F. A. C. C. T. experts share useful tips for effective defense against hackers.
Cybersecurity researchers from the F. A. C. C. T. Threat Intelligence team recently identified a new malware campaign by the hacker group RedCurl targeting organizations in Australia, Singapore, and Hong Kong. The attacks affected the construction, logistics, air transportation, and mining industries.
The RedCurl group, which has been active since 2018 and was first identified in 2019, specializes in cyber espionage. Attackers use unique tools to steal business correspondence, personal data of employees, and legal documents.
From the initial infection of the target network to the actual theft of data, it usually takes from two to six months, as hackers carefully plan all their actions.
Analysis of RedCurl activity showed that the group continues to expand the geography of its operations. Of the 40 successful attacks only half came in Russia and CIS countries, while the rest of the UK, Germany, Canada and Norway.
In late 2023 attacks, the group continued to use emails with embedded SVG files or RAR archives for initial infection. These files are usually disguised as official documents from well-known companies such as Amazon and Samsung, and include mechanisms for downloading malicious code.
RedCurl uses sophisticated mechanisms to strengthen its presence on the victim's system, including by creating scheduled tasks in the Windows Scheduler. The next stages of the attack include collecting information about the system and then sending it to the hackers ' C2 servers.
The researchers also found examples of successful attacks in which attackers managed to exfiltrate casts of the Active Directory database from Australian companies.
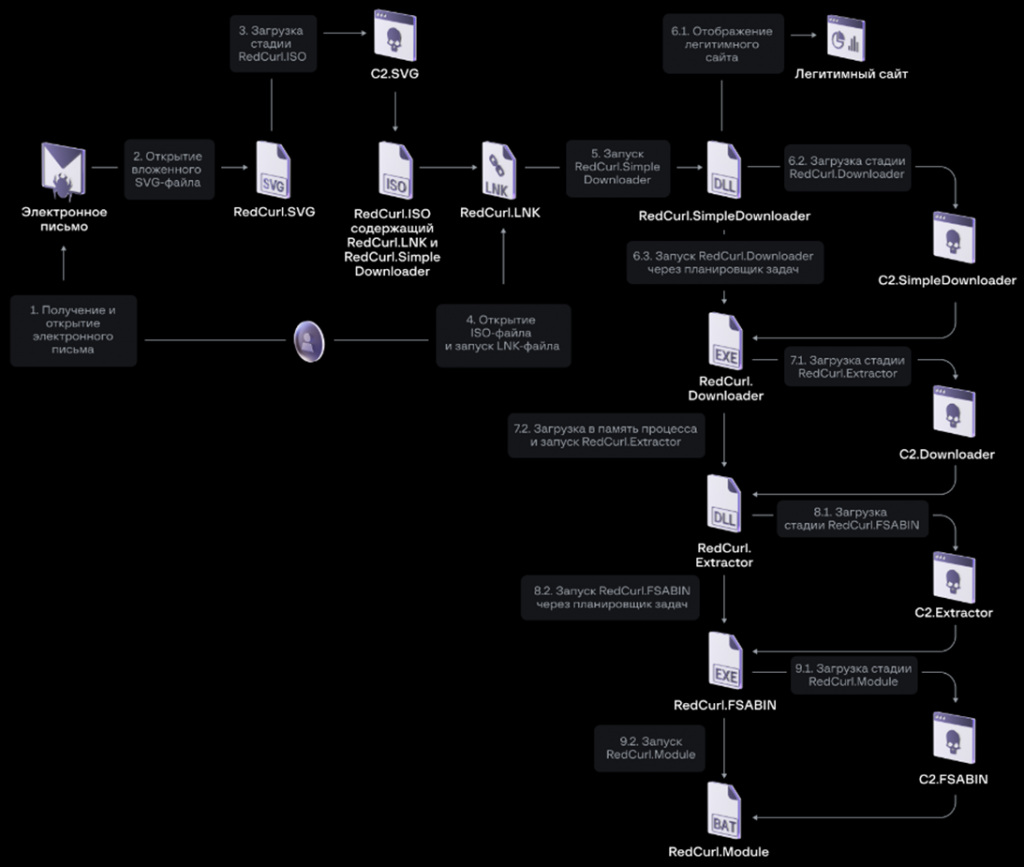
Infection chain in recent RedCurl attacks (courtesy of F. A. C. C. T.)
In response to the threats and risks presented by the RedCurl group, F. A. C. C. T. experts recommend that companies strengthen email protection, train employees to recognize phishing attacks, monitor unusual activity in the Windows task Scheduler, and use specialized solutions to protect Active Directory.
All the tactics, techniques and procedures used by attackers (TTP), as well as indicators of compromise (IoC) are described in detail in the full report of the researchers.
Cybersecurity researchers from the F. A. C. C. T. Threat Intelligence team recently identified a new malware campaign by the hacker group RedCurl targeting organizations in Australia, Singapore, and Hong Kong. The attacks affected the construction, logistics, air transportation, and mining industries.
The RedCurl group, which has been active since 2018 and was first identified in 2019, specializes in cyber espionage. Attackers use unique tools to steal business correspondence, personal data of employees, and legal documents.
From the initial infection of the target network to the actual theft of data, it usually takes from two to six months, as hackers carefully plan all their actions.
Analysis of RedCurl activity showed that the group continues to expand the geography of its operations. Of the 40 successful attacks only half came in Russia and CIS countries, while the rest of the UK, Germany, Canada and Norway.
In late 2023 attacks, the group continued to use emails with embedded SVG files or RAR archives for initial infection. These files are usually disguised as official documents from well-known companies such as Amazon and Samsung, and include mechanisms for downloading malicious code.
RedCurl uses sophisticated mechanisms to strengthen its presence on the victim's system, including by creating scheduled tasks in the Windows Scheduler. The next stages of the attack include collecting information about the system and then sending it to the hackers ' C2 servers.
The researchers also found examples of successful attacks in which attackers managed to exfiltrate casts of the Active Directory database from Australian companies.

Infection chain in recent RedCurl attacks (courtesy of F. A. C. C. T.)
In response to the threats and risks presented by the RedCurl group, F. A. C. C. T. experts recommend that companies strengthen email protection, train employees to recognize phishing attacks, monitor unusual activity in the Windows task Scheduler, and use specialized solutions to protect Active Directory.
All the tactics, techniques and procedures used by attackers (TTP), as well as indicators of compromise (IoC) are described in detail in the full report of the researchers.
