Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113

Shalom, running in the shadows! Hello, random carders. Briefly, for those interested, about the botnet and the main protocol it uses.
Go:
Akamai specialists have released a report in which they reported that botnet operators and cyber espionage groups actively use routers and the Universal Plug and Play (UPnP) protocol to proxy malicious traffic. Thus, criminals hide from the attention of experts and law enforcement agencies, " confusing their tracks." Experts write that more than 65,000 devices are already in use, and more than 4.8 million are potentially vulnerable. Analysts called such malicious activity UPnProxy.
Although the UPnP protocol has been proven insecure for quite some time, it is still widely used for universal automatic configuration of network devices both locally and remotely. The researchers explain that attackers find routers with vulnerable and incorrectly configured UPnP services, since routers are often accessed via the WAN interface, which means that they are accessible from the Internet. Most often, we are talking about "weak" passwords and the use of brute force.
Through UPnP, attackers modify the NAT (Network Address Translation) tables and create custom rules that allow accessing the router's public IP address on a specific port, so that then automatic forwarding to another IP address and port occurs.
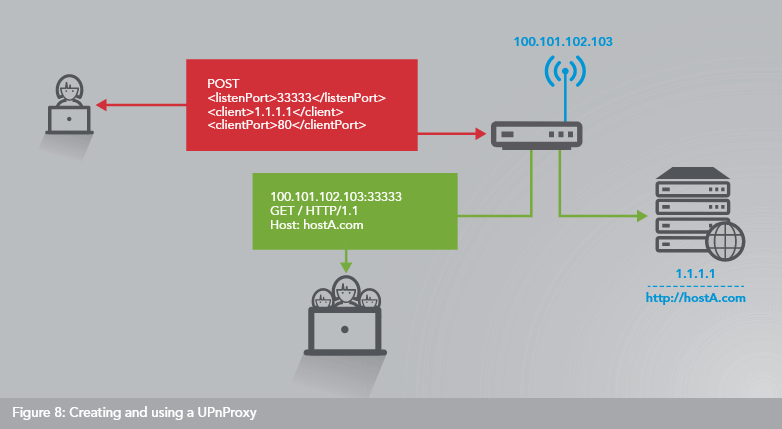

This allows you to use compromised devices both as proxy servers and bypass the firewall by reaching local devices located behind the router. In addition, using UPnProxy, attackers can gain access to the router's control panel, which in normal circumstances should not be accessible. However, the combination of port and IP address, as in the screenshot above, allows attackers to access the "forbidden" internal IP.
Akamai experts warn that various UPnP services are available over the WAN on more than 4.8 million devices. According to the company, at least 65,000 routers were compromised using UPnProxy, but it is extremely difficult to detect such devices: you need to study the NAT tables and in almost every case contact the owner of the device.
Akamai researchers also cite their Symantec colleagues who recently discovered the Inception Framework malware campaign. According to experts, the UPnProxy technique is already being used by the APT group responsible for this campaign, and it is possible that these are government hackers
At the end of their report, Akamai experts provide a long list of manufacturers and specific router models that are potentially vulnerable to this attack vector. It includes 73 vendors and more than 400 devices. At the same time, the researchers warn that in theory, fixing the problem will require considerable effort on the part of manufacturers, who will have to develop and release firmware that changes UPnP settings so that vulnerable services are not detected over the WAN. Currently, Akamai experts advise users who have found their devices among potentially problematic models to change their router to another model that is not on the list.
A special bash script was created to check the routers. Unfortunately, it will be almost useless for ordinary users who are unlikely to be able to connect to their devices via SSH and run such scripts.
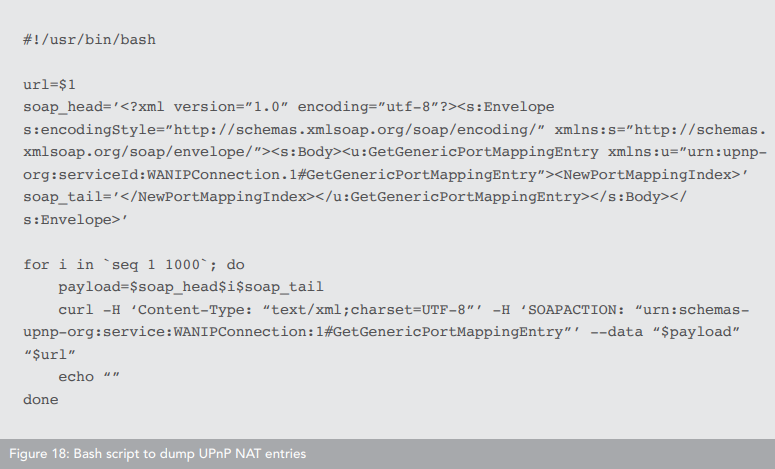
Gentlemen, we draw conclusions and take this little article in mind. It will be useful to earn money online.
xakep.ru

