Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,025
- Points
- 113
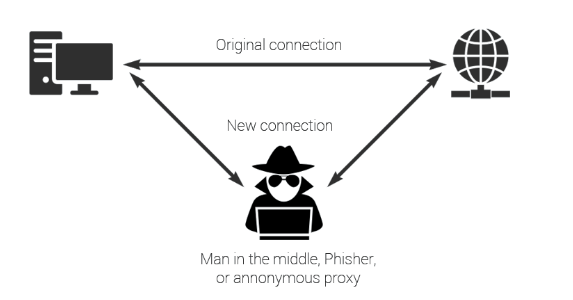
In this article, I'm going to explain to you what a "man in the middle" is, or one of the classic ways to steal data and control traffic.
To understand how it works:
To fully understand how this internet connection attack works, you first need to learn how the internet works in its basic form. There are three types of devices that are used: clients, routers, and servers. The most common protocol for a client is communication through a server, with a transfer protocol called http. Most web pages, as well as e-mail, instant messaging, etc., are implemented through this http protocol.
When you enter any site into your browser, client- you send a request to the web server. The http packet is passed through multiple routers on the server. The server then returns a web page, which is passed back to the client, and when it receives it, it displays it on your screen. This is vital to ensure that http messages can be transmitted in a secure manner to ensure anonymity and confidentiality.
Providing communication protocol
A secure communication protocol must have each of the following properties:
Privacy - only the recipient can read this message
Authenticity - the authenticity of the interacting parties
Integrity - confirmation that the message has not been altered in any way along the way
If any of this huge list fails, then the entire protocol is not functional!
Man in the middle http attack
On computer networks, an attacker can easily gain this position using a technique called ARP spoofing. Someone on Wi-FI can send you fake ARP packets, and you will unknowingly start sending all your traffic through an attacker-controlled router.
An attacker can sniff out, alter, or even terminate all movements of your traffic. He usually wants you to continue on the network, so he will configure a specific port that he will start using to forward requests.
To prevent such attacks, a secure version of the http protocol was created. Transport Node Security TLS and its predecessor, the Secure Sockets Layer (SSL) protocol, are both cryptographic protocols that ensure the security of data transmission over a network. Both are often referred to as SSL, and here we come to an interesting topic: you know this protocol as https, which means that the http puncture is implemented using the SSL protocol. You can configure your browser to use SSL by requesting any site (note the S at the end of http).
Such attacks are poorly implemented on the SSL protocol.
Modern SSL uses a good encryption protocol, but that doesn't mean anything if at least something is wrong. Since an attacker can modify the request, he intercepts your traffic, he will easily remove the "S" from the requested URL, the absence of which will allow the attacker to make sure that SSL is simply not used.
You can easily notice that your connection is not confidential and can be intercepted. If your request https://login.yahoo.com/ receives a response from http://login.yahoo.com, then you must suspect something. This simple check does indeed work on the Yahoo server, at least at the time of this writing.
To prevent this type of attack, servers can implement http with strict security, which is a way in which the server forces all connections to go through SSL only. If an attacker tries to delete S in this case, then the server simply will not respond to the web page, theoretically, a redirect to an unprotected version of the protocol is unlikely.
This way of implementing SSL is vulnerable to other attacks, an attacker can create an SSL connection to the server, but relay it to the user over the http protocol.
To prevent such attacks, modern browsers such as Chrome, Firefox and Tor (of course) track sites that use HSTS and SSL connections to them from the client side. So, the man in the middle - he needs to create an SSL connection for the victim. If the attacker does not have access to the victim's browser, then he is forced to act as a server with an SSL protocol, which is extremely difficult to obtain.
To secure SSL connectivity to the victim, an attacker must know how to act as a server, so let's dig into the intricacies of SSL.
Understanding the SSL protocol.
Let's take a look at all this through the eyes of a hacker. Hacking any communication protocol comes down to the ability to attack the weak link of the above three properties (confidentiality, integrity, authenticity).
SSL uses an asymmetric encryption algorithm as opposed to symmetric encryption. In symmetric encryption, the same key is used to encrypt and decrypt data. This is terrible for Internet protocols, because an attacker can always steal and obtain the protocol during the start of the conversation, when the participants choose the key.
Asymmetric encryption includes 2 keys, for each participant, the public key is used for encryption and the corresponding private key for complete decryption of the data. All you have to do is tell everyone to use your public key and everyone can send an encrypted message, but only you can read it.
How does SSL provide the three properties necessary for secure communication? Communication is private because asymmetric cryptography is used for the transmitted data. This encryption is not something that ordinary Vasya can easily break, so that an attacker cannot quickly and easily change messages without being detected, the integrity will be violated.
The server verifies the identity of the client by sending an SSL certificate signed by a certification authority - a third trusted party. Certificates are designed so that only a valid server will have the private key.
If the attacker somehow still gets the certificate, then he will get the position of the man in the middle. Then the attacker needs to create 2 SSL connections, one with the server and one with the victim. The server will think that it is a regular client, and the victim does not even have the ability to detect the attacker, because he has provided "evidence" proving that he is the owner of the server.
Your messages from end to end are encrypted, except for the attacker's computer, where he will have full control. It can also improve the effectiveness of any attacks. so there is no need to strain hard and decrypt the data.
If done correctly, the best attack is certificate manipulation.
The certificate must not be fake if the attacker decides to compromise the victim's browser. In this case, he can insert a self-signed certificate that can be trusted by default. This is how most attacks have been done before. In other cases, the offender will take on more business - forge a certificate on his own.
Issues with certificates
Server certificates are sent by special offices that issued and signed certificates. Each browser has a list of trusted CAs, and you can add or remove any. The problem here is that if you decide to remove, for example, the third, largest authority, you will not be able to visit almost any sites that use certificates from this center, will write that it is dangerous or an attack is possible.
Certificates and CAs have always been the weak link of the https connection. Even if everything was done correctly and each certification authority issued only these certificates to trusted servers, I still cannot understand - why should I trust some unknown people?
Today, a huge number of people work for 650+ organizations that issue these same certificates, the number, I am sure, is such that many of you will suspect that something is wrong. If any of them is hacked, then the attacker will receive any evidence he wishes.
Even when there was a single certification authority, VeriSign, an absurd problem arose - the people we should trust to prevent attacks on us just started selling data interception services.
Many certificates have been cracked, at very many levels. Countless bugs have been used to trick victims into trusting bogus certificates. If you are interested in the topic. then I recommend that you study it much more carefully, the network is full of information, otherwise I will write a treatise in a couple of volumes.
Forensic examination
The attacker is sending a fake ARP packet, you will not see his IP address wherever he is, but you must insist on finding the MAC address, which is specific to each piece of equipment on the network. If you know that your router has a specific MAC address, then you can compare it with the MAC address of your default gateway to see if this is really your router at all or is it an intruder.
On Windows, for example, you can use the "ipconfig" command at the cmd prompt to see the IP address of your default gateway, this is the last line.
Then use the “arp –a” command to see your MAC address, physical, and gateway.
If you do not know the MAC address of your router, you can still spot the attack if you are monitoring network activity while the attack has begun, observe the packets. You can use wireshark to monitor and log network activity. If you have reason to believe that someone will try to attack you, he is not crazy by the way, you need to run an automated tool that will notify you if the MAC address of the default gateway changes.
Note: if the attacker is far from being a fool, he will change the MAC address correctly, and playing Sherlock Holmes will become a headache for you.
Conclusion
SSL is a good protocol because it forces an attacker to do a tremendous amount of work if they want to sniff out your sensitive data, but that will not protect you and us from government hackers and qualified organizations.
Like any ordinary user, you are interested in the confidentiality of your work, you want to protect your browser, personal computer, in order to prevent the insertion of a fake certificate, you must first study all certification authorities and consider the entire list, in turn deleting all those whom you personally do not trust.

