The brainchild of the hacker group Golden Chickens dealt a powerful blow to the segment of personnel search.
Last week, the Canadian company eSentire reported a failed phishing attack targeting an unnamed industrial services company. Cybersecurity researchers found that attackers used the "More_eggs" malware, disguising it as a resume for a job search.
The attack was carried out in May of this year and was aimed at a recruiter who was deceived by the attackers into believing that he was dealing with an applicant. Scammers attracted him to a fake site, where the victim was asked to upload a malicious file.
The "More_eggs" malware developed by the Golden Chickens group (also known as Venom Spider) is a modular backdoor capable of collecting confidential information from infected devices. Malware is offered to other criminals using the Malware-as-a-Service (MaaS) model.
Last year, eSentire revealed the identities of two people running the operation — Chuck from Montreal and Jack from Romania. The latest chain of attacks using "More_eggs" includes responses to vacancies on the LinkedIn platform, accompanied by a link to the site to download a fake resume.
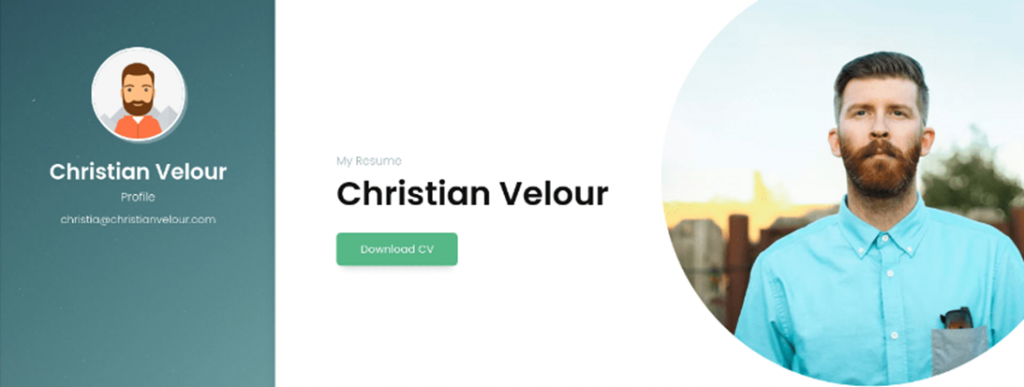
Personal one-page website of the prospective candidate
After clicking on the "Download" button, a malicious shortcut in LNK format is downloaded to the victim's computer, and it initiates further infection. It is noteworthy that switching to the URL from the shortcut, but only a few days after the attack, leads to the display of a summary in HTML format without any signs of malicious activity.
In the active phase of the attack, the LNK file loads a malicious DLL using a legitimate Microsoft program "ie4uinit.exe", after which the library is executed via "regsvr32.exe" to establish persistence in the system, collect data about the infected device, and download additional components, including the More_eggs malware itself.
"More_eggs campaigns continue to use social engineering techniques, posing as job seekers, to trick recruiters into downloading malware," eSentire reported.
In addition, such campaigns that use MaaS are rare and selective compared to typical malicious email distribution networks, which also affects the frequency of their detection by email filters.
To prevent such incidents, it is extremely important to raise staff awareness, strictly follow security policies, check all incoming files for threats, and update security systems in a timely manner and restrict downloading of potentially dangerous files. Training employees to recognize social engineering tricks is also a key protection factor.
Last week, the Canadian company eSentire reported a failed phishing attack targeting an unnamed industrial services company. Cybersecurity researchers found that attackers used the "More_eggs" malware, disguising it as a resume for a job search.
The attack was carried out in May of this year and was aimed at a recruiter who was deceived by the attackers into believing that he was dealing with an applicant. Scammers attracted him to a fake site, where the victim was asked to upload a malicious file.
The "More_eggs" malware developed by the Golden Chickens group (also known as Venom Spider) is a modular backdoor capable of collecting confidential information from infected devices. Malware is offered to other criminals using the Malware-as-a-Service (MaaS) model.
Last year, eSentire revealed the identities of two people running the operation — Chuck from Montreal and Jack from Romania. The latest chain of attacks using "More_eggs" includes responses to vacancies on the LinkedIn platform, accompanied by a link to the site to download a fake resume.

Personal one-page website of the prospective candidate
After clicking on the "Download" button, a malicious shortcut in LNK format is downloaded to the victim's computer, and it initiates further infection. It is noteworthy that switching to the URL from the shortcut, but only a few days after the attack, leads to the display of a summary in HTML format without any signs of malicious activity.
In the active phase of the attack, the LNK file loads a malicious DLL using a legitimate Microsoft program "ie4uinit.exe", after which the library is executed via "regsvr32.exe" to establish persistence in the system, collect data about the infected device, and download additional components, including the More_eggs malware itself.
"More_eggs campaigns continue to use social engineering techniques, posing as job seekers, to trick recruiters into downloading malware," eSentire reported.
In addition, such campaigns that use MaaS are rare and selective compared to typical malicious email distribution networks, which also affects the frequency of their detection by email filters.
To prevent such incidents, it is extremely important to raise staff awareness, strictly follow security policies, check all incoming files for threats, and update security systems in a timely manner and restrict downloading of potentially dangerous files. Training employees to recognize social engineering tricks is also a key protection factor.
