Tomcat
Professional
- Messages
- 2,695
- Reaction score
- 1,059
- Points
- 113
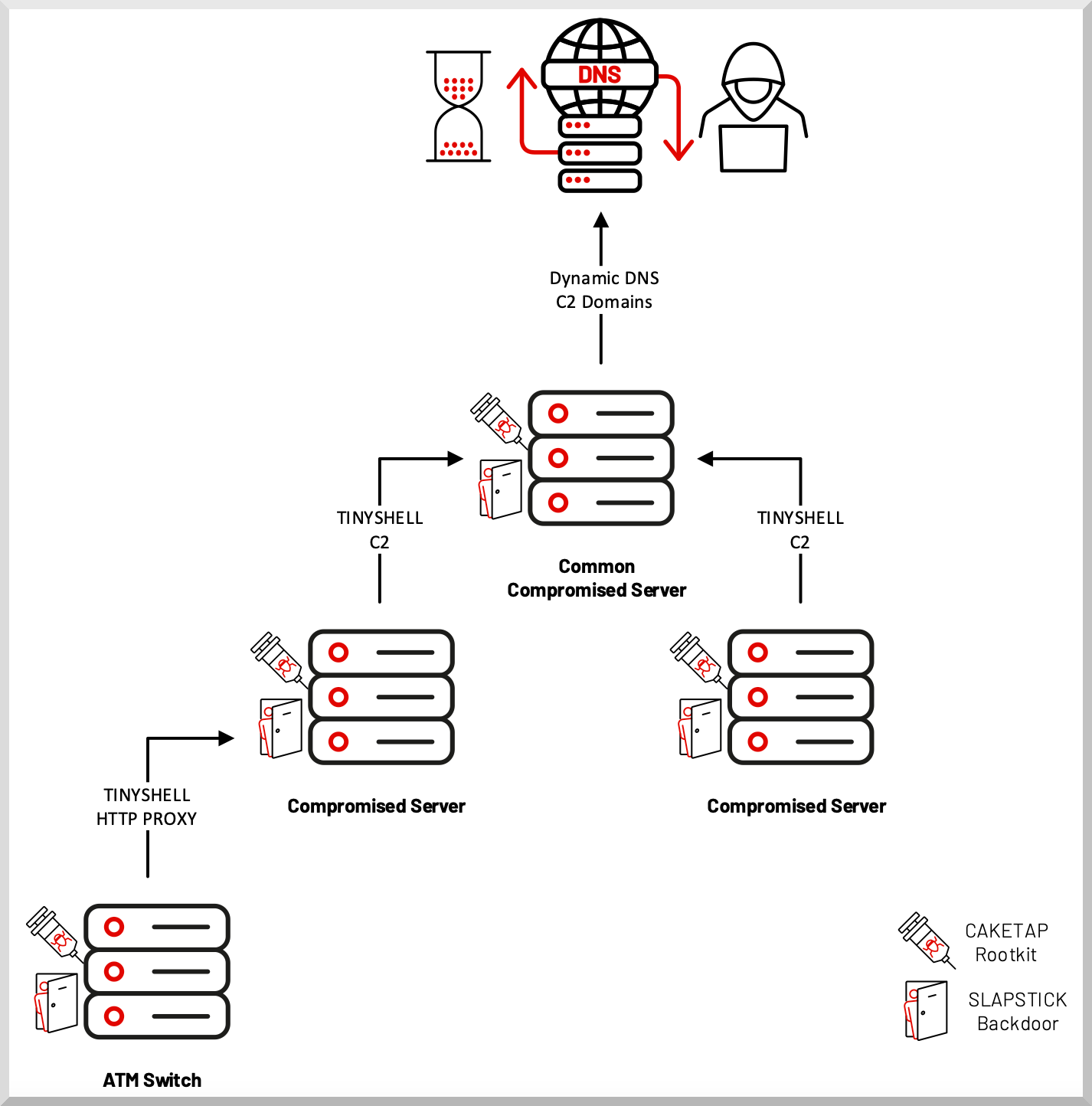
While monitoring the activity of the LightBasin cybercriminal group, experts came across a previously unknown Unix rootkit that is used to steal payment data from ATMs. Using this malware, attackers can conduct unauthorized transactions.
The operators of the new rootkit are known for their attacks on telecommunications companies using custom samples of the malware. Mandiant researchers, who described LightBasin activity in 2020, have now published a new report on the cyber group's activities.
The rootkit is a Unix kernel module called "Caketap" that operators install on servers running the Oracle Solaris operating system.
During operation, Caketap masks the Internet connection, processes and files, installing several hooks in system functions in parallel.
The main goal of the malware is to intercept bank card data and PIN codes processed by an ATM, in order to then make transfers and conduct transactions. To do this, Caketap must receive messages intended for the Payment Hardware Security Module (HSM).
HSM is known to be used in the banking industry to generate, manage and validate cryptographic keys for PIN codes and EMV chips. Having intercepted such messages, Caketap substitutes the received card data and generates a valid response.
At the second stage of the attack, the rootkit stores valid messages corresponding to legitimate PAN numbers (Primary Account Numbers) and sends them to the HSM. At the same time, the malware acts extremely carefully, remaining invisible.
(c) https://www.anti-malware.ru/news/2022-03-18-111332/38359
The operators of the new rootkit are known for their attacks on telecommunications companies using custom samples of the malware. Mandiant researchers, who described LightBasin activity in 2020, have now published a new report on the cyber group's activities.
The rootkit is a Unix kernel module called "Caketap" that operators install on servers running the Oracle Solaris operating system.
During operation, Caketap masks the Internet connection, processes and files, installing several hooks in system functions in parallel.
The main goal of the malware is to intercept bank card data and PIN codes processed by an ATM, in order to then make transfers and conduct transactions. To do this, Caketap must receive messages intended for the Payment Hardware Security Module (HSM).
HSM is known to be used in the banking industry to generate, manage and validate cryptographic keys for PIN codes and EMV chips. Having intercepted such messages, Caketap substitutes the received card data and generates a valid response.
At the second stage of the attack, the rootkit stores valid messages corresponding to legitimate PAN numbers (Primary Account Numbers) and sends them to the HSM. At the same time, the malware acts extremely carefully, remaining invisible.

“We believe that the UNC2891 (LightBasin) group is behind CAKETAP and has launched a massive campaign. Attackers are trying to withdraw as much money as possible from ATMs of several credit institutions,” Mandiant experts write in the report.
(c) https://www.anti-malware.ru/news/2022-03-18-111332/38359
