Tomcat
Professional
- Messages
- 2,688
- Reaction score
- 1,015
- Points
- 113
How NIST plans to return to the previous pace of work with errors.
The National Institute of Standards and Technology (NIST) has announced a new contract with an external contractor that will help the federal government handle software and hardware vulnerabilities from the NVD database.
In recent months, government officials, cybersecurity experts and cybersecurity specialists have repeatedly expressed concern about the accumulated volume of new vulnerabilities that have not been analyzed or supplemented since February, when the agency announced the cuts. The add-on includes adding contextual data to the vulnerability description.
A NIST spokesperson said that the new contract provides "additional support in processing incoming CVEs" that will be added to the NVD. NIST is confident that the additional support will allow us to return to the processing rates that the institute maintained until February 2024 over the next few months. The agency is working with CISA to add raw CVEs to the database.
NIST expects that the accumulated volume will be eliminated by the end of the fiscal year, which ends on September 30. However, the NIST representative did not answer questions about which company was hired to help handle the vulnerabilities and how much cheaper it is for the government to assign such tasks to third-party organizations.
NIST is working to address "the increasing volume of vulnerabilities through technology and process updates." The agency's goal is to create a program that is sustainable in the long term and supports the automation of vulnerability management, security measurement, and compliance.
NIST assured that it is "fully committed to supporting and modernizing the resource, which is vital for building and maintaining trust in information technology and stimulating innovation." The Agency plans to provide further updates as it attempts to return to a normal level of operational activity.
Since its inception in 2005, NVD has become an indispensable resource for experts and information security professionals. In April, NIST attributed delays in vulnerability analysis to an increase in the volume of software and changes in support for interagency programs. A notice was posted on the agency's website stating that it is "working to create a consortium to address issues in the NVD program and develop improved tools and techniques."
NIST recently had to cut its budget for the current fiscal year by 12% compared to the previous year. Earlier, NVD noted that the staff of NVD employees remained unchanged — 21 people, while the number of incoming vulnerabilities continues to grow.
Researchers from VulnCheck analyzed the activity of NVD since the announcement of the cuts on February 12 and found that out of 12,720 new vulnerabilities, 11,885 were not analyzed or supplemented with important data that helps information security specialists determine which software was affected by the vulnerability.
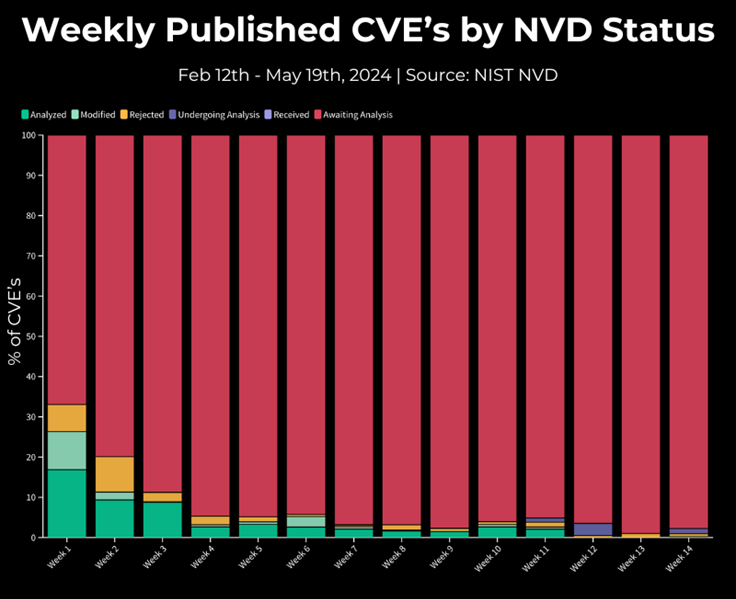
VulnCheck Analysis
On May 8, the CISA agency announced the launch of the Vulnrichment program to add metadata to vulnerabilities. MITRE, which manages the CVE program, also approved new rules for organizations that assign CVEs. Dozens of cybersecurity experts previously signed a letter addressed to Congress and U.S. Commerce Secretary Gina Raimondo, urging them to fund and protect NVD, calling it "a critical infrastructure for a multitude of cybersecurity products."
The National Institute of Standards and Technology (NIST) has announced a new contract with an external contractor that will help the federal government handle software and hardware vulnerabilities from the NVD database.
In recent months, government officials, cybersecurity experts and cybersecurity specialists have repeatedly expressed concern about the accumulated volume of new vulnerabilities that have not been analyzed or supplemented since February, when the agency announced the cuts. The add-on includes adding contextual data to the vulnerability description.
A NIST spokesperson said that the new contract provides "additional support in processing incoming CVEs" that will be added to the NVD. NIST is confident that the additional support will allow us to return to the processing rates that the institute maintained until February 2024 over the next few months. The agency is working with CISA to add raw CVEs to the database.
NIST expects that the accumulated volume will be eliminated by the end of the fiscal year, which ends on September 30. However, the NIST representative did not answer questions about which company was hired to help handle the vulnerabilities and how much cheaper it is for the government to assign such tasks to third-party organizations.
NIST is working to address "the increasing volume of vulnerabilities through technology and process updates." The agency's goal is to create a program that is sustainable in the long term and supports the automation of vulnerability management, security measurement, and compliance.
NIST assured that it is "fully committed to supporting and modernizing the resource, which is vital for building and maintaining trust in information technology and stimulating innovation." The Agency plans to provide further updates as it attempts to return to a normal level of operational activity.
Since its inception in 2005, NVD has become an indispensable resource for experts and information security professionals. In April, NIST attributed delays in vulnerability analysis to an increase in the volume of software and changes in support for interagency programs. A notice was posted on the agency's website stating that it is "working to create a consortium to address issues in the NVD program and develop improved tools and techniques."
NIST recently had to cut its budget for the current fiscal year by 12% compared to the previous year. Earlier, NVD noted that the staff of NVD employees remained unchanged — 21 people, while the number of incoming vulnerabilities continues to grow.
Researchers from VulnCheck analyzed the activity of NVD since the announcement of the cuts on February 12 and found that out of 12,720 new vulnerabilities, 11,885 were not analyzed or supplemented with important data that helps information security specialists determine which software was affected by the vulnerability.

VulnCheck Analysis
On May 8, the CISA agency announced the launch of the Vulnrichment program to add metadata to vulnerabilities. MITRE, which manages the CVE program, also approved new rules for organizations that assign CVEs. Dozens of cybersecurity experts previously signed a letter addressed to Congress and U.S. Commerce Secretary Gina Raimondo, urging them to fund and protect NVD, calling it "a critical infrastructure for a multitude of cybersecurity products."
