Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
The cryptographer's attack geography has expanded to prepare for more sophisticated attacks.
ESET experts have identified a significant increase in attacks using the AceCryptor cryptographer in the second half of 2023. The tool allows hackers to invisibly inject malware to bypass antivirus programs.
Researchers have been tracking AceCryptor's activities for several years and noted that the latest campaign differs from the previous ones in that the attackers have expanded the range of embedded malicious code.
In the first 6 months of 2023, about 13,000 victims were attacked using AceCryptor. However, by the end of the year, the number of detected threats increased by more than 3 times, reaching over 42,000 users.
In the first half of 2023, the largest number of attacks using AceCryptor occurred in Peru, Mexico, Egypt,and Turkey, with the largest number of attacks recorded in Peru — 4,700. Europe took the brunt of the second half of the year, with Poland particularly affected, where more than 26,000 attacks were prevented.
AceCryptor has traditionally been used in conjunction with the remote surveillance tool Remcos (Rescoms) and the SmokeLoader loaders, and is also designed to distribute the STOP ransomware and Vidar infostiler.
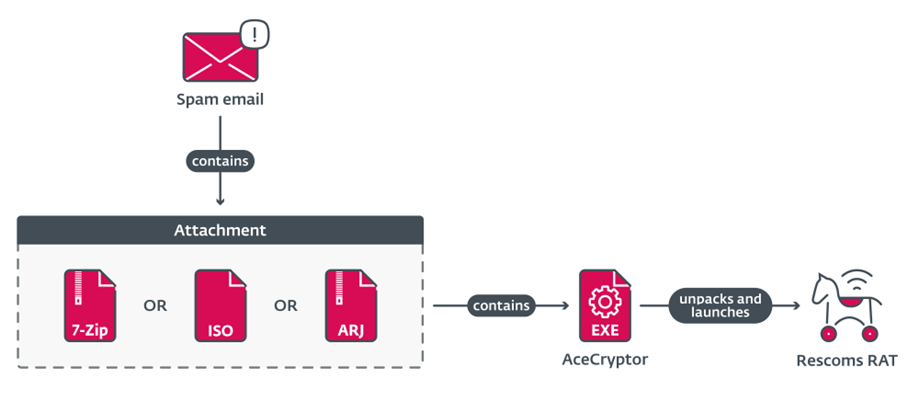
Remcos Infection Chain
The researchers found that attacks in different countries have their own characteristics. For example, SmokeLoader was used in Ukraine, and Remcos was used in Poland, Slovakia, Bulgaria, and Serbia. The goal of the campaign is to collect the credentials of email and browser accounts for further attacks against targeted companies.
The report pays special attention to campaigns that use Remcos. In the second half of the year, the number of attacks using Remcos exceeded 32,000, with more than half of them recorded in Poland. The attacks targeted businesses and used a variety of deception techniques, including spoofing email addresses and using real company names and employee names to make phishing emails more plausible. The email attachments contained AceCryptor executable files that activated the Remcos malware when launched.
Researchers from ESET can not yet say whether the attackers plan to use the stolen credentials themselves or sell them to other cybercriminals.
ESET experts have identified a significant increase in attacks using the AceCryptor cryptographer in the second half of 2023. The tool allows hackers to invisibly inject malware to bypass antivirus programs.
Researchers have been tracking AceCryptor's activities for several years and noted that the latest campaign differs from the previous ones in that the attackers have expanded the range of embedded malicious code.
In the first 6 months of 2023, about 13,000 victims were attacked using AceCryptor. However, by the end of the year, the number of detected threats increased by more than 3 times, reaching over 42,000 users.
In the first half of 2023, the largest number of attacks using AceCryptor occurred in Peru, Mexico, Egypt,and Turkey, with the largest number of attacks recorded in Peru — 4,700. Europe took the brunt of the second half of the year, with Poland particularly affected, where more than 26,000 attacks were prevented.
AceCryptor has traditionally been used in conjunction with the remote surveillance tool Remcos (Rescoms) and the SmokeLoader loaders, and is also designed to distribute the STOP ransomware and Vidar infostiler.

Remcos Infection Chain
The researchers found that attacks in different countries have their own characteristics. For example, SmokeLoader was used in Ukraine, and Remcos was used in Poland, Slovakia, Bulgaria, and Serbia. The goal of the campaign is to collect the credentials of email and browser accounts for further attacks against targeted companies.
The report pays special attention to campaigns that use Remcos. In the second half of the year, the number of attacks using Remcos exceeded 32,000, with more than half of them recorded in Poland. The attacks targeted businesses and used a variety of deception techniques, including spoofing email addresses and using real company names and employee names to make phishing emails more plausible. The email attachments contained AceCryptor executable files that activated the Remcos malware when launched.
Researchers from ESET can not yet say whether the attackers plan to use the stolen credentials themselves or sell them to other cybercriminals.

