Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
Remcos found a distribution method through the hidden IDAT Loader.
According to a Morphisec report, Ukrainian organizations based in Finland were targeted in a malicious campaign to spread the Remcos RAT . The attack was attributed to the UAC-0184 group.
The Remote Access Trojan (Remcos RAT) is delivered using the IDAT Loader. The phishing campaign involves using military-themed baits as a starting point for launching an infection chain that leads to the deployment of IDAT Loader, which, in turn, uses the built-in PNG image steganography algorithm to find and extract Remcos RAT. Remcos RAT allows an attacker to control an infected computer, steal personal information, and monitor the victim's actions.
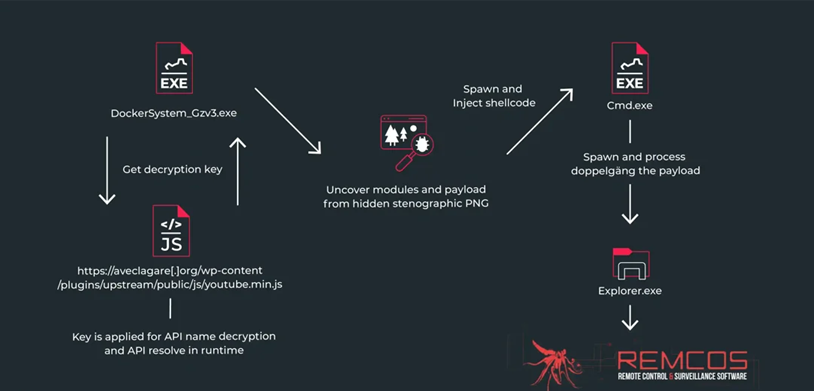
Remcos RAT infection Chain
The attack used phishing emails disguised as messages from the Israeli Defense Forces, and employed sophisticated malware delivery techniques, including dynamic loading of Windows API functions, checking Internet connectivity, and bypassing process blocking lists.
IDAT Loader, which has a modular architecture and features unique from other loaders, including code injection, was previously used to distribute the DanaBot, SystemBC, and RedLine Stealer malware families. In the detected campaign, IDAT modules were embedded directly into the executable file, which is a distinctive feature from the usual practice of downloading from a remote server.
The study also examines anti-detection techniques using steganography and Module Stomping, a technique that allows malicious code to evade detection by antivirus solutions by injecting it into legitimate libraries.
IDAT Loader overlaps with another family of loaders called HijackLoader, which was first spotted in July 2023 and allows delivery of DanaBot, SystemBC, and RedLine Stealer payloads. Despite the lack of advanced features, the loader uses a modular architecture for code injection and execution, which is rare for most loaders.
According to a Morphisec report, Ukrainian organizations based in Finland were targeted in a malicious campaign to spread the Remcos RAT . The attack was attributed to the UAC-0184 group.
The Remote Access Trojan (Remcos RAT) is delivered using the IDAT Loader. The phishing campaign involves using military-themed baits as a starting point for launching an infection chain that leads to the deployment of IDAT Loader, which, in turn, uses the built-in PNG image steganography algorithm to find and extract Remcos RAT. Remcos RAT allows an attacker to control an infected computer, steal personal information, and monitor the victim's actions.

Remcos RAT infection Chain
The attack used phishing emails disguised as messages from the Israeli Defense Forces, and employed sophisticated malware delivery techniques, including dynamic loading of Windows API functions, checking Internet connectivity, and bypassing process blocking lists.
IDAT Loader, which has a modular architecture and features unique from other loaders, including code injection, was previously used to distribute the DanaBot, SystemBC, and RedLine Stealer malware families. In the detected campaign, IDAT modules were embedded directly into the executable file, which is a distinctive feature from the usual practice of downloading from a remote server.
The study also examines anti-detection techniques using steganography and Module Stomping, a technique that allows malicious code to evade detection by antivirus solutions by injecting it into legitimate libraries.
IDAT Loader overlaps with another family of loaders called HijackLoader, which was first spotted in July 2023 and allows delivery of DanaBot, SystemBC, and RedLine Stealer payloads. Despite the lack of advanced features, the loader uses a modular architecture for code injection and execution, which is rare for most loaders.

