This article will contain several methods for obtaining SS and draining them from the database of different sites. Those who have not yet tried to enter - read the previous articles.
The extraction of the mat usually occurs in the following ways:
1. Botnet.
2. Hacking shops, installing a sniffer.
3. Fake shop.
4. Vulnerabilities in ssl, extraction of exploitation-from mat.
5. Social engineering.
6. In Real.
Today we will look at how to break websites, leak databases and also extract SS.
Extraction of the victims' base.
It is very easy to get a database with SQLIDumper, a little patience and a straight hand will help. There are many articles written about the dumper on many forums, so I will run through it superficially. We will need SQLIDumper and Web Cruiser.
Here are the software/sources:
http://www.janusec.com/download/WebCruiserEnt.zip
https://www.sendspace.com/file/lwqsk1
(ATTENTION) If you don't trust my links, search the forums.
1. Having previously found the victim's website, copy its URL and paste it into the line of the same name in the program and click Scanner. Like this:
2. Next we go to the program vulnerability scanner tab window. Click Scan Current Site, in the window that appears click "OK" and see that the program has started "digging around" in the depths of the site - in all its contents, in order to find a vulnerability:

If everything goes well for us, and the site has "holes", then the program will definitely find them and indicate the above in the lower window:

Z. Once the scan of the current site is complete, the value "Done" will appear at the bottom.

What are we interested in? We are interested in URL Sql injection and POST Sql Injection vulnerabilities! If the program finds such, then:
Right-click on one of the vulnerabilities - a window appears in which we select SQL INJECTION POC: We have moved to the SQL server vulnerabilities tab:


What do we need now!? Now we need to determine the type of the database (Mysql, Sql server etc) and additional parameters that are available to us through this vulnerability. Click at the bottom of the window "Get Environment Information" (see the picture above) If everything went well, the program will find the type of database and give us columns with information about the database and the server.
If the database is unavailable, we will see a window with the message "Get database Type Failed Please select DB type manually!"

4. Check the boxes for what we need - user, database, Sa_PasswordHash and root_passwordhash (optional) and click Get Environment Information again.
We get the name of the db and the root hash of the admin (from the Sql server):
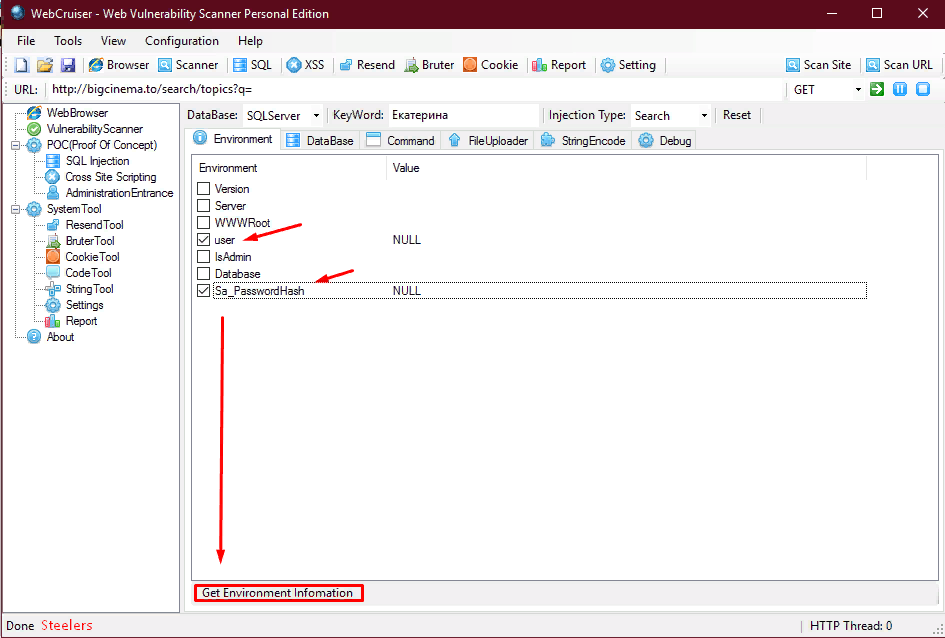
In my case, instead of user it showed NULL because for some reason the program could not get the information or it was unavailable.
Also, if NULL is written opposite the database, it means that most likely the database is not available to us (try through others,
vulnerabilities found using the algorithm described above):

Next, go to the tab
"DataBase"
where we already see our found db.
5. We put a tick on our db and click "Table" at the bottom of the window.
The program will start loading tables with the db we selected:
In the lower left corner, where I marked the Done parameter, at the moment of loading the tables there will be the inscription Getting Table,
then something like Get 1/32,1/56 - this means that everything is fine and the tables are loading.
And so, having smoked, drunk tea, and generally waited for some time (I'll tell you right away, the tables don't load quickly. You'll have to wait.) We see that all the Sql tables have loaded. We're interested in the Accounts table.
6. Select it and click "Column" at the bottom. The program starts loading the found columns in this table.
In this screenshot the Column button is not active because it was already pressed!
So, after some time, we see that all our columns from the Accounts table have loaded. Now we need to select the login and password parameters from these columns. We check the boxes above and see that these same columns have appeared on the right side of the tab that imitates the sql table.
7. The Rows from 1 to 2 field is responsible for the number of rows shown by the program. That is, by default, 2 rows will be shown (from 1 to 2). Therefore, instead of 2, you need to put a number corresponding to the number of registered accounts. Often, the number of accounts can be viewed on the website. After checking the boxes, click the "Data" button in the lower right corner. All the valuesof these columns begin to load, in other words, all accounts and passwords.

It takes a very long time (but believe me, it's worth it).
8. After waiting for all accounts and passwords to load (this can be seen from the inscription Done in the lower left corner of the program), click export and save our database in the xml extension.
9. Open with notepad and see our merged database in the form of acc:hash and rejoice
2. Spam.
My victim was this shop hyenacart.com
We go to the main page and study it, fantasize, plan, think about how to interest the victim and make him perform the actions we need.
As you know, everyone loves freebies, gifts, discounts!
We are preparing a letter.
We register in the shop to receive a letter from it and see the design. Or we compose our own design. We come up with the text of a supposedly mega cool sale or bonus giveaway. We google the visual HTML editor and compose a letter.
It turned out something like this for me)

Click the button "Source code" copy the letter code. For now save the code in txt
So we will spam the fake itself as an attachment to the letter under the guise of a coupon in order to avoid abuse of the server on which this fake would be hosted.
Let's go in order.
To begin with, you will still need a simple hosting on which you need to upload gate.php
This script will receive the report and send it to the email that you need to specify in the code.
And also a link where to send the victim after entering the information. You can specify a link to the shop from which the database was leaked.

Next, you will need minimal knowledge of htmlphp, or better yet, a coder) who will help you design a beautiful fake that we will spam in the attachment. Don't forget to write the path to the gate in the code of the attachment file (coupon.html).

This is the fake I got.

All that's left is to spam the database and wait for profit.
Try, test, improve the scheme. You can achieve good profit.
If you spam 40-50k emails per day, you can forget about buying material) Many will now start talking about inbox, etc. Believe me, in the leaked databases, not only bigs, on small servers sender2.php delivers spam to inboxes very well.
SQLi Dumper for Beginners
General concept of URL Analyzer
Such a peculiar Heavy, inside the dumper, but as for me it will be more powerful, to work with this tab you need to insert a link in the top line (URL address)
As you can see in the settings - I check all the boxes, I set the number of columns to 40 (Column Count) - this is quite enough, but if the site is large, it makes sense to add a number of columns, here more by experiment.
It is important to understand that the dumper does not work with one method. But with two, these are the GET and POST methods (there is a lot of information in Google for those who want to know more). Simply put - if the site did not succumb to SQL injection using the GET method, there is a chance that it will happen using the POST method

After you have done everything, press the GO button

The process is quite long, you will have to be patient, after the dumper has finished working, we will see if we can get access to the database, in my case everything went successfully, I got access to the database, our next step will be to click the Go to dumper button to start working with the database itself.

We are transferred to theData Dumper tab where we see approximately the DB itself and all possible settings on the right. Select the required DB - click Get Tables

Let's look at the example that we need to get data of the login

After clicking, we get a list of tables in the database, thinking logically, the data should be in the table user, client, login and the like.

Found what we needed. Now a little about the Data Dumper settings. The panel is quite extensive and there are a lot of settings here. But we will look at the ones we need.

Threads - the same as streams. My advice is always unambiguous regarding streams - the smaller the DB - the fewer streams, in order to exclude gaps, and on 50 streams the dumper sometimes misses.
The following parameters make users horrified and think, "Oh, come on, what the hell am I supposed to click here?"

This is an indication to the dumper what encoding the table is in, sometimes the table can be in a certain encoding that will not allow the dumper to correctly dump it, if you google what encoding your table is - you will successfully dump the information you need.
Next tabs

Timeout, delay and limit. It makes sense to adjust - when your site is a bit slow and the response from it comes over 5000 ms, Delay - the delay in which when receiving lines. Retry limit - the number of repetitions of requests to the DB.

After we have configured everything, we select the required columns and click Dump Data - we successfully merge the columns.
Next we need to save them txt. Click export data

We save what we need.
I won't go into detail about the File Dumper tab. Let's briefly go over the Toolz tab.

Utilites - the dumper contains various utilities for working with text.
Admin Login finder - search for admin in DB
Proxy - no explanation
Notepad - a notepad inside the dumper - I don't know why Flash stuck it there, sometimes you can write down something that comes to mind.
Settings - dumper settings, as for me, there is no need to change anything there.







