BadB
Professional
- Messages
- 1,709
- Reaction score
- 1,697
- Points
- 113
It is no secret that most of the data, or at least hints of its existence, are contained in open sources. Social networks, various applications and just personal notes and photos in public - all this creates a unique digital imprint of a person. And in order to create to find out a sufficient amount of information about a person, it is not at all necessary to be a representative of the organs. Sometimes it's enough just to know where to look.
Properly honed information retrieval skills are essential. This knowledge is especially important when you collect information about a person or company, or you need to check important information. Wondering how to do this? Then today we'll talk about OSINT.
What is OSINT?
OSINT (Open Source Intelligence) - search, collection and analysis of information received from publicly available sources. For example, getting information from social networks, personal sites and forums, as well as from search engines. To better understand the essence of this term, let's look at examples.
If you look at history, one of the famous CIA analysts, Ken Sherman, stated that the state gets more than 80% of the information it needs from open sources. A little later, the head of the US Defense Intelligence Agency, Samuel Wilson, said that more than 90% of all intelligence data is in open sources, the rest is the success of agents. Statistics captures and confirms the relevance of OSINT.
In our age of Internet accessibility, there are a lot of search opportunities in open sources. An ordinary user tells a lot of information about himself: connections with other people, profiles on social networks, interests, geolocation, marital status, etc. Using such sources to collect information is OSINT.
Why don't most users know how to search for information?
Using open source search, you can solve more than one mystery of private detectives. After all, there are a lot of open government resources, forums, social networks and other sources for finding information around. But it is very important not to get confused in all this and learn to find the most important thing in order to find a real treasure among the tons of sand.
Beginners do not always correctly perceive the information received. Let's say there are some records, photos, the user lives like everyone else, and he has nothing serious. But if you dig deeper, analyze the activity, groups, geotags, comments, and also check the nickname for being busy on other services? After completing such a simple list, you can find a lot of interesting information. But that's not all either.
Let's take a look at the case. Let's imagine that there is a user Vasya from St. Petersburg, he is registered in Vkontakte and Facebook. Minimum information and photos, boring profile, nothing special. And now let's imagine that after a slash in the VK address bar his nickname vasechka66 is written. And having broken through such information, you can find an active user on forums with a similar place of residence. And this is more interesting, because here Vanya posts photos from his vacation, openly communicates about his political views, and also publishes incredible stories from his life. This is the beauty of OSINT.
How to approach open data search in a structured way?
This is not an exhaustive list and the methods I have described are not redundant. However, for beginners, this can serve as a starting point. And then - there is no limit to perfection.
For convenience, we have divided the entire process into stages.
1. Formation of tasks
At this stage, you need to clearly understand what you need to get in the end. This can be, for example, the nicknames that the target uses. Or you need to break through absolutely all the information about a person on the Internet. Typically, the key data for sending are phone numbers, email addresses, nicknames, or social media leads.
Stage 2. Planning
At this stage, you need to determine all possible directions and sources that will be used for the search. As a rule, there are 3 main ones:
Personal (social networks, blogs, websites, nicknames, etc.).
State (registers, bases, courts, taxes, border bases, diploma bases, base of invalid passports, etc.).
External sources (friends, acquaintances, media, employers, recommendations).
It is very important to visualize. The best way to do this is to use XMind, MindMap, Maltego or other similar apps. For each goal, you need to make your own roadmap.
3. Gathering information
This stage is the most time consuming, but it is mainly implemented using a set of software and online services. As you approach this stage, you should have some preliminary information. For example, you know that a person uses the last name of their first teacher as their password. And, let's say, our victim has it as a friend on VKontakte. This significantly narrows the circle and it becomes clear where to look first.
But sometimes there is no such information and you need to search for absolutely everything. It's best to start with your first name, last name and nickname first. Then you can promote and search for a phone number, a list of friends, build connections in social networks and forums. But as practice shows, almost all search results are based on three things: phone number, email and nickname.
Here we have compiled a small selection of resources and sites that you can search for.
Search by home phone, full name and city or address of residence http://spra.vkaru.net or http://nomerorg.me. Attention, you can search here if a person has a home or office number. The service does not search for SIP, mobile, etc.
Special sites. For example, the search engines Shodan and Censys. This will be relevant if you have the target IP address.
Search in court cases of the Russian Federation https://sudrf.ru/index.php?id=300
Base of diplomas http://frdocheck.obrnadzor.gov.ru
Base of bailiffs http://fssprus.ru/iss/ip/
Base of invalid passports http://services.fms.gov.ru/info-service.htm?sid=2000
TIN database https://service.nalog.ru/static/personal-data.html?svc=inn
As well as many other tax data available on the same website.
Everything about the owner of the car by license plate, phone number or VIN https://avinfo.co or https: //hybd.d.rf/check/auto
Information about individual entrepreneurs and organizations, including the full name of the entrepreneur https://egrul.nalog.ru/index.html
Get an extract from the USRN on the main characteristics and registered rights to the real estate object https://rosreestr.ru/wps/portal/p/cc_present/EGRN_1
You can also use your nickname, for this there are two sites to help you: https://knowem.com or https://namechk.com. Here are a few more sites that allow you to search by nickname according to the same principle:
https://www.namecheckr.comhttp://usersherlock.comhttps://usersearch.orghttps://thatsthem.comhttps://inteltechniques.com
Based on this information, you can see which social networks are occupied with a nickname.
Applications GetContact and Numbuster. They will allow you to determine how this number is recorded in other people's phone books. Ahtung! To use the applications, install them on a phone with an empty contact book, otherwise they will merge your contacts too!
Also install the Viber, Telegram, VK, and WhatsApp applications on your phone. Enter the desired number in the contacts on the phone, and import the contacts into the installed applications. This will allow you to find a person's accounts if his cell phone was used there for registration.
Search for people on social networks:
Search for information about VK records by user ID: https://vk.com/feed?obj=ID&q=§ion=mentions
Searching where else in the vastness of the Internet there is a photo (useful when searching for other social accounts of the object, or the original source of the photo):
Extract EXIF information from a photo (may contain geographic coordinates of the shooting location):
You can search for known database leaks. Very often hackers leak databases with names and passwords, and possibly other data. Other hackers meticulously monitor such leaks and organize these data. Just enter the address or nickname and see the results. For this, these services are suitable:
https://ghostproject.fr
https://haveibeenpwned.com/
https://hacked-emails.com/
https://weleakinfo.com/
https://leakedsource.ru/
Collecting information using other sources
OSINT Framework https://osintframework.com, https://github.com/lockfale/osint-framework
The author created this framework to automate the collection of information from various places and its further systematization. For further work with the framework, you may need to register on which of the resources that it uses, but in general, it is free and allows you to search a large number of resources, as well as google and other publicly available systems, and then systematize this information.
Awesome OSINT URL='https://github.com/jivoi/awesome-osint']https://github.com/jivoi/awesome-osint)[/URL]
No program this time, just a huge list of OSINT resources
Maltego https://paterva.com
An absolutely unrivaled tool for collecting and organizing OSINT data, included with Kali Linux. Nevertheless, even for the community version, the set of functions is very impressive, and all the rest of the systematization can be done either completely by hand, or written (or borrowed or redone ready-made ones).
DataSploit Framework https://github.com/datasploit/datasploit
DataSploit is an OSINT framework written in Python that automatically collects information about domains, email, usernames and phone numbers. You can use DataSploit both inside Python applications or as a standalone tool via the command line.
4. Analysis of results
The information found should be systematized. Better to add notes on during the reset process. For example, if you found something interesting at the stage of collecting information, then you must definitely note it visually. So that at the stage of analysis it can be analyzed in detail and drawn conclusions.
If in the process of collecting information it was possible to find files, then you need to pull out the metadata. To do this, you can use programs such as FOCA, for example. You can also upload data from social networks and continue to work with them.
It is imperative to save correspondence, public messages or records in order to analyze them later. This is very important, because after reading the messages, you can roughly understand the psychological portrait of our target, and then work and use to use the attack.
At the end of this stage, we must have a clear understanding of everything with whom the target interacts, what it does, who it likes on social networks, with whom it communicates, as well as where it rests, what its geo-location is in social networks. Absolutely everything, down to the smallest details.
5. Formation of conclusions and preparation of results
At this stage, we have a so-called person card. We know basic information, we know preferences and interests, social circle, sphere of influence, activity in social networks, as well as on other resources. As a result of such work, one can understand that, in general, a person represents, how much he earns, what assets he has. And depending on this, we can make a start.
For example, if a person is fishing, then you can come up with an interesting story and offer a free outing tour, some super cool book or club membership. It is good to prepare a fake website, create a high-quality letter and send it to the target. You can, for example, ask that in order to get a free trip, you need to register on the site. So, for example, we can get an idea of what passwords our target is using. You can immediately check to see if the same policy is being used across all sites.
It is also very important to revise the roadmap, it will allow us to understand what we have in general and where the person spends the most time. If he communicates on social networks, and actively uploads photos to Instagram from photo exhibitions or from the same bar, then it means that you can very often meet him there. And if you also offer on behalf of the institution some kind of super offer through the mail, then you can meet a person in a specific place and at a specific time. It all depends on your imagination.
Visualization
When working with big data, it's very important to work with visualization. Thus, you can not get confused and get more information. That is why I will show you several services that allow you to implement this function.
Wisemapping http://www.wisemapping.com
A convenient set of icons, there is the possibility of drawing up notes, design, can be divided into levels and sublevels. Finished cards can be discarded for collaboration. There is of course a minus, you can pick up numbers in the link and find other cards.
Mindmeister https://www.mindmeister.com
Free functionality with paid features. There is a standard set of functions: icons, pictures, notes and links. You can work together. Not a bad service with average functionality.
Mindomo https://www.mindomo.com
There are paid features inside, but you can use the free version. Has more functionality for the design and placement of elements. You can use ready-made templates for building maps. You can see an example of ready-made maps at the link.
Maltego https://www.paterva.com
You've probably heard that this is a cool OSINT tool for automating search. It is installed in Kali and the free version is sufficient for use. But it can also be used to build links and visually display information in manual mode. Entities nodes can be used to add people, nicknames, servers, ports, images, and more. But this is a topic for a separate article rather than a paragraph. With the Social Links plugin https://www.mtg-bi.com worth $ 100, this already powerful "harvester" turns into a powerful search tool on social networks and other resources.
Who seeks will always find. And what I wrote about here is just a basic selection with which you can start. I will definitely write in the future about interesting software and new search technologies. Stay with us!
Properly honed information retrieval skills are essential. This knowledge is especially important when you collect information about a person or company, or you need to check important information. Wondering how to do this? Then today we'll talk about OSINT.
What is OSINT?
OSINT (Open Source Intelligence) - search, collection and analysis of information received from publicly available sources. For example, getting information from social networks, personal sites and forums, as well as from search engines. To better understand the essence of this term, let's look at examples.
If you look at history, one of the famous CIA analysts, Ken Sherman, stated that the state gets more than 80% of the information it needs from open sources. A little later, the head of the US Defense Intelligence Agency, Samuel Wilson, said that more than 90% of all intelligence data is in open sources, the rest is the success of agents. Statistics captures and confirms the relevance of OSINT.
In our age of Internet accessibility, there are a lot of search opportunities in open sources. An ordinary user tells a lot of information about himself: connections with other people, profiles on social networks, interests, geolocation, marital status, etc. Using such sources to collect information is OSINT.
Why don't most users know how to search for information?
Using open source search, you can solve more than one mystery of private detectives. After all, there are a lot of open government resources, forums, social networks and other sources for finding information around. But it is very important not to get confused in all this and learn to find the most important thing in order to find a real treasure among the tons of sand.
Beginners do not always correctly perceive the information received. Let's say there are some records, photos, the user lives like everyone else, and he has nothing serious. But if you dig deeper, analyze the activity, groups, geotags, comments, and also check the nickname for being busy on other services? After completing such a simple list, you can find a lot of interesting information. But that's not all either.
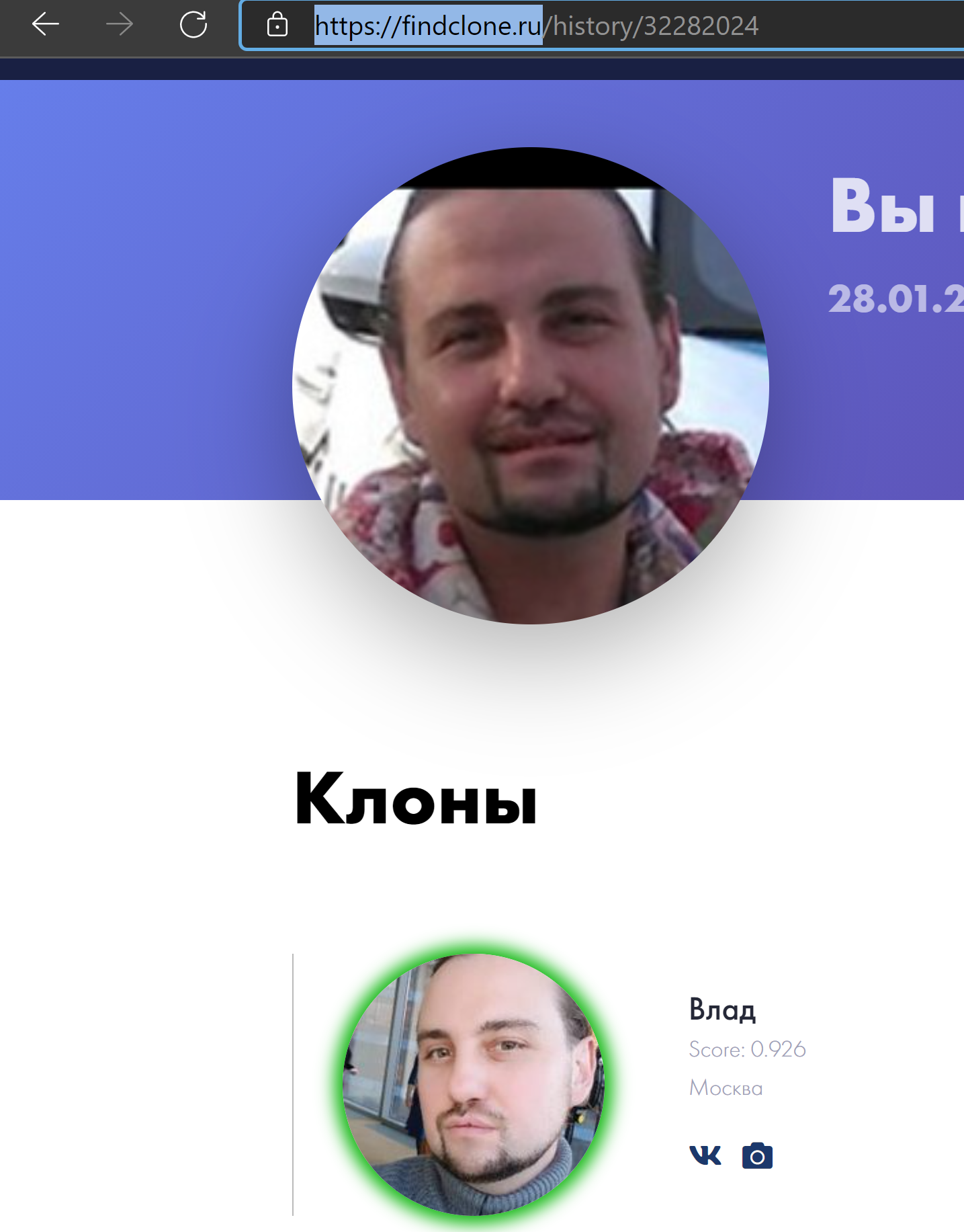
Let's take a look at the case. Let's imagine that there is a user Vasya from St. Petersburg, he is registered in Vkontakte and Facebook. Minimum information and photos, boring profile, nothing special. And now let's imagine that after a slash in the VK address bar his nickname vasechka66 is written. And having broken through such information, you can find an active user on forums with a similar place of residence. And this is more interesting, because here Vanya posts photos from his vacation, openly communicates about his political views, and also publishes incredible stories from his life. This is the beauty of OSINT.
How to approach open data search in a structured way?
This is not an exhaustive list and the methods I have described are not redundant. However, for beginners, this can serve as a starting point. And then - there is no limit to perfection.
For convenience, we have divided the entire process into stages.
1. Formation of tasks
At this stage, you need to clearly understand what you need to get in the end. This can be, for example, the nicknames that the target uses. Or you need to break through absolutely all the information about a person on the Internet. Typically, the key data for sending are phone numbers, email addresses, nicknames, or social media leads.
Stage 2. Planning
At this stage, you need to determine all possible directions and sources that will be used for the search. As a rule, there are 3 main ones:
Personal (social networks, blogs, websites, nicknames, etc.).
State (registers, bases, courts, taxes, border bases, diploma bases, base of invalid passports, etc.).
External sources (friends, acquaintances, media, employers, recommendations).
It is very important to visualize. The best way to do this is to use XMind, MindMap, Maltego or other similar apps. For each goal, you need to make your own roadmap.
3. Gathering information
This stage is the most time consuming, but it is mainly implemented using a set of software and online services. As you approach this stage, you should have some preliminary information. For example, you know that a person uses the last name of their first teacher as their password. And, let's say, our victim has it as a friend on VKontakte. This significantly narrows the circle and it becomes clear where to look first.
But sometimes there is no such information and you need to search for absolutely everything. It's best to start with your first name, last name and nickname first. Then you can promote and search for a phone number, a list of friends, build connections in social networks and forums. But as practice shows, almost all search results are based on three things: phone number, email and nickname.
Here we have compiled a small selection of resources and sites that you can search for.
Search by home phone, full name and city or address of residence http://spra.vkaru.net or http://nomerorg.me. Attention, you can search here if a person has a home or office number. The service does not search for SIP, mobile, etc.
Special sites. For example, the search engines Shodan and Censys. This will be relevant if you have the target IP address.
Search in court cases of the Russian Federation https://sudrf.ru/index.php?id=300
Base of diplomas http://frdocheck.obrnadzor.gov.ru
Base of bailiffs http://fssprus.ru/iss/ip/
Base of invalid passports http://services.fms.gov.ru/info-service.htm?sid=2000
TIN database https://service.nalog.ru/static/personal-data.html?svc=inn
As well as many other tax data available on the same website.
Everything about the owner of the car by license plate, phone number or VIN https://avinfo.co or https: //hybd.d.rf/check/auto
Information about individual entrepreneurs and organizations, including the full name of the entrepreneur https://egrul.nalog.ru/index.html
Get an extract from the USRN on the main characteristics and registered rights to the real estate object https://rosreestr.ru/wps/portal/p/cc_present/EGRN_1
You can also use your nickname, for this there are two sites to help you: https://knowem.com or https://namechk.com. Here are a few more sites that allow you to search by nickname according to the same principle:
https://www.namecheckr.comhttp://usersherlock.comhttps://usersearch.orghttps://thatsthem.comhttps://inteltechniques.com
Based on this information, you can see which social networks are occupied with a nickname.
Applications GetContact and Numbuster. They will allow you to determine how this number is recorded in other people's phone books. Ahtung! To use the applications, install them on a phone with an empty contact book, otherwise they will merge your contacts too!
Also install the Viber, Telegram, VK, and WhatsApp applications on your phone. Enter the desired number in the contacts on the phone, and import the contacts into the installed applications. This will allow you to find a person's accounts if his cell phone was used there for registration.
Search for people on social networks:
- http://people.yandex.ru
- https://vk.com/people
- https://bazaman.ru/
- https://www.facebook.com/friends/requests/
- https://twitter.com/search-advanced
- http://pipl.com
- https://www.spokeo.com/
Search for information about VK records by user ID: https://vk.com/feed?obj=ID&q=§ion=mentions
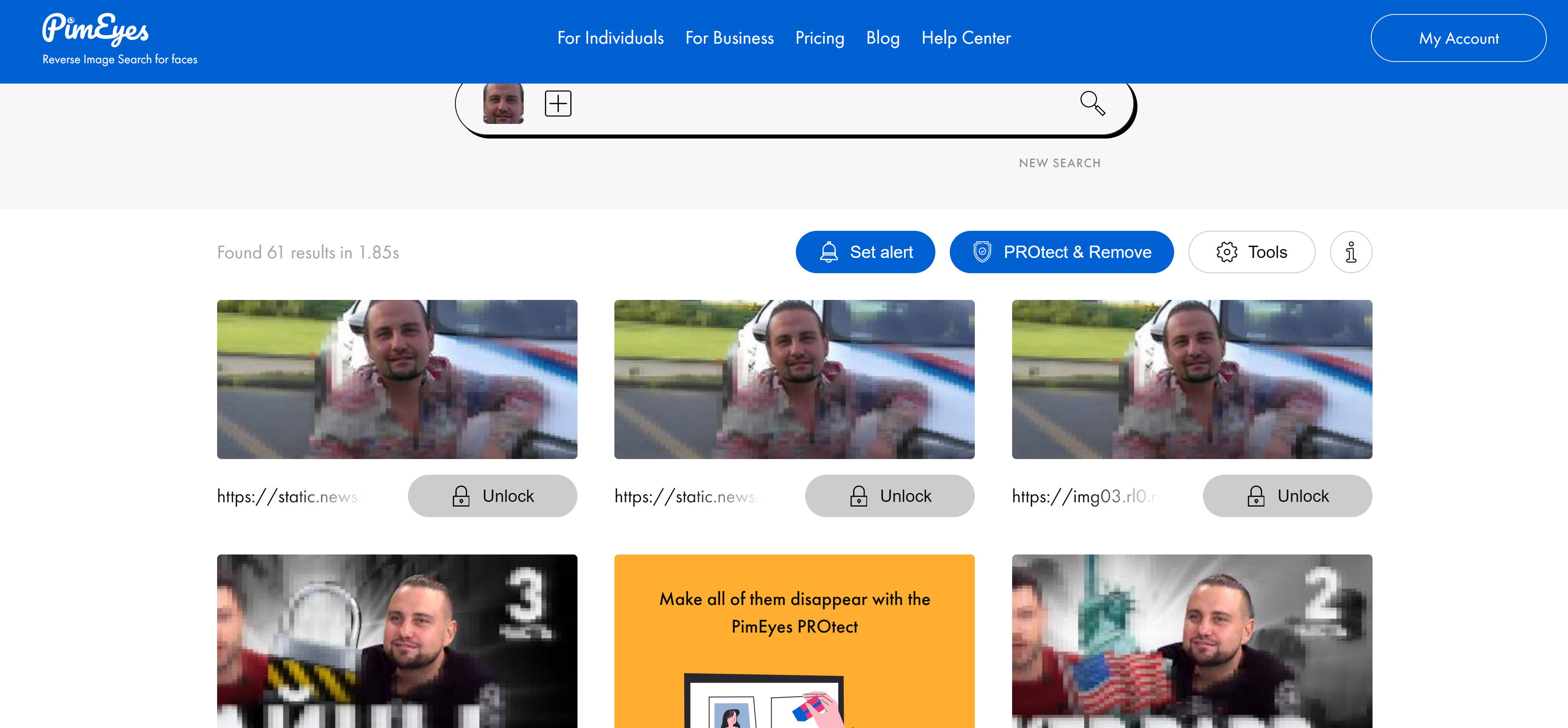
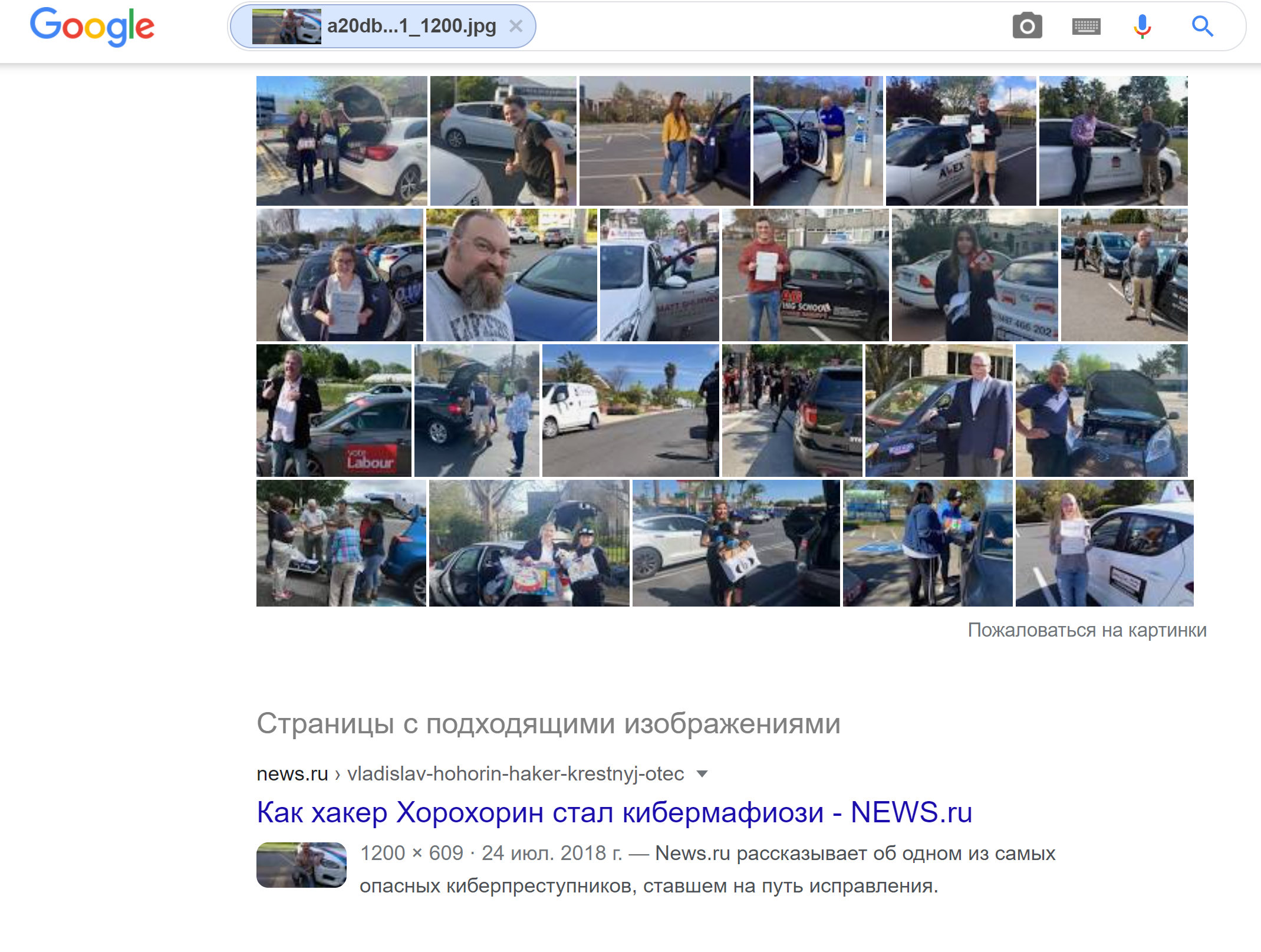
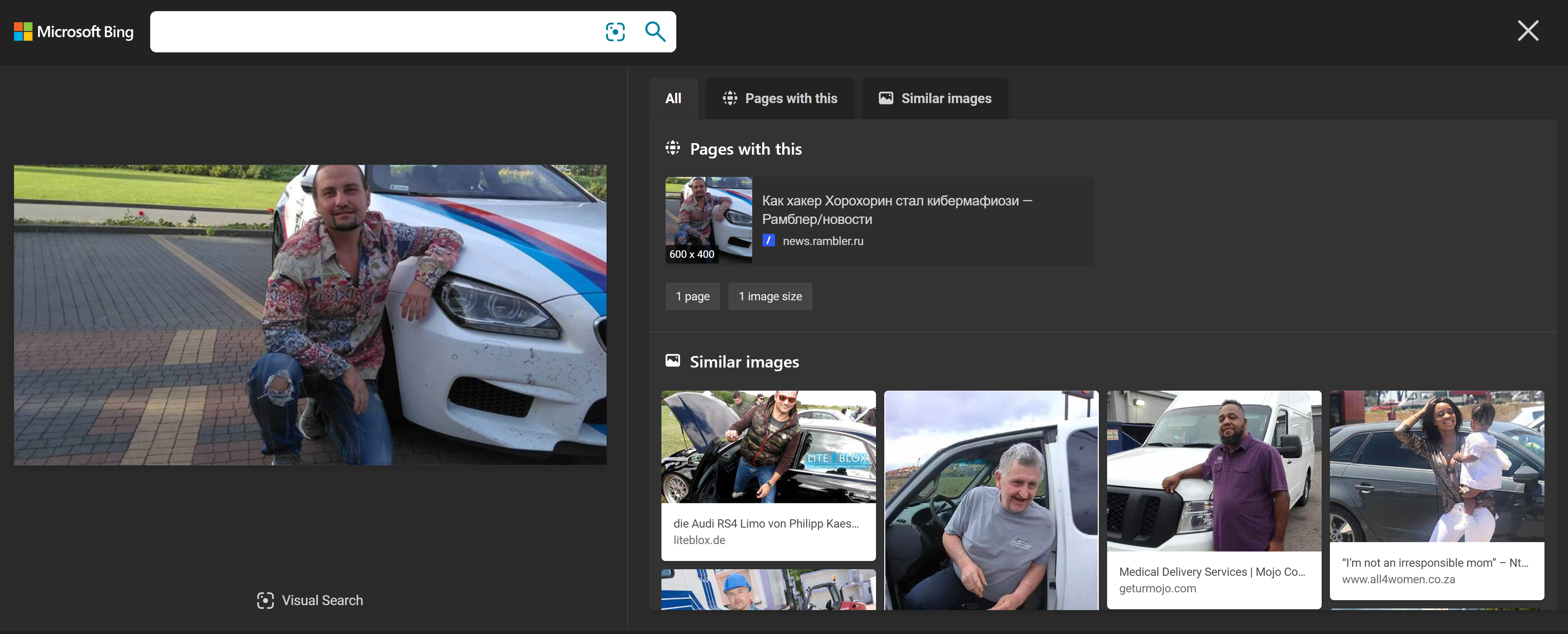
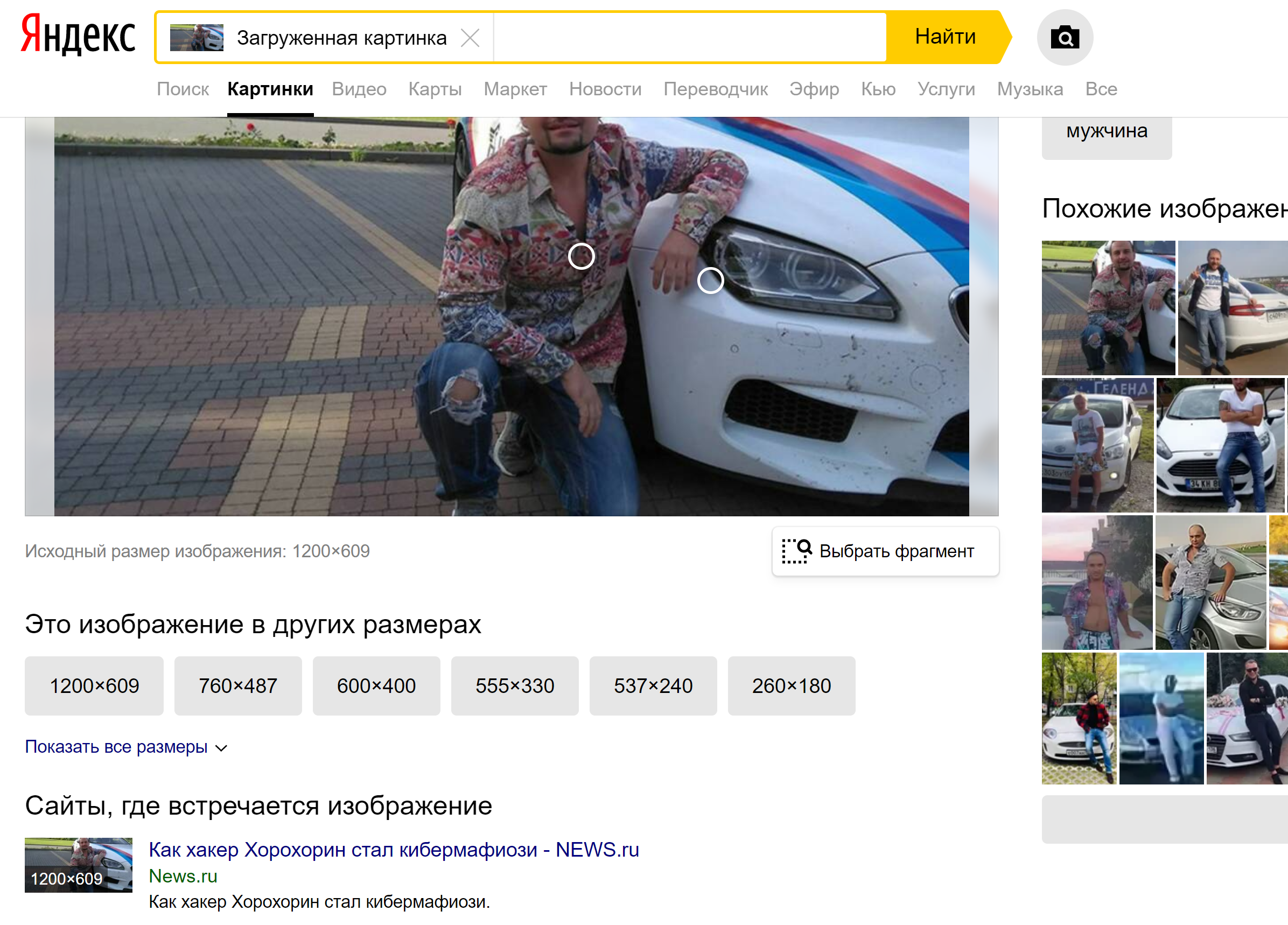
Searching where else in the vastness of the Internet there is a photo (useful when searching for other social accounts of the object, or the original source of the photo):
- https://images.google.com
- https://yandex.ru/images
- https://www.tineye.com
- https://findmevk.com
- https://vlicco.ru
- https://searchface.ru
- https://findface.pro
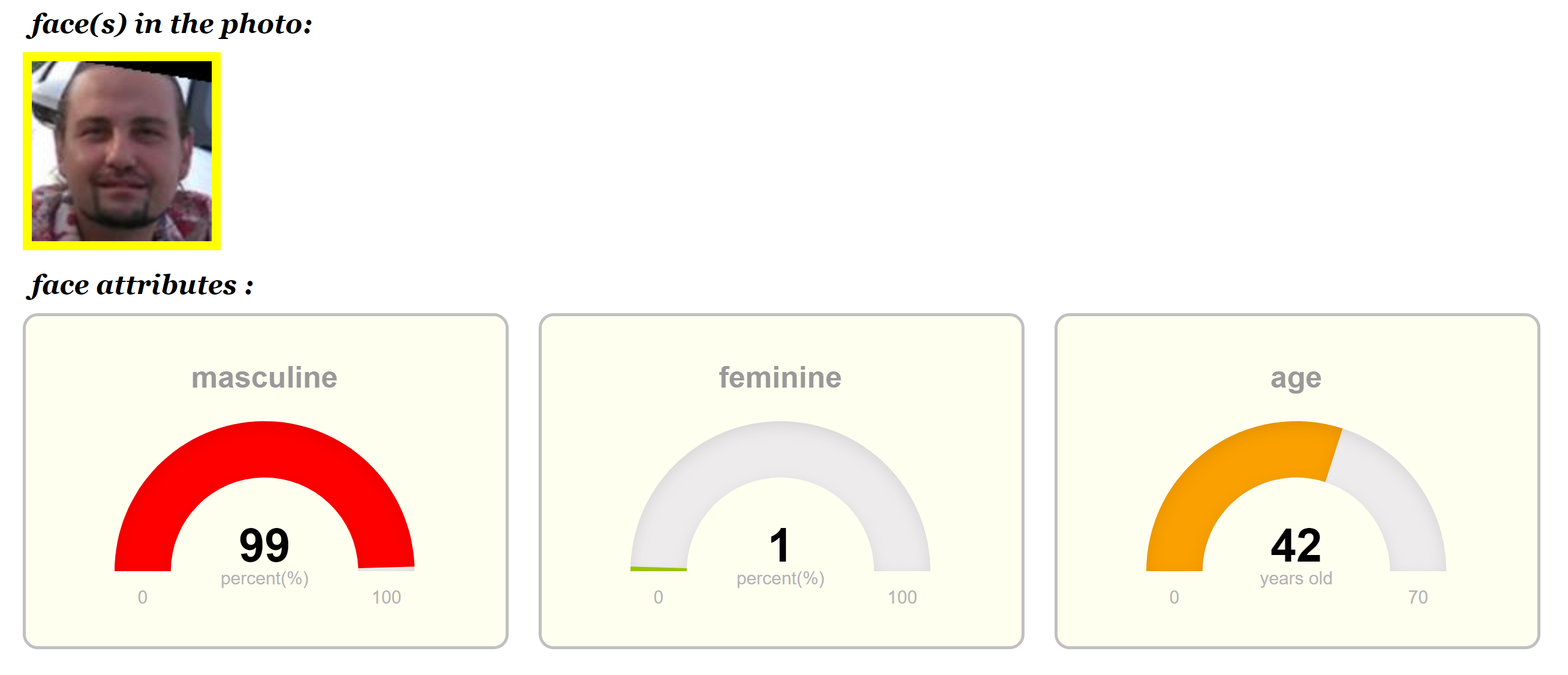
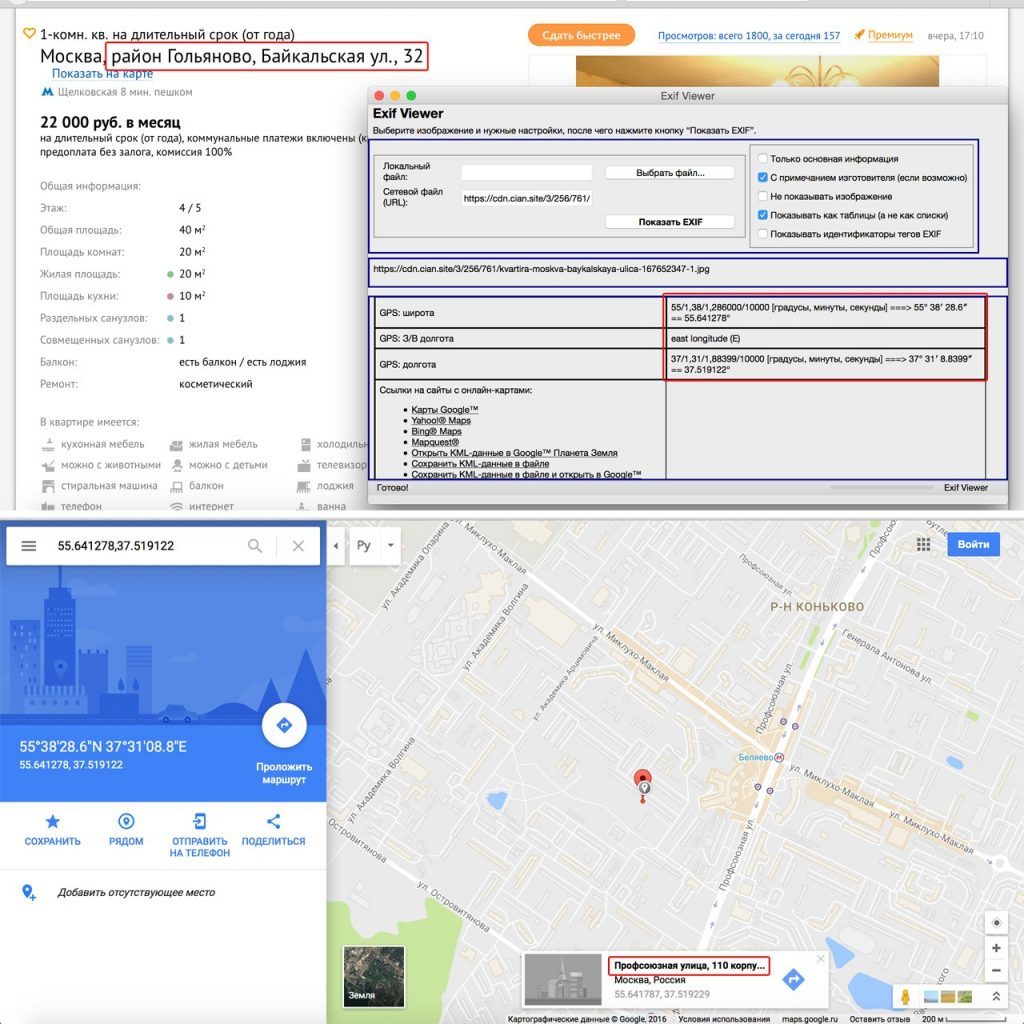
Extract EXIF information from a photo (may contain geographic coordinates of the shooting location):
You can search for known database leaks. Very often hackers leak databases with names and passwords, and possibly other data. Other hackers meticulously monitor such leaks and organize these data. Just enter the address or nickname and see the results. For this, these services are suitable:
https://ghostproject.fr
https://haveibeenpwned.com/
https://hacked-emails.com/
https://weleakinfo.com/
https://leakedsource.ru/
Collecting information using other sources
OSINT Framework https://osintframework.com, https://github.com/lockfale/osint-framework
The author created this framework to automate the collection of information from various places and its further systematization. For further work with the framework, you may need to register on which of the resources that it uses, but in general, it is free and allows you to search a large number of resources, as well as google and other publicly available systems, and then systematize this information.
Awesome OSINT URL='https://github.com/jivoi/awesome-osint']https://github.com/jivoi/awesome-osint)[/URL]
No program this time, just a huge list of OSINT resources
Maltego https://paterva.com
An absolutely unrivaled tool for collecting and organizing OSINT data, included with Kali Linux. Nevertheless, even for the community version, the set of functions is very impressive, and all the rest of the systematization can be done either completely by hand, or written (or borrowed or redone ready-made ones).
DataSploit Framework https://github.com/datasploit/datasploit
DataSploit is an OSINT framework written in Python that automatically collects information about domains, email, usernames and phone numbers. You can use DataSploit both inside Python applications or as a standalone tool via the command line.
4. Analysis of results
The information found should be systematized. Better to add notes on during the reset process. For example, if you found something interesting at the stage of collecting information, then you must definitely note it visually. So that at the stage of analysis it can be analyzed in detail and drawn conclusions.
If in the process of collecting information it was possible to find files, then you need to pull out the metadata. To do this, you can use programs such as FOCA, for example. You can also upload data from social networks and continue to work with them.
It is imperative to save correspondence, public messages or records in order to analyze them later. This is very important, because after reading the messages, you can roughly understand the psychological portrait of our target, and then work and use to use the attack.
At the end of this stage, we must have a clear understanding of everything with whom the target interacts, what it does, who it likes on social networks, with whom it communicates, as well as where it rests, what its geo-location is in social networks. Absolutely everything, down to the smallest details.
5. Formation of conclusions and preparation of results
At this stage, we have a so-called person card. We know basic information, we know preferences and interests, social circle, sphere of influence, activity in social networks, as well as on other resources. As a result of such work, one can understand that, in general, a person represents, how much he earns, what assets he has. And depending on this, we can make a start.
For example, if a person is fishing, then you can come up with an interesting story and offer a free outing tour, some super cool book or club membership. It is good to prepare a fake website, create a high-quality letter and send it to the target. You can, for example, ask that in order to get a free trip, you need to register on the site. So, for example, we can get an idea of what passwords our target is using. You can immediately check to see if the same policy is being used across all sites.
It is also very important to revise the roadmap, it will allow us to understand what we have in general and where the person spends the most time. If he communicates on social networks, and actively uploads photos to Instagram from photo exhibitions or from the same bar, then it means that you can very often meet him there. And if you also offer on behalf of the institution some kind of super offer through the mail, then you can meet a person in a specific place and at a specific time. It all depends on your imagination.
Visualization
When working with big data, it's very important to work with visualization. Thus, you can not get confused and get more information. That is why I will show you several services that allow you to implement this function.
Wisemapping http://www.wisemapping.com
A convenient set of icons, there is the possibility of drawing up notes, design, can be divided into levels and sublevels. Finished cards can be discarded for collaboration. There is of course a minus, you can pick up numbers in the link and find other cards.
Mindmeister https://www.mindmeister.com
Free functionality with paid features. There is a standard set of functions: icons, pictures, notes and links. You can work together. Not a bad service with average functionality.
Mindomo https://www.mindomo.com
There are paid features inside, but you can use the free version. Has more functionality for the design and placement of elements. You can use ready-made templates for building maps. You can see an example of ready-made maps at the link.
Maltego https://www.paterva.com
You've probably heard that this is a cool OSINT tool for automating search. It is installed in Kali and the free version is sufficient for use. But it can also be used to build links and visually display information in manual mode. Entities nodes can be used to add people, nicknames, servers, ports, images, and more. But this is a topic for a separate article rather than a paragraph. With the Social Links plugin https://www.mtg-bi.com worth $ 100, this already powerful "harvester" turns into a powerful search tool on social networks and other resources.
Who seeks will always find. And what I wrote about here is just a basic selection with which you can start. I will definitely write in the future about interesting software and new search technologies. Stay with us!