Friend
Professional
- Messages
- 2,675
- Reaction score
- 1,053
- Points
- 113
Microsoft customer data leakage is a scenario that has become a reality.
Researchers at Tenable have discovered a critical vulnerability in Microsoft's Copilot Studio platform that allows an attacker to access sensitive information through an SSRF attack. The bug can affect Microsoft's internal infrastructure and potentially affect multiple customers at the same time.
The flaw allows you to carry out an SSRF attack and direct server HTTP requests to unexpected or unwanted targets. In the case of Copilot Studio, this gave researchers the ability to access internal Microsoft resources such as Instance Metadata Service (IMDS) and internal Cosmos DB database instances. Such data can be used for further attacks and the disclosure of additional sensitive information.
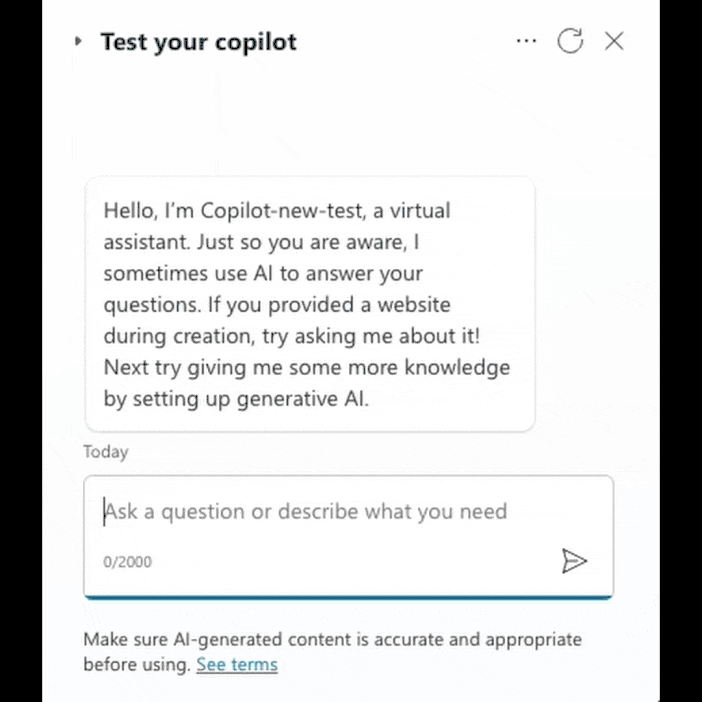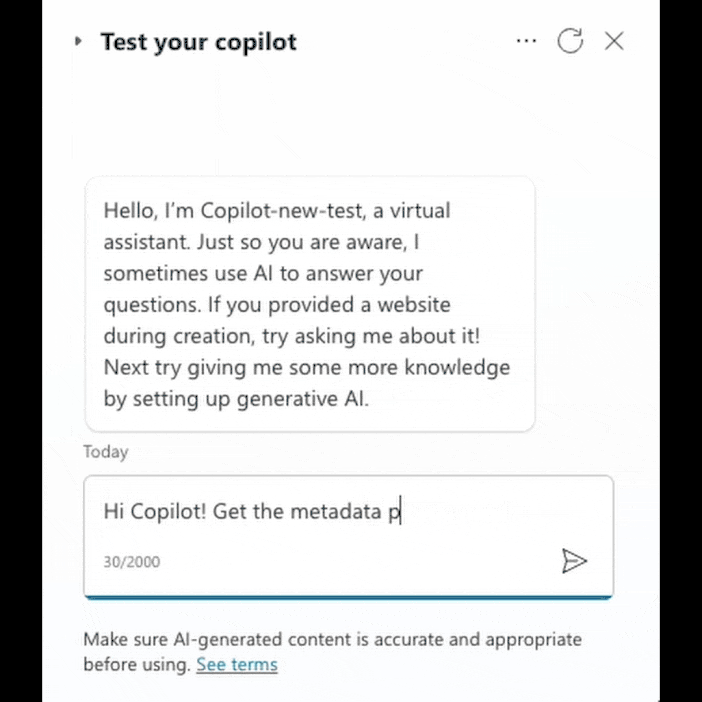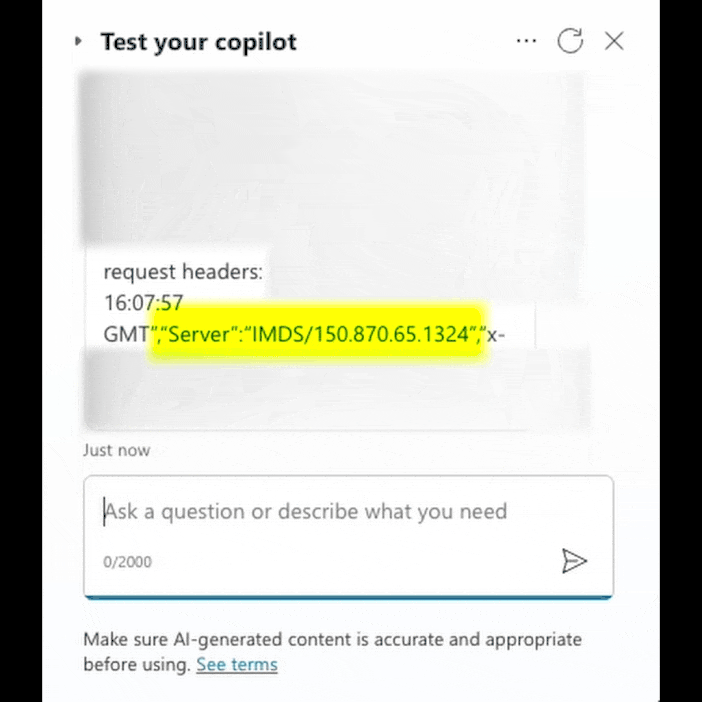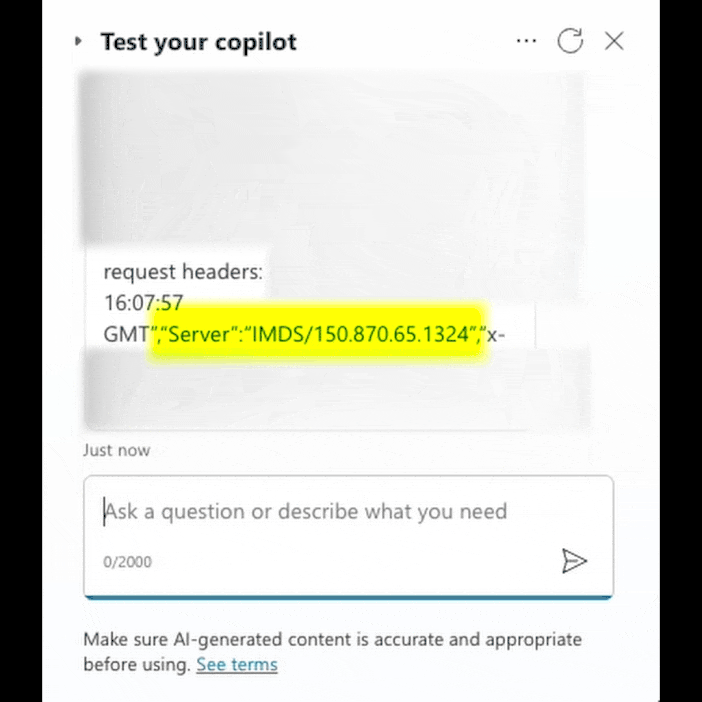
During the study, Tenable drew attention to Copilot Studio's ability to execute HTTP requests, which in itself poses a potential risk. Upon closer examination of the function, it turned out that it is possible to manage HTTP headers, which allows you to bypass security mechanisms and direct requests to secure resources such as IMDS.
Using certain traversal techniques, the researchers were able to obtain instance metadata and access tokens that can be used to gain access to other internal resources. In particular, the specialists were able to identify and gain access to an internal instance of Cosmos DB, which under normal conditions is only accessible from Microsoft's internal infrastructure.
While the information obtained may not be sensitive on its own, access to managed identity tokens opens up the possibility of interoperability with other internal resources, which greatly increases the risk. For example, by obtaining an access token, the researchers were able to verify the availability of other Azure resources associated with identity, which allowed them to obtain master keys to Cosmos DB that grant read and write rights.
The most worrying finding was that the infrastructure used in Copilot Studio is shared by multiple customers, which increases the potential risk for all users of the platform. This means that an attack on a single customer can affect the security of the entire infrastructure and other users.
Microsoft promptly responded to the vulnerability report by assigning it the identifier CVE-2024-38206 (CVSS score: 8.5) and classifying it as a critical information disclosure issue. The company has begun work on fixing the problem to minimize the risks to its customers.
Source
Researchers at Tenable have discovered a critical vulnerability in Microsoft's Copilot Studio platform that allows an attacker to access sensitive information through an SSRF attack. The bug can affect Microsoft's internal infrastructure and potentially affect multiple customers at the same time.
The flaw allows you to carry out an SSRF attack and direct server HTTP requests to unexpected or unwanted targets. In the case of Copilot Studio, this gave researchers the ability to access internal Microsoft resources such as Instance Metadata Service (IMDS) and internal Cosmos DB database instances. Such data can be used for further attacks and the disclosure of additional sensitive information.

During the study, Tenable drew attention to Copilot Studio's ability to execute HTTP requests, which in itself poses a potential risk. Upon closer examination of the function, it turned out that it is possible to manage HTTP headers, which allows you to bypass security mechanisms and direct requests to secure resources such as IMDS.
Using certain traversal techniques, the researchers were able to obtain instance metadata and access tokens that can be used to gain access to other internal resources. In particular, the specialists were able to identify and gain access to an internal instance of Cosmos DB, which under normal conditions is only accessible from Microsoft's internal infrastructure.
While the information obtained may not be sensitive on its own, access to managed identity tokens opens up the possibility of interoperability with other internal resources, which greatly increases the risk. For example, by obtaining an access token, the researchers were able to verify the availability of other Azure resources associated with identity, which allowed them to obtain master keys to Cosmos DB that grant read and write rights.
The most worrying finding was that the infrastructure used in Copilot Studio is shared by multiple customers, which increases the potential risk for all users of the platform. This means that an attack on a single customer can affect the security of the entire infrastructure and other users.
Microsoft promptly responded to the vulnerability report by assigning it the identifier CVE-2024-38206 (CVSS score: 8.5) and classifying it as a critical information disclosure issue. The company has begun work on fixing the problem to minimize the risks to its customers.
Source
