Tomcat
Professional
- Messages
- 2,695
- Reaction score
- 1,055
- Points
- 113
Doctor Web warns about the emergence of a new family of banking Trojans for Android devices, called Android.BankBot.Coper. Malware of this family has a modular architecture and a multi-stage infection mechanism, as well as a set of defensive techniques that help them resist removal. All this allows Trojans to remain operational longer and carry out more successful attacks. Currently known banker modifications are aimed at Colombian users, but over time, versions may appear that will attack users from other countries.
All detected samples of Android.BankBot.Coper, examined by our virus analysts, were distributed under the guise of the official software of the credit institution Bancolombia - the Bancolombia Personas application. To make it more convincing, their icon was designed in the same style as that of real bank programs. For comparison, below is an example of a fake icon (left) and an example of icons for real Bancolombia apps (right) available for download on Google Play:


The infection process itself occurs in several stages. The first step is to install the same decoy program that criminals pass off as a banking application. In fact, this is a dropper whose main task is to deliver and install on the target device the main malicious module hidden inside it. Since the logic of operation of the studied modifications of Trojans is almost the same, further description of the mechanism of their functioning will be based on the example of Android.BankBot.Coper.1 .
When launched, the dropper decrypts and runs an executable dex file ( Android.BankBot.Coper.2.origin), which is located in its resources and disguised as a web document named o.htm. This Trojan component plays the role of the second stage of infection. One of its tasks is to gain access to the Accessibility Services of the Android OS, with the help of which the Trojan will be able to completely control the infected device and imitate user actions (for example, clicking on menu buttons and closing windows). To do this, he requests the appropriate permission from the victim. Having successfully obtained the necessary powers, the Trojan carries out all further malicious actions independently. Thus, it tries to disable the Google Play Protect protection built into the operating system, allow the installation of applications from unknown sources, install and run the main malicious module, and also provide it with access to special features.
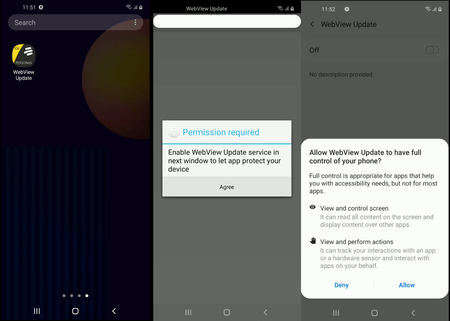
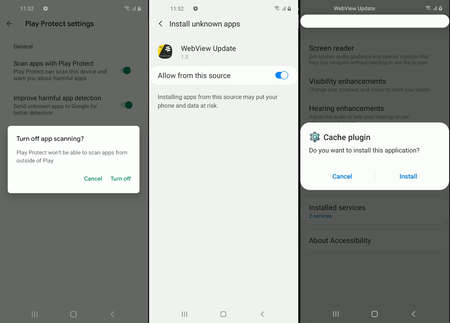
The Trojan decrypts and, using the received privileges, installs a malicious apk package ( Android.BankBot.Coper.2 ), hidden in a second encrypted file and disguised as an audio song named PViwFtl2r3.mp3. It contains the Trojan module Android.BankBot.Coper.1.origin , which performs the main malicious actions required by attackers. This component is installed under the guise of a system application called Cache plugin, which uses the gear icon standard for some Android system programs. Such a name and icon increases the likelihood that users will not see the program as a threat.
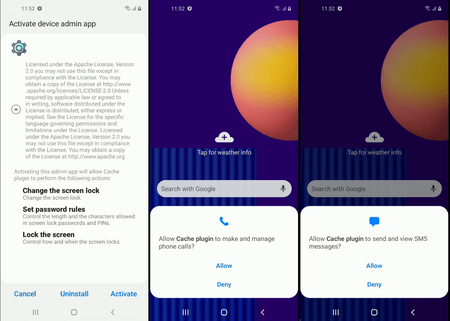
When launched, the module gains access to a number of important functions. Thus, the Trojan requests permission to read and manage notifications and add it to the system battery optimization exclusion list, which will allow it to work constantly. In addition, the Trojan becomes the device administrator and also gains access to manage phone calls and SMS messages.
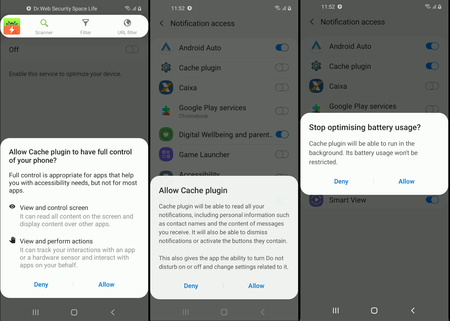
Next, this module hides its icon from the list of applications on the main screen, “hiding” from the user, after which it notifies the C&C server about successful infection and waits for further instructions. The Trojan maintains constant communication with the server, sending requests to it every minute. If necessary, this interval can be changed by the appropriate command. In addition, depending on the response received from the server, the Trojan can change its other settings, including:
When receiving commands directly, Android.BankBot.Coper.1.origin can perform the following actions:
To demonstrate the phishing window, Android.BankBot.Coper.1.origin uses a method that has already become classic for mobile banking Trojans. The content of such a window is downloaded from a remote server and placed in a WebView, which imitates the appearance of the target program to deceive the victim.
The Android.BankBot.Coper Trojans have a number of defense mechanisms. One of them is monitoring the integrity of the main malicious component. If it is deleted, bankers will try to install it again.
The second technique is to monitor events potentially dangerous for Trojans, such as:
In addition, the Android.BankBot.Coper Trojan droppers provide other protection mechanisms. For example, they check whether they are running in a virtual environment, and also monitor the presence of an active SIM card and the user’s country of residence. If the check fails, the bankers immediately terminate their work. It can be assumed that the purpose of such checks is to prevent the installation of the main malicious module in conditions unfavorable for Trojans (for example, under the control of information security specialists or on devices of users from non-target countries) and thereby avoid premature detection. This check is not used in the samples studied, but it can be used in future modifications of malicious applications.
Doctor Web recommends that owners of Android devices install banking applications only from official software catalogs or download them from the official websites of credit institutions if for some reason it is impossible to use the official application store.
Dr.Web anti-virus products for Android successfully detect and remove all known modifications of banking Trojans Android.BankBot.Coper, so they do not pose a threat to our users.
Indicators of compromise
(c) https://news.drweb.ru/show/?i=14259
All detected samples of Android.BankBot.Coper, examined by our virus analysts, were distributed under the guise of the official software of the credit institution Bancolombia - the Bancolombia Personas application. To make it more convincing, their icon was designed in the same style as that of real bank programs. For comparison, below is an example of a fake icon (left) and an example of icons for real Bancolombia apps (right) available for download on Google Play:


The infection process itself occurs in several stages. The first step is to install the same decoy program that criminals pass off as a banking application. In fact, this is a dropper whose main task is to deliver and install on the target device the main malicious module hidden inside it. Since the logic of operation of the studied modifications of Trojans is almost the same, further description of the mechanism of their functioning will be based on the example of Android.BankBot.Coper.1 .
When launched, the dropper decrypts and runs an executable dex file ( Android.BankBot.Coper.2.origin), which is located in its resources and disguised as a web document named o.htm. This Trojan component plays the role of the second stage of infection. One of its tasks is to gain access to the Accessibility Services of the Android OS, with the help of which the Trojan will be able to completely control the infected device and imitate user actions (for example, clicking on menu buttons and closing windows). To do this, he requests the appropriate permission from the victim. Having successfully obtained the necessary powers, the Trojan carries out all further malicious actions independently. Thus, it tries to disable the Google Play Protect protection built into the operating system, allow the installation of applications from unknown sources, install and run the main malicious module, and also provide it with access to special features.


The Trojan decrypts and, using the received privileges, installs a malicious apk package ( Android.BankBot.Coper.2 ), hidden in a second encrypted file and disguised as an audio song named PViwFtl2r3.mp3. It contains the Trojan module Android.BankBot.Coper.1.origin , which performs the main malicious actions required by attackers. This component is installed under the guise of a system application called Cache plugin, which uses the gear icon standard for some Android system programs. Such a name and icon increases the likelihood that users will not see the program as a threat.
When launched, the module gains access to a number of important functions. Thus, the Trojan requests permission to read and manage notifications and add it to the system battery optimization exclusion list, which will allow it to work constantly. In addition, the Trojan becomes the device administrator and also gains access to manage phone calls and SMS messages.


Next, this module hides its icon from the list of applications on the main screen, “hiding” from the user, after which it notifies the C&C server about successful infection and waits for further instructions. The Trojan maintains constant communication with the server, sending requests to it every minute. If necessary, this interval can be changed by the appropriate command. In addition, depending on the response received from the server, the Trojan can change its other settings, including:
- list of control servers;
- a list of target applications that will display phishing windows when launched;
- a list of programs that need to be removed;
- a list of applications that the Trojan will prevent from launching, returning the user to the home screen;
- a list of programs from which notifications will be blocked;
- other parameters.
When receiving commands directly, Android.BankBot.Coper.1.origin can perform the following actions:
- perform USSD requests;
- send SMS;
- lock the device screen;
- unlock the device screen;
- start intercepting SMS;
- stop intercepting SMS;
- show push notifications;
- re-display the phishing window on top of the specified application;
- launch keylogger;
- stop keylogger;
- delete the applications specified in the command;
- remove yourself as well as the dropper from the device.
To demonstrate the phishing window, Android.BankBot.Coper.1.origin uses a method that has already become classic for mobile banking Trojans. The content of such a window is downloaded from a remote server and placed in a WebView, which imitates the appearance of the target program to deceive the victim.
The Android.BankBot.Coper Trojans have a number of defense mechanisms. One of them is monitoring the integrity of the main malicious component. If it is deleted, bankers will try to install it again.
The second technique is to monitor events potentially dangerous for Trojans, such as:
- opening the Google Play Protect page in the Play Store;
- user attempt to change the list of device administrators;
- user access to the section with information about the Trojan application in the list of installed programs;
- an attempt by the user to change the access rights of a Trojan application to accessibility features.
In addition, the Android.BankBot.Coper Trojan droppers provide other protection mechanisms. For example, they check whether they are running in a virtual environment, and also monitor the presence of an active SIM card and the user’s country of residence. If the check fails, the bankers immediately terminate their work. It can be assumed that the purpose of such checks is to prevent the installation of the main malicious module in conditions unfavorable for Trojans (for example, under the control of information security specialists or on devices of users from non-target countries) and thereby avoid premature detection. This check is not used in the samples studied, but it can be used in future modifications of malicious applications.
Doctor Web recommends that owners of Android devices install banking applications only from official software catalogs or download them from the official websites of credit institutions if for some reason it is impossible to use the official application store.
Dr.Web anti-virus products for Android successfully detect and remove all known modifications of banking Trojans Android.BankBot.Coper, so they do not pose a threat to our users.
Indicators of compromise
(c) https://news.drweb.ru/show/?i=14259
Last edited by a moderator:
