CarderPlanet
Professional
- Messages
- 2,552
- Reaction score
- 730
- Points
- 113
All graphics adapters are subject to an unprecedented content theft attack.
Graphics processing units (GPUs) from six major manufacturers are vulnerable to a new method of browser-based data theft attacks. According to the researchers detailed article, malicious websites with special content can gain access to usernames, passwords, and other sensitive data displayed by other websites.
The new type of attack violates a security principle known as the "Domain Restriction Rule" or "Same Origin Policy", which requires the content of one domain to be isolated from all others.
The attack named by the researchers "GPU.zip", starts with the victim navigating to a malicious website that places in its code a link to the web page they want to read data from, inside an "iframe", a regular HTML element that allows sites to insert ads, images, or other content.
Typically, a domain restriction rule prohibits one site from verifying the source code, content, or final visual product of another. However, the researchers found that the data compression used by video adapters to improve performance can be used by attackers as a side channel and a step-by-step "pixel theft".
"We found that modern GPUs automatically attempt to compress this visual data, without any application involvement," said Yangchen Wang, the study's lead author.
For a successful attack, the malicious page must be loaded in the Chrome or Edge browsers. While Firefox and Safari are protected from this threat due to their unique characteristics.
The researchers showed how "GPU.zip" allows a malicious website that they created as a proof-of-concept attack to steal pixels one by one, thus stealing the name of one of the Wikipedia users.
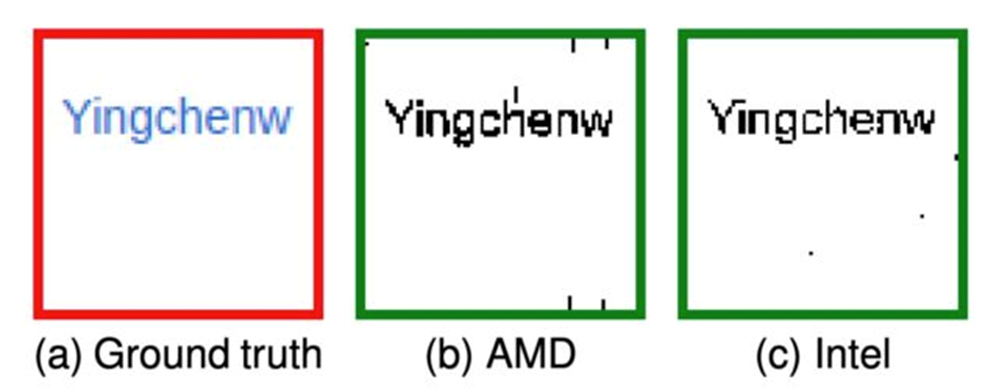
The attack works on GPUs supplied by Apple, Intel, AMD, Qualcomm, ARM, and Nvidia. At the same time, the attack speed also depends on the processor power.
So, on an AMD Ryzen 7 4800U with a Radeon RX Vega 8 video core, a successful attack took only 30 minutes to show the original content with 97% accuracy. However, on an Intel Core i7-8700 with integrated UHD Graphics 630, it took 215 minutes to restore pixels.
However, the attack is applicable not only to integrated video chips, but also to discrete ones, where the rate of content theft will be significantly higher.
Although the vulnerability is "GPU.zip" is currently more of a curiosity than a real threat, and it's important that web developers properly restrict access to sensitive pages. To check the presence of such restrictions, users can search for the "X-Frame-Options" or "Content-Security-Policy" headers in the code of the web pages used.
A Google spokesperson said that the company is actively discussing the results of the study with the authors. While an Intel representative pointed out that the root of the problem is not in their GPU, but in third-party software.
This research will be presented at the 45th IEEE Symposium on Security and Privacy in San Francisco. Although the current threat is from " GPU.zip" is small, and the results of the study are important for hardware and software developers.
"GPU.zip is another example of how incorrect hardware optimization creates a side channel that the software is not able to mitigate," said the author of the study.
Graphics processing units (GPUs) from six major manufacturers are vulnerable to a new method of browser-based data theft attacks. According to the researchers detailed article, malicious websites with special content can gain access to usernames, passwords, and other sensitive data displayed by other websites.
The new type of attack violates a security principle known as the "Domain Restriction Rule" or "Same Origin Policy", which requires the content of one domain to be isolated from all others.
The attack named by the researchers "GPU.zip", starts with the victim navigating to a malicious website that places in its code a link to the web page they want to read data from, inside an "iframe", a regular HTML element that allows sites to insert ads, images, or other content.
Typically, a domain restriction rule prohibits one site from verifying the source code, content, or final visual product of another. However, the researchers found that the data compression used by video adapters to improve performance can be used by attackers as a side channel and a step-by-step "pixel theft".
"We found that modern GPUs automatically attempt to compress this visual data, without any application involvement," said Yangchen Wang, the study's lead author.
For a successful attack, the malicious page must be loaded in the Chrome or Edge browsers. While Firefox and Safari are protected from this threat due to their unique characteristics.
The researchers showed how "GPU.zip" allows a malicious website that they created as a proof-of-concept attack to steal pixels one by one, thus stealing the name of one of the Wikipedia users.

The attack works on GPUs supplied by Apple, Intel, AMD, Qualcomm, ARM, and Nvidia. At the same time, the attack speed also depends on the processor power.
So, on an AMD Ryzen 7 4800U with a Radeon RX Vega 8 video core, a successful attack took only 30 minutes to show the original content with 97% accuracy. However, on an Intel Core i7-8700 with integrated UHD Graphics 630, it took 215 minutes to restore pixels.
However, the attack is applicable not only to integrated video chips, but also to discrete ones, where the rate of content theft will be significantly higher.
Although the vulnerability is "GPU.zip" is currently more of a curiosity than a real threat, and it's important that web developers properly restrict access to sensitive pages. To check the presence of such restrictions, users can search for the "X-Frame-Options" or "Content-Security-Policy" headers in the code of the web pages used.
A Google spokesperson said that the company is actively discussing the results of the study with the authors. While an Intel representative pointed out that the root of the problem is not in their GPU, but in third-party software.
This research will be presented at the 45th IEEE Symposium on Security and Privacy in San Francisco. Although the current threat is from " GPU.zip" is small, and the results of the study are important for hardware and software developers.
"GPU.zip is another example of how incorrect hardware optimization creates a side channel that the software is not able to mitigate," said the author of the study.

