Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
Traces of the group's unique Trojan lead to Kiev.
Experts from the Threat Intelligence department of F. A. C. C. T. have identified a new hacker group called PhantomCore. Since January 2024, this group has been actively attacking Russian companies using the unique, previously unknown remote access Trojan PhantomRAT.
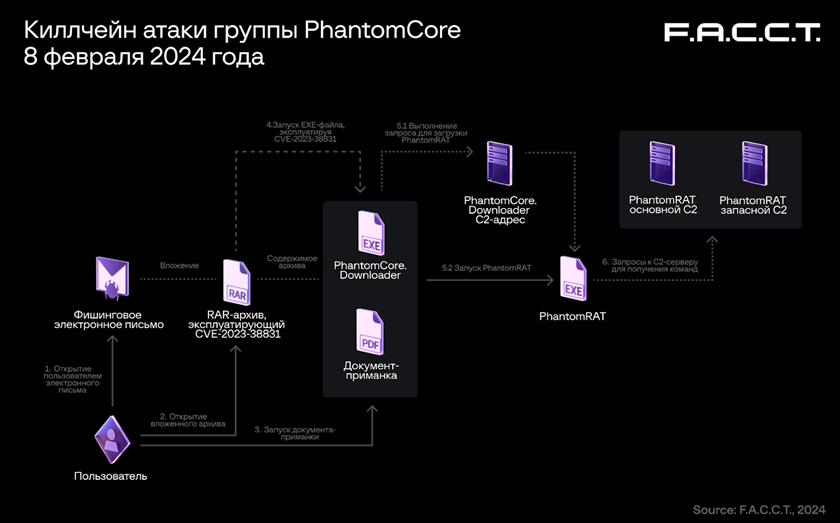
PhantomCore attacks start by sending phishing emails containing password-protected RAR archives. The password for the archives is specified directly in the message text. In archives, attackers exploit a new variation of the WinRAR vulnerability (CVE-2023-38831), where RAR archives are used instead of ZIP.
The archives themselves contain a PDF document and a directory of the same name where the executable file is located. When you try to open a PDF, a malicious executable file is launched. The final detected stage is the remote access Trojan PhantomRAT. The group also uses .NET applications, with a single-file deployment option to make detection on an infected system more difficult.
So far, the motives for the attacks are not exactly established, but judging by the goals and methods, it is most likely that we are talking about cyber espionage. Interestingly, one of the files intended for testing the PhantomRAT build was first uploaded to VirusTotal on February 26, 2024, from Kiev. Two more test samples of the unique PhantomCore malware were also uploaded from Ukraine.
According to the forecast of the F. A. C. C. T., the main cyber threats for Russian companies and government agencies in 2024 will be ransomware, cyber spies, saboteurs and hacktivists hunting for databases.
Details about the first attacks of the new group, as well as indicators of compromise, are given in the company's blog.
Experts from the Threat Intelligence department of F. A. C. C. T. have identified a new hacker group called PhantomCore. Since January 2024, this group has been actively attacking Russian companies using the unique, previously unknown remote access Trojan PhantomRAT.

PhantomCore attacks start by sending phishing emails containing password-protected RAR archives. The password for the archives is specified directly in the message text. In archives, attackers exploit a new variation of the WinRAR vulnerability (CVE-2023-38831), where RAR archives are used instead of ZIP.
The archives themselves contain a PDF document and a directory of the same name where the executable file is located. When you try to open a PDF, a malicious executable file is launched. The final detected stage is the remote access Trojan PhantomRAT. The group also uses .NET applications, with a single-file deployment option to make detection on an infected system more difficult.
So far, the motives for the attacks are not exactly established, but judging by the goals and methods, it is most likely that we are talking about cyber espionage. Interestingly, one of the files intended for testing the PhantomRAT build was first uploaded to VirusTotal on February 26, 2024, from Kiev. Two more test samples of the unique PhantomCore malware were also uploaded from Ukraine.
According to the forecast of the F. A. C. C. T., the main cyber threats for Russian companies and government agencies in 2024 will be ransomware, cyber spies, saboteurs and hacktivists hunting for databases.
Details about the first attacks of the new group, as well as indicators of compromise, are given in the company's blog.

