BadB
Professional
- Messages
- 2,488
- Reaction score
- 2,536
- Points
- 113
You may have already used the Tails distribution or even run it daily. But this is not the only operating system that can hide your presence on the network and help bypass regional blockages. In this article, we'll explore five of Tails' competitors, each with interesting features.
Components of privacy
An experienced Linux hacker will independently make an operating system to fit his needs, stuff it with his favorite tools and encrypt every bit. However, this will take a lot of time, and therefore this method is suitable only for the most red-eyed. For everyone else, there are ready-made options in which thousands of little things have already been thought out, proven privacy protection tools have been collected and configured.Despite the external diversity, these distributions have many similarities, since the preservation of privacy is built on the same approaches. Ensuring privacy consists of the following stages, which are solved at the local and network level:
- guaranteed removal of traces of work and any unique (and therefore potentially compromising) data used during the session;
- encryption of the data that needs to be saved (for example, electronic wallets, documents, audio and video recordings, other personal files and configs);
- hiding the very fact of storing encrypted data (using steganography methods and disguising them among more visible crypto-containers, which obviously do not contain valuable information);
- isolation of applications and the allocation of some services into separate virtual machines (sandbox, Xen, VirtualBox and other virtualization tools) to reduce the likelihood of deanonymization when infected with a Trojan;
- kernel patches for increased control over the interaction of processes and minimizing the risk of deanonymization through exploits;
- means of emergency shutdown of the OS with quick removal of the most compromising data in case of a threat of physical seizure of the boot drive;
- early spoofing of the MAC address of network devices (usually it occurs even at the boot stage);
- preventing IP address disclosure (monitoring VPN status, anti DNS leak, filtering scripts, using a chain of proxy servers with high anonymity, proxying the traffic of all applications through Tor, etc.);
- implementation of anonymous communication channels (chats, mail, file exchange);
- bypassing regional blocking (automatic configuration of the use of public DNS servers, free VPNs, fast proxies, Tor, I2P, Freenet).
Kodachi
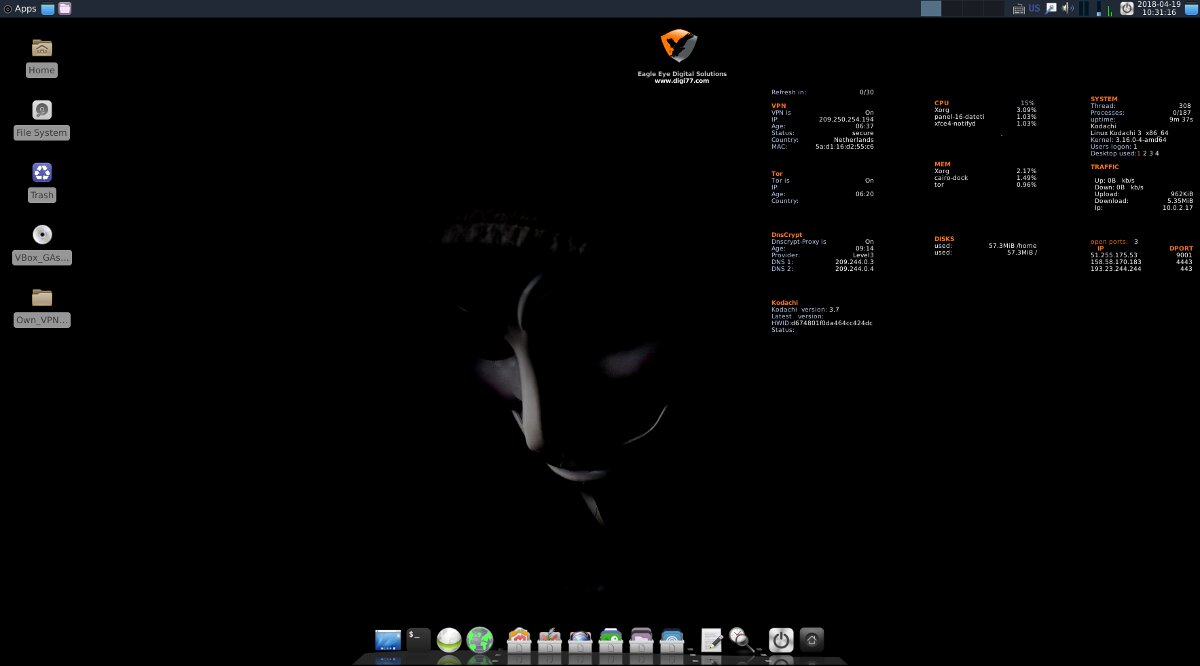
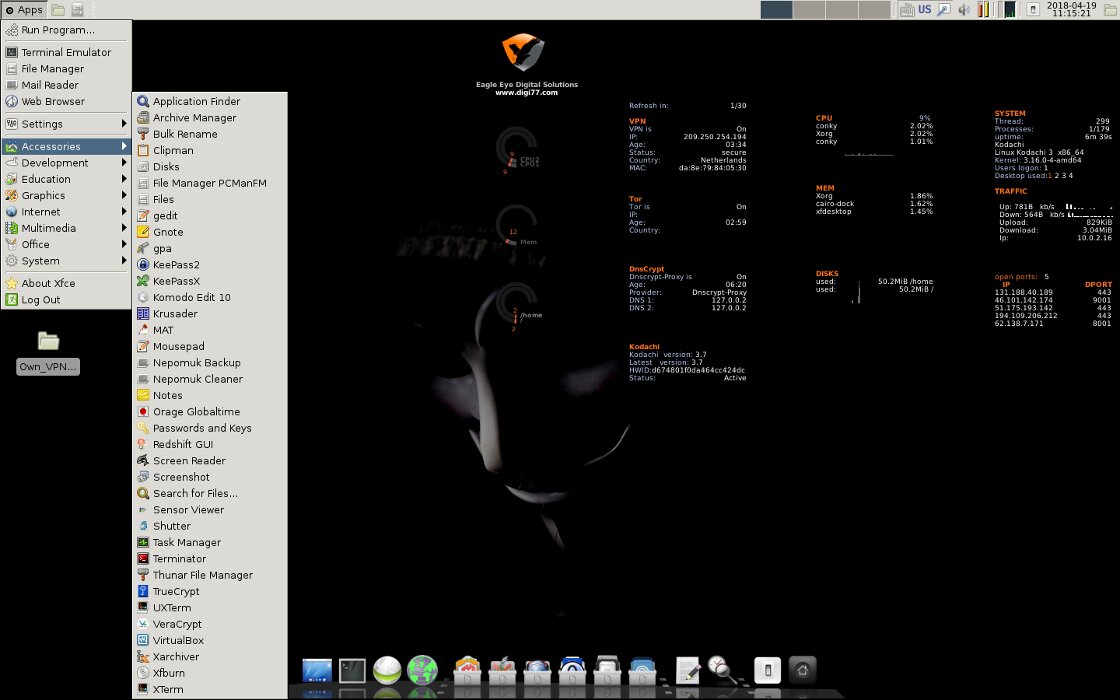
In the last issue, we analyzed distributions for forensics, and Kodachi is positioned as an anti-forensic development that makes it difficult to forensic analysis of your drives and RAM. Technically, this is another privacy-focused fork of Debian. In some ways, it is even more thoughtful than the popular Tails.The latest stable release of Kodachi 3.7 was written in January last year. The operating system comes from Oman (where they are familiar with Internet censorship), which adds color to it.
Xfce was chosen as the desktop environment for Kodachi, and the general operating system interface was stylized for macOS. Tor and VPN connection status, as well as most of the current system boot parameters, are displayed in real time and displayed right on the desktop.

Kodachi GUI
Key features of Kodachi include forced tunneling of traffic through Tor and VPN, with a free VPN already set up.
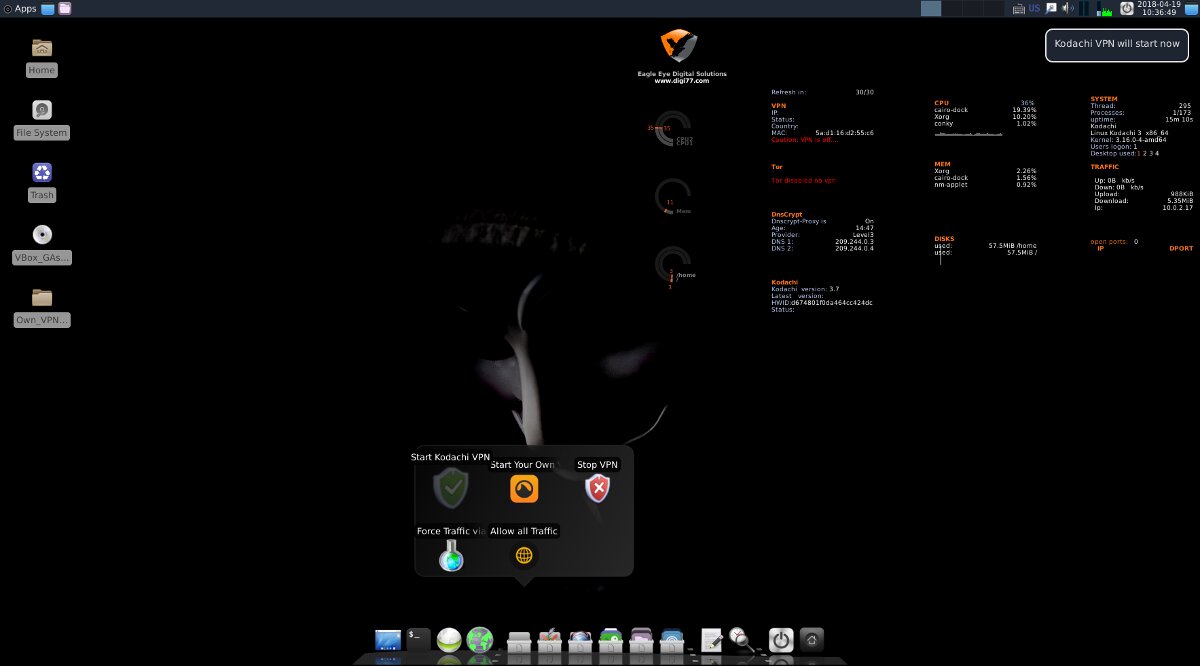
Launching Kodachi VPN
Plus, Kodachi integrates support for DNScrypt, a protocol and utility of the same name that encrypts requests to OpenDNS servers using elliptic cryptography. It eliminates a number of common problems, such as DNS leaks and network traces on the ISP's servers.
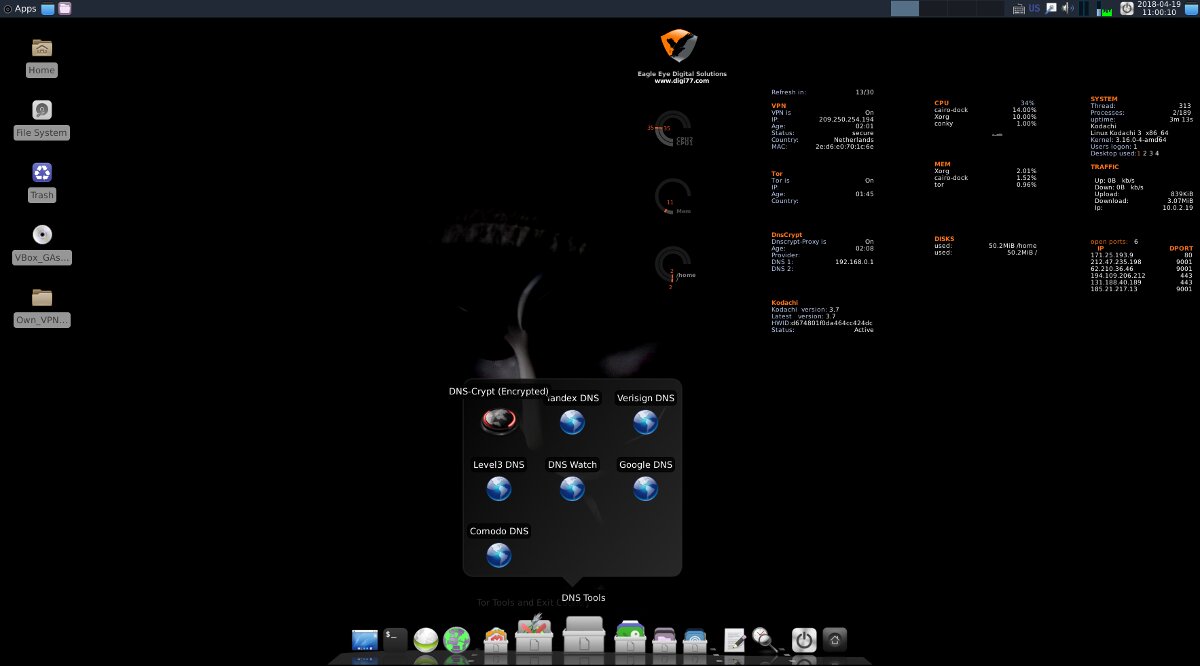
Kodachi DNS tools
Another difference of Kodachi is the integrated Multi Tor for quick change of exit nodes with the choice of a specific country and PeerGuardian for hiding its IP address in P2P networks (as well as blocking network nodes from a long black list).
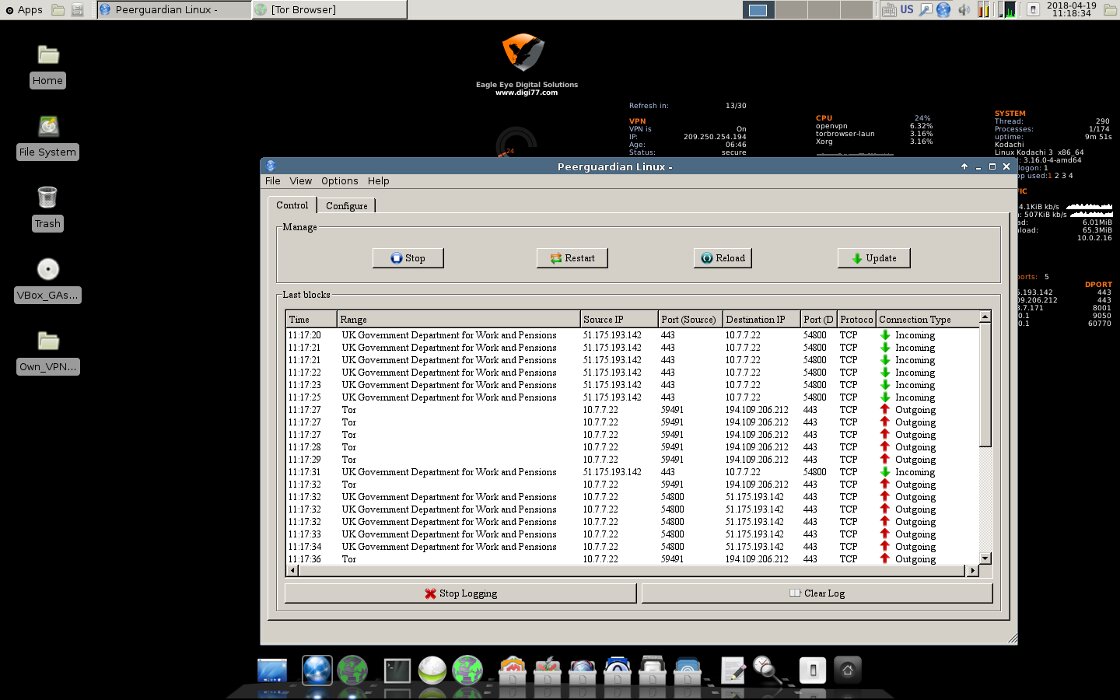
PeerGuardian
In addition to PeerGuardian, the Uncomplicated Firewall (uwf) with a graphical shell is used as a firewall guwf.
Applications in Kodachi are easy to isolate using the built-in Firejail sandbox (we already talked about it ). It is especially recommended to do this for the browser, mail and messenger.

Firejail sandbox
The operating system is tightly packed with cryptography (TrueCrypt, VeraCrypt, KeePass, GnuPG, Enigmail, Seahorse, GNU Privacy Guard Assistant) and trail-covering (BleachBit, Nepomuk Cleaner, Nautilus-wipe).
A set of preinstalled utilities

Built-in system applications
Kodachi provides protection against cold boot attacks. During a cold boot attack, you can partially recover data that was recently (seconds ago) stored in RAM. To avoid this, Kodachi overwrites the RAM with random data when the computer is turned off.
Rapid response tools are collected in the section Panic room. It has programs for wiping data on disk and in RAM, restarting network connections, locking the screen (xtrlock), and even a command to completely destroy the operating system.
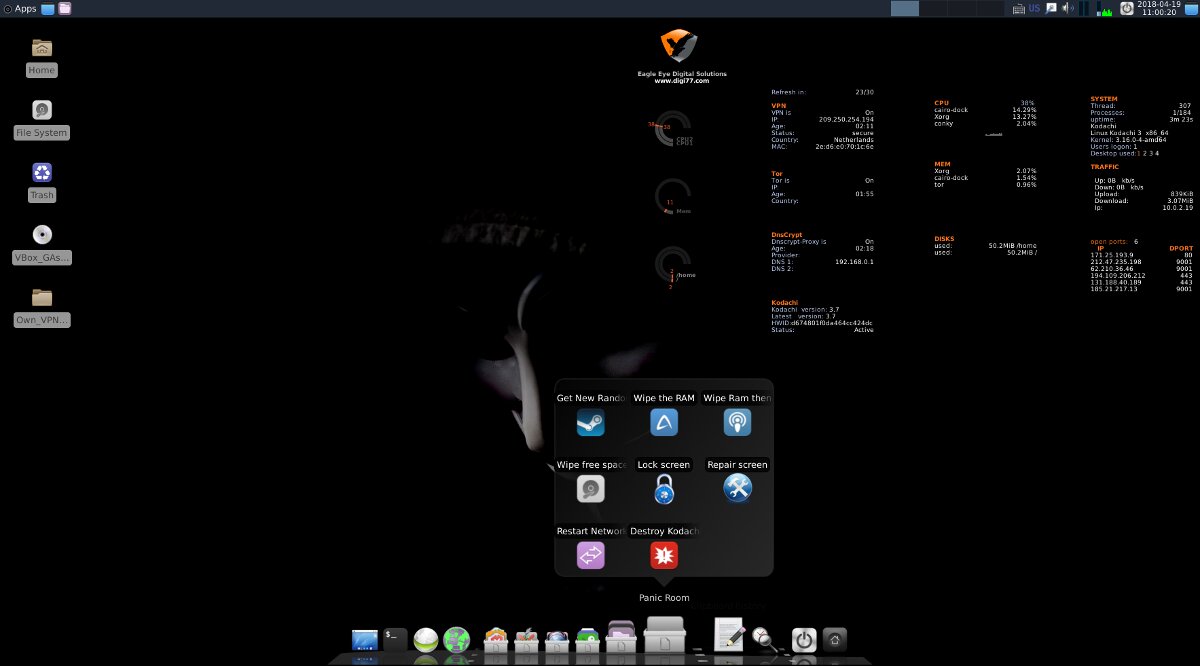
Paranoid set
Kodachi works with USB-Flash like a typical Live distribution (so as not to leave traces on the local computer), but if you want, you can run it in a virtual machine (if you trust the main OS). In any case, by default, you are logged in as a user with a name kodachi and password r@@t00. To use sudo, enter username root and the same password r@@t00.
MOFO Linux
It is a fast growing and heavily stuffed Ubuntu based OS. Out of the box, it offers SoftEther VPN and OpenVPN with automatic detection of the fifteen fastest (not necessarily closest to you) free servers. Indicates their ping to you, to google.com and the bandwidth of the channel.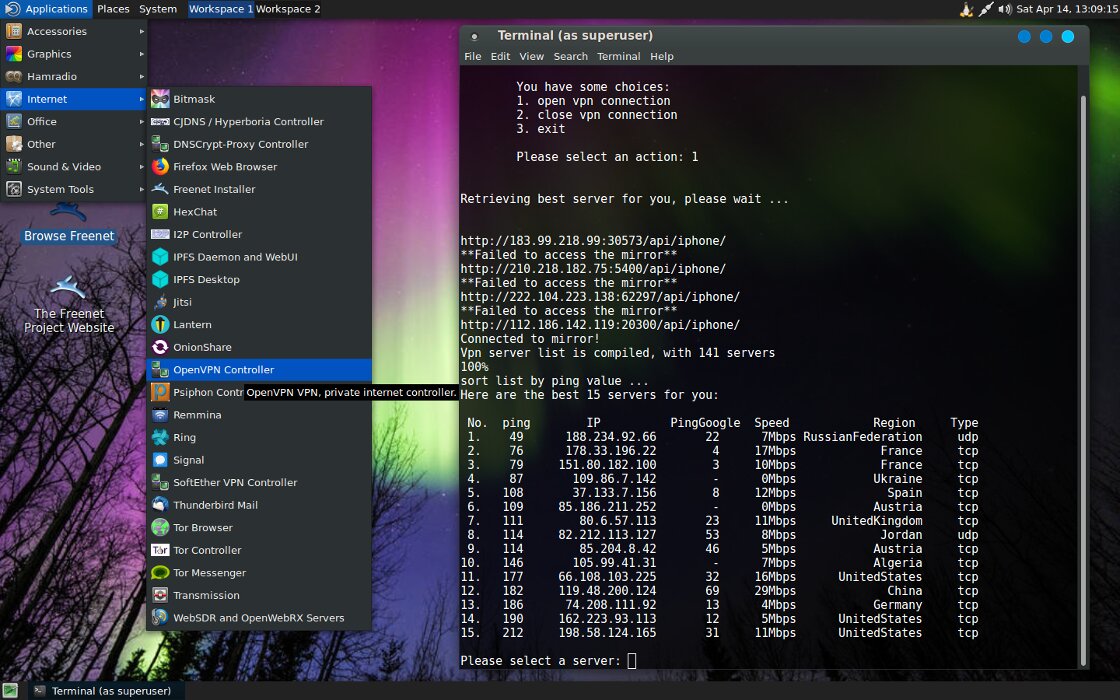
OpenVPN setup
Besides Tor and VPN, MOFO supports I2P plus Lantern and Psiphon as fast proxies. True, now Psiphon is buggy, and Lantern has only 500 MB per month for a free plan without speed limit, but you can always buy a paid account.
The Freenet client, a peer-to-peer anonymous network with distributed encrypted data storage, is installed directly from the graphical menu in a couple of clicks. It has its own sites and forums, which are almost impossible to censor.
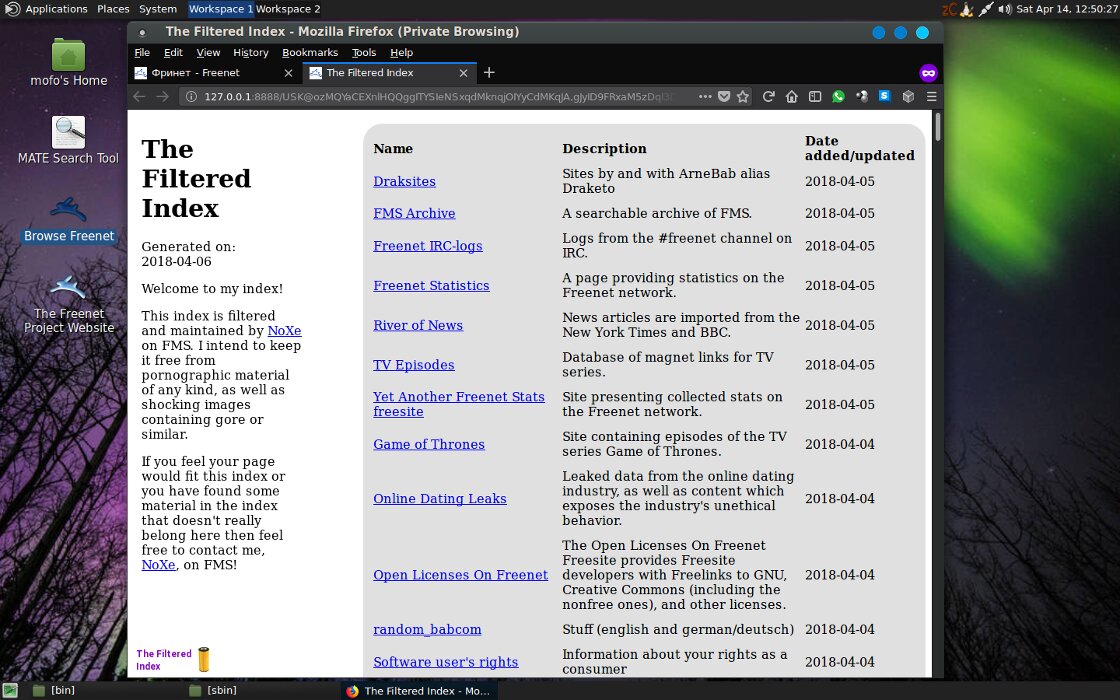
MOFO adds a link to install the Interplanetary File System (IPFS) support package based on P2P technologies. Thanks to IPFS, you can share local files and create sites that will not disappear due to blocking (we have already written about IPFS). MOFO also supports the Cjdns networking protocol. It can be used to create a virtual IPv6 network with traffic encryption.
Installing IPFS
Cryptographic protection of personal data in MOFO is provided by eCryptfs - a multi-layered file system with on-the-fly encryption. It works on top of an existing file system (ext3, ext4 or XFS) and does not require a special partition.
Turn on encryption
Additionally, MOFO comes preinstalled with the ZuluCrypt utility with support for the TrueCrypt and VeraCrypt encrypted containers.
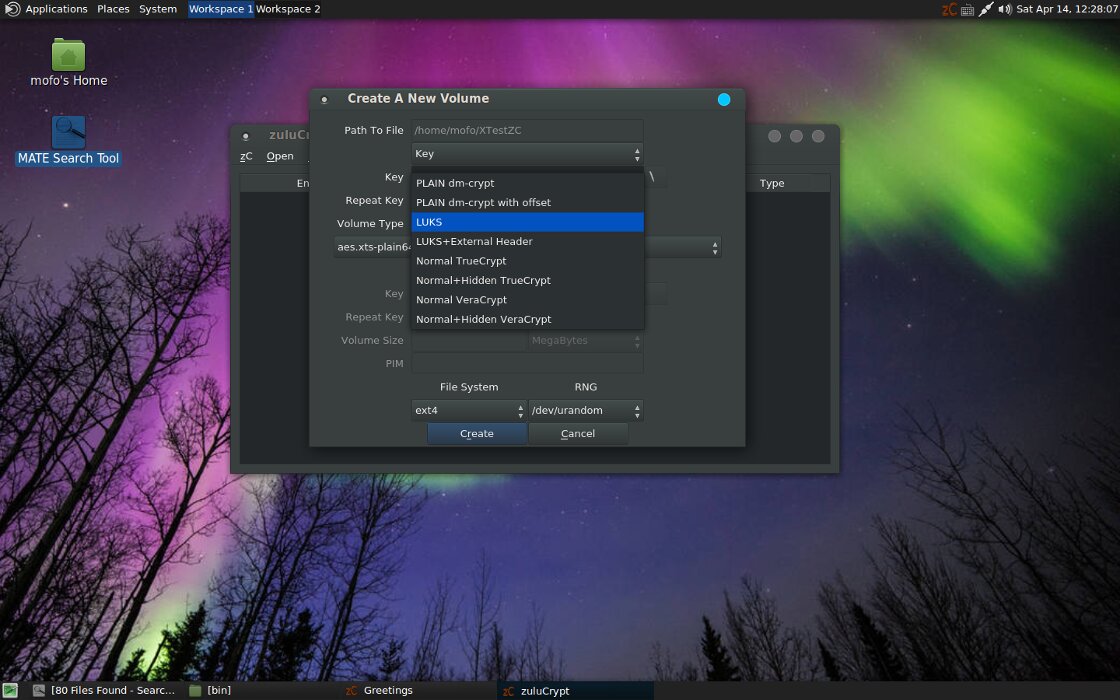
ZuluCrypt - Encrypted Volumes Variants
At the time of testing, version mofolinux-6.0 dated February 18, 2021 was available. By default, no administrator password is set.
Subgraph OS
We wrote about this operating system in 2020, and since then, little has changed. This is still a very crude Debian fork that once praised Snowden for the idea, but not for the implementation. The only thing that has changed noticeably in Subgraph is the list of pre-installed software.
Integrated utilities in Subgraph OS
The latest version is now September 2021 alpha. It can run in Live mode, but for full operation it requires installation on a hard drive.
A key feature of Subgraph OS is the Oz sandbox application launcher. It isolates selected applications from each other and from the main system using namespaces and enforces restrictions using seccomp-bpf, just like the already mentioned Firejail.
Subgraph OS kernel compiled with PaX / Grsecurity patches. They restrict file access /proc, use tighter chroot () isolation, include more advanced ASLR address space randomization, mark the stack as non-executable, and control network socket allocation.
Subgraph OS is installed on an encrypted partition, has the means to allow / deny application access to the network, and supports YubiKey hardware keys with one-time passwords.
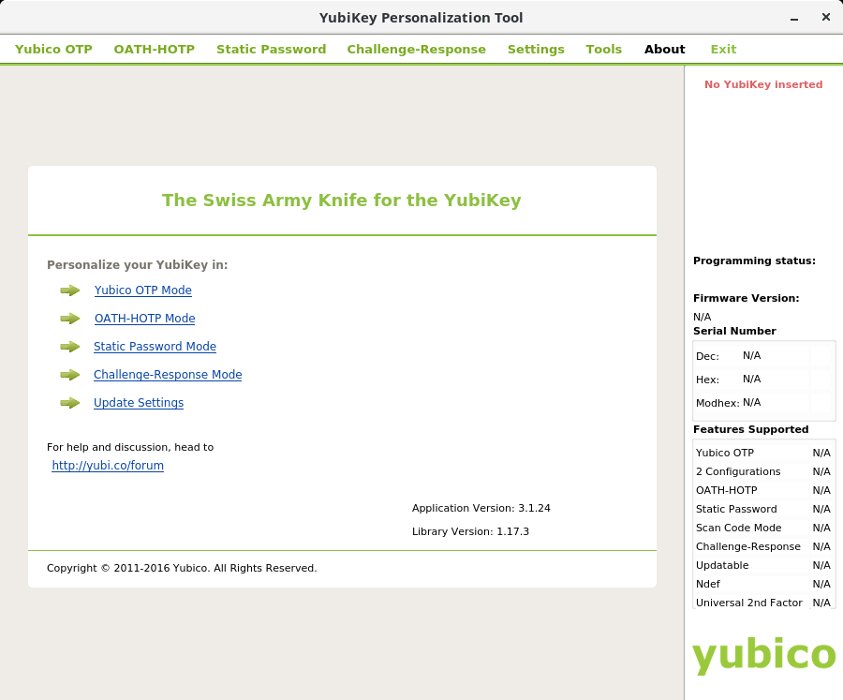
YubiKey PT in Subgraph OS
Email is protected with PGP, and a built-in firewall routes all outgoing connections through the Tor anonymous network.
The integrated Subgraph OS Instant Messenger is an XMPP fork of CoyIM that also works over Tor by default.
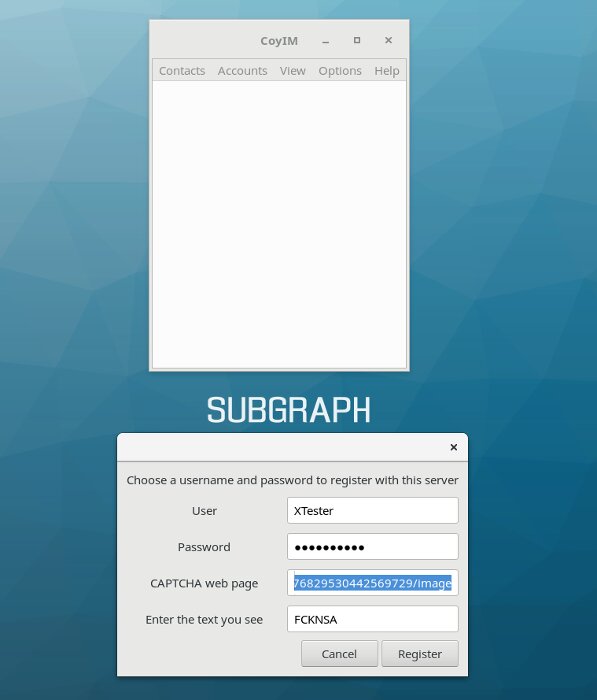
Anonymous messenger Subgraph OS
The creation of anonymous file shares is available through OnionShare, but the utility works in the same way in other versions of Linux.
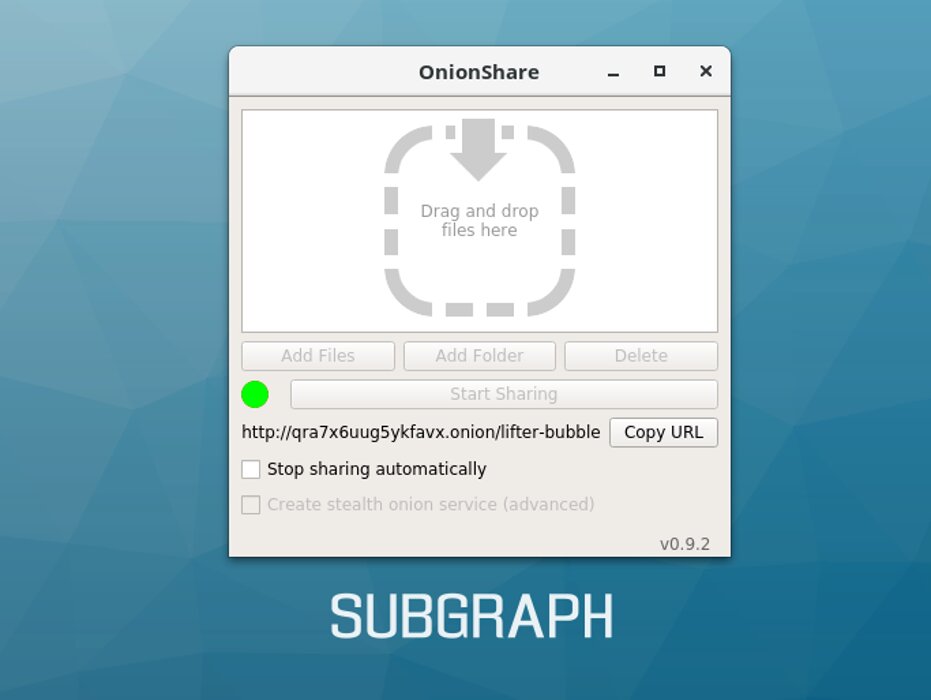
OnionShare in Subgraph OS
At first glance, it may seem that everything is fine in Subgraph OS and it is a really decent OS, but in reality everything is much more complicated. The built-in sandbox only runs certain applications. There is a list of applications that automatically fall into the sandbox, the rest, including the GNOME desktop, run like regular applications in any other Linux distribution.
This architecture opens up many paths to compromise the operating system. For example, Tor Browser runs in a sandbox, but has full directory access ~/Downloads (to save downloaded files). If a hole is found in the browser and an attacker finds a way to use it to launch an exploit, he can write to ~/Downloads whatever he wants, including, for example, a .desktop. Any script can be placed in such a file, and it will be executed when the user switches to the directory ~/Downloads and clicks on it. And since the Nautilus file manager working outside the sandbox is used to navigate the FS in Subgraph OS, the script will have access to the entire system.
In April 2021, Micah Lee and Joanna Rutkowska (creator of Qubes OS) took advantage of this misunderstanding by performing an illustrative Subgraph OS hack.
Heads
The relatively new operating system is called that way - heads with a lowercase letter. A short explanation of the developer is written in the FAQ on this matter: "because I said so." The rest of the answers in it are no more meaningful. The project is young, it develops on sheer enthusiasm, and therefore there is not enough documentation.At the time of this writing, version 0.4 of March 26, 2018 was available on the official website. Technically, this is a fork based on Devuan, which in turn is a fork of Debian with the SysVinit init daemon instead of SystemD.
Heads only supports i386, x86_64 processor architectures, so it is not suitable for use on mobile devices with ARM processors. As a graphical shell, heads offers the Awesome tile window manager, which implements fast window management from the keyboard. Openbox is available as a more familiar alternative.
The set of utilities in heads is very modest. There is a browser, mail, chat, cryptocurrency wallet and a couple of programs for working with different types of files.
Minimalism heads
On the other hand, Tor starts very quickly because of its lightness, and you can use the browser almost immediately.
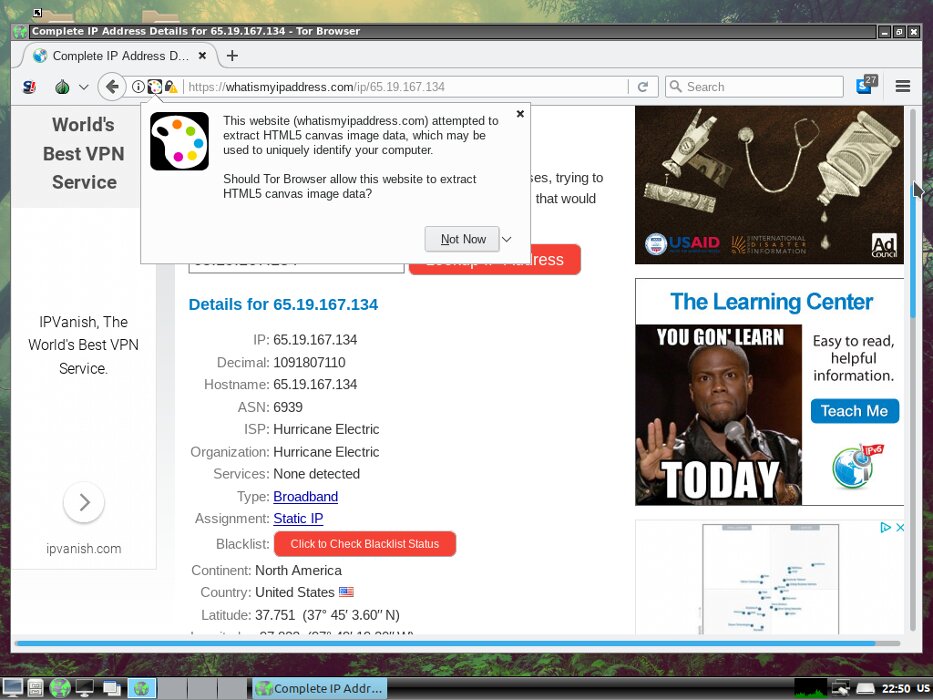
Tor browser
The key features of heads are deep Tor integration and free software only. All traffic (not just browser traffic) to heads goes through Tor. The heads site is also available on Tor.
Additionally, heads can spoof the MAC address at startup, and the Permakey kernel module automatically shuts down the OS when the bootable flash drive is removed (useful in case of a hurry). You can disable this behavior by checking the appropriate boxes at the start of the operating system. There, at the start, the administrator password is set.
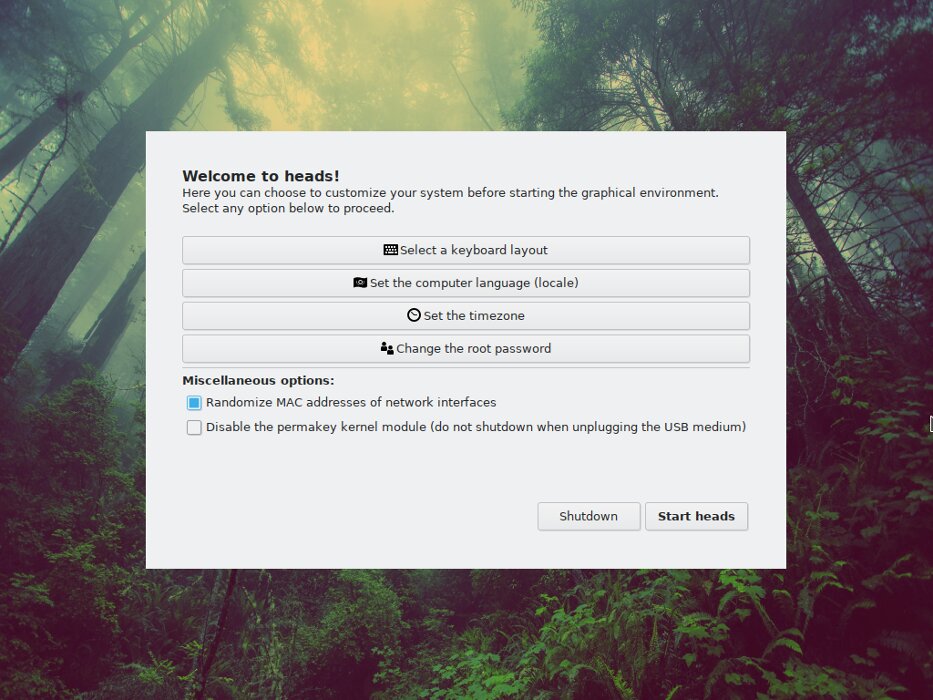
Running heads
By default, external drives are not connected. In Openbox, they are mounted by clicking on the udiskie utility icon in the bottom right pane. The operating system is at an early stage of development, so there are enough imperfections in it. Problems arise already with the search for drivers for video cards, network adapters and other hardware. If you're lucky with the config, heads will quickly start up in Live mode and let all application traffic through Tor.
However, this is not always necessary. For example, when using HexChat, you cannot connect to many popular channels. They see an attempt to log in through the Tor exit nodes and kick you automatically.
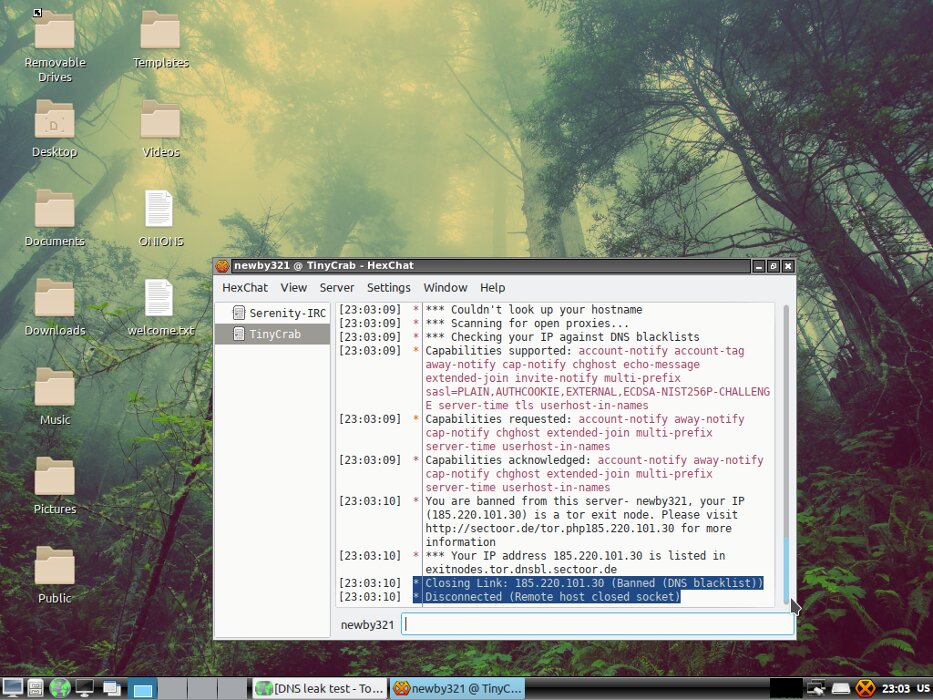
Loki is not happy with Thor
Heads have a very short list of Tor resources, but they are easy to find on your own.
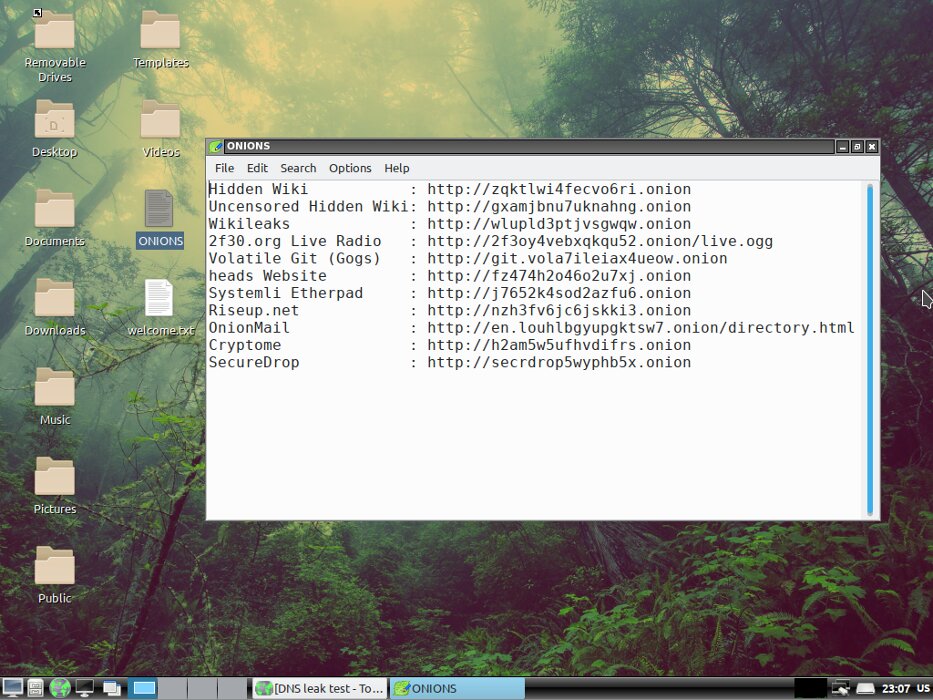
Some addresses in Tor
Tails
Tails (The Amnesiac Incognito Live System) is perhaps the most famous operating system for anonymous web surfing and bypassing Internet censorship. We have written about her more than once, so we will not pay much attention to her now. In particular, on the pages] [they talked about how to install Tails on a USB flash drive and how to use VirtualBox in Tails. Now the latest version 3.6.2 from April 11, 2018 has got into the review.Technically, Tails is an Irish fork of Debian (based on the stable branch) with GNOME as its graphical environment. Tails supports Russian, can configure different methods of connecting to Tor and change the MAC address immediately at startup.
Tor's auto-configuration takes a few minutes, but is easily controlled through Onion Circuits.
Tails updates are released regularly and are mainly security patches. A lot of vulnerabilities are discovered in each version, and a new one is quickly released - all in the tradition of cyclical development.
It is noteworthy that Tails detects the launch in a virtual machine and warns that in this case it does not guarantee anonymity, since it cannot vouch for the security of the main OS.
The set of preinstalled programs in Tails is medium in size (it was once very minimalistic), but you can always install any software from the Debian repositories. But it will take a long time (due to its downloading via Tor), and after the session ends, all changes will be lost (unless, of course, you create an encrypted partition on the USB flash drive using the built-in utility) ...
All data is stored in the RAM and is not stored on disk, so as not to leave traces (again, if you do not use an encrypted partition). When turned off, Tails will flood the RAM with random data to prevent it from being read during a cold boot attack. Protection against sudden pulling out of the flash drive, randomization of the MAC address of the network card (also works for external network cards) are also present. All traffic, including DNS requests, goes exclusively through Tor.
For collaborative anonymous work in real time, the Gobby utility is integrated into Tails. It supports Unicode, syntax highlighting in popular programming languages, and color highlighting of text fragments added by different users. Versions of it are also available for Windows and macOS.
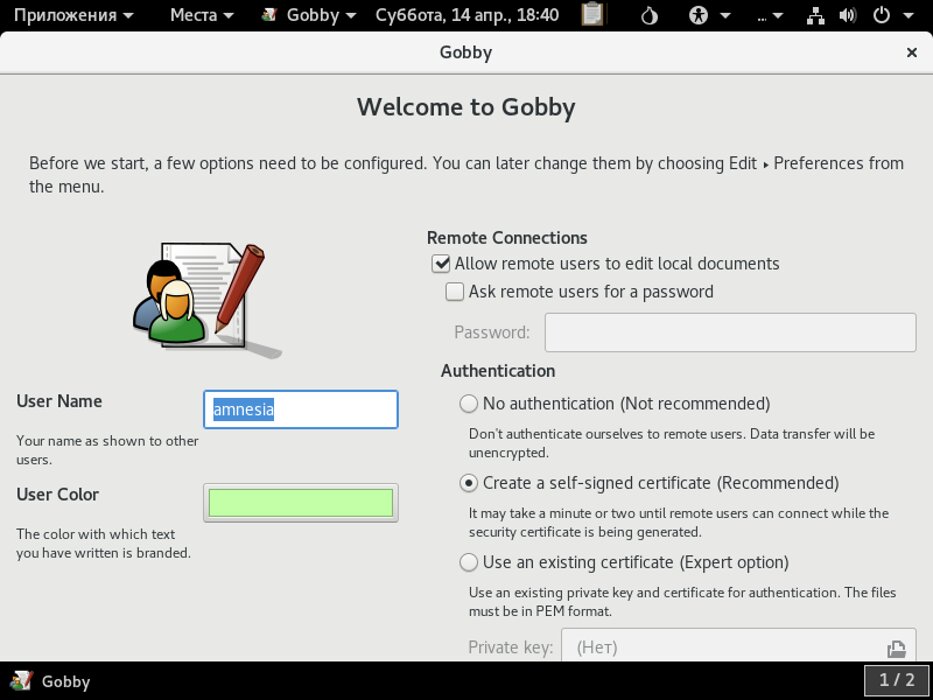
Collaborate anonymously at Tails
Despite its considerable age (the project is almost nine years old), Tails is still prone to strange glitches. For example, when reading news through Liferea, from time to time its search results disappear from the screen or all applications are terminated altogether. This does not happen all the time, and we have not yet managed to catch the relationship with any specific actions.
Uncensored News
Whonix
Perhaps this is the least trivial operating system in today's review. It comes in the form of off-the-shelf virtual machines (.ova) and consists of two interconnected parts.The server side is called Whonix-Gateway, and the client side is called Whonix Workstation. The last stable release was released on May 31, 2016. By default, Whonix has a username user and password changeme.
To use Whonix, you need to download both virtual machines, import their configs using VirtualBox and run one by one, starting with Gateway. They don't need a lot of resources. The optimal parameters have already been set.
Further configuration is performed using the wizard in a few clicks. Console casting is not required.
Configuring Whonix-Gateway
The server side will take care of routing through Tor and VPN, processing DNS requests and filtering network packets.
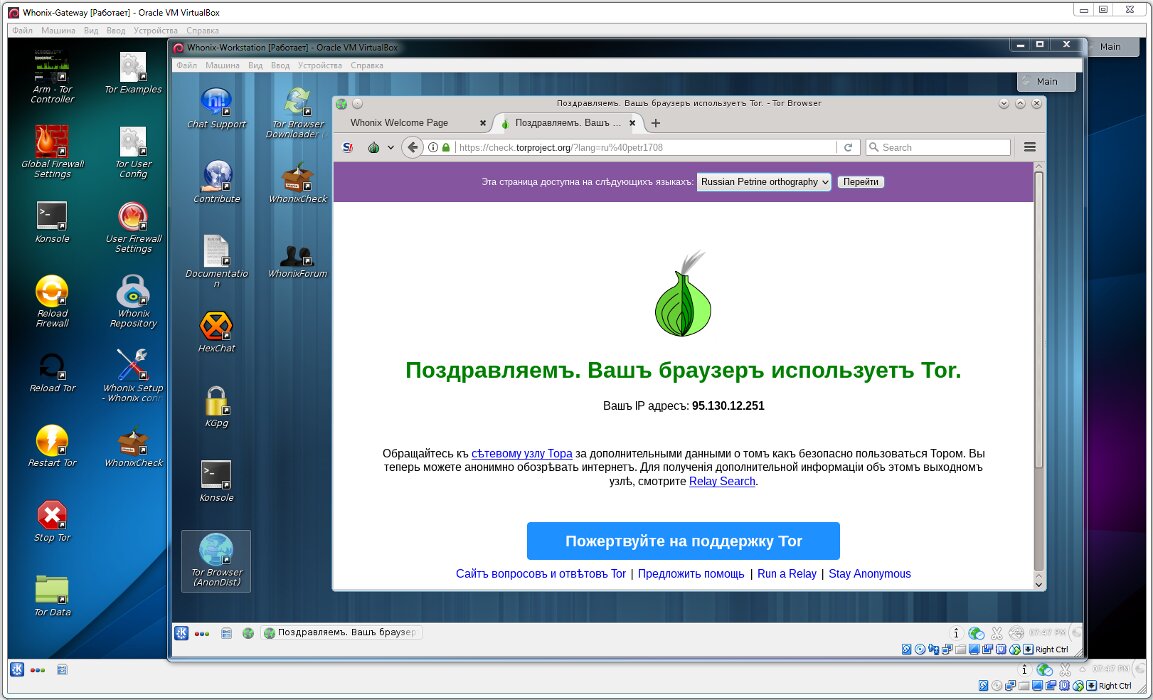
Split Virtual Personality with Whonix
This approach allows you to hide all user data on one virtual machine, while the other, Gateway, is attacked. At the same time, the well-known problem of deanonymization is solved in this way. There is no risk of a real IP address leakage due to DNS leak and routing glitches.
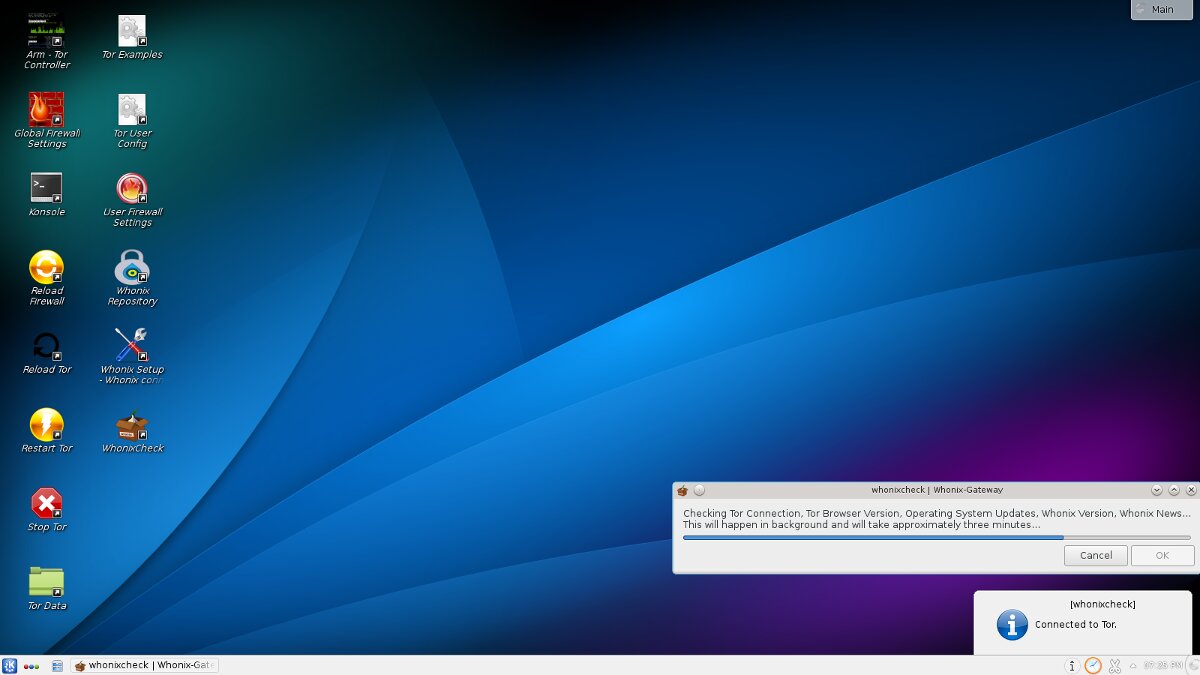
Tor connection status
Even if the server side of Whonix is hacked, the attacker will not figure out your IP address and will not get to your documents and bitcoins, since they are stored in another (client) virtual machine.
Whonix has a fairly standard list of preinstalled programs: Tor browser, Tor Messenger, Tox and Ricochet messengers, Mozilla Thunderbird and TorBirdy mail clients with PGP support, secure file transfer via SCP (RCP over SSH) and system utilities. For a complete list by category, see here.
As with any virtual machine, Whonix reliability depends on the security level of the underlying operating system. It can be run on Windows, macOS or Linux computers.
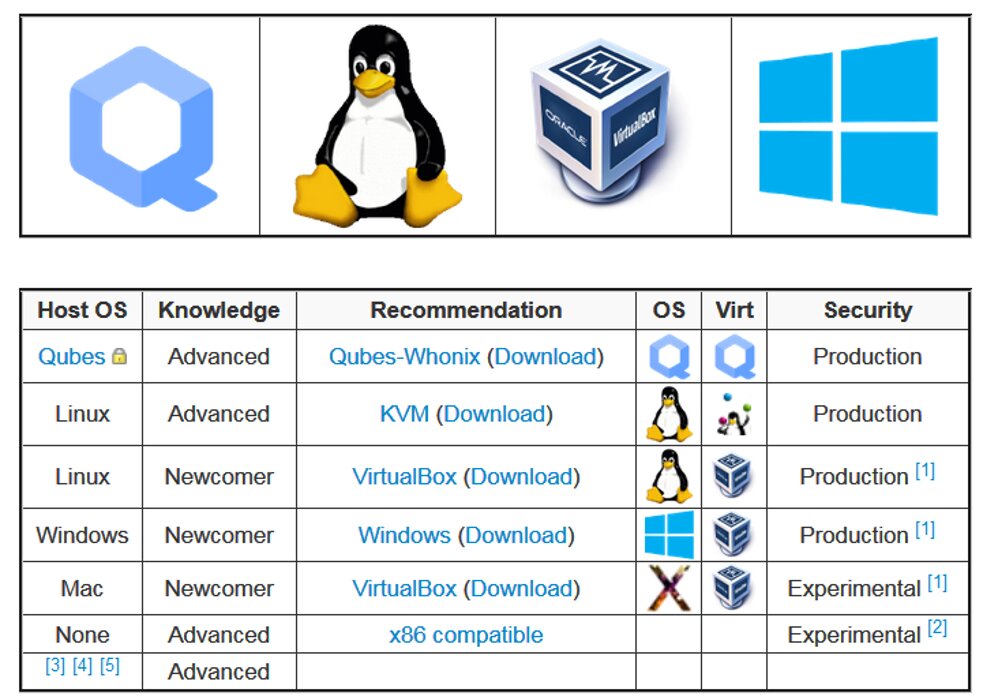
Whonix launch options
One of the most reliable options is to run Whonix in Qubes OS on trusted hardware with reference firmware. This is a fork of Fedora from Yoanna Rutkowska using the Xen hypervisor. This operating system does not apply to Live distributions and therefore is not considered in the current review. However, its basic structure has already been described earlier on the pages of "Hacker".
Conclusions
Among the distributions for anonymous web surfing and bypassing Internet censorship there are both very advertised (Tails, Subgraph OS), but not very convenient, and less well-known, but more functional (MOFO, Kodachi). It is the latter that I advise you to pay attention to when choosing Live OS.This review does not include distributions whose development was suspended two years or more ago. These are JonDo , Sabayon Linux, NSA-blessed TENS, Discreete Linux, IprediaOS and many others. This does not mean that they are bad, just now there are more relevant ones, and only the lazy did not make their fork of anonymous Linux.
xakep.ru

