Father
Professional
- Messages
- 2,602
- Reaction score
- 837
- Points
- 113
PowerHost customers in America and Europe lost access to their websites.
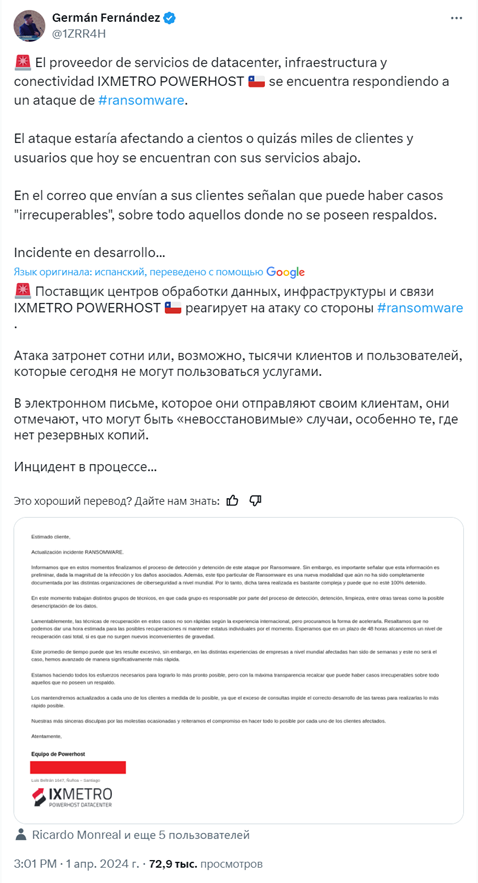
On March 30, the Chilean division of PowerHost, IxMetro, <a>was the victim of a cyberattack</a> by a new group of SEXI ransomware. As a result of the attack, the company's VMware ESXi servers and data backups were encrypted.
PowerHost is a data center, hosting, and internetworking company located in the United States, South America, and Europe.
Some encrypted VMware ESXi servers hosted client VPS servers. Currently, websites or services on VPS servers are unavailable to customers. The company is making efforts to restore terabytes of data from backups, but the latest statement from IxMetro indicates that it is impossible to restore servers, since the backups were also encrypted.
Cybersecurity researcher Herman Fernandez's tweet about the IxMetro attack
PowerHost reported that it is negotiating with cybercriminals to obtain the decryption key . The criminals demanded 2 BTC for each victim, which would amount to about $140 million. The company stressed that all law enforcement agencies unanimously recommend not to negotiate, since in most cases criminals disappear after receiving a ransom.
For VPS customers whose websites were affected by the attack, but who still have the content of the sites, the company offers the creation of new VPS to restore their online presence.
Details about the SEXi ransomware
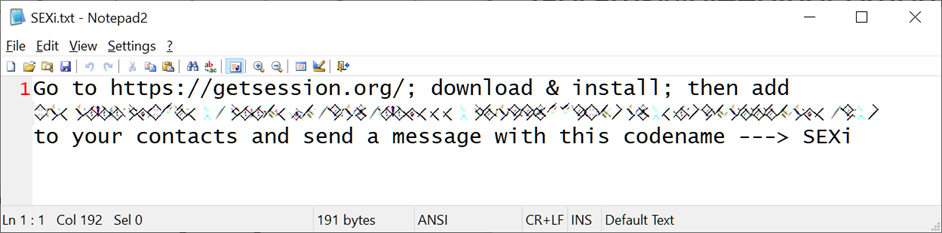
According to cybersecurity researcher Herman Fernandez of CronUp, the Sexi ransomware adds the extension ".SEXi" to encrypted files and creates ransom notes with the name "SEXi.txt". It is known that the group's attacks target only VMware ESXi servers, and it is possible that Windows-based devices may also be attacked in the future.
Sexi Ransom Note
According to BleepingComputer, the infrastructure of the SEXi operation does not have any special characteristics. The ransom notes only contain a message calling you to download the Session app to contact the ransomware at the specified address. All ransom notes have the same contact address in the Session, meaning each attack is not unique.
At the moment, it is not known whether attackers steal data to conduct double-ransomware attacks through data leak sites. However, given that this is a new campaign, the situation may change at any time.
On March 30, the Chilean division of PowerHost, IxMetro, <a>was the victim of a cyberattack</a> by a new group of SEXI ransomware. As a result of the attack, the company's VMware ESXi servers and data backups were encrypted.
PowerHost is a data center, hosting, and internetworking company located in the United States, South America, and Europe.
Some encrypted VMware ESXi servers hosted client VPS servers. Currently, websites or services on VPS servers are unavailable to customers. The company is making efforts to restore terabytes of data from backups, but the latest statement from IxMetro indicates that it is impossible to restore servers, since the backups were also encrypted.

Cybersecurity researcher Herman Fernandez's tweet about the IxMetro attack
PowerHost reported that it is negotiating with cybercriminals to obtain the decryption key . The criminals demanded 2 BTC for each victim, which would amount to about $140 million. The company stressed that all law enforcement agencies unanimously recommend not to negotiate, since in most cases criminals disappear after receiving a ransom.
For VPS customers whose websites were affected by the attack, but who still have the content of the sites, the company offers the creation of new VPS to restore their online presence.
Details about the SEXi ransomware
According to cybersecurity researcher Herman Fernandez of CronUp, the Sexi ransomware adds the extension ".SEXi" to encrypted files and creates ransom notes with the name "SEXi.txt". It is known that the group's attacks target only VMware ESXi servers, and it is possible that Windows-based devices may also be attacked in the future.

Sexi Ransom Note
According to BleepingComputer, the infrastructure of the SEXi operation does not have any special characteristics. The ransom notes only contain a message calling you to download the Session app to contact the ransomware at the specified address. All ransom notes have the same contact address in the Session, meaning each attack is not unique.
At the moment, it is not known whether attackers steal data to conduct double-ransomware attacks through data leak sites. However, given that this is a new campaign, the situation may change at any time.

