Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,195
- Points
- 113
The NOOPDOOR malware uses a dual strategy to bypass security.
According to the Japan Computer Response Coordination Center (JPCERT), the MirrorFace hacker group has been targeting media, political organizations, and academic institutions in Japan since 2022. And recently, hackers have also started attacking manufacturers and research institutes. Attacks range from targeted phishing emails to exploiting vulnerabilities in Array AG and FortiGate products.
Hackers use malicious NOOPDOOR software and various tools to steal data after entering the network. NOOPDOOR is a shellcode that is embedded in legitimate applications using two methods.
The first method involves running NOOPDOOR using an XML file containing masked code that is compiled and executed using MSBuild. This method stores encrypted data in specific registers for later use.
The second method uses a DLL file to load NOOPLDR into legitimate applications, hiding its actions through complex code obfuscation methods. Both types extract encrypted data from files or the registry, decrypting it using AES-CBC based on system information.
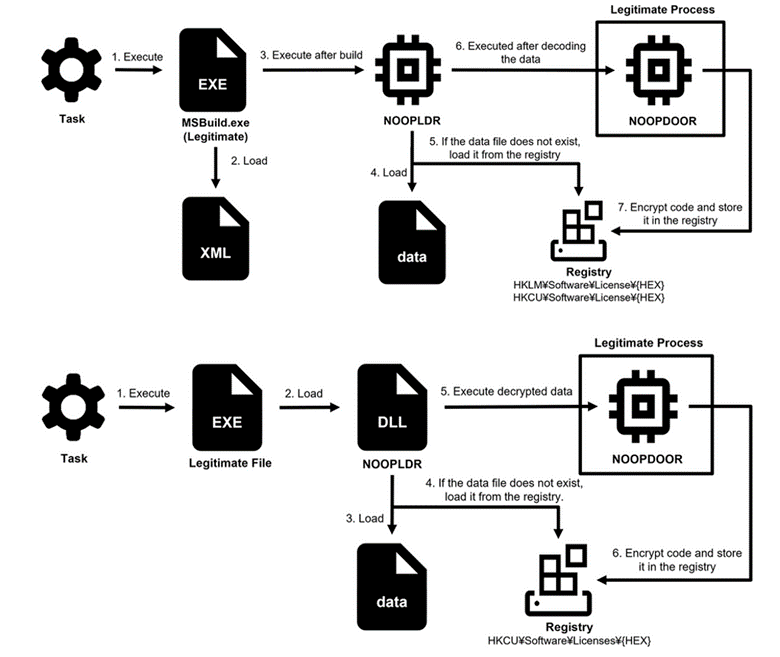
Both NOOPLDR attack methods (XML at the top, DLL at the bottom)
NOOPLDR samples vary in format (XML and DLL) and how they are implemented in Windows processes. XML samples mostly use legitimate processes for execution and store encrypted payloads in the registry. DLL samples show more complex behavior, including installing services and hiding them in the registry.
Some samples use the process "wuauclt.exe" for injections, others rely on "lsass.exe", "svchost.exe" and "vdsldr.exe". DLL variants also use Control Flow Flattening (CFF) obfuscation, complicating analysis. For deobfuscation, JPCERT / CC offers a Python script on GitHub.
NOOPDOOR can communicate on port 443 using the Domain Generation Algorithm (DGA) and receive commands on port 47000. In addition to standard actions such as transferring and executing files, NOOPDOOR can manipulate file timestamps, making it difficult for forensic investigations.
Hackers seek to gain Windows network credentials by analyzing process memory dumps, the domain controller's NTDS.dit database, and sensitive registry keys (SYSTEM, SAM, SECURITY).
After gaining administrator privileges on the Windows network, hackers spread malware through SMB and scheduled tasks, targeting file servers, AD and antivirus management servers.
After penetration, attackers conduct intelligence using the auditpol, bitsadmin, and dfsutil commands. They extract data using WinRAR and SFTP, after pre-scanning files with "dir /s" commands and attacking OneDrive, Teams, IIS, and other services.
The sophistication of MirrorFace's hacking techniques shows that cybersecurity is not a static state, but a dynamic process. It is not enough for organizations to rely on existing security systems; they need to constantly analyze new threats and adapt security strategies to stay one step ahead of attackers.
Source
According to the Japan Computer Response Coordination Center (JPCERT), the MirrorFace hacker group has been targeting media, political organizations, and academic institutions in Japan since 2022. And recently, hackers have also started attacking manufacturers and research institutes. Attacks range from targeted phishing emails to exploiting vulnerabilities in Array AG and FortiGate products.
Hackers use malicious NOOPDOOR software and various tools to steal data after entering the network. NOOPDOOR is a shellcode that is embedded in legitimate applications using two methods.
The first method involves running NOOPDOOR using an XML file containing masked code that is compiled and executed using MSBuild. This method stores encrypted data in specific registers for later use.
The second method uses a DLL file to load NOOPLDR into legitimate applications, hiding its actions through complex code obfuscation methods. Both types extract encrypted data from files or the registry, decrypting it using AES-CBC based on system information.

Both NOOPLDR attack methods (XML at the top, DLL at the bottom)
NOOPLDR samples vary in format (XML and DLL) and how they are implemented in Windows processes. XML samples mostly use legitimate processes for execution and store encrypted payloads in the registry. DLL samples show more complex behavior, including installing services and hiding them in the registry.
Some samples use the process "wuauclt.exe" for injections, others rely on "lsass.exe", "svchost.exe" and "vdsldr.exe". DLL variants also use Control Flow Flattening (CFF) obfuscation, complicating analysis. For deobfuscation, JPCERT / CC offers a Python script on GitHub.
NOOPDOOR can communicate on port 443 using the Domain Generation Algorithm (DGA) and receive commands on port 47000. In addition to standard actions such as transferring and executing files, NOOPDOOR can manipulate file timestamps, making it difficult for forensic investigations.
Hackers seek to gain Windows network credentials by analyzing process memory dumps, the domain controller's NTDS.dit database, and sensitive registry keys (SYSTEM, SAM, SECURITY).
After gaining administrator privileges on the Windows network, hackers spread malware through SMB and scheduled tasks, targeting file servers, AD and antivirus management servers.
After penetration, attackers conduct intelligence using the auditpol, bitsadmin, and dfsutil commands. They extract data using WinRAR and SFTP, after pre-scanning files with "dir /s" commands and attacking OneDrive, Teams, IIS, and other services.
The sophistication of MirrorFace's hacking techniques shows that cybersecurity is not a static state, but a dynamic process. It is not enough for organizations to rely on existing security systems; they need to constantly analyze new threats and adapt security strategies to stay one step ahead of attackers.
Source
