Brother
Professional
- Messages
- 2,590
- Reaction score
- 533
- Points
- 113

Information security specialist Alex Birsan received $ 15,300 through the bug bounty program, having discovered a critical vulnerability in the PayPal authentication process.
The expert explains that the vulnerability was related to the way PayPal stores CSRF tokens and session IDs in a JavaScript file, which made them available to attackers through XSSI attacks. Although an obfuscator was used to randomize the names for each request, it was still possible to predict where the tokens were and retrieve them.
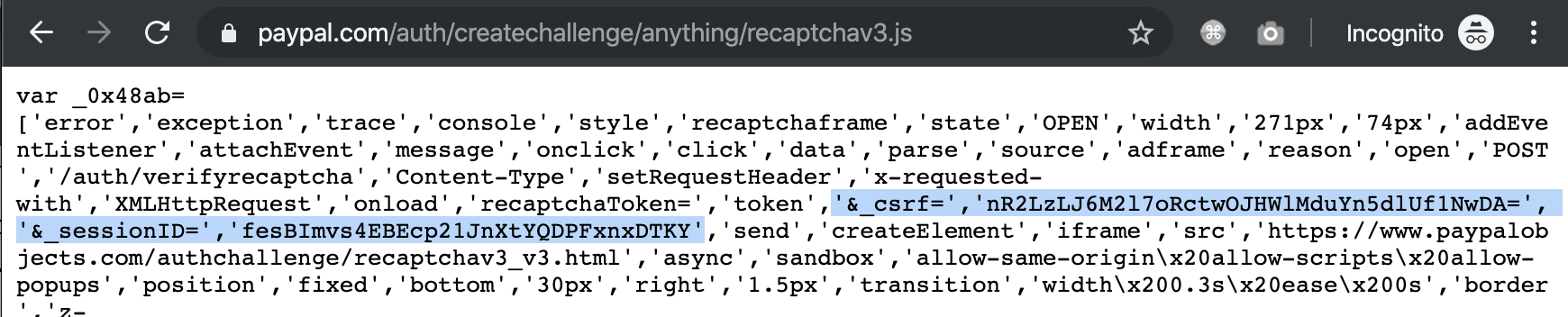
While session IDs and tokens by themselves are useless for direct attacks, Birsan used them while compromising a mechanism that protects PayPal from brute force. So, after several unsuccessful login attempts, the user must solve the reCAPTCHA problem. This page does not contain anything other than Google CAPTCHA, and if the task is successfully completed, a POST request is generated to / auth / validatecaptcha.
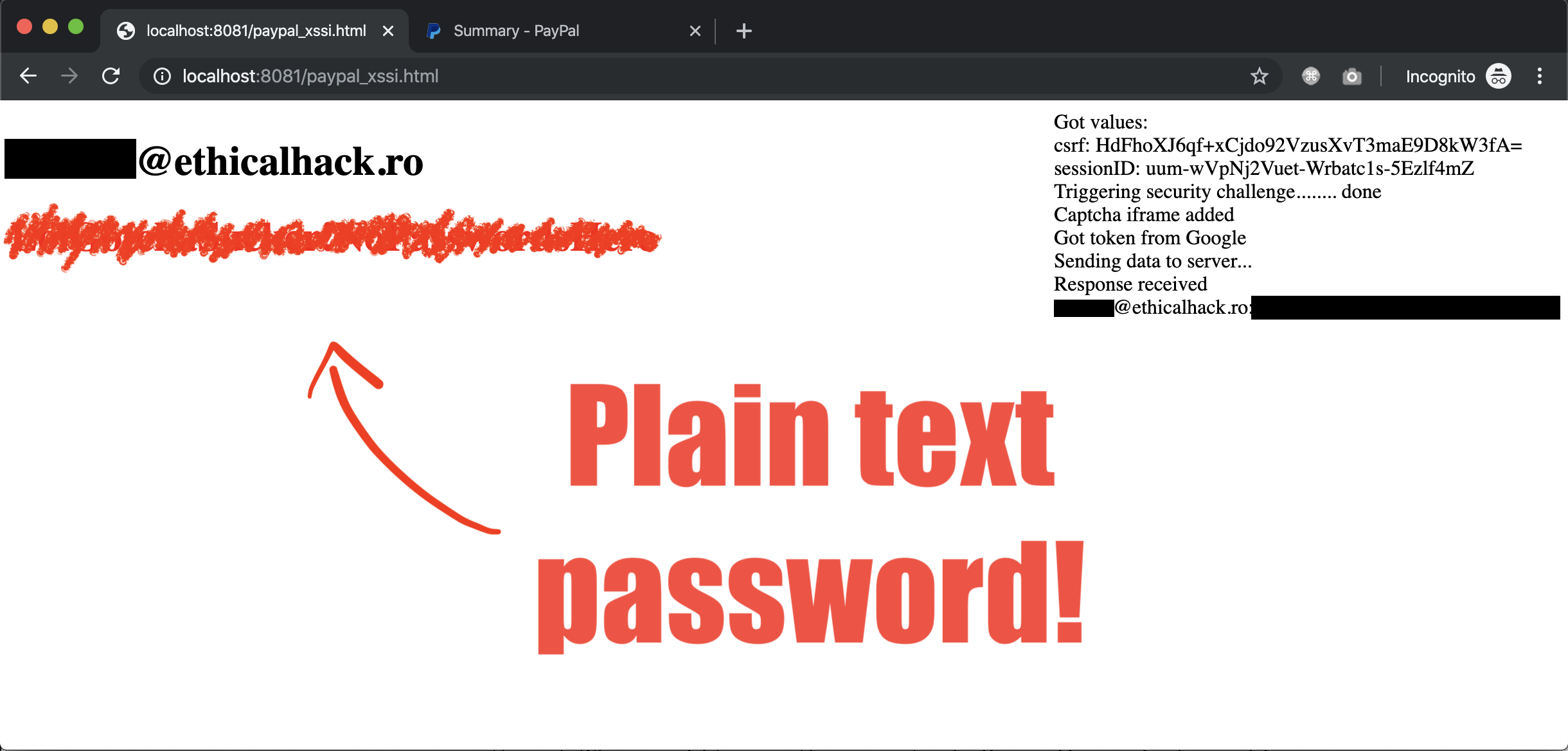
The response to this request, in essence, should re-enter the user into the authentication process. To do this, it contains a form with all the data specified in the user's last login request, including his email address, a plain text password. To get to these credentials, the attacker would need to convince the victim to visit the malicious site before logging into their PayPal account.
Since the CSRF token and session ID are present in the request body, along with two other tokens, the victim's credentials can be obtained if all tokens used in the request are known. The value of one of these unknown tokens is not validated, while the other is the recaptcha token provided by Google when solving the reCAPTCHA problem. The latter is not session bound, that is, any valid token is suitable, including from the autoresolve service.
Using the information above, the researcher created an expoit that first exploited the XSSI vulnerability to obtain valid tokens from the victim, and then attempted a brute-force attempt to trigger the defense mechanism.
Birsan reported the vulnerability to PayPal representatives through the HackerOne platform back in November 2019. Already on December 11, 2019, the developers released a patch, and the specialist was rewarded for finding an error 15 300 US dollars.
(c) xakep.ru

