Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,038
- Points
- 113
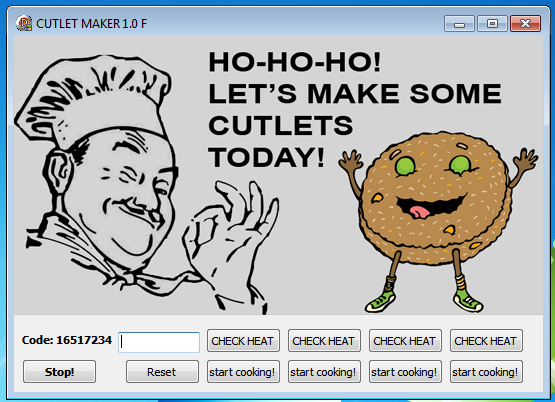
No, this is not cooking software at all. Here we are talking about a “cutlet of money”, not a dish.
Automated teller machines (ATM) are specialized machines that are designed to conduct various types of financial transactions, including issuing cash. As a rule, their control unit is a modified PC running Windows OS. Accordingly, these computers are susceptible to software written by attackers for the Microsoft operating system.
Until now, cybercriminals have written such software for personal needs or to sell to a select few for huge sums of money. But now the situation has changed: software of this kind has appeared in the public domain. Or rather, not entirely open. Kaspersky Lab discovered that malware called Cutlet Maker is freely sold on the Darknet, which is intended for only one thing - to force ATMs of certain models to dispense cash in unlimited quantities.
However, this cannot be done remotely. Physical access to the machine is required, namely a connection to the system’s USB port.
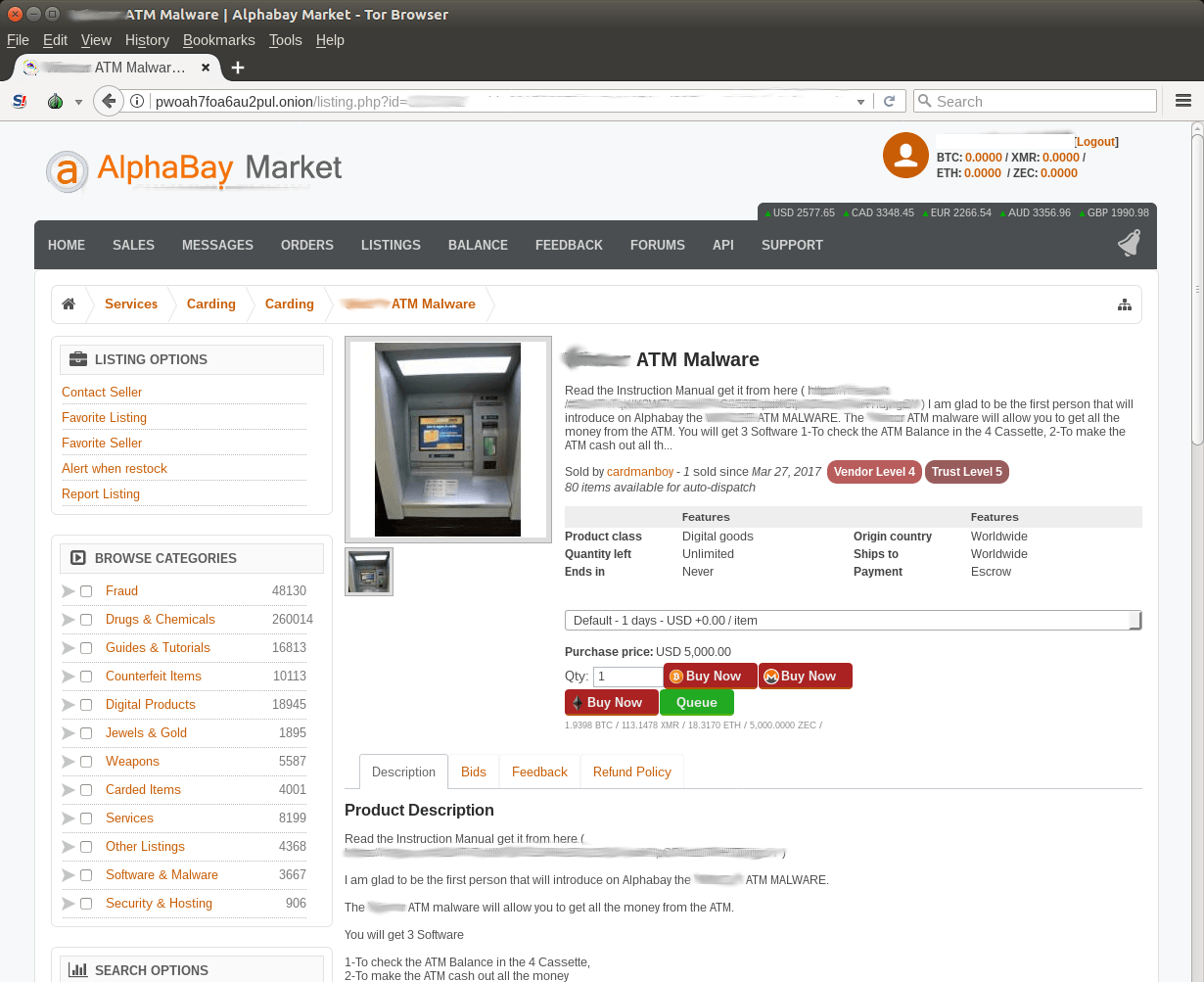
The screenshot shows a description of malware sold on the now closed AlphaBay. However, software authors have switched to selling software through their own website.
Kaspersky Lab claims that software offered by cybercriminals is now finding more and more buyers. In particular, attackers sell it on their own onion website; attempts to sell this software have been recorded on the underground forum “migalki.pw” and some other resources. At the same time, the cost of the package is falling - if previously it cost $5,000, now there are also offers with a price of $800–1,200.
The program is called Cutlet Maker. It consists of three modules. The first one generates passwords to run the Cutlet Maker application, which prevents those who have not paid for it from using the software. The second is the Stimulator application, which shows the number and denomination of banknotes in the ATM cassettes. Thanks to it, the burglar can stop guessing how much money is in the ATM and in which cassette, but immediately select the desired object. Well, the third element is the main module for working with the money dispensing device.
By the way, the newer version of malware no longer contains the module that generates codes. Instead, code generation is carried out on the software developers' website.
To start the “work,” the attacker must find the ATM’s USB port. Due to the fact that all such systems are typed, the task of connecting is not too difficult for an experienced hacker. “Cutlet” is designed to work with Wincor Nixdorf ATMs, so all a cybercriminal needs is to study the ATM models of this company, finding out exactly where the USB port is located.
According to Kommersant, the cost of software of this kind was previously at least $100,000. In the case of the cutlet, we see a much lower price. Moreover, this is a really working product that was created by professionals.
““Cutlet” is unique in that it is not difficult to purchase, and it is also very affordable in price. If you consider that an ATM costs on average from 5 million to 10 million rubles, then it pays for itself in one theft,” says Sergey Golovanov, leading anti-virus expert at Kaspersky Lab.
According to experts, if banks do not pay due attention to this problem, then at the current cost of the “cutlet” this software will be used en masse, which will entail an increase in the number of thefts of funds from ATMs.
“Despite the fact that banks, on average, pay a lot of attention to information security, attacks using such a “set” can cause serious financial damage to some of them,” says Valentin Krokhin.
There's a catch. The fact is that banks do not consider ATM vulnerabilities to be their problems. According to representatives of such organizations, eliminating vulnerabilities lies on the shoulders of ATM manufacturers. Since we are talking about Wincor Nixdorf systems, many banks can expect solutions to problems with their devices from Wincor. At the same time, since Wincor Nixdorf systems are the most common in the Russian Federation and some other countries, you need to act very quickly before the problem becomes truly widespread.
To solve this problem, ATM manufacturers and banks should join forces. Kaspersky Lab said it is protecting the system from malware. But there is already evidence that KESS can be bypassed.

