Friend
Professional
- Messages
- 2,669
- Reaction score
- 944
- Points
- 113
Iranian hackers have changed tactics to gain credibility.
Proofpoint reports that Iranian hackers carried out a phishing attack on a well-known Jewish religious figure using several fake email addresses.
It was not possible to establish a direct connection between the attack and members of the IRGC. However, the hackers' activities have been monitored by other specialists for many years and have a number of similarities with the activity of the APT42 group, also known as TA453, Mint Sandstorm, Charming Kitten and Yellow Garuda.
The attackers first sent several emails, introducing themselves as the director of research at the American think tank Institute for the Study of War (ISW), and invited the victim to be a guest on a podcast. The initial email contained no malicious links, allowing the group to establish contact and gain the trust of the target.
However, after receiving a response from the target, TA453 sent a link to a document posted on the DocSend platform. The document contained a link to the real ISW podcast, protected by a password. This is probably done so that the target gets used to the idea of entering passwords and clicking on links.
Then, after another exchange of emails, the hackers sent a link to Google Drive with a ZIP archive of "Podcast Plan-2024.zip". Inside the archive was an LNK file designed to download a set of BlackSmith malicious tools, which, in turn, downloaded the AnvilEcho PowerShell Trojan. Notably, the LNK file is disguised as a PDF, and the fake PDF is displayed to the user while the malware is downloading in the background.
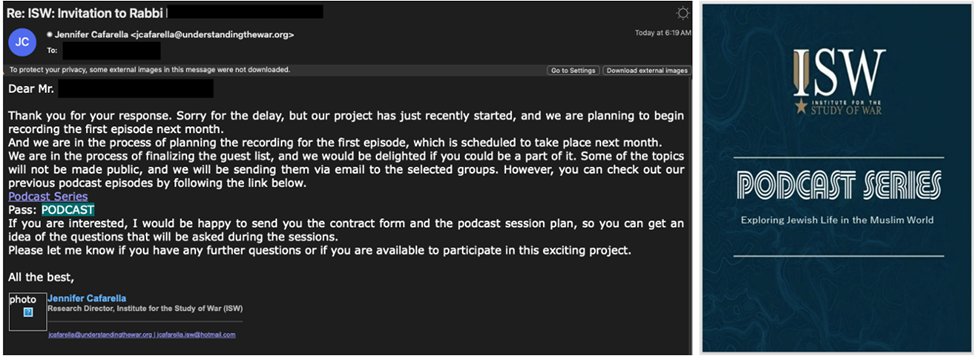
Email with a link to a ZIP archive (left) and a fake PDF (right)
The main goal of AnvilEcho is to collect and transmit the data of the attacker. The Trojan's modularity avoids detection and complicates analysis, as operators actively use encryption and methods to bypass security systems.
It was also found that the targets of the attack are in line with the strategic objectives of Iranian intelligence and are part of a general scheme of phishing attacks targeting politicians, human rights activists, dissidents and academics.
The attack on the religious figure began on July 22, and as it turned out, this is not the first time that TA453 has used fake podcast invitations. Earlier in February 2024, Proofpoint had already recorded similar phishing attacks using fake domains registered by the group in January. Fake podcast invitations have become a new tactic, but TA453 has already used various social engineering techniques to convince its targets to open or download malicious content.
Source
Proofpoint reports that Iranian hackers carried out a phishing attack on a well-known Jewish religious figure using several fake email addresses.
It was not possible to establish a direct connection between the attack and members of the IRGC. However, the hackers' activities have been monitored by other specialists for many years and have a number of similarities with the activity of the APT42 group, also known as TA453, Mint Sandstorm, Charming Kitten and Yellow Garuda.
The attackers first sent several emails, introducing themselves as the director of research at the American think tank Institute for the Study of War (ISW), and invited the victim to be a guest on a podcast. The initial email contained no malicious links, allowing the group to establish contact and gain the trust of the target.
However, after receiving a response from the target, TA453 sent a link to a document posted on the DocSend platform. The document contained a link to the real ISW podcast, protected by a password. This is probably done so that the target gets used to the idea of entering passwords and clicking on links.
Then, after another exchange of emails, the hackers sent a link to Google Drive with a ZIP archive of "Podcast Plan-2024.zip". Inside the archive was an LNK file designed to download a set of BlackSmith malicious tools, which, in turn, downloaded the AnvilEcho PowerShell Trojan. Notably, the LNK file is disguised as a PDF, and the fake PDF is displayed to the user while the malware is downloading in the background.

Email with a link to a ZIP archive (left) and a fake PDF (right)
The main goal of AnvilEcho is to collect and transmit the data of the attacker. The Trojan's modularity avoids detection and complicates analysis, as operators actively use encryption and methods to bypass security systems.
It was also found that the targets of the attack are in line with the strategic objectives of Iranian intelligence and are part of a general scheme of phishing attacks targeting politicians, human rights activists, dissidents and academics.
The attack on the religious figure began on July 22, and as it turned out, this is not the first time that TA453 has used fake podcast invitations. Earlier in February 2024, Proofpoint had already recorded similar phishing attacks using fake domains registered by the group in January. Fake podcast invitations have become a new tactic, but TA453 has already used various social engineering techniques to convince its targets to open or download malicious content.
Source
