Carding 4 Carders
Professional
- Messages
- 2,728
- Reaction score
- 1,541
- Points
- 113
If you're the owner, you'd better check your devices.
More than 40,000 Cisco devices running on the IOS XE operating system were compromised after hackers exploited a newly discovered maximum-security vulnerability known as CVE-2023-20198 . At the moment, there is no patch or workaround, and the only recommendation for customers to ensure device security is to " disable the HTTP server function on all systems accessible from the Internet."
Network equipment running on Cisco IOS XE includes enterprise switches, industrial routers, access points, wireless controllers, aggregation and branch routers.
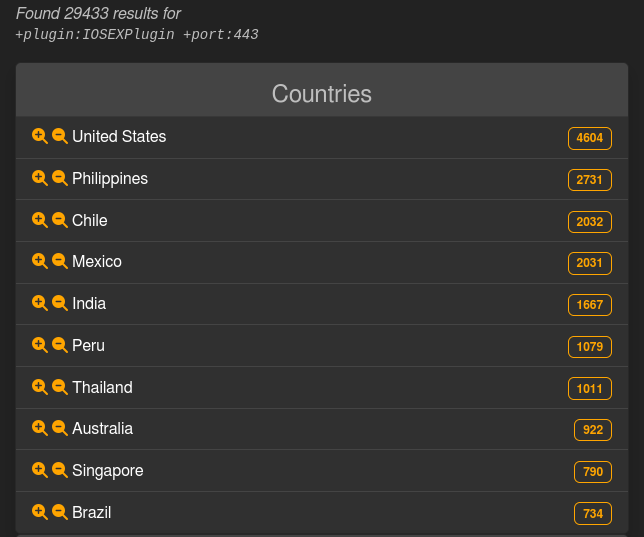
LeakIX results for Cisco IOS XE devices published online,
Initial estimates of compromised Cisco IOS XE devices were around 10,000, but that number began to grow as security researchers began scanning the Internet for a more accurate figure. On Tuesday, LeakIX, a tool for indexing services and web applications available on the public Internet, reported the presence of about 30,000 infected devices.
Using the same verification method from Cisco, Orange's private CERT announced on Wednesday that more than 34,500 Cisco IOS XE IP addresses with malicious code were detected as a result of exploiting CVE-2023-20198.
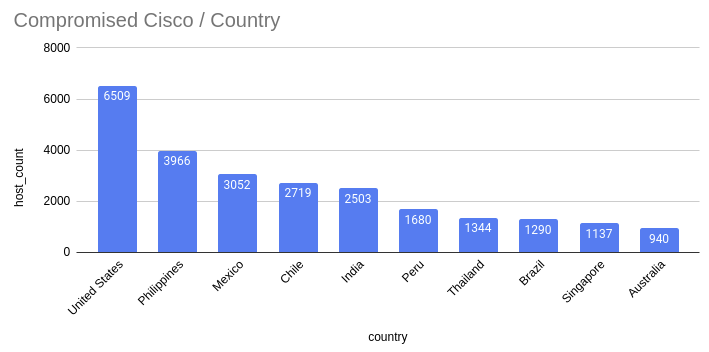
Censys results for Cisco IOS XE hosts on the public web
Below is a screenshot of Shodan results for Cisco devices whose web interface is accessible over the Internet, requested by Simo Kohonen, CEO of cybersecurity company Aves Netsec.
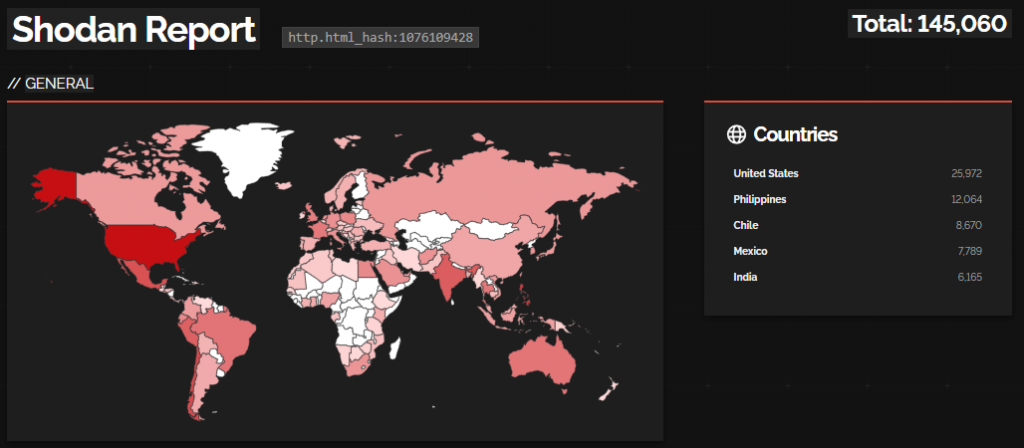
Geography of Cisco devices available on the Internet
Security researcher Yutaka Sejiyama also searched Shodan for Cisco IOS XE devices vulnerable to CVE-2023-20198 and found about 90,000 hosts on the network.
In the United States, many devices are owned by Comcast, Verizon, Cox Communications, Frontier, AT&T, Spirit, CenturyLink, Charter, Cobridge, Windstream, and Google Fiber.
Sejiyama's list also includes medical centers, universities, sheriff's offices, school districts, convenience stores, banks, hospitals, and government agencies whose Cisco IOS XE devices are available online.
Cisco has updated its security guidelines to include new IP addresses and account names for malicious users. New rules have also been added for the open source Snort intrusion detection system and intrusion prevention tools.
Experts report that attackers use malware that is lost after the device is rebooted. However, accounts created with it remain active and have maximum administrative privileges.
Analysis from Cisco showed that the attacker collects detailed information about the system and conducts intelligence. They also erase system logs and delete accounts, probably to hide their tracks.
According to the researchers, all the attacks were carried out by one group. However, the initial method of their distribution has not yet been established.
Cisco has not yet shared additional details about the attacks, but promises to publish more information after the investigation is completed and after the patch is released.
More than 40,000 Cisco devices running on the IOS XE operating system were compromised after hackers exploited a newly discovered maximum-security vulnerability known as CVE-2023-20198 . At the moment, there is no patch or workaround, and the only recommendation for customers to ensure device security is to " disable the HTTP server function on all systems accessible from the Internet."
Network equipment running on Cisco IOS XE includes enterprise switches, industrial routers, access points, wireless controllers, aggregation and branch routers.

LeakIX results for Cisco IOS XE devices published online,
Initial estimates of compromised Cisco IOS XE devices were around 10,000, but that number began to grow as security researchers began scanning the Internet for a more accurate figure. On Tuesday, LeakIX, a tool for indexing services and web applications available on the public Internet, reported the presence of about 30,000 infected devices.
Using the same verification method from Cisco, Orange's private CERT announced on Wednesday that more than 34,500 Cisco IOS XE IP addresses with malicious code were detected as a result of exploiting CVE-2023-20198.

Censys results for Cisco IOS XE hosts on the public web
Below is a screenshot of Shodan results for Cisco devices whose web interface is accessible over the Internet, requested by Simo Kohonen, CEO of cybersecurity company Aves Netsec.

Geography of Cisco devices available on the Internet
Security researcher Yutaka Sejiyama also searched Shodan for Cisco IOS XE devices vulnerable to CVE-2023-20198 and found about 90,000 hosts on the network.
In the United States, many devices are owned by Comcast, Verizon, Cox Communications, Frontier, AT&T, Spirit, CenturyLink, Charter, Cobridge, Windstream, and Google Fiber.
Sejiyama's list also includes medical centers, universities, sheriff's offices, school districts, convenience stores, banks, hospitals, and government agencies whose Cisco IOS XE devices are available online.
Cisco has updated its security guidelines to include new IP addresses and account names for malicious users. New rules have also been added for the open source Snort intrusion detection system and intrusion prevention tools.
Experts report that attackers use malware that is lost after the device is rebooted. However, accounts created with it remain active and have maximum administrative privileges.
Analysis from Cisco showed that the attacker collects detailed information about the system and conducts intelligence. They also erase system logs and delete accounts, probably to hide their tracks.
According to the researchers, all the attacks were carried out by one group. However, the initial method of their distribution has not yet been established.
Cisco has not yet shared additional details about the attacks, but promises to publish more information after the investigation is completed and after the patch is released.
