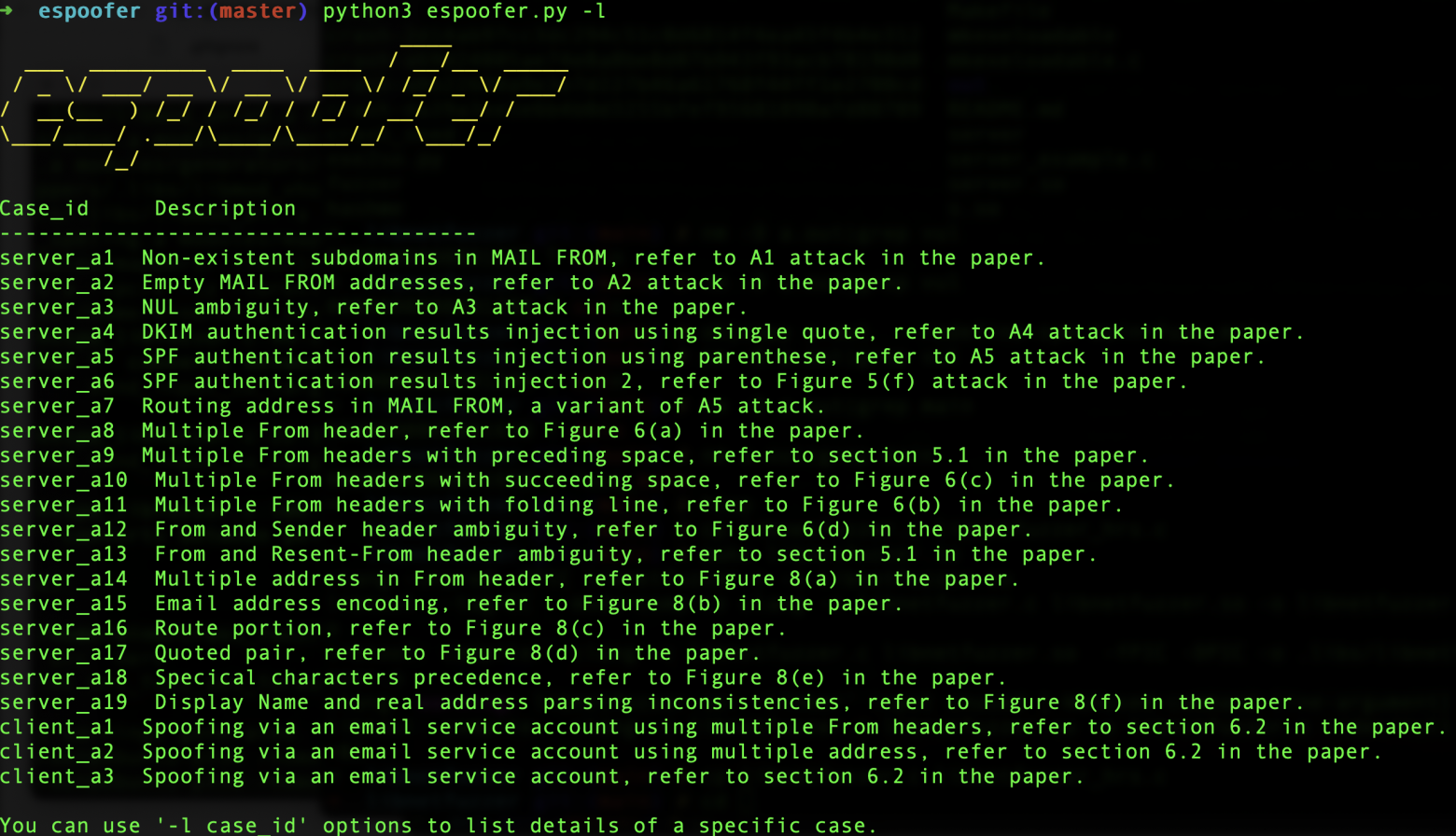
There are at least 18 ways to spoof an email sender address. For example, in 2020, the DEFCON hacker conference presented the espoofer utility, which allows you to bypass SPF, DKIM, and DMARC authentication in mail systems (see presentation slides, video).
The espoofer program helps system administrators and pentesters quickly identify vulnerabilities in target mail servers. Vulnerabilities in the mail server, issuing espoofer Unfortunately, there are a lot of such vulnerabilities, and attackers are finding new ways to bypass protection, because the email infrastructure is fundamentally vulnerable to such attacks (see below).
Protecting Electronic Messages
As practice shows, fraudsters successfully bypass SPF, DKIM and DMARC protection. All these policies have three common vulnerabilities:
- All of them are DNS-based, so all known types of DNS attacks (such as DNS query spoofing) are effective.
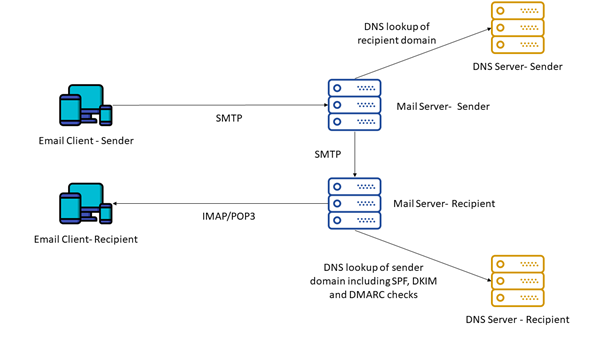
- Address protection is limited to the domain part only.
- Because DKIM signatures are only applied by the sender's mail server and verified by the recipient's mail server, the guarantee of content integrity and sender authenticity is not completely end-to-end. The message remains vulnerable between the client and the mail server for both the sender and the recipient. This problem can be solved by properly implementing TLS on both servers.
This is exactly the task that S/MIME does better than SPF, DKIM and DMARC.
Protection with S/MIME
S/MIME (Secure/Multipurpose Internet Mail Extensions) is a standard for encrypting and signing email using a public key:
- S/MIME signatures are applied directly by the sender's email client and are verified only by the recipient's email client. No manipulation of the message is possible at any stage.
- The public key for verifying the signature is included with the certificate that comes with the email, so the email client does not need to rely on the DNS record.
- The sender's organization in the certificate has been verified by a certification authority.
- The RFC 822 name format in the certificate exactly matches the field from, meaning the sender's authenticity is guaranteed at the email address level, not just at the domain level.
As we can see, existing SPF, DKIM and DMARC methods can be bypassed and the email can be forged if the sender does not use S/MIME protection with end-to-end encryption and digital signature.
Source
