How MS Office delivers a cocktail of viruses to your computer.
Cybercriminals distribute a set of malware through hacked versions of Microsoft Office, which are promoted on torrent sites. Malicious programs include Trojans, cryptocurrency miners, malware loaders, proxy tools, and programs that disrupt antivirus programs.
The ASEC identified the campaign and warned about the risks of downloading pirated software. The researchers found that the attackers used several decoys, including Microsoft Office, Windows, and the popular Korean text editor Hangul Word Processor.
The hacked Microsoft Office installer has a well-designed interface that allows users to choose the version, language, and bit depth (32 or 64 bits).
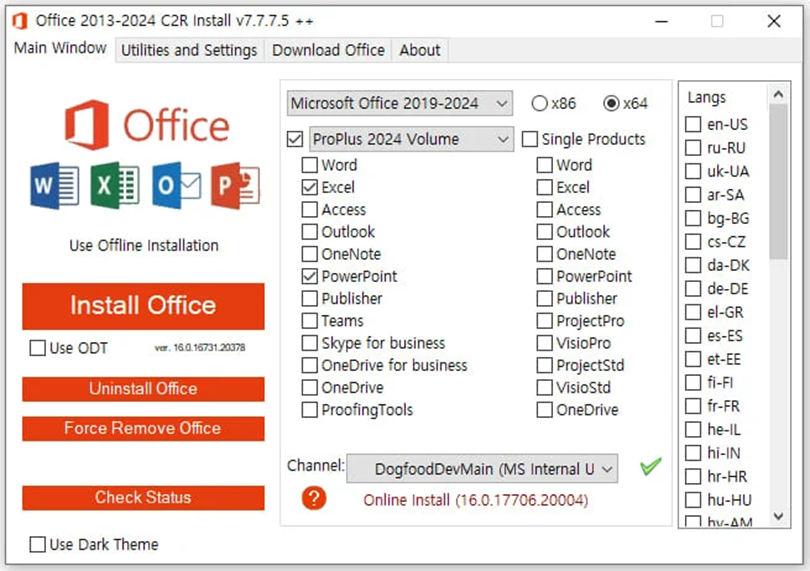
Installer Interface
However, in the background, the installer runs obfuscated malware based on .NET, which communicates with the Telegram or Mastodon channel to get a valid URL for downloading additional components. URLs point to Google Drive or GitHub-legitimate services that rarely trigger antivirus warnings.
base64 payloads hosted on Google Drive and GitHub contain PowerShell commands that inject various strains of malware unpacked using 7Zip into the system. One of the components, called "Updater", registers tasks in the Windows Task Scheduler to ensure that they are saved between system reboots.
Eventually, the following programs are delivered to the system:
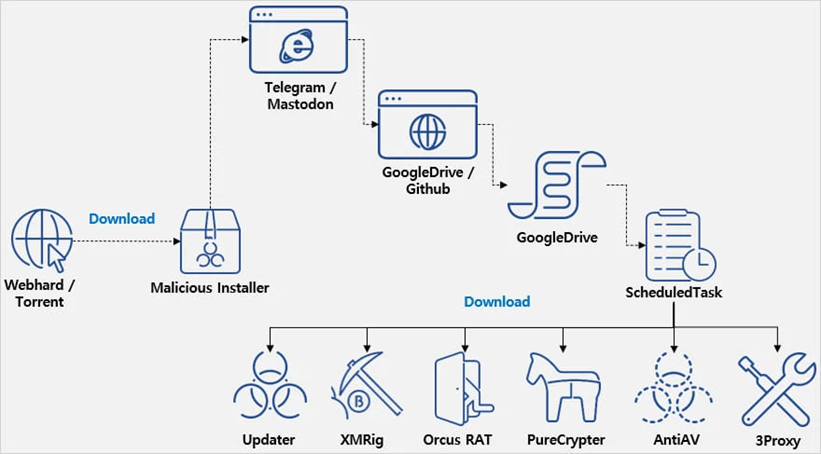
Infection chain
Users should be careful when installing files downloaded from dubious sources and avoid using pirated software. Similar campaigns are also often used to distribute ransomware, such as STOP, which is one of the most active ransomware operations targeting consumers.
Cybercriminals distribute a set of malware through hacked versions of Microsoft Office, which are promoted on torrent sites. Malicious programs include Trojans, cryptocurrency miners, malware loaders, proxy tools, and programs that disrupt antivirus programs.
The ASEC identified the campaign and warned about the risks of downloading pirated software. The researchers found that the attackers used several decoys, including Microsoft Office, Windows, and the popular Korean text editor Hangul Word Processor.
The hacked Microsoft Office installer has a well-designed interface that allows users to choose the version, language, and bit depth (32 or 64 bits).

Installer Interface
However, in the background, the installer runs obfuscated malware based on .NET, which communicates with the Telegram or Mastodon channel to get a valid URL for downloading additional components. URLs point to Google Drive or GitHub-legitimate services that rarely trigger antivirus warnings.
base64 payloads hosted on Google Drive and GitHub contain PowerShell commands that inject various strains of malware unpacked using 7Zip into the system. One of the components, called "Updater", registers tasks in the Windows Task Scheduler to ensure that they are saved between system reboots.
Eventually, the following programs are delivered to the system:
- Orcus RAT: Provides comprehensive remote management, including keystroke logging (keylogger), webcam access, screen capture, and manipulating the system to steal data;
- XMRig: a cryptocurrency miner that uses system resources to mine Monero. Stops mining during heavy resource usage, such as when the victim is playing to avoid detection;
- 3Proxy: Converts infected systems into proxy servers, allowing attackers to route malicious traffic;
- PureCrypter: downloads and executes additional malicious files from external sources, ensuring that the system remains infected with the latest threats;
- AntiAV: disrupts and disables security software, making the system vulnerable to other components.

Infection chain
Users should be careful when installing files downloaded from dubious sources and avoid using pirated software. Similar campaigns are also often used to distribute ransomware, such as STOP, which is one of the most active ransomware operations targeting consumers.
