Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,298
- Points
- 113
A massive supply chain problem affects 813 UEFI products.
Binarly experts report that hundreds of UEFI products from 10 vendors are at risk of being hacked due to a critical PKfail vulnerability in the firmware supply chain that allows you to bypass Secure Boot and install malware.
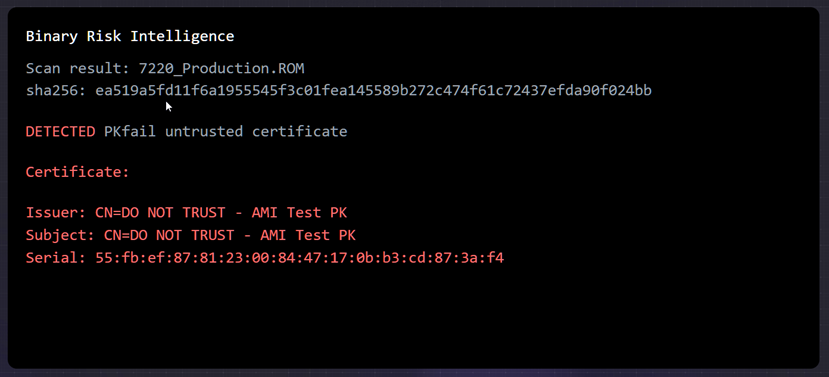
Vulnerable devices use the Secure Boot test key, also known as the Platform Key (PK), generated by American Megatrends International (AMI). The key was marked as "DO NOT TRUST" and the vendors had to replace it with their own keys generated in a secure manner.
However, often OEMs or device vendors do not replace the Platform Key, which leads to the delivery of devices with unreliable keys. Note that the Platform Key manages Secure Boot databases and supports a chain of trust from the firmware to the operating system.
Among the manufacturers of UEFI devices that used unreliable test keys were Acer, Aopen, Dell, Formelife, Fujitsu, Gigabyte, HP, Intel, Lenovo and Supermicro. In total, 813 products were under threat.
Vulnerable Intel firmware
If the PKfail issue is successfully exploited, a cybercriminal with access to vulnerable devices and a private part of the Platform Key can bypass Secure Boot protection by manipulating the Key Exchange Key, Signature Database, and Forbidden Signature Database databases. After hacking the entire chain, from the firmware to the operating system, an attacker can sign malicious code and distribute the CosmicStrand and BlackLotus UEFI rootkits.
Binarly notes that more than 10% of the firmware images in this set use an untrusted Platform Key. The first vulnerable firmware was released in May 2012, and the latest in June 2024, making the PKfail issue one of the longest-running of its kind, spanning more than 12 years.
The list of affected devices, which currently contains almost 900 devices, can be found in the vulnerability description (BRLY-2024-005, CVSS score: 8.2). A more detailed analysis of the scan results showed that our platform extracted and identified 22 unique untrusted keys
To prevent an attack, vendors are encouraged to generate and manage a Platform Key using hardware security modules. You must replace any test keys provided by independent BIOS vendors with your own keys generated in a secure manner.
Users should monitor firmware updates and apply all security fixes related to the PKfail issue in a timely manner. Binarly also published the pk. fail website, which helps users scan binary firmware files for free to find vulnerable devices and malicious downloads.
Source
Binarly experts report that hundreds of UEFI products from 10 vendors are at risk of being hacked due to a critical PKfail vulnerability in the firmware supply chain that allows you to bypass Secure Boot and install malware.
Vulnerable devices use the Secure Boot test key, also known as the Platform Key (PK), generated by American Megatrends International (AMI). The key was marked as "DO NOT TRUST" and the vendors had to replace it with their own keys generated in a secure manner.
However, often OEMs or device vendors do not replace the Platform Key, which leads to the delivery of devices with unreliable keys. Note that the Platform Key manages Secure Boot databases and supports a chain of trust from the firmware to the operating system.
Among the manufacturers of UEFI devices that used unreliable test keys were Acer, Aopen, Dell, Formelife, Fujitsu, Gigabyte, HP, Intel, Lenovo and Supermicro. In total, 813 products were under threat.

Vulnerable Intel firmware
If the PKfail issue is successfully exploited, a cybercriminal with access to vulnerable devices and a private part of the Platform Key can bypass Secure Boot protection by manipulating the Key Exchange Key, Signature Database, and Forbidden Signature Database databases. After hacking the entire chain, from the firmware to the operating system, an attacker can sign malicious code and distribute the CosmicStrand and BlackLotus UEFI rootkits.
Binarly notes that more than 10% of the firmware images in this set use an untrusted Platform Key. The first vulnerable firmware was released in May 2012, and the latest in June 2024, making the PKfail issue one of the longest-running of its kind, spanning more than 12 years.
The list of affected devices, which currently contains almost 900 devices, can be found in the vulnerability description (BRLY-2024-005, CVSS score: 8.2). A more detailed analysis of the scan results showed that our platform extracted and identified 22 unique untrusted keys
To prevent an attack, vendors are encouraged to generate and manage a Platform Key using hardware security modules. You must replace any test keys provided by independent BIOS vendors with your own keys generated in a secure manner.
Users should monitor firmware updates and apply all security fixes related to the PKfail issue in a timely manner. Binarly also published the pk. fail website, which helps users scan binary firmware files for free to find vulnerable devices and malicious downloads.
Source
