Father
Professional
- Messages
- 2,602
- Reaction score
- 831
- Points
- 113
A highly qualified group of ransomware is active from December 2023.
F. A. C. C. T. has identified a new criminal group of ransomware called Muliaka. They started attacking Russian companies in December 2023. In one of the attacks, a popular corporate antivirus program was used to distribute the ransomware on the victim's network and run it on Windows hosts.
In January 2024, one of the Russian enterprises was attacked by Muliaka, as a result of which Windows systems and virtual infrastructure based on VMware ESXi were encrypted. It took criminals about two weeks from the moment they penetrated the victim's IT infrastructure to start the data encryption process. F. A. C. C. T. specialists found out that the affected company's VPN service was used to access the systems, and movement across the network was carried out using the WinRM remote management service.
An interesting fact lies in the origin of the name Muliaka, which F. A. C. C. T. specialists derived from part of the email address used by ransomware to contact victims (kilamulia@proton.me), and the word "mulyaka", meaning dirty muddy water in the South Russian dialect.
To distribute their ransomware program on the victim's network and run it on Windows hosts, the attackers used the installed corporate antivirus software. To launch the cryptographer remotely, the attackers created an installation package and a corresponding task.
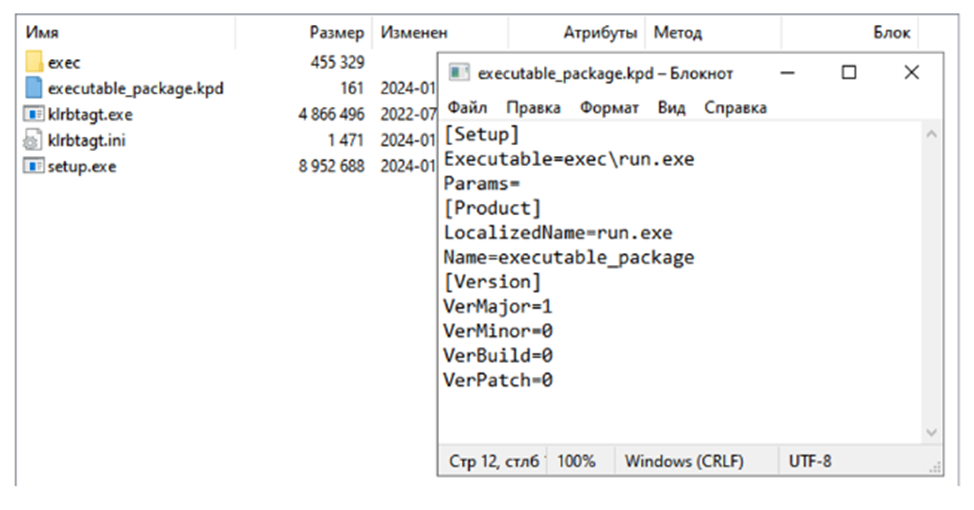
Contents of the ransomware installation package.
Before encryption, the attackers ran the Update.ps1 auxiliary PowerShell script on the hosts, which is designed to stop and disable database and backup services, delete restore points and shadow copies of volumes, and it also disables network adapters on the host, and thereby disconnects the host from the network. This method was previously used by another group of cyber ransomware called OldGremlin.
Experts were particularly interested in the ransomware programs currently in service with the Muliaka group. So, the cryptographer for Windows was developed based on the source codes of the Conti 3 ransomware that were leaked to the public, but it is one of the most interesting modifications of it.
Data encryption was carried out in two stages, which made it possible to quickly block access to data at first, and then complicate the process of restoring them without paying a ransom.
Despite efforts to find a sample of the ESXi ransomware, the criminals managed to remove it. However, the information obtained was enough to find other samples of ransomware for Windows and ESXi. Two months ago, a sample of the ESXi ransomware was uploaded to the VirusTotal portal and is still not detected by any antivirus vendor. It is noted that almost all the samples found were uploaded to the VirusTotal portal from Ukraine.
F. A. C. C. T. specialists joined the investigation of the attack at the stage of restoring the affected company's IT infrastructure. It is not yet clear whether the VPN was the initial entry point for attackers, and it is possible to use phishing or vulnerabilities in public applications as alternative methods of gaining access. The Muliaka group, which has been active since December 2023, demonstrated high qualification, leaving behind a minimum of traces of its activities and preferring to attack exclusively Russian companies, F. A. C. C. T. noted.
F. A. C. C. T. has identified a new criminal group of ransomware called Muliaka. They started attacking Russian companies in December 2023. In one of the attacks, a popular corporate antivirus program was used to distribute the ransomware on the victim's network and run it on Windows hosts.
In January 2024, one of the Russian enterprises was attacked by Muliaka, as a result of which Windows systems and virtual infrastructure based on VMware ESXi were encrypted. It took criminals about two weeks from the moment they penetrated the victim's IT infrastructure to start the data encryption process. F. A. C. C. T. specialists found out that the affected company's VPN service was used to access the systems, and movement across the network was carried out using the WinRM remote management service.
An interesting fact lies in the origin of the name Muliaka, which F. A. C. C. T. specialists derived from part of the email address used by ransomware to contact victims (kilamulia@proton.me), and the word "mulyaka", meaning dirty muddy water in the South Russian dialect.
To distribute their ransomware program on the victim's network and run it on Windows hosts, the attackers used the installed corporate antivirus software. To launch the cryptographer remotely, the attackers created an installation package and a corresponding task.

Contents of the ransomware installation package.
Before encryption, the attackers ran the Update.ps1 auxiliary PowerShell script on the hosts, which is designed to stop and disable database and backup services, delete restore points and shadow copies of volumes, and it also disables network adapters on the host, and thereby disconnects the host from the network. This method was previously used by another group of cyber ransomware called OldGremlin.
Experts were particularly interested in the ransomware programs currently in service with the Muliaka group. So, the cryptographer for Windows was developed based on the source codes of the Conti 3 ransomware that were leaked to the public, but it is one of the most interesting modifications of it.
Data encryption was carried out in two stages, which made it possible to quickly block access to data at first, and then complicate the process of restoring them without paying a ransom.
Despite efforts to find a sample of the ESXi ransomware, the criminals managed to remove it. However, the information obtained was enough to find other samples of ransomware for Windows and ESXi. Two months ago, a sample of the ESXi ransomware was uploaded to the VirusTotal portal and is still not detected by any antivirus vendor. It is noted that almost all the samples found were uploaded to the VirusTotal portal from Ukraine.
F. A. C. C. T. specialists joined the investigation of the attack at the stage of restoring the affected company's IT infrastructure. It is not yet clear whether the VPN was the initial entry point for attackers, and it is possible to use phishing or vulnerabilities in public applications as alternative methods of gaining access. The Muliaka group, which has been active since December 2023, demonstrated high qualification, leaving behind a minimum of traces of its activities and preferring to attack exclusively Russian companies, F. A. C. C. T. noted.
