The U.S. indictment charges two Russian citizens with assaults on multiple victims from the U.S. and other countries; the FBI seizes infrastructure; and the Treasury Department takes additional action against LockBit.
The Department of Justice joined the United Kingdom and international law enforcement partners in London today to announce the crackdown on the LockBit ransomware group, one of the most active ransomware groups in the world, which targeted more than 2,000 victims, received more than $ 120 million in ransom payments, and made demands totaling hundreds of millions of dollars..
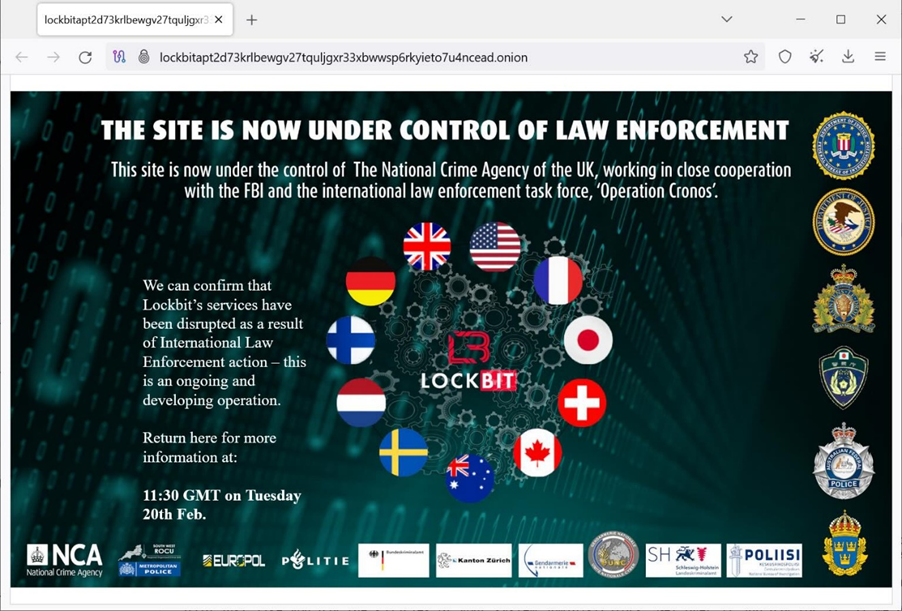
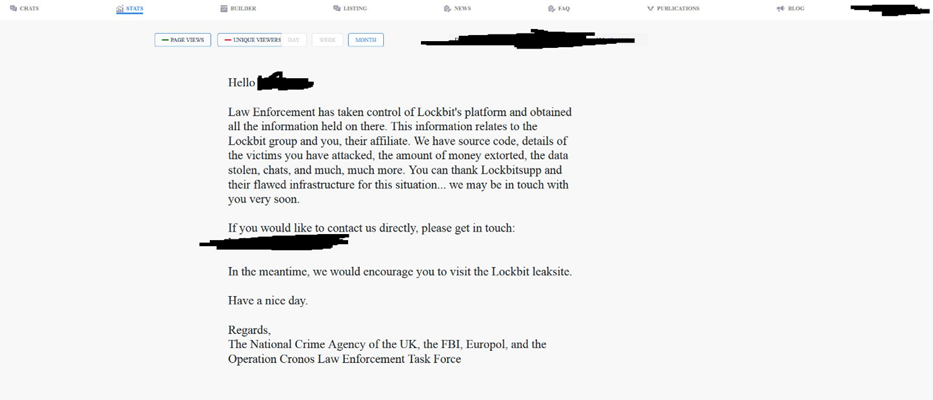
The cyber division of the UK's National Crime Agency (NCA), working in collaboration with the Department of Justice, the Federal Bureau of Investigation (FBI) and other international law enforcement partners, disrupted LockBit by hijacking numerous publicly accessible websites used by LockBit to connect to the organization's infrastructure and seizing control of the servers. This will disrupt the ability of LockBit participants to attack and encrypt networks, as well as extort threats to publish stolen data from victims.
"Over the years, LockBit employees have carried out similar attacks again and again throughout the United States and around the world. Today, law enforcement agencies in the United States and Great Britain are taking the keys to their criminal activities,” said Attorney General Merrick B. Garland. “And we're going further — we've also obtained keys to the hijacked LockBit infrastructure to help victims decrypt their hijacked systems and restore access to their data. LockBit is not the first ransomware that has been defused by the Justice Department and its international partners. It won't be the last one.”
In addition, the NCA, in collaboration with the FBI and international law enforcement partners, has developed decryption capabilities that could allow hundreds of victims around the world to recover systems encrypted with the LockBit ransomware. Starting today, victims targeted by this malware are advised to contact the FBI at
https://lockbitvictims.ic3.gov/, so that law enforcement agencies can determine whether vulnerable systems can be successfully decrypted.
”Today's actions are yet another down payment as part of our commitment to continue dismantling the ecosystem that fuels cybercrime, prioritizing disruption and putting victims first," Deputy Attorney General Lisa Monaco said in a statement. "Using our full powers and working alongside partners in the United Kingdom and around the world, we have destroyed the online backbone of the LockBit group, one of the most prolific ransomware gangs in the world. But this is not the end of our work: Together with our partners, we are changing the situation with LockBit-we provide decryption keys, unlock victims ' data, and target LockBit's criminal affiliates around the world.”
The Justice Department also released an indictment obtained in the District of New Jersey that indicts Russian citizens Arthur Sungatov and Ivan Kondratyev, also known as Bassterlord, for using LockBit against numerous victims across the United States, including businesses across the country in manufacturing and other industries, as well as victims around the world worldwide in the semiconductor and other industries. Additional criminal charges were filed today in the Northern District of California against Kondratiev related to his use of a ransomware program in 2020 against a victim located in California.
Finally, the Department also unsealed two search warrants issued in the District of New Jersey that authorized the FBI to shut down several U.S. servers used by LockBit members due to the LockBit outage. As indicated in these search warrants, LockBit administrators used these servers to host the so-called “StealBit” platform, a criminal tool used by LockBit members to organize and transfer victims ' data.
”Today, the FBI and our partners successfully disrupted the LockBit criminal ecosystem, which is one of the most widespread types of ransomware around the world," said FBI Director Christopher A. Ray. “Over years of groundbreaking investigative work, the FBI and our partners have significantly reduced the ability of hackers responsible for launching devastating ransomware attacks on critical infrastructure and other public and private organizations around the world. This operation demonstrates both our capabilities and our commitment to protecting our nation's cybersecurity and national security from any attacker who seeks to affect our way of life. We will continue to work with our domestic and international allies to identify, combat and contain cyber threats and bring those responsible to justice."
According to an indictment obtained in the District of New Jersey, since at least January 2021, Sungatov allegedly used the LockBit ransomware program against victim corporations and took steps to fund additional LockBit attacks against other victims. Sungatov allegedly used the LockBit ransomware against manufacturing, logistics, insurance and other companies located in Minnesota, Indiana, Puerto Rico, Wisconsin, Florida and New Mexico. In addition, as early as August 2021, Kondratyev allegedly began using LockBit against several victims in a similar way. Kondratyev, who operates under the online pseudonym "Bassterlord” allegedly used LockBit against municipal and private facilities in Oregon, Puerto Rico, and New York, as well as additional targets located in Singapore, Taiwan, and Lebanon. It is alleged that both Sungatov and Kondratyev participated in the LockBit global conspiracy, which also allegedly included Russian citizens Mikhail Pavlovich Matveev and Mikhail Vasiliev, as well as other LockBit participants, in order to develop and implement the LockBit ransomware program and extort payments from victim corporations.
” Today's indictment, released as part of a global coordinated action against the world's most active ransomware group, brings to five the total number of LockBit members indicted by my office and our partners in the FBI and the Computer Crimes and Intellectual Property Division for their crimes," said New Jersey District Attorney Philip R. Sellinger. “And even with today's LockBit outage, we won't stop there. Our investigation will continue, and we remain determined to identify and bring charges against all LockBit members - from its developers and administrators to its affiliates. We will draw attention to them as wanted criminals. They will no longer hide in the shadows.”
Today, when the indictment was made public, a total of five LockBit members were indicted for their involvement in the LockBit conspiracy. In May 2023, two indictments were released in Washington, D.C., and the District of New Jersey, accusing Matveev of using various ransomware programs, including LockBit, to attack numerous victims across the United States, including the Washington, D.C. Metropolitan Police Department. Currently, Matveev faces a reward of up to $ 10 million under the US State Department's Program to Reward Transnational Organized Crime, information is received through the FBI tip website at
https://tips.fbi.gov. In November 2022, a criminal case was filed in the District of New Jersey, in which Vasiliev was charged in connection with his participation in the global LockBit ransomware campaign. Vasiliev, who holds dual Russian-Canadian citizenship, is currently in Canadian custody awaiting extradition to the United States. In June 2023, Russian citizen Ruslan Magomedovich Astamirov was indicted on criminal charges in the District of New Jersey for his involvement in the LockBit conspiracy, including using LockBit against victims in Florida, Japan, France, and Kenya. Astamirov is currently in custody in the United States awaiting trial.
Kondratyev, according to the indictment obtained in the Northern District of California and released today, is also charged with three criminal counts related to his use of the Sodinokibi ransomware program, also known as REvil, to encrypt data, extract information about the victim, and extort ransom from the victim corporation based in Alameda County, California.
The LockBit ransomware version first appeared around January 2020 and, having started operating today, has become one of the most active and destructive versions in the world. LockBit members have carried out attacks against more than 2,000 victims in the United States and around the world, making ransom demands worth at least hundreds of millions of US dollars and receiving more than $ 120 million in ransom payments. The LockBit ransomware program, like other major ransomware variants, operates on a ransomware-as-a-service (RaaS) model, in which administrators, also called developers, develop the ransomware, hire other contributors, called affiliates, to deploy it, and maintain an online software dashboard. a platform called the "control panel" to provide affiliates with the tools they need to deploy LockBit. Affiliates, in turn, identify vulnerable computer systems and gain access to them illegally, sometimes by hacking themselves or in other cases by acquiring stolen access credentials from others. Using a developer-managed control panel, affiliates then inject LockBit into the victim's computer system, allowing them to encrypt and steal ransom-worthy data to decrypt or avoid publication on a public website maintained by LockBit developers, often referred to as a data leak site.
The local FBI office in Newark is investigating a version of the LockBit ransomware.
Assistant U.S. Attorneys Andrew M. Trombley, David E. Malagold, and Vinay Limbachia of the District of New Jersey, and Trial attorneys Jessica K. Peck, Debra Ireland, and Jorge Gonzalez of the Criminal Division's Computer Crimes and Intellectual Property Division filed charges against Sungatov and Kondratyev, which were released today in the District of New Jersey. The Prosecutor for Cybercrime Relations of the Ministry of Justice at Eurojust and the Office for International Affairs also provided significant assistance.
The glitch announced today was the result of a joint operation by the FBI; the NCA's Southwest Regional Organized Crime Unit; France's National Cyberspace Command; Germany's Schleswig-Holstein Landskriminal Office and the German Bundeskriminal Office; the Swiss Federal Police Department, the Zurich Canton Prosecutor's Office and the Zurich Cantonal Police; the Japanese National Policy Agency; the Australian Federal Police; the Swiss Federal Police Department; the Swiss Federal national security of Sweden. The Netherlands Police; the Royal Canadian Mounted Police; the Netherlands East Brabant Regional Policy Office; the Finnish Police; Europol; and Eurojust.
The Phoenix Field office of the FBI and Assistant U.S. Attorney Helen L. Gilbert are investigating and opening a criminal case against Kondratiev in the Northern District of California.
In addition, the U.S. Treasury's Office of Foreign Assets Control announced today that it is appointing Sungatov and Kondratiev for their roles in organizing the cyberattacks.
As mentioned above, LockBit victims should contact the FBI at
https://lockbitvictims.ic3.gov for more information. For more information about protecting your networks from the LockBit ransomware, visit StopRansomware.gov. These include the Agency's Cybersecurity and Infrastructure Security recommendations AA23-325A, AA23-165A, and AA23-075A.
Follow the Attorney General's comments at
www.youtube.com/watch?v=-jKykhKKMZw.