Lord777
Professional
- Messages
- 2,577
- Reaction score
- 1,553
- Points
- 113

A mobile phone is a universal bug that a person constantly and voluntarily carries with them. The perfect device for round-the-clock surveillance and listening. To the delight of intelligence agencies and hackers, most people do not even know how easy it is to connect to the communication channel and listen to their conversations, read SMS and messages in instant messengers.
1. SORM - official wiretapping service
The most obvious method is official wiretapping by the state.In many countries around the world, telephone companies are required to provide access to wiretapping lines for the competent authorities. For example, in Russia, in practice, this is done technically through SORM - a system of technical means to ensure the functions of operational search activities.
Each operator is required to install an integrated SORM module on its PBX.
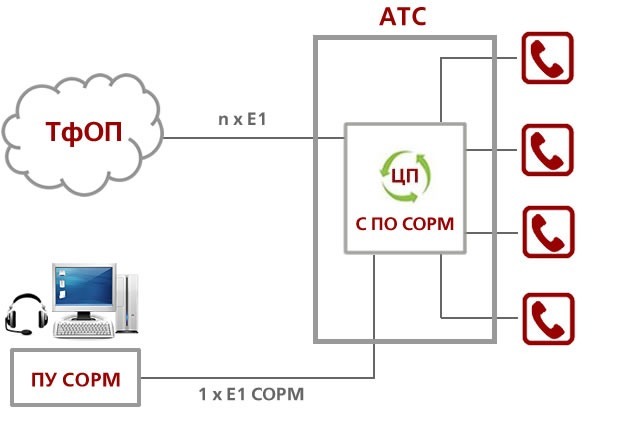
If the telecom operator has not installed equipment for wiretapping all users phones on its PBX, its license in Russia will be revoked. Similar total wiretapping programs operate in Kazakhstan, Ukraine, the United States, the United Kingdom (Interception Modernisation Programme, Tempora) и других странах.
The corruption of government officials and intelligence officers is well known to everyone. If they have access to the system in "god mode", then for an appropriate fee, you can also get it. As in all state systems, in the Russian SORM — a big mess and typically Russian fuck. Most technical specialists actually have very low qualifications, which allows unauthorized access to the system without being noticed by the special services themselves.
Telecom operators do not control when and which subscribers are listened to on SORM lines. The operator does not check in any way whether there is a court sanction for wiretapping a particular user.
"Take a certain criminal case on the investigation of an organized criminal group, which lists 10 numbers. You need to listen to a person who has nothing to do with this investigation. You just finish off this number and say that you have operational information that this is the number of one of the leaders of a criminal group, "knowledgeable people say from the website "Agentura.ru".
Thus, through SORM, you can listen to anyone on "legal" grounds. This is a secure connection.
2. Wiretapping through an operator
Mobile operators generally view the list of calls and the history of mobile phone movements without any problems, which is registered at various base stations based on its physical location. To get call records, like the special services, the operator needs to connect to the SORM system.По new Russian laws, operators will be required to store audio recordings of all users ' conversations from six months to three years (the exact time limit is currently being agreed). The law comes into force in 2018.
3. Connecting to the SS7 signal network
Knowing the victim's phone number, it is possible to listen to the phone by connecting to the network of the mobile network operator through vulnerabilities in the SS7 signaling protocol (Signaling System No. 7).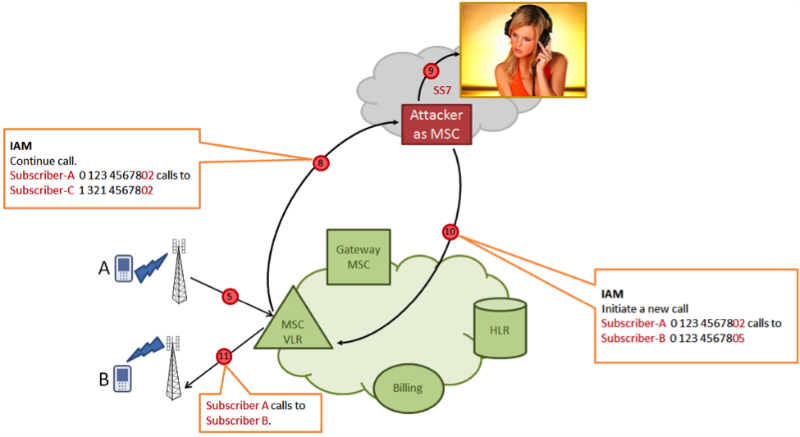
Security experts describe this technique in this way.
The attacker is embedded in the SS7 signaling network, in the channels of which it sends a service message Send Routing Info For SM (SRI4SM), specifying the phone number of the attacked subscriber as a parameter. In response, Subscriber A's home network sends the attacker some technical information: the IMSI (International Subscriber Identifier) and the address of the MSC switch that currently serves the subscriber.
Then the attacker uses the Insert Subscriber Data (ISD) message to inject the updated subscriber profile into the VLR database, changing the billing system address to the address of his own pseudo-billing system. Then, when the attacked subscriber makes an outgoing call, his switch turns instead of the real billing system to the attacker's system, which instructs the switch to redirect the call to a third party, again controlled by the attacker. On this third party, a conference call is collected from three subscribers, two of which are real (caller A and called B), and the third is introduced by an attacker without authorization and can listen to and record the conversation.
The scheme is quite working. Experts say that when developing the SS7 signal network, it did not have any protection mechanisms against such attacks. It was assumed that this system is already closed and protected from external connections, but in practice, an attacker can find a way to join this signal network.
You can connect to the SS7 network in any country in the world, for example, in a poor African country — and you will have access to switches from all operators in Russia, the United States, Europe, and other countries. This method allows you to listen to any subscriber in the world, even on the other side of the globe. Intercepting incoming SMS messages from any subscriber is also elementary, as is transferring a balance via a USSD request (for more information, see the presentation of Sergey Puzankov and Dmitry Kurbatov at the PHDays IV hacker conference).
4. Connecting to the cable
From the documents of Edward Snowden, it became known that the special services not only" officially " listen to phones through communication switches, but also connect directly to optical fiber, recording all traffic in its entirety. This allows you to listen to foreign operators who do not allow you to officially install listening equipment on their PBX.This is probably a fairly rare practice for international espionage. Since PBX stations in Russia already have listening equipment everywhere, there is no special need to connect to fiber. It may make sense to use this method only for intercepting and recording traffic in local networks at local PBX stations. For example, to record internal conversations in the company, if they are carried out within the local PBX or via VoIP.
5. Installing a Spy Trojan
At the domestic level, the easiest way to listen to a user's conversations on a mobile phone, Skype, and other programs is simply to install a Trojan on their smartphone. This method is available to everyone, and it does not require the authority of state special services or a court decision.Abroad, law enforcement agencies often purchase special Trojans that use unknown 0day vulnerabilities in Android and iOS to install programs. Such Trojans are developed by companies like Gamma Group (the FinFisher).
Russian law enforcement agencies do not really need to install Trojans, unless they need the ability to activate the smartphone's microphone and record even if the user is not talking on a mobile phone. In other cases, SORM does a great job with wiretapping. Therefore, Russian security services are not actively implementing Trojans. But for unofficial use, it's a favorite hacking tool.
Wives spy on their husbands, businessmen study the activities of competitors. In Russia, Trojan software is widely used for wiretapping by private clients.
The Trojan is installed on a smartphone in various ways: through a fake software update, through an email with a fake app, through a vulnerability in Android, or in popular software such as iTunes.
New vulnerabilities in programs are found literally every day, and then very slowly closed. For example, the FinFisher Trojan was installed through a уязвимость в iTunes, which Apple did not close from 2008 to 2011. Through this hole, it was possible to install any software on behalf of Apple on the victim's computer.
You may already have such a Trojan installed on your smartphone. Have you ever felt that your smartphone's battery has been draining a little faster than it should?
6. Updating the app
Instead of installing a special spy Trojan, an attacker can do even more correctly: choose an application that you voluntarily install on your smartphone, and then give it all the permissions to access phone calls, record conversations, and transfer data to a remote server.For example, it can be a popular game that is distributed through the "left" directories of mobile applications. At first glance, it looks like an ordinary game, but with the function of wiretapping and recording conversations. Very convenient. The user allows the program to access the Internet with their own hands, where it sends files with recorded conversations.
Alternatively, malicious app functionality can be added as an update.
7. Fake base station
A fake base station has a stronger signal than a real BS. Due to this, it intercepts subscriber traffic and allows you to manipulate data on your phone. It is known that fake base stations are widely used by law enforcement agencies abroad.In the US, a fake BS model called StingRay is popular.

And not only law enforcement agencies use such devices. For example, merchants in China often use fake BS to send mass spam to mobile phones that are located within a radius of hundreds of meters around. In general, in China, the production of "fake honeycombs" is put on stream, so in local stores it is not a problem to find a similar device assembled literally on the knee.
8. Femtocell Hacking
Recently, some companies have been using femtocells — low-power miniature cellular communication stations that intercept traffic from mobile phones located in the coverage area. This femtocell allows you to record calls from all employees of the company before redirecting calls to the base station of mobile operators.Accordingly, to eavesdrop on the subscriber, you need to install your own femtocell or hack the operator's original femtocell.
9. Mobile system for remote wiretapping
In this case, the radio antenna is installed near the subscriber (works at a distance of up to 500 meters). A directional antenna connected to the computer intercepts all phone signals, and when it is finished, it is simply taken away.Unlike a fake femtocell or Trojan, here an attacker does not need to worry about breaking into the site and installing the femtocell, and then removing it (or deleting the Trojan without leaving any traces of hacking).
The capabilities of modern PCs are enough to record a GSM signal on a large number of frequencies, and then crack the encryption using rainbow tables (here is a description of the technique from a well-known specialist in this field, Carsten Nohl).
If you voluntarily carry a universal bug with you, you automatically collect an extensive dossier on yourself. The only question is who will need this file. But if necessary, he can get it without much difficulty.

