Tomcat
Professional
- Messages
- 2,688
- Reaction score
- 1,037
- Points
- 113

EnSilo made a presentation at the Black Hat Europe 2017 conference and talked about a new attack technique called Process Doppelgänging. Such attacks work against all versions of Windows and can deceive most modern antiviruses by executing malicious code right under their noses.
How Process Doppelgänging works is similar to another well-known attack technique called Process Hollowing. This method of code injection involves creating a new instance of a legitimate process and then replacing the legitimate code with malicious code. Since the existence of Process Hollowing has been known for a long time, most security solutions successfully detect and suppress such manipulations.
But enSilo experts decided to develop this idea further and created an attack that allows you to more effectively hide malware from antiviruses in the context of legitimate processes. Process Doppelgänging involves the use of NTFS transactions, which allows you to modify a legitimate file in the context of the transaction, and then execute malicious code that eventually does not reach the disk at all (the attack turns out to be a bass file).
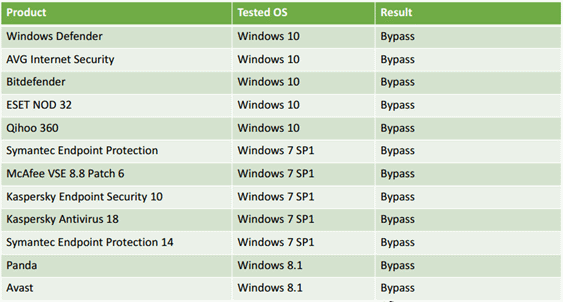
The researchers report that using Process Doppelgänging, they managed to trick the security solutions of Kaspersky Lab, Bitdefender, ESET, Symantec, McAfee, Windows Defender, AVG, Avast, Qihoo 360 and Panda. Even advanced cybercriminal software like Volatility failed to detect the attack. During the experiments, the specialists used Process Doppelgänging to run the well-known utility for recovering and stealing passwords, Mimikatz.NTFS (New Technology File System) is a standard file system for the Microsoft Windows NT family of operating systems. NTFS replaced the FAT file systems previously used in Microsoft Windows and MS-DOS. NTFS supports the metadata system, and also uses specialized data structures to store information about files to improve performance, reliability, and disk space efficiency.
Experts said that in order to use Process Doppelgänging, attackers need to know a lot of undocumented details about the operation and creation of processes, that is, it is unlikely that criminals will be able to easily adopt this technique. On the other hand, there is bad news: it is impossible to release patches for Process Doppelgänging, since the attack exploits the fundamental mechanisms and functions of Windows. However, enSilo products are already capable of detecting such attacks, which means that other vendors can also develop mechanisms for detecting Process Doppelgänging.

