Brother
Professional
- Messages
- 2,590
- Reaction score
- 533
- Points
- 113
Your pool party may be invaded by an intruder.
SafeBreach has developed a set of process integration techniques called Pool Party, which allows you to bypass EDR solutions (Endpoint Detection and Response). This technique was presented at the Black Hat Europe 2023 conference.
The researchers focused on poorly understood Windows thread pools (thread pool), opening up a new attack vector for embedding in processes. Experts have discovered 8 new methods of implementation in processes that allow you to initiate malicious execution as a result of a legitimate operation.
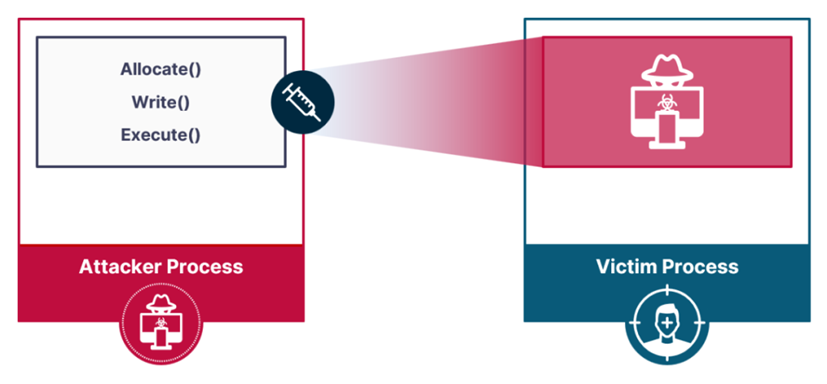
Implementation scheme in processes
The process injection technique consists of three stages: allocating memory in the target process, writing malicious code to the allocated memory, and executing the written malicious code. Researchers tested various methods and found that EDR solutions detect implementation in processes mainly through tracking the execution stage. They focused on creating an execution method based only on the allocation and write steps.
During the study of the thread pool in Windows user mode, experts came to the conclusion that it is possible to use worker factories objects for embedding in processes. A worker factory is a Windows object that manages pool worker threads, creating them or terminating them as needed. One of the methods discovered by the researchers uses the worker factories startup procedure, while the others use three types of queues. SafeBreach achieved 100% success in bypassing popular EDR solutions from Palo Alto, SentinelOne, CrowdStrike, Microsoft Defender For Endpoint and Cybereason.
SafeBreach has developed a set of process integration techniques called Pool Party, which allows you to bypass EDR solutions (Endpoint Detection and Response). This technique was presented at the Black Hat Europe 2023 conference.
The researchers focused on poorly understood Windows thread pools (thread pool), opening up a new attack vector for embedding in processes. Experts have discovered 8 new methods of implementation in processes that allow you to initiate malicious execution as a result of a legitimate operation.

Implementation scheme in processes
The process injection technique consists of three stages: allocating memory in the target process, writing malicious code to the allocated memory, and executing the written malicious code. Researchers tested various methods and found that EDR solutions detect implementation in processes mainly through tracking the execution stage. They focused on creating an execution method based only on the allocation and write steps.
During the study of the thread pool in Windows user mode, experts came to the conclusion that it is possible to use worker factories objects for embedding in processes. A worker factory is a Windows object that manages pool worker threads, creating them or terminating them as needed. One of the methods discovered by the researchers uses the worker factories startup procedure, while the others use three types of queues. SafeBreach achieved 100% success in bypassing popular EDR solutions from Palo Alto, SentinelOne, CrowdStrike, Microsoft Defender For Endpoint and Cybereason.

