Man
Professional
- Messages
- 3,221
- Reaction score
- 1,187
- Points
- 113

With Google moving away from passwords and toward Passkey by default, it seems that the concept of text passwords (passphrases) is itself obsolete. Indeed, in some cases, you can achieve a sufficient level of security without passwords at all.
For example, a simple utility called horcrux splits a file into several encrypted parts (e.g., five), and to decrypt and restore the original text, you don’t need a password, but you need to find and combine several of these parts (e.g., three). It is assumed that the individual parts themselves are stored by different people in different places and/or securely hidden, for example, in different places of the house, safes, bank cells, etc.
* Horcrux is a magical artifact created with the help of dark magic, from the Harry Potter universe.
The general principle of the program is shown on KDPV. The program has horcruxtwo commands: splitand bindfor splitting the file and joining the parts (horcruxes). As you might guess, the Shamir secret sharing scheme is used here.
For example, if the current directory contains a file named habr.txt, then you can run the split command:
Code:
$ horcrux split habr.txtThe utility will ask how many Horcruxes to create and how many will be needed to restore the original file. If we want five and three, then we specify these numbers - and the program creates files as follows: Alternatively, you can immediately specify these parameters in the command line:
Code:
habr_1_of_5.horcrux
habr_2_of_5.horcrux
...
Code:
$ horcrux -t 3 -n 5 split habr.txtThe result will be identical.
As we can see, each of the encrypted files is larger than the original:
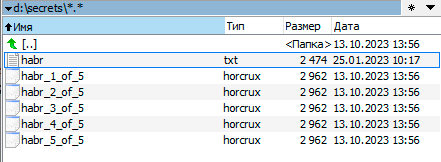
This indicates that according to Shamir's scheme, it is not the file itself that is divided, but the decryption key. In reality, each of the fragments stores all the original information.
All that remains is to scatter the Horcruxes around the house on USB flash drives or on different hosting sites on the Internet.
To restore the original file, you now need to remember not the password, but the places where the Horcruxes are hidden. This can also be a difficult task, especially if the artifacts are very well hidden, for example, buried in an uninhabited area without identification marks.
Restoring the original file in the presence of encrypted parts is carried out by a command bindindicating the folder where the files are located:
Code:
$ horcrux bind d:\secrets\The original file will be recreated.
Theoretically, this program can replace or complement classic encryption (with a password) in the following cases:
- for long-term storage of confidential information for decades, when a person does not feel confident that he will save or remember the password;
- to transmit confidential information over open channels to minimize the risk of interception.
It should be added that encrypting Horcruxes does not cancel the ability to encrypt plaintext before splitting it into parts. That is, you can encrypt (or archive) a file using a password - and then split it into parts. This will provide an additional level of protection.
Installing the program under Linux:
Code:
curl https://api.github.com/repos/jesseduffield/horcrux/releases/latest | \
jq '.assets[] | select(.browser_download_url | endswith("_Linux_x86_64.tar.gz")) | .browser_download_url' | \
xargs curl -Lo /tmp/horcrux.tar.gz && \
tar xfz /tmp/horcrux.tar.gz -C /tmp && \
rm /tmp/horcrux.tar.gz && \
sudo mv /tmp/horcrux /usr/local/bin/horcruxInstallation under Windows via the Scoop console installer:
Just first you need to install Scoop using the following commands in the console:
Code:
Set-ExecutionPolicy RemoteSigned -Scope CurrentUser # Optional: Needed to run a remote script the first time
irm get.scoop.sh | iexIf you run the console as an administrator, Scoop is installed with the following command:
Code:
iex "& {$(irm get.scoop.sh)} -RunAsAdmin"By the way, there is a similar tool paperback, it also splits the decryption key according to the Shamir scheme, and prints it out on paper (generates PDF). You don't have to remember the password either, the main thing is to collect the parts of the key on paper. Below are examples.
Main document:

Part of the key:

A Caveat About Block Ciphers
The program horcruxuses the AES cipher in OFB mode.
The output feedback (OFB) mode turns the block cipher into a synchronous stream cipher. During encryption, blocks of the key stream are generated. They are combined with blocks of the plaintext to obtain the ciphertext.
Due to the XOR symmetry, encryption and decryption are performed in the same way:
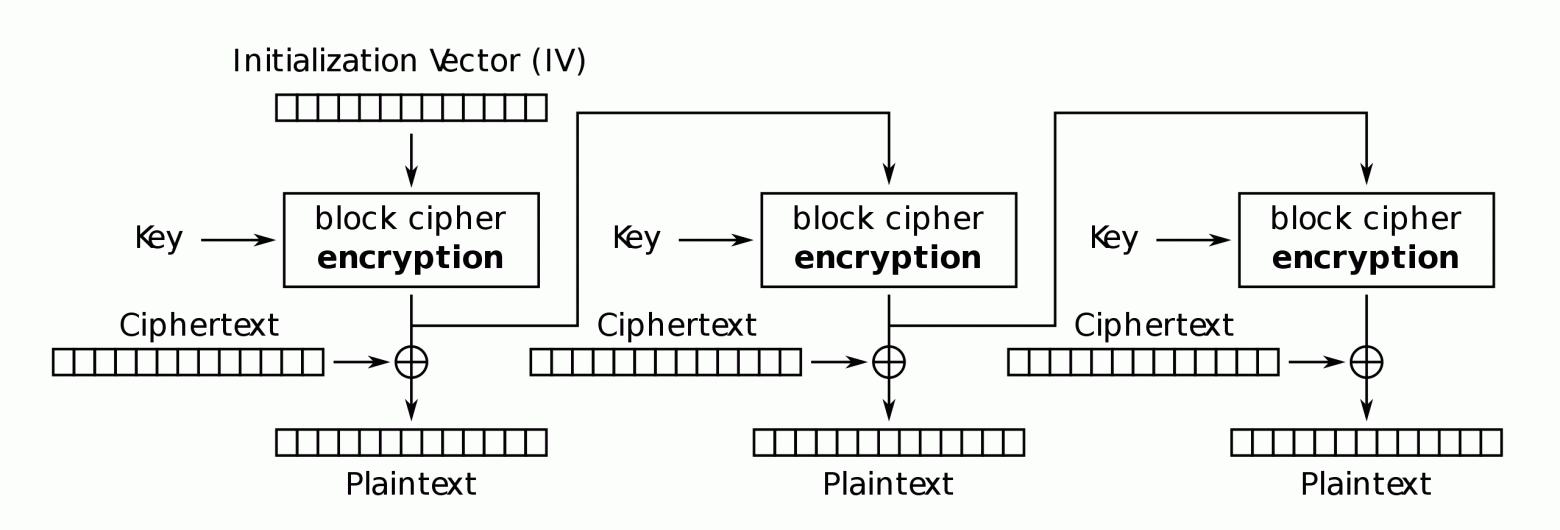
Encryption and decryption in OFB mode are performed according to the same scheme.
It should be noted that this is not the most reliable option from a security point of view. If we simplify the above scheme, the stream cipher works as follows (via XOR):
Code:
ciphertext = plaintext ^ generated_keystream(key)
plaintext = ciphertext ^ generated_keystream(key)The problem here is quite obvious, and it is common to all ciphers of this class. As in other stream ciphers, replacing one bit in the ciphertext results in replacing a bit in the plaintext in the same place. This property allows many error-correcting codes to function normally even when applied before encryption.
On the other hand, it gives potential attackers the opportunity to "damage" encrypted files.
Very often, an attacker knows the contents of a part of the plaintext - for example, these can be standard file headers of a certain format. Having the original text and the encryption result, he can perform calculations - and replace specific bytes of the ciphertext with values that will give the desired result after decryption. That is, he can replace fragments of the encrypted file without knowing the key. This feature should always be kept in mind when working with block ciphers.
Source

