Friend
Professional
- Messages
- 2,653
- Reaction score
- 850
- Points
- 113
The digital chameleon opens a new chapter in the alliance of cybercriminals.
The NoName ransomware group has been trying to build a reputation for itself for over three years by targeting small and medium-sized businesses around the world with its ransomware. ESET specialists suggested that NoName now cooperates with RansomHub as a partner.
Hackers use customized tools that are part of the Spacecolon malware family. To penetrate the network, cybercriminals use brute-force attack methods, as well as exploit old vulnerabilities. Recently, a new ransomware appeared in NoName's arsenal — ScRansom, which replaced Scarab.
Researchers have been tracking the group's activities since 2023, giving it the codename CosmicBeetle. ESET emphasizes that despite ScRansom's lower sophistication compared to other known threats, this ransomware continues to evolve and poses a threat.
ScRansom supports partial encryption with different speed modes, giving attackers flexibility. The program also replaces the contents of the files with a permanent value, making them impossible to recover. The ransomware is capable of working with all types of media — local, remote, and removable. Before running encryption, ScRansom disables key Windows processes and services, including Windows Defender, shadow copies, and virtualization-related processes.
ScRansom encryption uses a complex scheme by combining AES-CTR-128 and RSA-1024 algorithms. However, the multi-step encryption process sometimes leads to errors that can prevent decryption even if the correct keys are available. In one case, the victim obtained 31 decryption keys but was never able to recover all the files.
ScRansom continues to evolve. The virus itself is written in the Delphi language, like other CosmicBeetle tools. Interestingly, encryption requires human intervention to run, making it difficult to detect in automated sandboxes. The latest versions of the virus are automated and require minimal intervention. ScRansom attacks files on all disks and uses several encryption modes, one of which completely destroys data, making it impossible to recover it.
In addition to brute force attacks, NoName actively exploits vulnerabilities that are most commonly found in the infrastructure of small and medium-sized companies. These include CVE-2017-0144 (EternalBlue), CVE-2020-1472 (ZeroLogon), FortiOS SSL-VPN (CVE-2022-42475) vulnerabilities, and vulnerabilities in Veeam and Active Directory. NoName attacks also exploit the CVE-2017-0290 vulnerability through a special script that disables Windows security features.
The group's attempts to assert itself are not limited to the introduction of new ransomware. Researchers noticed that CosmicBeetle began exploiting the leaked source code of the LockBit virus, mimicking a known criminal group in both ransom demands and data leak sites. This helps convince victims to pay the ransom, thinking that they are dealing with more experienced attackers.
In September 2023, CosmicBeetle created a website that is a copy of the LockBit website, which published the data of victims affected not only by NoName, but also by LockBit itself. In November, the attackers went further, registering the domain lockbitblog[.] info and using the LockBit brand for further attacks.
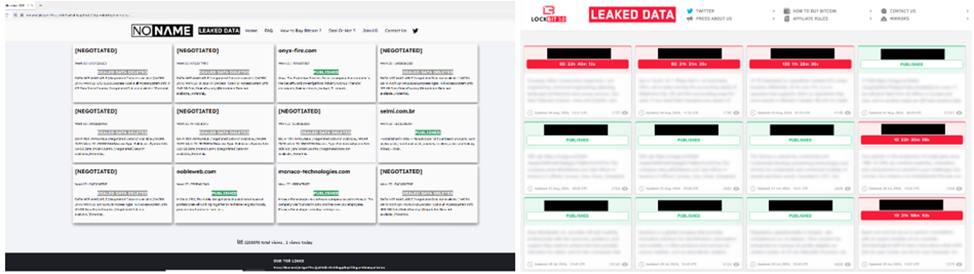
NoName Leak Site (left) and LockBit Site (right)
Using leaked encryption tools, as is the case with LockBit, is a common practice for inexperienced ransomware groups. This helps them not only to take advantage of a recognizable brand, but also to get a reliably working sample of the ransomware. In one incident, which began with a failed attempt to deploy ScRansom, the hackers used RansomHub's tools a few days later, leading researchers to speculate on a possible partnership between NoName and the group.
Although there is no definitive evidence of cooperation, the active development of ScRansom and the transition to the use of LockBit tools indicate that NoName is not going to stop its activities.
Source
The NoName ransomware group has been trying to build a reputation for itself for over three years by targeting small and medium-sized businesses around the world with its ransomware. ESET specialists suggested that NoName now cooperates with RansomHub as a partner.
Hackers use customized tools that are part of the Spacecolon malware family. To penetrate the network, cybercriminals use brute-force attack methods, as well as exploit old vulnerabilities. Recently, a new ransomware appeared in NoName's arsenal — ScRansom, which replaced Scarab.
Researchers have been tracking the group's activities since 2023, giving it the codename CosmicBeetle. ESET emphasizes that despite ScRansom's lower sophistication compared to other known threats, this ransomware continues to evolve and poses a threat.
ScRansom supports partial encryption with different speed modes, giving attackers flexibility. The program also replaces the contents of the files with a permanent value, making them impossible to recover. The ransomware is capable of working with all types of media — local, remote, and removable. Before running encryption, ScRansom disables key Windows processes and services, including Windows Defender, shadow copies, and virtualization-related processes.
ScRansom encryption uses a complex scheme by combining AES-CTR-128 and RSA-1024 algorithms. However, the multi-step encryption process sometimes leads to errors that can prevent decryption even if the correct keys are available. In one case, the victim obtained 31 decryption keys but was never able to recover all the files.
ScRansom continues to evolve. The virus itself is written in the Delphi language, like other CosmicBeetle tools. Interestingly, encryption requires human intervention to run, making it difficult to detect in automated sandboxes. The latest versions of the virus are automated and require minimal intervention. ScRansom attacks files on all disks and uses several encryption modes, one of which completely destroys data, making it impossible to recover it.
In addition to brute force attacks, NoName actively exploits vulnerabilities that are most commonly found in the infrastructure of small and medium-sized companies. These include CVE-2017-0144 (EternalBlue), CVE-2020-1472 (ZeroLogon), FortiOS SSL-VPN (CVE-2022-42475) vulnerabilities, and vulnerabilities in Veeam and Active Directory. NoName attacks also exploit the CVE-2017-0290 vulnerability through a special script that disables Windows security features.
The group's attempts to assert itself are not limited to the introduction of new ransomware. Researchers noticed that CosmicBeetle began exploiting the leaked source code of the LockBit virus, mimicking a known criminal group in both ransom demands and data leak sites. This helps convince victims to pay the ransom, thinking that they are dealing with more experienced attackers.
In September 2023, CosmicBeetle created a website that is a copy of the LockBit website, which published the data of victims affected not only by NoName, but also by LockBit itself. In November, the attackers went further, registering the domain lockbitblog[.] info and using the LockBit brand for further attacks.

NoName Leak Site (left) and LockBit Site (right)
Using leaked encryption tools, as is the case with LockBit, is a common practice for inexperienced ransomware groups. This helps them not only to take advantage of a recognizable brand, but also to get a reliably working sample of the ransomware. In one incident, which began with a failed attempt to deploy ScRansom, the hackers used RansomHub's tools a few days later, leading researchers to speculate on a possible partnership between NoName and the group.
Although there is no definitive evidence of cooperation, the active development of ScRansom and the transition to the use of LockBit tools indicate that NoName is not going to stop its activities.
Source

