Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,038
- Points
- 113
Who are the workers and how do they cheat on trading platforms?
Fraud on message boards and trading platforms has become a serious problem due to the emergence of organized criminal groups. They work on the Fraud-as-a-Service model, constantly improving schemes for stealing money and personal data from gullible users.
There are two main schemes of deception:
In the scam 2.0 scheme, attackers carefully select potential victims. They are interested in ads that the seller paid money to promote. Also attract high-quality photos of the product and the willingness to communicate in messengers. Finally, attackers are looking for sellers who use third-party messengers and are willing to provide a phone number. This is found out already at the stage of communication with the seller.
The main goal of scammers is to convince the victim to click on a phishing link and enter payment details. Communication begins with standard questions about the product, its condition, reasons for sale, etc. Experienced scammers ask no more than 3 questions to avoid arousing suspicion.
Then the attacker declares interest in the purchase, but indicates that he cannot pick up the product in person and pay in cash due to being in another city (or for another reason). After that, you are offered to use "secure delivery".
The fraudster describes in detail the scheme of an imaginary payment, in which the victim is asked to click on a phishing link and specify the details for transferring money. The payment scheme is approximately as follows:
If the victim starts arguing and insistently refuses this payment method, the fraudster disappears, because he does not want to waste time. If the seller asks to continue the correspondence on the official website of the trading platform, the attacker concludes that he knows about the fraud and is unlikely to follow the phishing link, so he also stops responding and starts looking for a new victim.
In the scam 2.0 scheme, there are two main variants of phishing pages: some are copies of the trading platform page with the victim's ad, while others imitate secure payment services such as Twin.
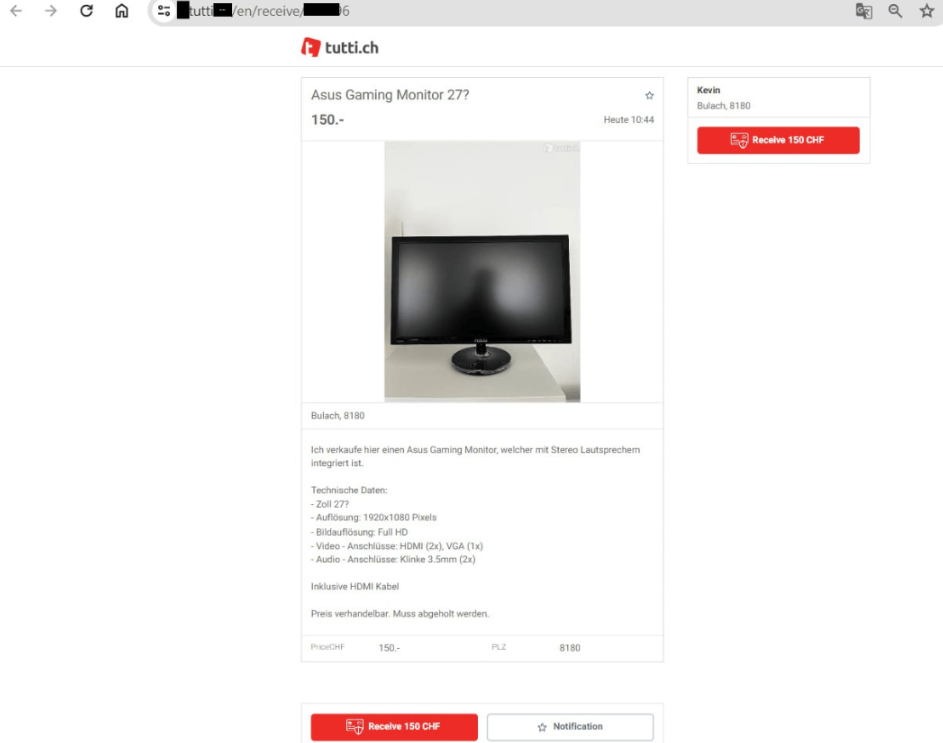
Phishing Ad
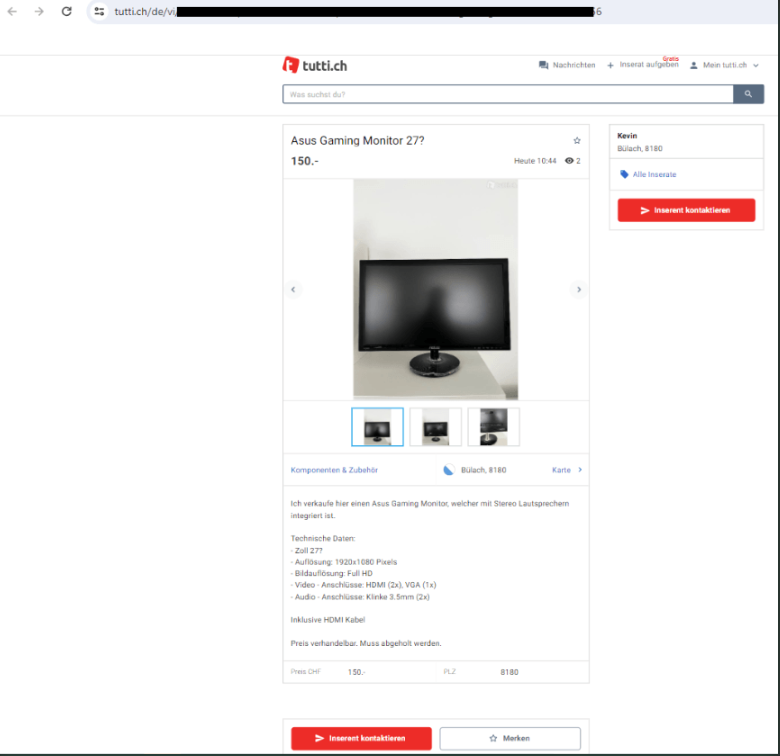
Original ad
The fake page differs from the original one only in minor details. In particular, instead of the Inserent kontaktieren button ("Contact the ad author"), the phishing page contains the Receive 150 CHF button ("Receive 150 Swiss francs").
Structure of fraudulent groups
Recently, there have been whole groups of scammers who specialize in bulletin boards. There is a clear division of roles in criminal groups:
Attackers communicate in private chats, keep statistics, and constantly improve their working methods.
Geographical coverage and goal selection
Scam 1.0 and scam 2.0 appeared several years ago, and both schemes can still be found on Russian-language message boards. However, scammers have recently switched to foreign countries, especially Switzerland, where the population is less familiar with such deception schemes. To increase their confidence, they learn local languages and traditions. The group also operates in Canada, Austria, France, and Norway.
Detailed manuals have been developed for novice workers: how to register, ensure anonymity, conduct dialogues with victims, circumvent the site's security restrictions, and so on. After receiving the payment data, "VB players" withdraw money in various ways - they make out loans, transfer them to electronic wallets, buy equipment, and so on.
Special Telegram bots are used to automate the process. They allow you to quickly create phishing links that copy the interface of real sites, track victims 'clicks on links, and receive notifications about "successful" payments. Bots are constantly updated with new statistics, tools, and features.
In order not to become a victim of fraud, it is important to trust only official sites, do not go to third-party resources from unreliable sources, do not enter card details until the product is received, and avoid QR codes from suspicious places.
Fraud on message boards and trading platforms has become a serious problem due to the emergence of organized criminal groups. They work on the Fraud-as-a-Service model, constantly improving schemes for stealing money and personal data from gullible users.
There are two main schemes of deception:
- Buyer scam (scam 1.0) - a fraudster impersonates the seller and offers the buyer to receive the goods by delivery. When the buyer asks about the terms of delivery and payment, the fraudster (in the role of the seller) asks you to send your full name, address and phone number, as well as pay for the order on the site. If the victim agrees, they are sent a phishing link to pay for the product (in a third-party messenger or in the dialog itself on the site, if the site does not block such links). As soon as the user enters the card details on the fake site, the fraudster gets access to them and debits all funds.
- Seller scam (scam 2.0) is a more common scheme. The fraudster introduces himself as the buyer and deceives the seller, persuading him to send the goods by delivery and make a so-called "safe transaction" or use a "secure payment method". As in the case of scam 1.0, attackers send a phishing link to the seller who agrees to the transaction in a third-party messenger or directly in the dialog on the site. The page that follows the link requests payment card details. If the seller enters them, the attacker debits all the money from the card.
In the scam 2.0 scheme, attackers carefully select potential victims. They are interested in ads that the seller paid money to promote. Also attract high-quality photos of the product and the willingness to communicate in messengers. Finally, attackers are looking for sellers who use third-party messengers and are willing to provide a phone number. This is found out already at the stage of communication with the seller.
The main goal of scammers is to convince the victim to click on a phishing link and enter payment details. Communication begins with standard questions about the product, its condition, reasons for sale, etc. Experienced scammers ask no more than 3 questions to avoid arousing suspicion.
Then the attacker declares interest in the purchase, but indicates that he cannot pick up the product in person and pay in cash due to being in another city (or for another reason). After that, you are offered to use "secure delivery".
The fraudster describes in detail the scheme of an imaginary payment, in which the victim is asked to click on a phishing link and specify the details for transferring money. The payment scheme is approximately as follows:
- I pay for your product on [ad platform name].
- You will receive a link to receive money.
- You click on the link and specify the account number to which it is convenient to receive money.
- As soon as you receive the money, the checkout service contacts you and assigns you a convenient delivery method. Delivery will already be paid for. The goods will be packed and processed for you.
If the victim starts arguing and insistently refuses this payment method, the fraudster disappears, because he does not want to waste time. If the seller asks to continue the correspondence on the official website of the trading platform, the attacker concludes that he knows about the fraud and is unlikely to follow the phishing link, so he also stops responding and starts looking for a new victim.
In the scam 2.0 scheme, there are two main variants of phishing pages: some are copies of the trading platform page with the victim's ad, while others imitate secure payment services such as Twin.

Phishing Ad

Original ad
The fake page differs from the original one only in minor details. In particular, instead of the Inserent kontaktieren button ("Contact the ad author"), the phishing page contains the Receive 150 CHF button ("Receive 150 Swiss francs").
Structure of fraudulent groups
Recently, there have been whole groups of scammers who specialize in bulletin boards. There is a clear division of roles in criminal groups:
- Topikstarters (organizers) manage all the group's activities.
- Coders are responsible for developing and maintaining the technical infrastructure.
- Refunds (technical support) help victims "solve" their questions until their money is stolen.
- Vbeevers are engaged in direct debiting of money from stolen accounts.
- Workers are "field agents" who interact directly with victims
- and others.
Attackers communicate in private chats, keep statistics, and constantly improve their working methods.
Geographical coverage and goal selection
Scam 1.0 and scam 2.0 appeared several years ago, and both schemes can still be found on Russian-language message boards. However, scammers have recently switched to foreign countries, especially Switzerland, where the population is less familiar with such deception schemes. To increase their confidence, they learn local languages and traditions. The group also operates in Canada, Austria, France, and Norway.
Detailed manuals have been developed for novice workers: how to register, ensure anonymity, conduct dialogues with victims, circumvent the site's security restrictions, and so on. After receiving the payment data, "VB players" withdraw money in various ways - they make out loans, transfer them to electronic wallets, buy equipment, and so on.
Special Telegram bots are used to automate the process. They allow you to quickly create phishing links that copy the interface of real sites, track victims 'clicks on links, and receive notifications about "successful" payments. Bots are constantly updated with new statistics, tools, and features.
In order not to become a victim of fraud, it is important to trust only official sites, do not go to third-party resources from unreliable sources, do not enter card details until the product is received, and avoid QR codes from suspicious places.

