Man
Professional
- Messages
- 3,221
- Reaction score
- 1,187
- Points
- 113

End-to-end encryption is gradually becoming a standard on file hosting and cloud services. Even if you store backup copies in a safe, encryption will not be superfluous. And if you send files to a remote server, even more so.
Although the question of government control measures remains, but at the moment, the use of strong cryptography is a legal and reliable means of protecting information.
There are a number of programs that specialize in encryption of backups. They complement the standard toolkit for file synchronization and backup, including rcp, scp, rsync, casync, restic, bupstash and other tools. All this software can be used in different combinations to achieve an acceptable result. Some programs are more versatile and perform several functions simultaneously, while others specialize in one thing.
New tools appear constantly, such as kopia. But backup is a specific area. The main thing here is reliability. Therefore, old proven tools are rarely abandoned. New ones are usually trusted only some time after their appearance, and even then, if no serious problems have arisen during all the previous time. Unfortunately, not all programs pass such a test, but BorgBackup has passed.
BorgBackup: Time-tested
The BorgBackup backup utility is a deduplicator with compression and encryption, i.e. a 3-in-1 tool. In some functionality, it can replace restic, kopia, attic and other programs in this area. BorgBackup is considered a relatively stable option for constant use (for example, restic is known to have problems when working with the CIFS/SMB protocol, but BorgBackup does not have such problems).
Main functions:
- Backup compression LZ4, zlib, LZMA, zstd (since version 1.1.4), saving space on storage devices
- Secure encryption with authentication
- Ability to mount backups using FUSE
- Easy installation on various platforms: Linux, macOS, BSD, etc.
- Open source, free license, large user community
Example of use:
Code:
$ borg create --stats --progress --compression lz4 /media/backup/borgdemo::bac
kup1 Wallpaper
Enter passphrase for key /media/backup/borgdemo:
------------------------------------------------------------------------------
Archive name: backup1
Archive fingerprint: 9758c7db339a066360bffad17b2ffac4fb368c6722c0be3a47a7a9b63
1f06407
Time (start): Fri, 2023-01-08 21:54:06
Time (end): Fri, 2023-01-08 21:54:17
Duration: 11.40 seconds
Number of files: 1050
Utilization of maximum supported archive size: 0%
------------------------------------------------------------------------------
Original size Compressed size Deduplicated size
This archive: 618.96 MB 617.47 MB 561.67 MB
All archives: 618.96 MB 617.47 MB 561.67 MB
Unique chunks Total chunks
Chunk index: 999 1093
------------------------------------------------------------------------------Adding single files happens almost instantly thanks to deduplication:
Code:
$ borg create --stats --progress --compression lz4 /media/backup/borgdemo::bac
kup2 Wallpaper
Enter passphrase for key /media/backup/borgdemo:
------------------------------------------------------------------------------
Archive name: backup2
Archive fingerprint: 5aaf03d1c710cf774f9c9ff1c6317b621c14e519c6bac459f6d64b31e
3bbd200
Time (start): Fri, 2023-01-08 21:54:56
Time (end): Fri, 2023-01-08 21:54:56
Duration: 0.33 seconds
Number of files: 1051
Utilization of maximum supported archive size: 0%
------------------------------------------------------------------------------
Original size Compressed size Deduplicated size
This archive: 618.96 MB 617.47 MB 106.70 kB
All archives: 1.24 GB 1.23 GB 561.77 MB
Unique chunks Total chunks
Chunk index: 1002 2187
------------------------------------------------------------------------------For more demo examples, see here.
Bupstash: for single-payers
There is an opinion that on low-power machines and single-board computers like Raspberry Pi, bupstash works more effectively instead of BorgBackup , although this is a relatively new development and the author himself does not recommend running it in production.
Dublicati and Kopia: simple interface
Another utility for backup with encryption is Duplicati. It has the simplest GUI for the average user, there is a version for Windows.

According to some reviews, the program is too unstable to recommend it for permanent backup of important information. But others have been using it for years without any complaints, and the simple interface is available to users of any level.
As an alternative for backup under Windows, the Kopia program has recently appeared (also works on Linux and macOS). It supports deduplication, compression and encryption of backups, copying by mask, templates, etc. Encrypted and compressed backups can be sent to one of the cloud hostings or any remote server via WebDAV and SFTP.
Cloud Services Encryption
Encryption of backups is becoming an industry standard. Amazon S3 recently began automatically encrypting all new objects added to the storage with AES-256 by default. The scheme, called SSE-S3, looks like this:
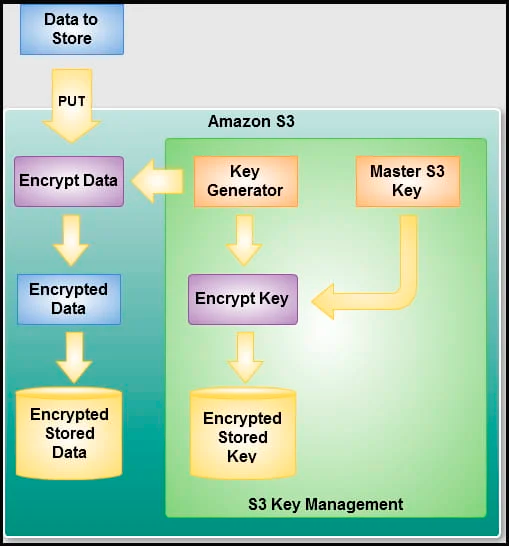
As you can see, encryption occurs on the server side, not on the client side, so this implementation does not fall under the definition of full-fledged end-to-end encryption (E2E). However, an alternative SSE-C scheme has also been implemented, according to which encryption keys are transmitted to the user.
No additional actions are required from administrators, and the performance of I/O operations will not suffer. The scheme applies only to newly written data. Amazon explains that server encryption was implemented more than ten years ago, but now it will become the default standard. In addition, instructions have been published for retroactive encryption of old files saved earlier.
In November 2022, Dropbox announced similar measures. To implement this task, the assets of Boxcryptor, a company that specializes in end-to-end encryption of cloud services, were acquired.
Previously, it was believed that mandatory encryption of cloud data was some kind of exotic option for corporate customers and semi-underground hosting services like Mega.nz from Kim Dotcom. But in recent years, two things have become clear:
- Massive data leaks from cloud services continue.
- Not only corporate but also private users react painfully to leaks of their data, including home photos, videos, etc.
For this reason, E2E is gradually being implemented in mass services such as Dropbox, Amazon S3 and Apple iCloud. The only question that remains is whether a “backdoor” should be left for the competent authorities or whether the protection should be total.
Source

