Man
Professional
- Messages
- 3,222
- Reaction score
- 1,201
- Points
- 113
Awaken Likho is changing tactics against government agencies.
SecureList researchers have discovered a new wave of attacks targeting Russian government organizations and industrial enterprises. The threat actors known as Awaken Likho (or Core Werewolf) have significantly changed their arsenal: they have moved from UltraVNC to the legitimate MeshCentral platform for remote access.
The campaign started in June 2024 and lasted at least until August. According to analysts, the Awaken Likho group has stepped up its activities since the start of the Russian-Ukrainian conflict.
The new implant was identified in September 2024. Telemetry analysis showed that the attackers had started using it about a month earlier. The software was distributed through phishing emails containing malicious URLs.
Hackers carefully prepare their attacks by using search engines to gather information about potential victims. This allows them to generate convincing phishing messages. The new implant is packaged using UPX and distributed in a self-extracting archive created using 7-Zip. The archive contains five files, four of which are disguised as normal system services and batch files.

The main component of the new malware is MeshAgent, an agent for the MeshCentral system. This legitimate open-source platform is designed to manage devices remotely.
The infection process begins with the execution of a MicrosoftStores.exe file that contains a compiled and obfuscated AutoIt script. It runs two other components: NetworkDrivers.exe and nKka9a82kjn8KJHA9.cmd.
NetworkDrivers.exe is a MeshCentral agent that provides remote access to an infected system. In turn, nKka9a82kjn8KJHA9.cmd is a heavily obfuscated batch file larger than 1MB.

Despite the significant amount of code, the principle of obfuscation is relatively simple. Attackers use large placeholder text insertions, which are skipped by the interpreter through the use of labels with the GOTO operator. After deobfuscation, it turns out that the main purpose of this batch file is to create a scheduler task called MicrosoftEdgeUpdateTaskMachineMS. And the task is executed by another script - EdgeBrowser.cmd, which is also contained in the unpacked archive.
Next, EdgeBrowser.cmd runs NetworkDrivers.exe (MeshAgent) using PowerShell to establish a connection to the attackers' command center.
The archive also contains the NetworkDrivers.msh configuration file, which contains parameters for connecting the agent to the MeshCentral server. These parameters include MeshName, MeshID, ServerID, and the address of a command center with a WebSocket connection.
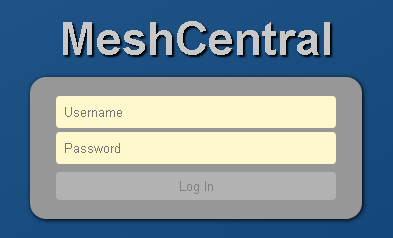
When trying to open the said address via HTTPS, the researchers found a login form for the MeshCentral platform – the main evidence of the previous findings.
The main victims of the described attack were government agencies in Russia, their contractors and industrial enterprises. All this also coincides with the previous goals of the group.
Researchers attribute the detected campaign to the Awaken Likho group with a high degree of confidence, relying on the tactics, techniques, and procedures (TTP) used, as well as information about the victims.
It is important to note that the new version of the malware differs from previous samples in the absence of files without payloads. This may indicate that the malware is still under development. Awaken Likho is likely to continue its activities in the future. Experts expect the emergence of new attacks using improved tools and techniques.
Source
SecureList researchers have discovered a new wave of attacks targeting Russian government organizations and industrial enterprises. The threat actors known as Awaken Likho (or Core Werewolf) have significantly changed their arsenal: they have moved from UltraVNC to the legitimate MeshCentral platform for remote access.
The campaign started in June 2024 and lasted at least until August. According to analysts, the Awaken Likho group has stepped up its activities since the start of the Russian-Ukrainian conflict.
The new implant was identified in September 2024. Telemetry analysis showed that the attackers had started using it about a month earlier. The software was distributed through phishing emails containing malicious URLs.
Hackers carefully prepare their attacks by using search engines to gather information about potential victims. This allows them to generate convincing phishing messages. The new implant is packaged using UPX and distributed in a self-extracting archive created using 7-Zip. The archive contains five files, four of which are disguised as normal system services and batch files.
The main component of the new malware is MeshAgent, an agent for the MeshCentral system. This legitimate open-source platform is designed to manage devices remotely.
The infection process begins with the execution of a MicrosoftStores.exe file that contains a compiled and obfuscated AutoIt script. It runs two other components: NetworkDrivers.exe and nKka9a82kjn8KJHA9.cmd.
NetworkDrivers.exe is a MeshCentral agent that provides remote access to an infected system. In turn, nKka9a82kjn8KJHA9.cmd is a heavily obfuscated batch file larger than 1MB.

Despite the significant amount of code, the principle of obfuscation is relatively simple. Attackers use large placeholder text insertions, which are skipped by the interpreter through the use of labels with the GOTO operator. After deobfuscation, it turns out that the main purpose of this batch file is to create a scheduler task called MicrosoftEdgeUpdateTaskMachineMS. And the task is executed by another script - EdgeBrowser.cmd, which is also contained in the unpacked archive.
Next, EdgeBrowser.cmd runs NetworkDrivers.exe (MeshAgent) using PowerShell to establish a connection to the attackers' command center.
The archive also contains the NetworkDrivers.msh configuration file, which contains parameters for connecting the agent to the MeshCentral server. These parameters include MeshName, MeshID, ServerID, and the address of a command center with a WebSocket connection.
When trying to open the said address via HTTPS, the researchers found a login form for the MeshCentral platform – the main evidence of the previous findings.

The main victims of the described attack were government agencies in Russia, their contractors and industrial enterprises. All this also coincides with the previous goals of the group.
Researchers attribute the detected campaign to the Awaken Likho group with a high degree of confidence, relying on the tactics, techniques, and procedures (TTP) used, as well as information about the victims.
It is important to note that the new version of the malware differs from previous samples in the absence of files without payloads. This may indicate that the malware is still under development. Awaken Likho is likely to continue its activities in the future. Experts expect the emergence of new attacks using improved tools and techniques.
Source

