Man
Professional
- Messages
- 3,223
- Reaction score
- 1,160
- Points
- 113

Baiting is one of the common ways to detect intruder activity. Honeypot class solutions are a resource that is a bait for intruders. In practice, this is usually a special application that emulates the presence of vulnerable services on open ports. This can be a web server, database, file resource, etc. The main task of a honeypot is to attract the attention of an intruder in order to, firstly, make him waste time hacking resources that do not represent real value, secondly, with the help of bait it is easier for us to detect the hacker and take protective measures before he starts breaking real resources, and thirdly, with the help of a honeypot we can collect information about the hacking methods used by intruders.
However, honeypots should not just emulate vulnerable systems, they should also report all actions performed by the attacker. As a rule, in practice, all significant actions of the attackers are recorded in event logs.
This records the time, commands entered by the attacker, IP addresses from which the connection was made, user names, passwords and other information used for hacking. Of course, it is best to send all recorded events to SIEM for subsequent analysis.
Types of baits
Conventionally, honeypots can be divided into three types by the level of interaction with the attacker. Honeypots with a low level of interaction. Typically, such honeypots emulate the operation of network services by opening the appropriate ports and responding when connecting to these ports. For example, we can emulate the operation of a DBMS. When scanning, the required port will be open, and upon subsequent connection, an invitation with a corresponding banner will be displayed containing information on the OS and DBMS version. However, in fact, the honeypot will not emulate anything further. That is, the attacker can spend time picking a password for an account that does not lead anywhere.That is, in essence, low-interaction lures are placeholders that only imitate individual features of target services.
Medium-interaction honeypots mimic the operating system and can better emulate vulnerable applications. They typically collect more information because their goal is to stop the attacker, giving more time to respond to the threat.
High-interaction honeypots are really vulnerable software that interacts with different applications. A classic example of such a honeypot is the vulnerable Metasploitable OS.
What do we fish with?
Also, Honeypot can only emulate individual services. So, email lures are fake email addresses. They are usually published on external resources. An attacker can send an email with malware or a phishing link to this address. By tracking such emails, we will be aware of phishing mailings and other malicious activities carried out against the company.Hackers can also be caught using passwords intercepted on the network using a sniffer. It is impossible to detect a sniffer in a local network using technical means. In general, you can crimp a twisted pair in such a way that only the wires responsible for receiving data are connected to the network, and then not a single bit can go into the network. If there is physical access to network sockets, such a cable guarantees no impact on the network. This principle is used in unidirectional gateways (data diodes), which receive copies of traffic from critical segments of industrial networks.
But you can detect traffic eavesdropping using a simple bait. We create a fake service in the local network, for example, a web application for accounting of working hours. It should work via HTTP and use the transfer of the password in clear text or Basic authentication. Very often in the local networks of organizations you can find such self-written portals, and sometimes they use domain authentication, but the password from the domain account still needs to be entered manually.
Next, we write a script that successfully connects to this node with some random frequency. All connections are recorded in logs and sent to SIEM. Next, we set up a correlation rule in SIEM that looks at which addresses, under which accounts and when there were connections to our web resource, if someone logged in with our account from the script and from an outside node, then there is a sniffer in the network.
But all of these are homemade honeypot solutions. But is there anything ready-made? The article already mentioned the vulnerable Metasploitable distribution. You can download a virtual machine with the third version of this distribution. Metasploitable has vulnerable services FTP, Apache, CUPS web applications Drupal, phpMyAdmin and other applications and services. In general, Metasploitable is quite suitable for use as a bait with a high level of interaction, except for the fact that an experienced attacker will quickly, perhaps already at the scanning stage, understand that this is a Honeypot, since too many leaky versions of software are used there. Therefore, for serious use, it is better to carry out some customization.
Taming the Canary
OpenCanary is a medium-level interaction honeypot. It is an open-source honeypot written in Python, and therefore the honeypot core is cross-platform, but some features require specific operating systems. It has extremely low resource requirements and can simulate Linux Web Server, Windows Server, MySQL Server and MSSQL servers, and others.The installation of this honeypot is quite simple.
Code:
sudo apt-get install python3-dev python3-pip python3-virtualenv python3-venv python3-scapy libssl-dev libpcap-dev
$ virtualenv env/
$ . env/bin/activate
$ pip install opencanary
Optionally, you can also install Samba and Scapy if you want to simulate Windows shares and SNMP.
Code:
$ sudo apt install samba # if you plan to use the Windows File Share module
$ pip install scapy pcapy-ng # if you plan to use the SNMP moduleNext we need to initialize the canary. To do this, run the command:
Code:
$ opencanaryd --copyconfigAnd then we open the configuration file for editing:
Code:
$ nano /etc/opencanaryd/opencanary.conf
Next we see a JSON file. Its structure is very simple. As an example, let's consider the settings block for HTTP/HTTPS.
Code:
"http.banner": "Apache/2.2.22 (Ubuntu)",
"http.enabled": false,
"http.port": 80,
"http.skin": "nasLogin",
"https.enabled": false,
"https.port": 443,
"https.skin": "nasLogin",
"https.certificate": "/etc/ssl/opencanary/opencanary.pem",
"https.key": "/etc/ssl/opencanary/opencanary.key",First of all, we are interested in the *.enabled parameter. If we want to enable this service, this parameter must be true. Next, *.port, by default, the port numbers accepted for these protocols are offered. The *.banner parameter shows which version of the software is used. Do not put too old and leaky version numbers, it will be too suspicious. The http.skin parameter indicates which type of interface will be used. For https, we must also specify the paths to the pem and key files used for TLS encryption.
I also recommend enabling port scan detection as shown in the figure.
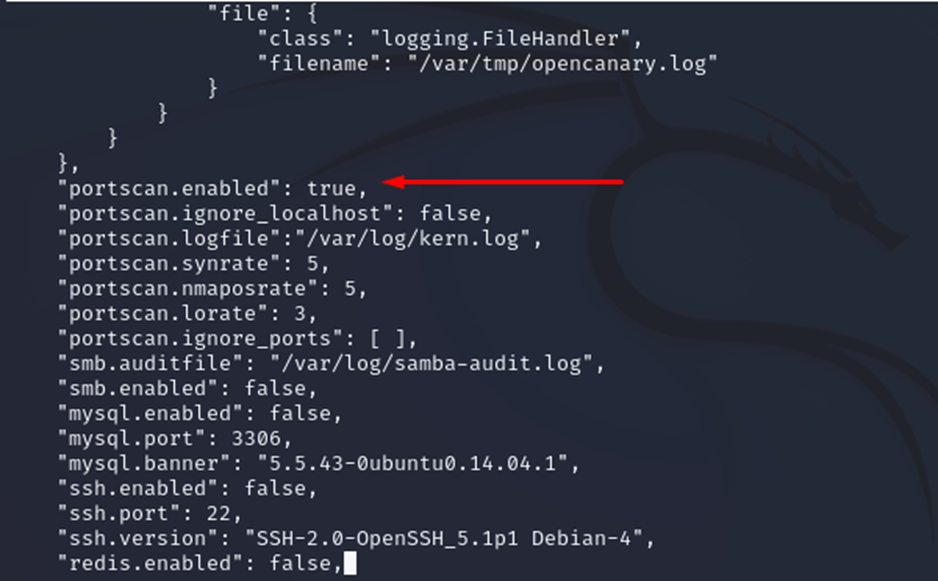
To launch OpenCanary, run the following commands:
Code:
$ . env/bin/activate
$ opencanaryd –startIf we want to run the bait as a daemon, we need to run a few more commands.
Code:
sudo nano /etc/systemd/system/opencanary.serviceAdding a block.
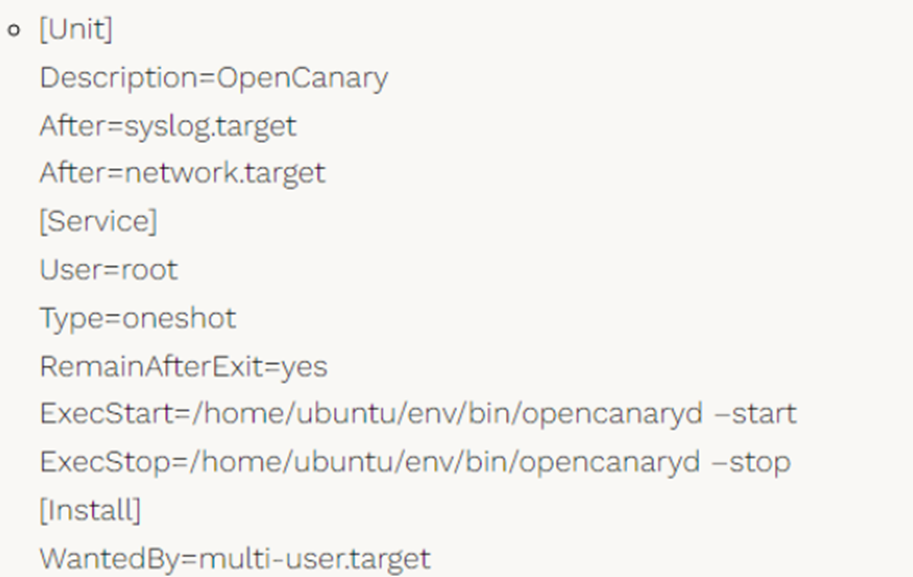
And we set up the launch:
Code:
sudo systemctl enable opencanary.service
sudo systemctl start opencanary
sudo systemctl status opencanaryChecking the bait
To make sure that OpenCanary is actually starting the appropriate services, let's first perform a port scan.
Code:
$ nmap -sV IP_address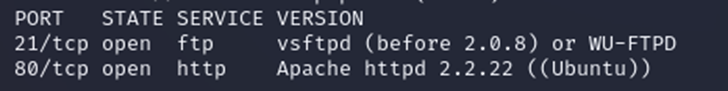
You can also try to immediately search for vulnerabilities using the same Nmap
Code:
nmap --script=vuln 127.0.0.1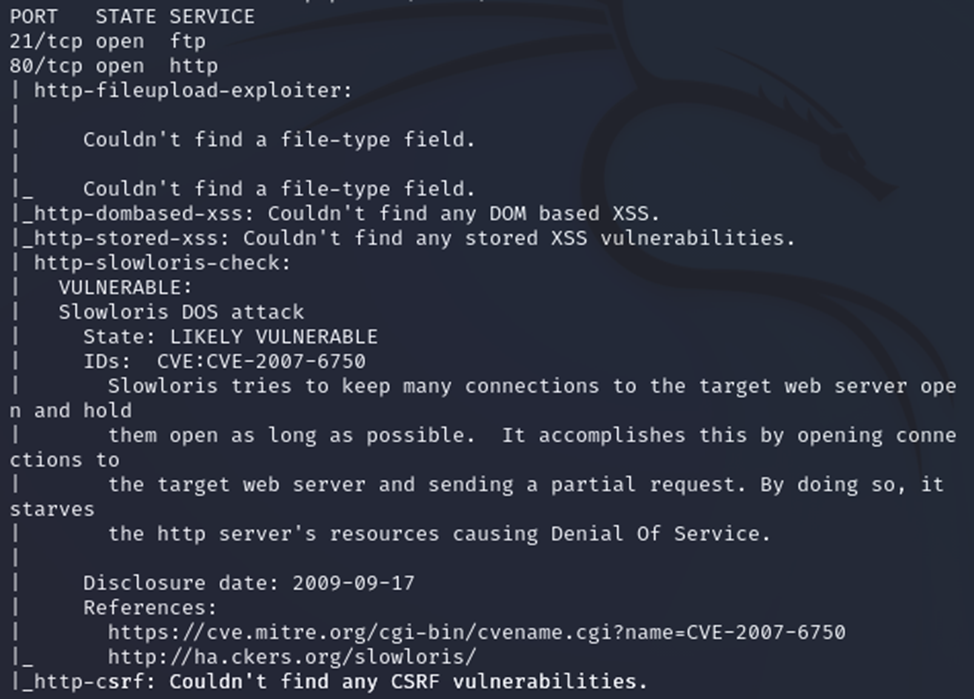
I believe that such a result will interest an attacker, although of course the vulnerability is old. But the web interface looks quite modern.
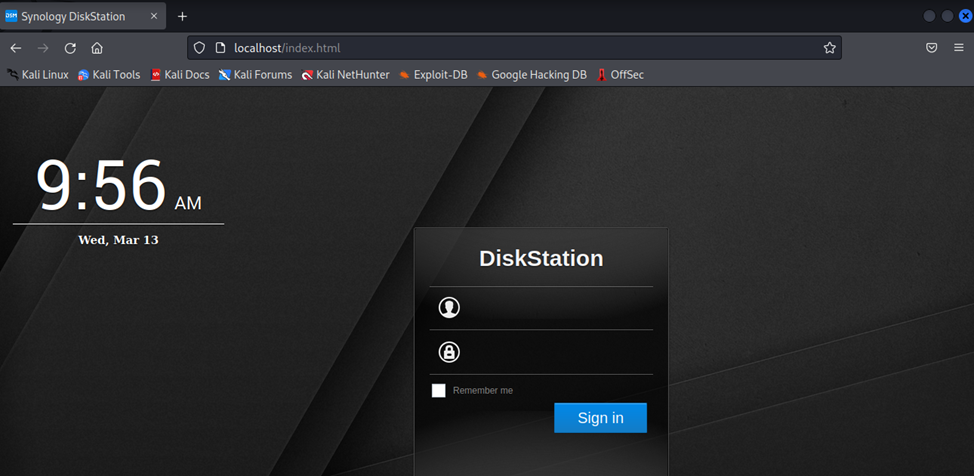
Well, we have kept the attacker busy for a while, while he will configure Hydra to brute force passwords and try to exploit vulnerabilities using Metasploit, we have time to take protective measures.
But first, let's see what events our honeypot recorded for subsequent forwarding to SIEM.
Harvest of logs
The standard log file /var/log/syslog contains many messages about connection attempts on various ports, attempts to exploit vulnerabilities, connections to the web interface, and other suspicious activities. In general, there is enough information for correlations in SIEM.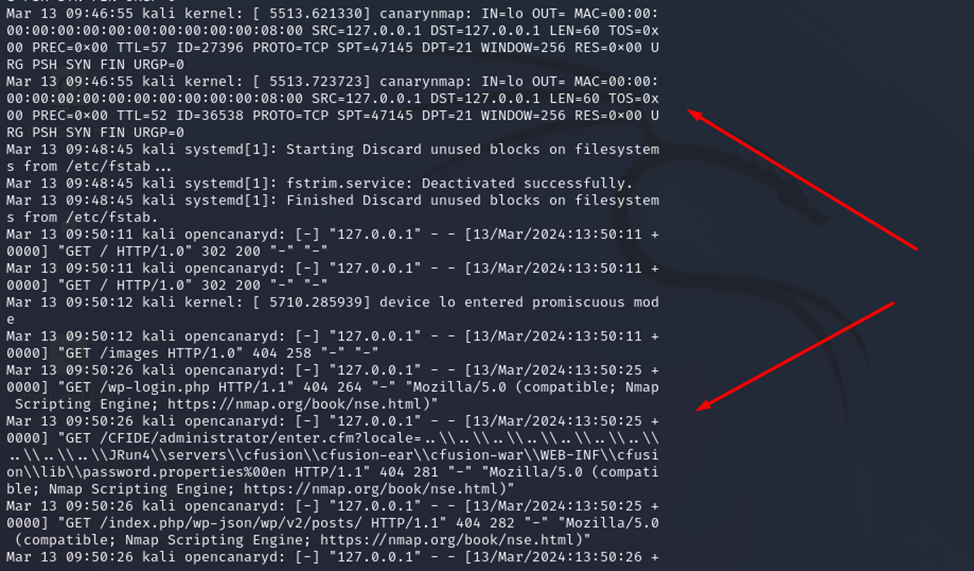
Canary in a box
Honeypot can be deployed on a virtual machine, in a container or on a physical device. However, when using the first two technologies, there is a theoretical risk that an attacker will be able to get out of the isolated environment of the honeypot and launch a real attack. In order to minimize such a risk, you can deploy the honeypot on a physical device. Of course, you can take an old laptop, install Linux and OpenCanary on it.But more mobile and easier to use is to deploy the bait on a microcomputer, for example, on a Raspberry Pi. In this article, we will not consider the features of installing the OS on the Raspberry. Installing OpenCanary on Ubuntu under Raspberry is no different from the installation process described above.
Conclusion
Having a properly configured bait in the network allows not only to distract the attacker and gain valuable time, but also to detect it in time and take the necessary measures for protection.You can learn more practical tools on information security in online courses from industry experts. Go to the catalog and choose the appropriate direction.
Source
