Father
Professional
- Messages
- 2,602
- Reaction score
- 837
- Points
- 113
Armenian traces were found in a cyberattack on the Russian military.
F. A. C. C. T. specialists have identified a malicious file uploaded from the Armenian city of Gyumri on VirusTotal.
The file is associated with the Core Werewolf cyberespionage group and is a 7zSFX self-extracting archive. It is designed for unobtrusive installation and activation of the UltraVNC remote access program.
It is assumed that the main target of the attack is the 102nd Russian military base in Gyumri. The goal is confirmed by using as a trap a document with a request for awarding the military with the "Order of Courage", distinguished themselves during the SVO.
Technical aspects of the malicious file include details of the PE32 executable file, which runs a series of commands that include modifying, copying, and running an obfuscated Batch file to install and configure UltraVNC, as well as creating tasks in the Windows Scheduler to establish permanent management of infected systems.
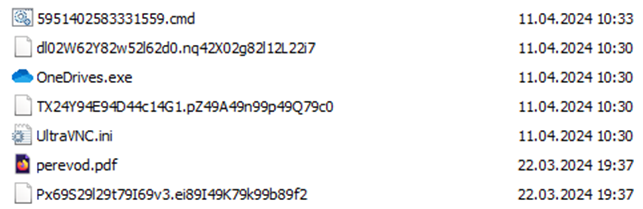
Archive contents
Based on the contents of the archive, experts determined that the attack could have started before April 15, 2024. Among other things, the archive contains a decoy document "period.pdf" containing a list of military personnel submitted for state awards.
The configuration file "UltraVNC.ini" with detailed settings for connecting to the server via the C2 domain "mailcommunity[.]ru"is also used. The attackers network infrastructure was registered a year earlier and coincides with the infrastructure used in the group's previous attacks. And the recent extension of domains indicates the continuation of cyber espionage activity.
F. A. C. C. T. specialists have identified a malicious file uploaded from the Armenian city of Gyumri on VirusTotal.
The file is associated with the Core Werewolf cyberespionage group and is a 7zSFX self-extracting archive. It is designed for unobtrusive installation and activation of the UltraVNC remote access program.
It is assumed that the main target of the attack is the 102nd Russian military base in Gyumri. The goal is confirmed by using as a trap a document with a request for awarding the military with the "Order of Courage", distinguished themselves during the SVO.
Technical aspects of the malicious file include details of the PE32 executable file, which runs a series of commands that include modifying, copying, and running an obfuscated Batch file to install and configure UltraVNC, as well as creating tasks in the Windows Scheduler to establish permanent management of infected systems.

Archive contents
Based on the contents of the archive, experts determined that the attack could have started before April 15, 2024. Among other things, the archive contains a decoy document "period.pdf" containing a list of military personnel submitted for state awards.
The configuration file "UltraVNC.ini" with detailed settings for connecting to the server via the C2 domain "mailcommunity[.]ru"is also used. The attackers network infrastructure was registered a year earlier and coincides with the infrastructure used in the group's previous attacks. And the recent extension of domains indicates the continuation of cyber espionage activity.

