BadB
Professional
- Messages
- 2,494
- Reaction score
- 2,549
- Points
- 113

Experts from Cisco Talos and Doctor Web announced the emergence of new modifications of the Trojan, which appears in companies' reports under the names Trojan.PWS.Stealer.23012 and TeleGrab.
Malvar
This malware was first detected in early April 2018, but after a couple of weeks, experts noticed that new versions of the malware had appeared. So, the first variant was written in Python and stole credentials from Chromium-based browsers, along with cookies and text documents found on the system.Other versions, in turn, acquired functionality that allows you to collect cache files and keys from the Telegram messenger, as well as credentials from games on Steam, information from the FileZilla FTP client, copy image files and office documents according to a predefined list, passwords, etc. cookies from the browsers Google Chrome, Opera, Yandex Browser, Vivaldi, Kometa, Orbitum, Comodo, Amigo and Torch, as well as copies of images and documents stored on the Windows desktop.
Doctor Web experts write about a modification of the Trojan (Trojan.PWS.Stealer.23732), the dropper of which is written in Autoit. It saves to disk and launches several applications that are components of the malicious program. One of them is a spy module, like its predecessors, written in Python and converted into an executable file. It steals confidential information on an infected device. All other components are written in the Go language. One of them scans disks in search of folders in which browsers are installed, and another one packs the stolen data into archives and uploads them to pCloud storage.
Analysts say that threats are mostly spread through links in comments posted on YouTube videos. The videos themselves were devoted to the use of special programs that facilitate the passage of computer games - various cheats, guides and trainers. Attackers leave comments under such videos from fake accounts with a link to Yandex.Disk. Also, these malicious links were actively promoted on Twitter.
In addition, to distribute new modifications of the malware, the cybercriminals who bought it from the virus writer came up with another, more original method. Thus, the criminals contacted the administrators of thematic Telegram channels and suggested that they write a post dedicated to the new program allegedly developed by them, and offered to test it. Allegedly, the program allowed you to simultaneously connect to several Telegram accounts on one computer. In fact, under the guise of a useful application, they offered potential victims to download the spyware.
Cisco researchers emphasize that criminals do not exploit any vulnerabilities in Telegram, they simply attack users of desktop versions of Telegram who do not support secret chats and generally have weaker default settings.
For example, the malware collects all Telegram cache data and sends it to the attackers. During the investigation, experts even found a training video that explained in detail how to use this data to intercept someone else's session. Unfortunately, the video has now been removed. The point was that restoring cache and map files in an existing installation of the desktop version of Telegram, with an open session, allows an attacker to gain access to the victim's session. This includes all contacts and previous chats. Cisco believes that the author of the malware and the author of the mentioned video are one person.
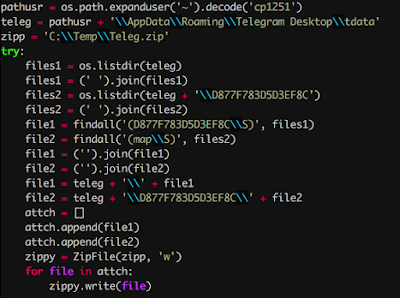
Preparing to retrieve data
Experts note that the described technique is very unusual, because, as far as experts know, there is currently no decryptor for cache information. However, in the TelegramDesktop GitHub repository, you can find discussions that suggest that in theory it is possible to create such a tool.
So, the keys used to encrypt Telegram files are stored in map * files, and those, in turn, are encrypted with the user's password. In theory, the attacker does not have a password for these files, but he could create a tool to brute force passwords. Since Telegram uses AES encryption, the researchers speculate that an attacker could use OpenCL or could create an addon for HashCat .
At the same time, experts emphasize that even in the above-described case, the criminal gains access only to the local cache, and it is impossible to predict what exactly is stored locally. We can only say with confidence that chats are stored in the cloud.
Virus writer
Analysts from both companies managed to get on the trail of the author of the above malware. Researchers say that he is hiding under the pseudonyms Eyenot (Raccoon / Enot) and Raccoon Pogromist, while he not only develops the Mavar, but also sells it.Doctor Web writes that the author of the malware maintains a YouTube channel dedicated to malware development and has his own page on GitHub, where he uploads the source code of his malware.
Cisco specialists give more details and say that since 2017 the malware author has been active on the lolzteam.net hacker forum, where, for example, he recently posted an article titled " Hacking Telegrams in 2021", which traces the malware customization process.
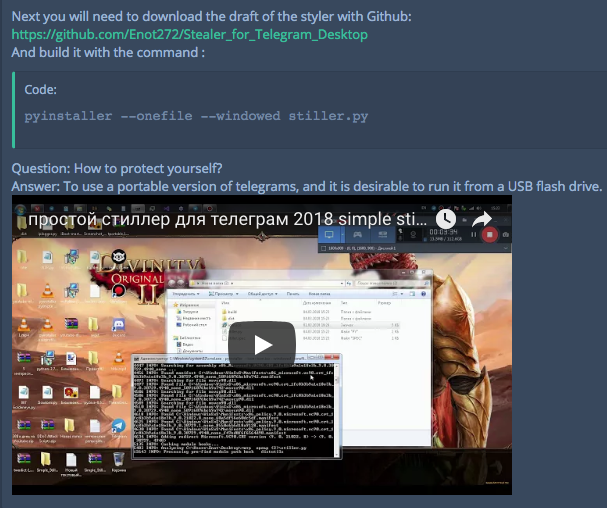
Another hacker forum (sft.st) advertises this malware as a product for sale. There, analysts found a link to a GitHub account owned by the user Enot272, as well as a Python script and other tools (already removed from the repository, but can be seen in the screenshot below), with which users were asked to reproduce the hacker's actions and demonstrate it.
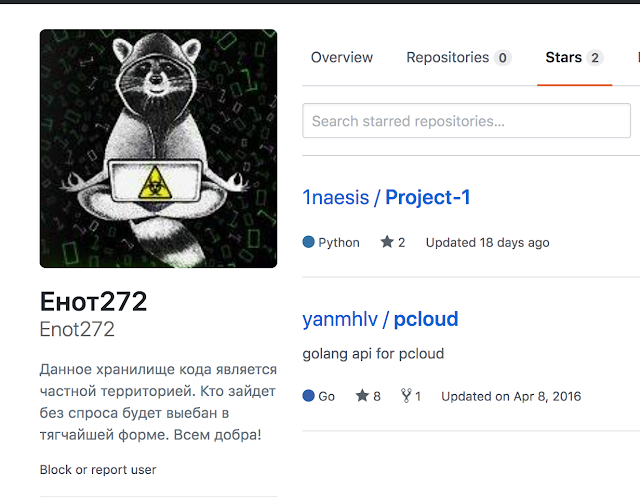
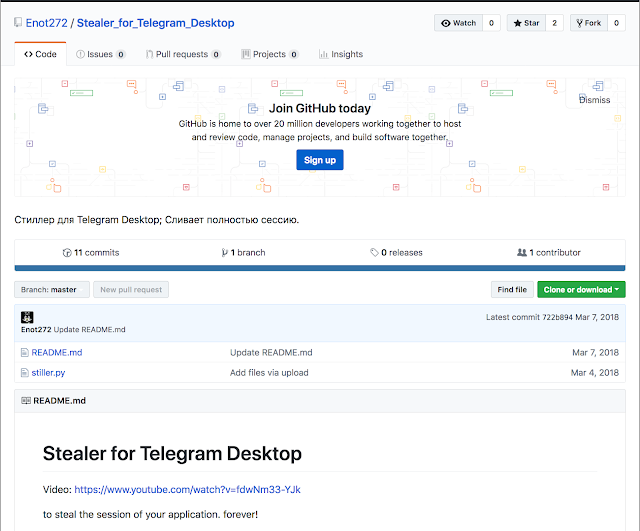
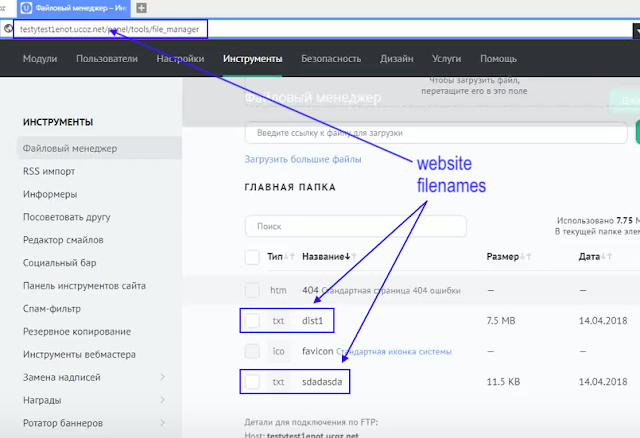
The researchers noticed that the profile icon on GitHub matches the icon for the aforementioned YouTube account. One of the videos made it possible to establish a connection between the Raccoon and the malware, since the video just described the creation of a loader using AutoIt. This video flashed the site testytest1enot.ucoz.net and its contents, among which experts noticed the files dist1.txt and sdadasda.txt, which exactly matched the samples available to the specialists and the URLs in the droppers.
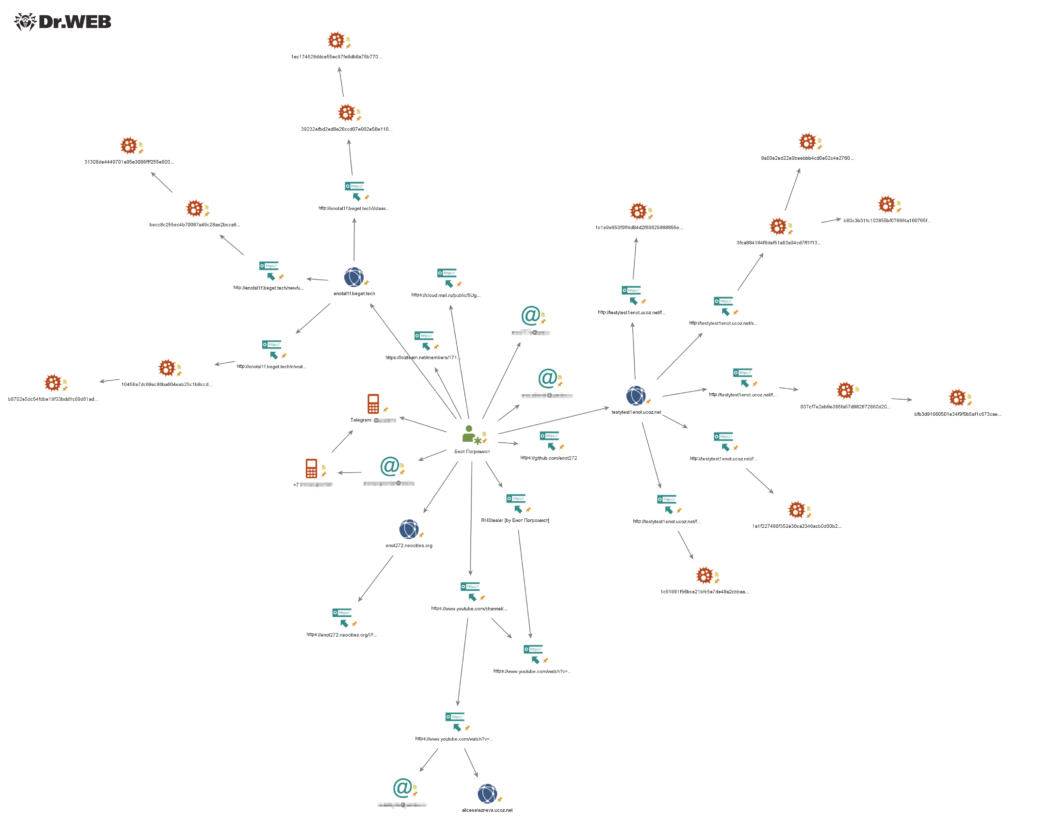
Doctor Web's specialists also analyzed data from open sources and identified several email addresses of the Trojan developer, as well as his mobile phone number, to which the Telegram account used for illegal activities is linked. In addition, they managed to find a number of domains used by the virus writer to spread malware, as well as determine the city of his residence. The diagram below shows some of the Pogromist Raccoon's identified connections with the technical resources it uses.
Doctor Web experts write that logins and passwords from cloud storages, into which archives with stolen files are loaded, are embedded in the body of Trojans, which makes it possible to easily identify all Raccoon Pogromist clients who purchased malware from him. These are mainly citizens of Russia and Ukraine. Some of them use email addresses that make it easy to identify their social media pages and establish their real identities. For example, Doctor Web employees managed to find out that many of Raccoon Pogromist's clients also use another spyware, which is sold on underground forums. It is worth noting that individual buyers were so smart that they ran the spy on their own computers, probably in an attempt to evaluate its work. As a result, their personal files were also uploaded to cloud storage.

