Father
Professional
- Messages
- 2,602
- Reaction score
- 850
- Points
- 113
Massive attacks on vulnerable routers are now a matter of time.
SSD Secure Disclosure discovered vulnerabilities in the D-Link EXO AX4800 router (DIR-X4860) that allow you to take full control of the device.
Flaws were found in DIR-X4860 routers with the latest firmware version "DIRX4860A1_FWV1. 04B03". The vulnerabilities allow a remote unauthorized attacker with access to the HNAP port to gain root privileges and execute commands remotely (Remote Code Execution, RCE). By combining authentication bypass with command execution, an attacker can completely compromise the device.
Access to the Home Network Administration Protocol (HNAP) port is not difficult, as it is usually accessed via HTTP (port 80) or HTTPS (port 443) via the router's remote management interface.
Operation process
SSD analysts provided step-by-step instructions for exploiting the discovered vulnerabilities, making the Proof-of-Concept (PoC) publicly available. The attack begins by sending a specially crafted login request through the router's management interface, which includes the 'PrivateLogin' parameter, which is set to "Username", and the username"Admin".
The router responds with a call, a cookie, and a public key that are used to generate a valid password to log in to the "Admin"account. Then a second login request is sent with the HNAP_AUTH header and the generated LoginPassword, which effectively bypasses authentication.
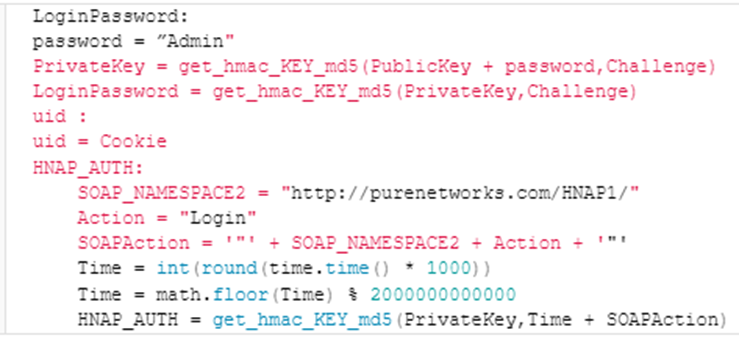
Login request that bypasses the authentication stage
With this access, the attacker then exploits the command injection vulnerability in the 'SetVirtualServerSettings' function using a specially crafted request. The function processes the 'LocalIPAddress' parameter without proper cleaning, which allows you to execute the entered command in the context of the router's operating system.
SSD claims to have contacted D-Link three times to share its findings over the past 30 days, but all notification attempts were unsuccessful, leaving vulnerabilities unresolved. Until a security firmware update is available, users of the DIR-X4860 router are advised to disable the device's remote management interface to prevent exploiting the vulnerability.
SSD Secure Disclosure discovered vulnerabilities in the D-Link EXO AX4800 router (DIR-X4860) that allow you to take full control of the device.
Flaws were found in DIR-X4860 routers with the latest firmware version "DIRX4860A1_FWV1. 04B03". The vulnerabilities allow a remote unauthorized attacker with access to the HNAP port to gain root privileges and execute commands remotely (Remote Code Execution, RCE). By combining authentication bypass with command execution, an attacker can completely compromise the device.
Access to the Home Network Administration Protocol (HNAP) port is not difficult, as it is usually accessed via HTTP (port 80) or HTTPS (port 443) via the router's remote management interface.
Operation process
SSD analysts provided step-by-step instructions for exploiting the discovered vulnerabilities, making the Proof-of-Concept (PoC) publicly available. The attack begins by sending a specially crafted login request through the router's management interface, which includes the 'PrivateLogin' parameter, which is set to "Username", and the username"Admin".
The router responds with a call, a cookie, and a public key that are used to generate a valid password to log in to the "Admin"account. Then a second login request is sent with the HNAP_AUTH header and the generated LoginPassword, which effectively bypasses authentication.

Login request that bypasses the authentication stage
With this access, the attacker then exploits the command injection vulnerability in the 'SetVirtualServerSettings' function using a specially crafted request. The function processes the 'LocalIPAddress' parameter without proper cleaning, which allows you to execute the entered command in the context of the router's operating system.
SSD claims to have contacted D-Link three times to share its findings over the past 30 days, but all notification attempts were unsuccessful, leaving vulnerabilities unresolved. Until a security firmware update is available, users of the DIR-X4860 router are advised to disable the device's remote management interface to prevent exploiting the vulnerability.
